Telecommunications Industry Credential Exposure
