SpyCloud Resources
Insights from the criminal underground that help you get ahead of the latest threats
Main Menu
Case Studies
How 360 Privacy consolidated their tech stack while expanding their service offerings with SpyCloud
LendingTree, the nation’s largest financial lending marketplace, works to stay ahead of cyberattacks and protects sensitive business-critical information with SpyCloud Employee ATO Prevention.
With Session Identity Protection, Atlassian now protects its more than 250K cloud customer accounts from session hijacking, automatically, with zero operational overhead.
A biomedical research firm protects its employee accounts from account takeover and ransomware with SpyCloud’s automated Enterprise Protection solutions.
This Fortune 50 computer manufacturer and retailer incorporated SpyCloud’s automated consumer fraud risk analytics into their security technology stack to reduce manual review and enhance fraud investigations.
EUROCONTROL protects its 2,000 employees and 1 million constituent accounts on 130 domains from ATO that can lead to ransomware attacks, increases cybersecurity awareness, and provides enormous value to their security program with SpyCloud.
An ecommerce marketplace uses SpyCloud Consumer ATO Prevention to reduce ATO fraud, avoid fraud losses, and reduce resources dedicated to ATO prevention.
Atlassian protects its employees and customers from cyberattacks with SpyCloud’s solutions, reducing resource hours spent researching Atlassian’s potential involvement in public breaches and securing its brand reputation.
This Fortune 100 financial services company protects millions of financial services consumers from account takeover fraud with SpyCloud, while also enriching their online fraud investigations with SpyCloud data.
A global professional services firm uses SpyCloud Active Directory Guardian to monitor the credentials of over 6,000 employees across all of the company’s global offices, as well as service providers enrolled in their Active Directory.
With SpyCloud, this global fintech platform has been able to automate consumer account takeover prevention at scale, protect thousands of users infected with credential-stealing botnets, and enrich their predictive models and investigations.
SpyCloud enabled a global managed services provider to expand the value of their offering by adding credential monitoring services and increasing the quality of their threat intelligence reports—all without hiring additional staff.
Zscaler is a cloud-based security company that is completely transforming the way companies approach information security.
With few resources to dedicate to account takeover prevention, this large US university was settling for a mediocre security solution that required too much manual effort.
With few internal resources or sufficient tools to identify and remediate exposed student, faculty and staff email accounts, OU was at constant risk for accounts being compromised.
Discovering exposed user credentials across the global networking company’s many domains proved to be challenging using old, redundant, and undecrypted password data from an incomplete solution.
Preventing account takeover begins with monitoring the dark web, but without the ability to match user accounts with a database of exposed credentials, a top 10 travel booking site was vulnerable to attack.
Preventing a security breach that impacts their customer data is a top priority, yet without credential exposure monitoring & reporting, this company was at constant risk.
Datasheets
Reduce your risk of ransomware and other critical attacks by acting on known points of compromise before they can be used by cybercriminals.
Cover a range of NIS2 requirements and see value on day one with SpyCloud.
Dramatically increase the accuracy and speed of investigations
Take a proactive approach to combating ATO by identifying your customers’ darknet exposures and stoping high-risk attacks tied to malware
Stop session hijacking by securing your consumers' accounts
Strengthen account security and reduce account takeover
Leverage SpyCloud cybercrime telemetry in your Zero Trust policy engine for always-on authentication.
Tools
- Tools
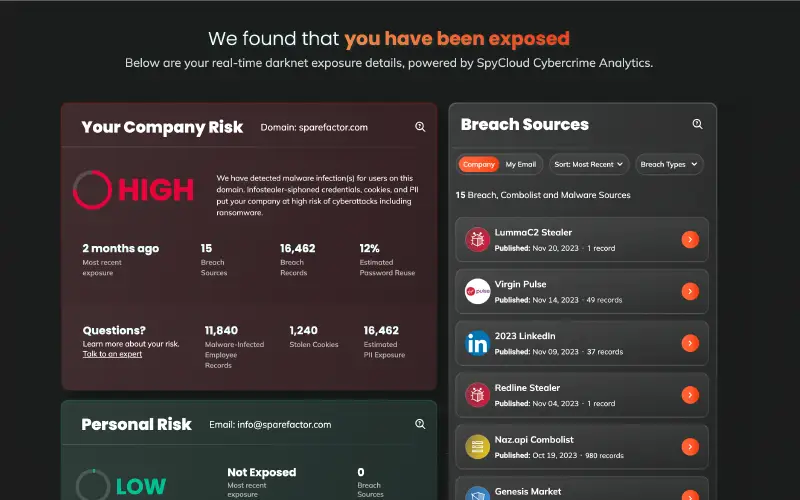
Darknet Exposure Check
Identify threats to your organization including third-party breach exposures, malware-infected employees, stolen session cookies, and more.
- Tools
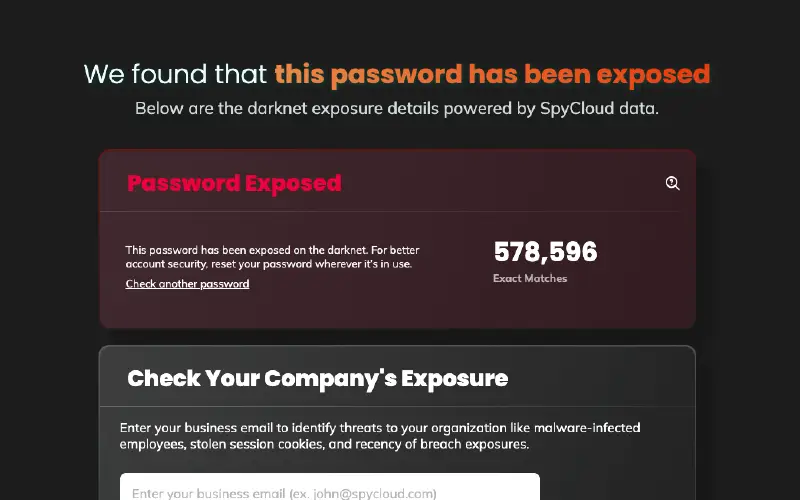
Password Exposure Check
Test any password to see how many times it has appeared on the darknet, meaning it’s unsafe to use.
Guides
Security teams are up against a lot. This checklist will help your team optimize your data so you can use powerful automation to protect against next-gen threats.
Learn how SpyCloud Consumer Risk Protection helps you navigate modern account takeover methods by strengthening account security and reducing risk.
SpyCloud Enterprise Protection integrates with security tools you’re already using and scales with the threat landscape – backed by analytics
derived from the industry’s largest repository of recaptured data. See how it works.
Ransomware is a top cybersecurity challenge for organizations today. Use this handy checklist to inform your ransomware prevention strategy as attackers evolve their techniques.
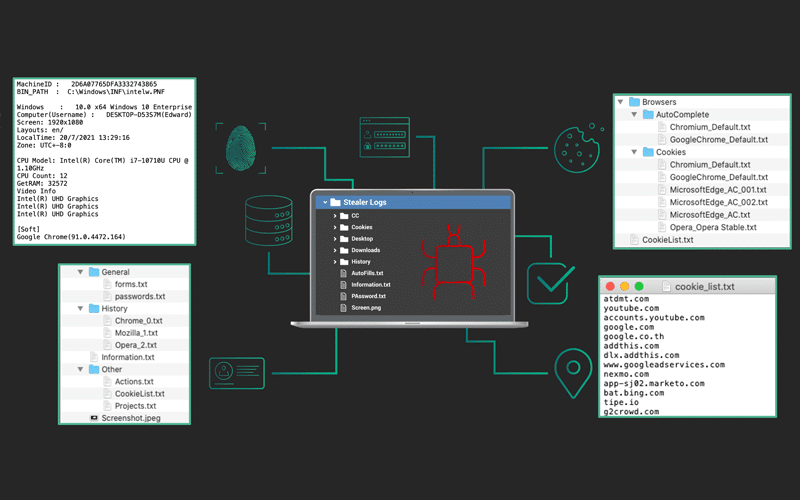
Post-Infection Remediation is SpyCloud’s new, critical addition to malware infection response. This guide goes in-depth on how to stop malware exposures from becoming full-blown ransomware incidents.
Handy guide to decipher what it means when employee or consumer information appears on a botnet log, and how to contact infected users with an action plan.
When your consumers' passwords appear in a third-party breach, the language you use to notify them that their passwords must be reset requires careful consideration.
Our guide includes a 20-item checklist of topics to discuss with each ATO prevention vendor you're evaluating.
Download our guide to learn what swift actions government agencies can take to prevent employees' and consumers' data from being siphoned by keylogger malware.
Get advice from CISOs who have been through worst-case scenarios: breaches that exposed customer data. Their experience will help you better prepare your own breach prevention and response plans.
Aligning your enterprise’s password policy with the latest guidelines from NIST can help encourage better password habits and reduce the risk of account takeover.
Read this solution brief to understand the benefits of using SpyCloud to align with NIST password guidelines.
Over the years, security professionals have learned surprising lessons about how password policies affect user behavior.
Research Reports
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.
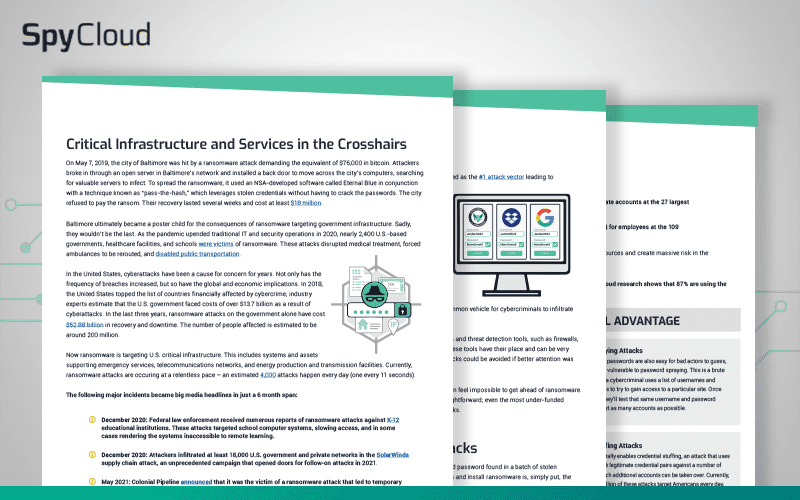
As cybercriminals continue to reap rewards from ransomware attacks, how are security teams keeping pace? Download this year’s report for insights on new trends, attack precursors, and critical defense gaps.
SpyCloud’s new report reveals gaps that exist in malware remediation practices and what enterprises can do to slam the door on cybercriminals seeking to harm your business via infostealer malware.
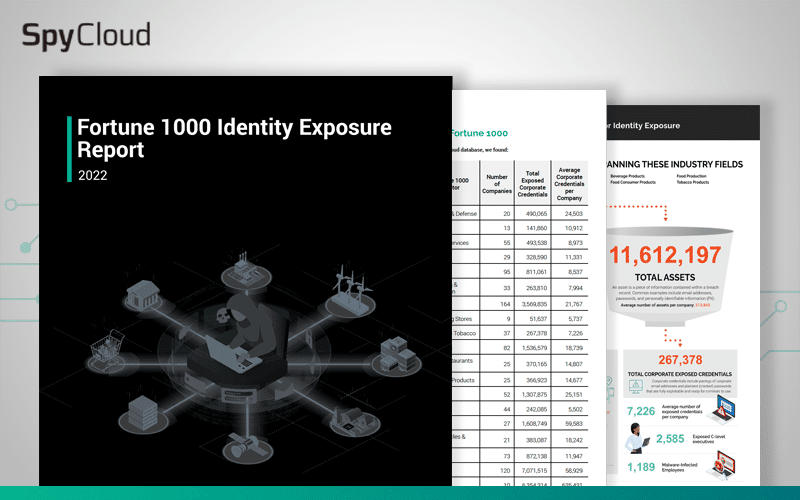
This year’s analysis of stolen identity data tied to Fortune 1000 companies uncovered shocking amounts of breach and malware-exfiltrated assets that put large enterprises at risk of ransomware and other critical cyber threats.
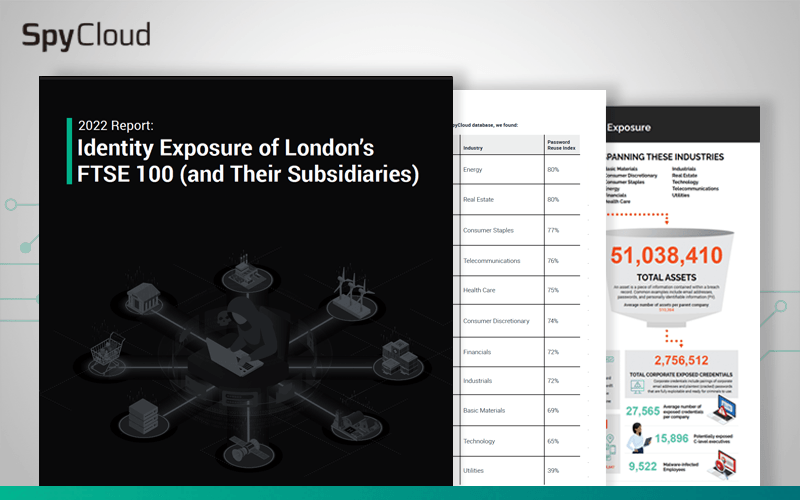
Read how the more than 100M breach assets and malware-exfiltrated cookie records tied to FTSE 100 companies and their subsidiaries on the darknet make these large UK enterprises susceptible to cyberattacks.
With nearly half of our data coming from botnets last year, our annual report of recaptured darknet data features key trends about malware and identity exposure.
Our annual report shows a surprising increase in organizations that experienced multiple ransomware attacks, the costly impacts of ineffective countermeasures, and future plans to improve defenses.
Read key insights from CISOs on the challenges facing organizations, including compromised identities, ransomware attempts, and implementation of Zero Trust Models.
Our annual analysis of data tied to Fortune 1000 companies includes insights on credential exposure, password reuse rates, and the impact of malware-infected employees and consumers.
Our annual analysis of exposed credentials and PII tied to London's FTSE 100 employees uncovered insights about password reuse and malware-infected devices that put these organisations and the companies that rely on them at risk.
Our annual reports analyzes the 15.5 billion assets we recaptured from the criminal underground last year, and how enterprises can use this information to protect themselves from ATO, malware, and ransomware, and protect their consumers from online fraud.
Our report breaks down the frequency of ransomware attacks on organizations of all sizes, insights on ransomware preparedness measures, and details on the criminal economy that’s fueling ransomware right now.
The prevalence of password reuse and loose credential security protocols are gifts to cybercriminals that expose the U.S. to significant risks.
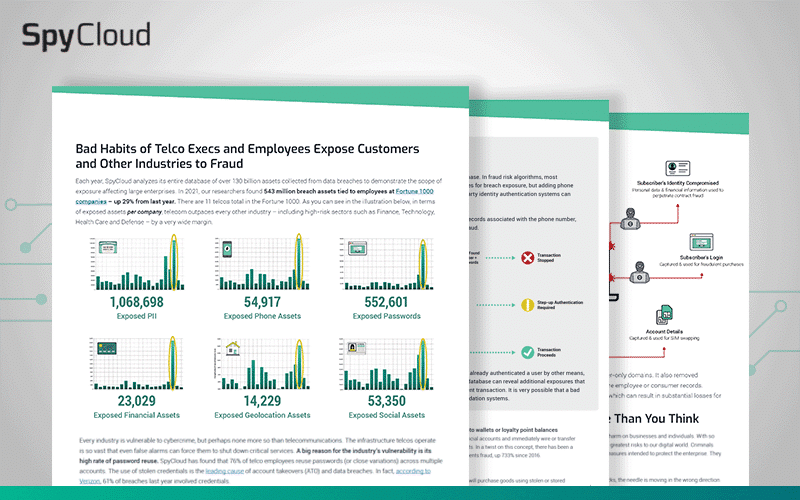
Every industry is vulnerable to cybercrime, but perhaps none more so than Telecommunications. Find out why, see the extent of exposed data, and discover specific ways to shore up your defenses.
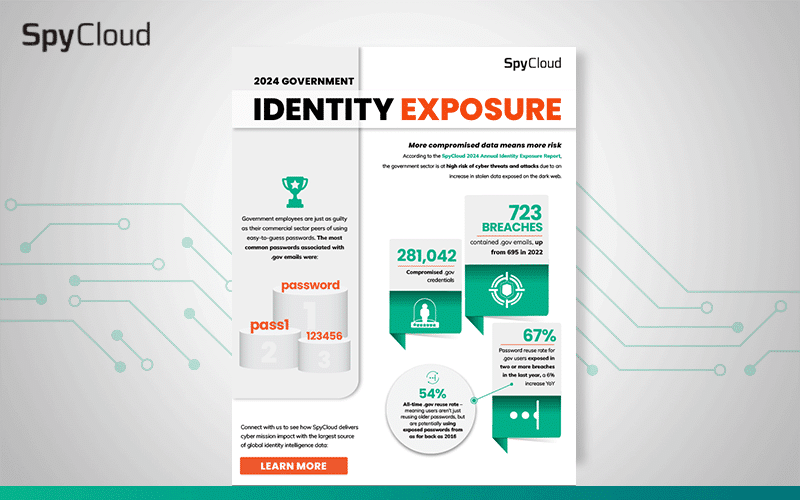
Over the last 12 months, SpyCloud has recovered 1.5 billion credentials from 854 breach sources. Find out the trends our researchers have observed, including exposed .gov credentials and pandemic-themed keywords in users' passwords.
SpyCloud found over 39 million breach assets tied to FTSE 100 & subsidiary companies on the criminal underground. What else did we discover and how does your industry stack up?
Find out what SpyCloud learned by analyzing millions of data breach records and botnet logs tied to employees of Fortune 1000 enterprises.
Learn how your peers are tackling the top threat vectors facing remote workers, including phishing, malware, and account takeover.
Whitepapers & Ebooks
Examining the state of password security today and the challenges facing passwordless solutions, this SpyCloud report offers clear guidance on protecting your user accounts without having to reinvent the wheel.
Learn about the new way to disrupt cybercrime with automated analytics that drive action. Discover why market leaders across all industries are choosing Cybercrime Analytics over threat intelligence, how this approach boosts anti-fraud solutions, and its use cases and benefits in detail.
Malware infections siphon valuable data like fresh credentials and web session cookies, giving bad actors the virtual keys to your enterprise. SpyCloud breaks down malware infections and offers context around the steps criminals take with malware-stolen data, and what can be done to stop this insidious threat.
How can merchants best balance the customer experience and fraud prevention? Our report offers a new approach for merchants to differentiate between low- and high-risk customers.
FIs must strike a balance between prevention controls and fraud mitigation while ensuring a quality customer experience. Our report delves into a new framework for understanding the risk that each individual consumer presents at key points in their journey.
SpyCloud and the Communications Fraud Control Association (CFCA) created this consumer education document to help you understand what identity theft is & how to prevent it.
As stolen credentials have become more accessible on the dark web, so has the ability to compromise legitimate business email accounts to commit fraud.
Understand how hackers combine attack methods and stolen credentials to sidestep multi-factor authentication.
We tap our expertise in helping organizations recover exposed credentials to help you understand the anatomy of credential stuffing attacks, why they persist, and what you can do to prevent them.
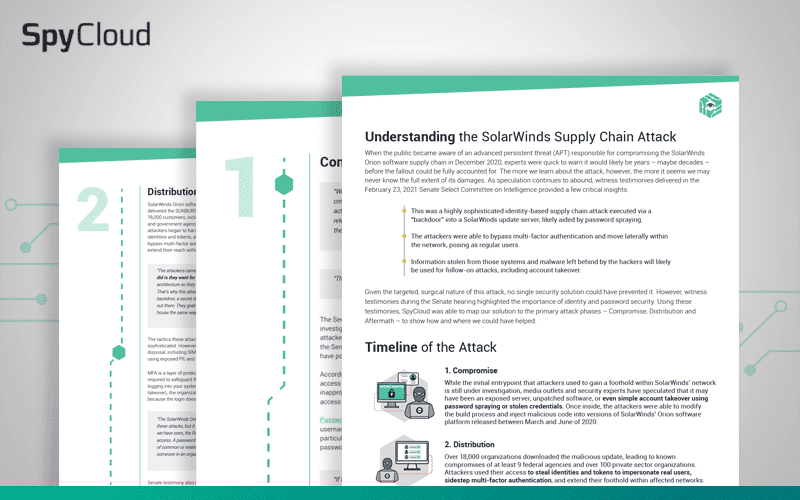
The SolarWinds supply chain compromise will have repercussions for years to come. Using witness testimony from the February 23, 2021 Senate Select Committee on Intelligence hearing, we broke down the timeline of the attack and examined how SpyCloud could have helped at each stage.
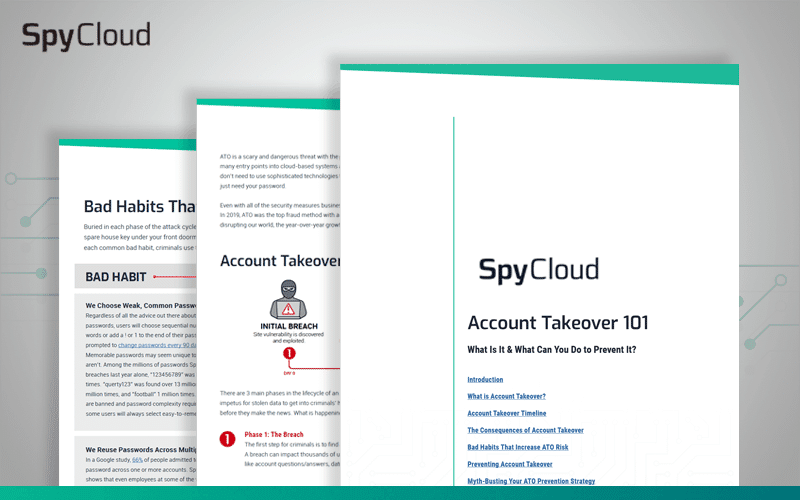
You can’t stop ATO until you understand it. Get this plain-English primer on the latest attack methods, bad habits that increase ATO risk, and strategies for prevention.
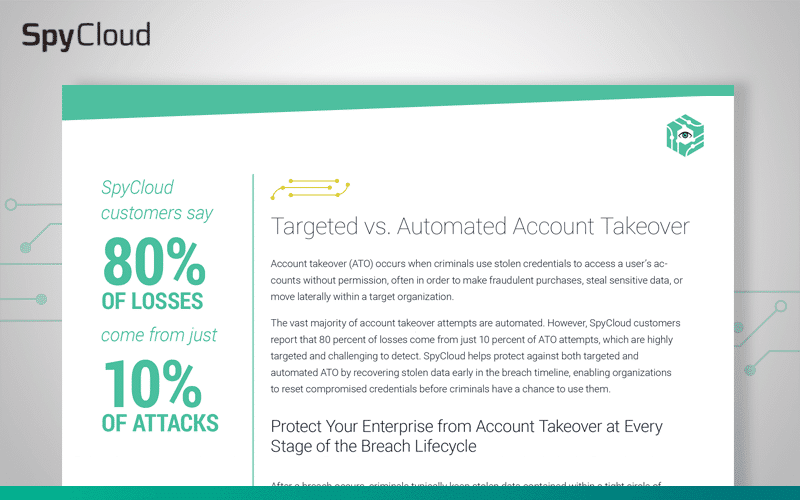
Account takeover can be highly-targeted, sophisticated, and manual, or it can be high-volume and automated. Learn how to protect your enterprise from both types of ATO.
Everything you ever wanted to know about GDPR in (Relatively) plain english, along with information for companies evaluating SpyCloud.
Download the ebook, 6 Myths about ATO Prevention Strategies to learn which of the most common techniques and technologies help and which provide false hope.
Webinars
Learn how to address a common Zero Trust implementation gap that is leaving organizations vulnerable to targeted attacks: users' stolen session cookies.
In this webinar, we cover top trends from the SpyCloud 2024 Identity Exposure Report. Learn about the identity threats putting organizations everywhere at risk.
Learn how actionable data analytics from SpyCloud helps your security team scale, use resources more efficiently, and shorten investigation time.
Hear from SpyCloud Labs researchers how Chinese cybercriminals are accessing, exfiltrating, and trading vast amounts of PII, with international impact.
This webinar breaks down the most important findings from SpyCloud’s 2023 Ransomware Defense Report, and what your organization can do to get ahead of emerging cyber threats.
On-Demand Webinar: Explore the evolution of authentication and scrutinize common myths around passwordless technology.
On-Demand Webinar: Unveil the top darknet exposure trends for London’s FTSE 100 companies, including insights on password reuse, stolen session cookies and cloud app exposures
On-Demand Webinar: We break down the latest trends related to identity exposure in the criminal underground and how this data puts organizations and consumers at risk of cybercrime.
On-Demand Webinar: Learn about a new, more complete and more effective approach to preventing ransomware called Post-Infection Remediation.
On-Demand Webinar: Learn how stolen data makes its way from small circles of bad actors to the dark web and how to identify legitimate consumers interacting with your site vs. criminals leveraging stolen data.
On-Demand Webinar: Benchmark your ransomware preparedness & discover proactive strategies to solve your defense blindspots.
On-Demand Webinar: A detailed look at how anti-detect browsers + malware-stolen data put consumers at risk of fraud, and how Session Identity Protection helps protect your bottom line by offering early warning of malware-infected consumers with compromised web session cookies.
On-Demand Webinar: Analysis of the 15+ billion assets we recaptured in 2021 and what we can learn from patterns we've observed in the criminal underground over the last 12 months.
On-Demand Webinar: SpyCloud researchers share an inside look at 2021 holiday shopping trends on popular cybercriminal communities, including botnet logs for sale that allow bad actors to impersonate your consumers.
On-Demand Webinar: We break down the ransomware ecosystem, adversary groups’ latest tactics, and strategies to mitigate your risk and avoid paying millions to ransomware gangs.
Security leaders who have been through worst-case scenarios offer real-world advice for stronger breach prevention & response. Get the audio file or watch the panel webinar on-demand.
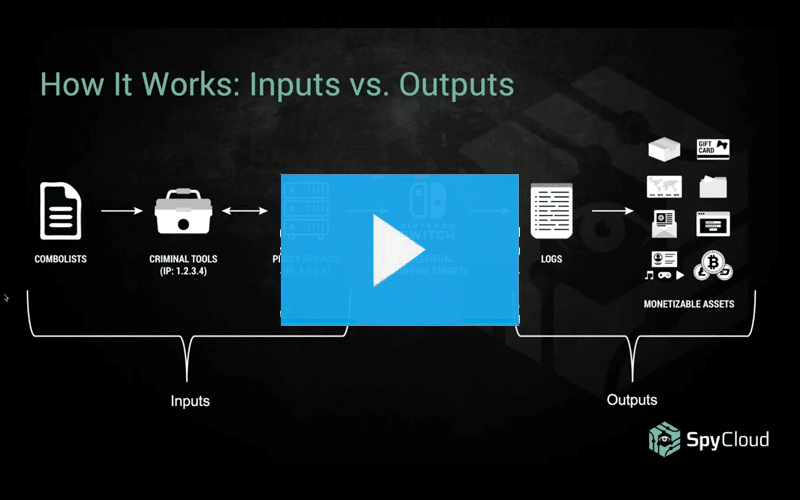
Learn how credential stuffing works and get insights into the tools of the trade (including some very sophisticated custom Nintendo crimeware). Discover why stolen accounts that don’t have obvious monetary value can be profitable for cybercriminals.
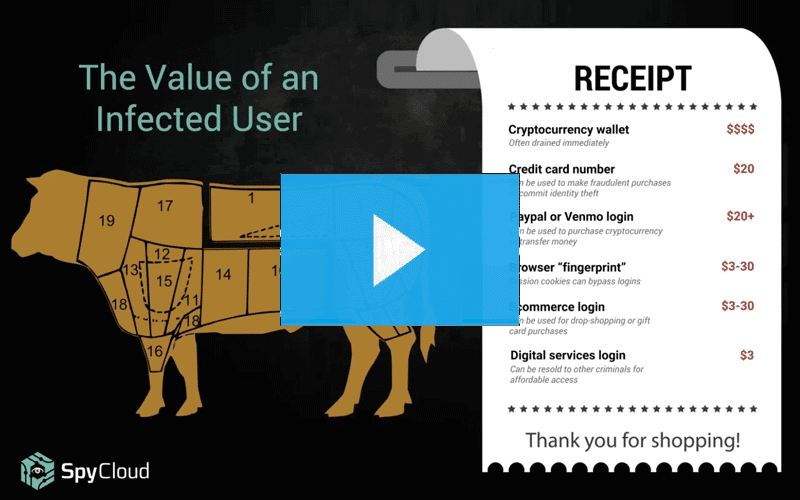
See malware from the criminal perspective, including how the data collected from infected machines gets monetized. Learn how to shield your organization from the damage caused by credential-stealing malware.
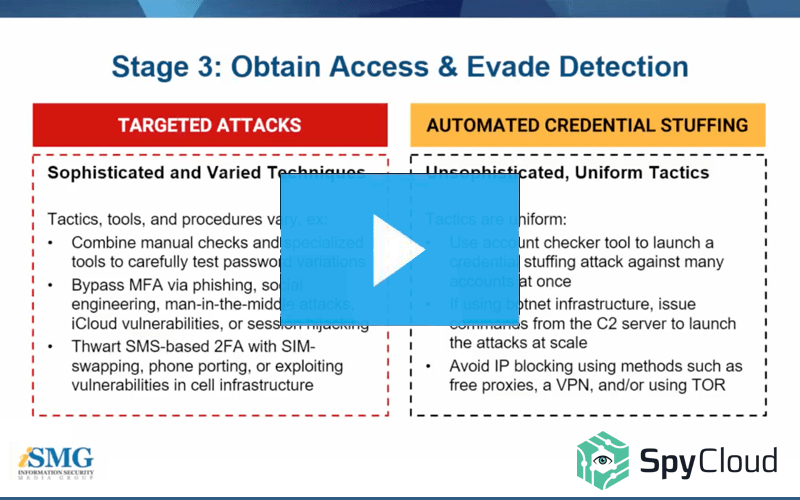
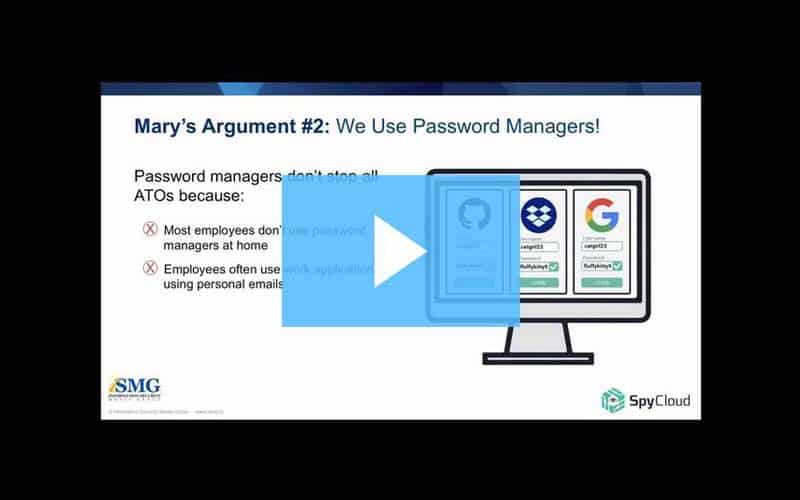
If your account takeover prevention program primarily focuses on automated credential stuffing attacks, you may be leaving your organization exposed to serious losses. Learn more in this webinar we hosted with ISMG.
Protecting your enterprise from breaches and account takeovers has never been a bigger challenge.
Infographics
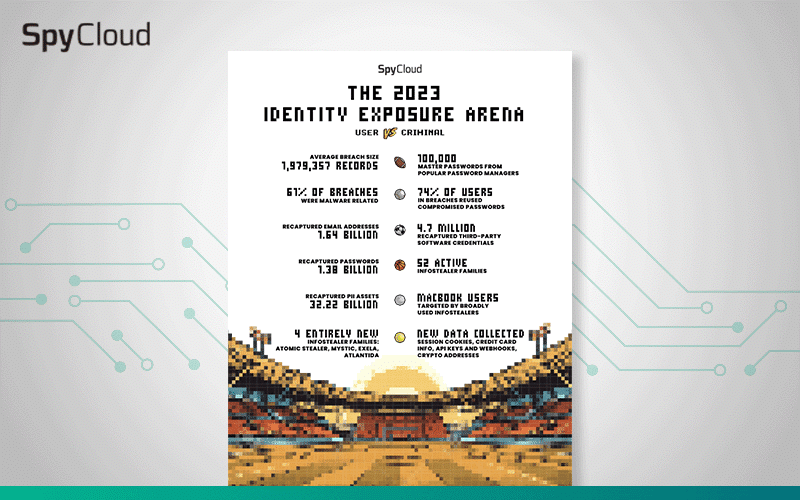
A summary of the stolen data SpyCloud recaptured from the criminal underground in 2023.
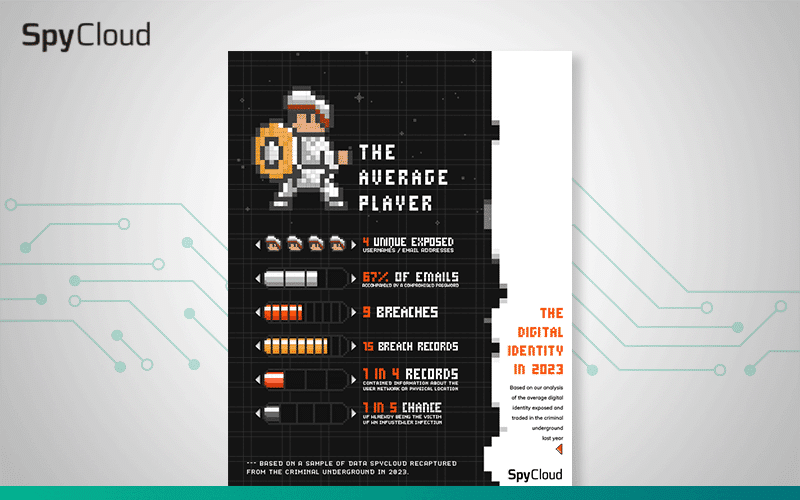
An analysis of the average digital identity exposed and traded in the criminal underground.
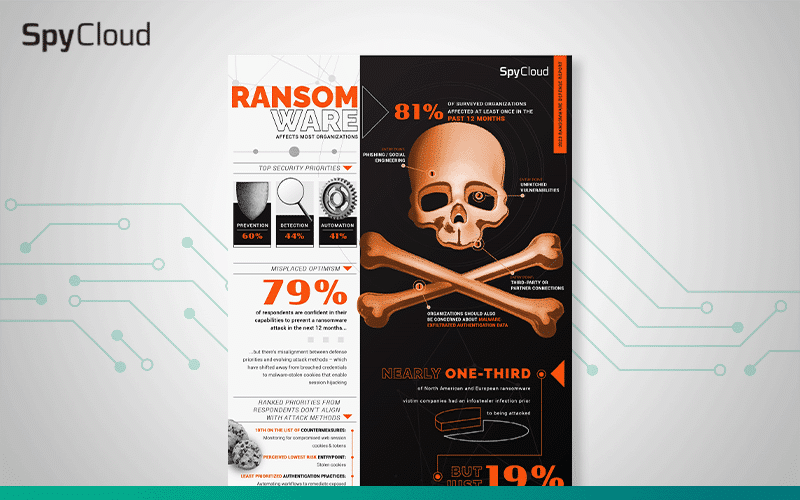
Recent ransomware trends, including insights into ransomware precursors and countermeasures.
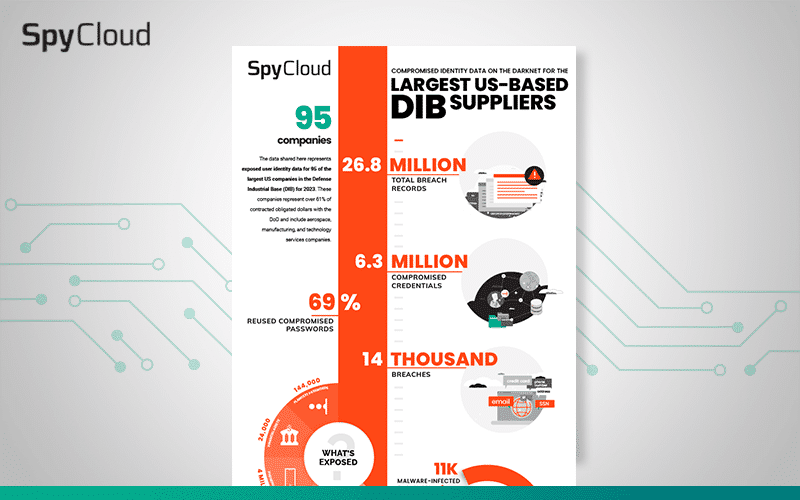
A summary of top DIB contractor darknet exposures that put federal government entities at risk.
See the stolen data trends that are putting government entities at high risk of cyber threats and attacks.
How malware can lead to a ransomware attack in just 6 short steps.
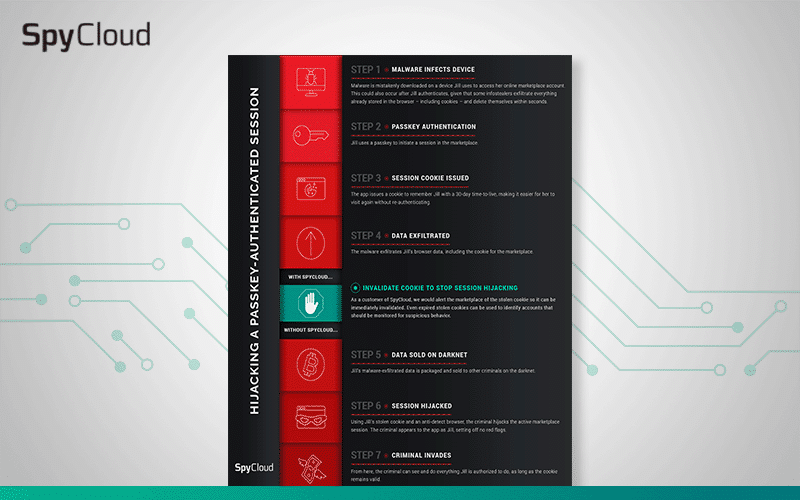
The 7 steps of a successful session hijacking attack.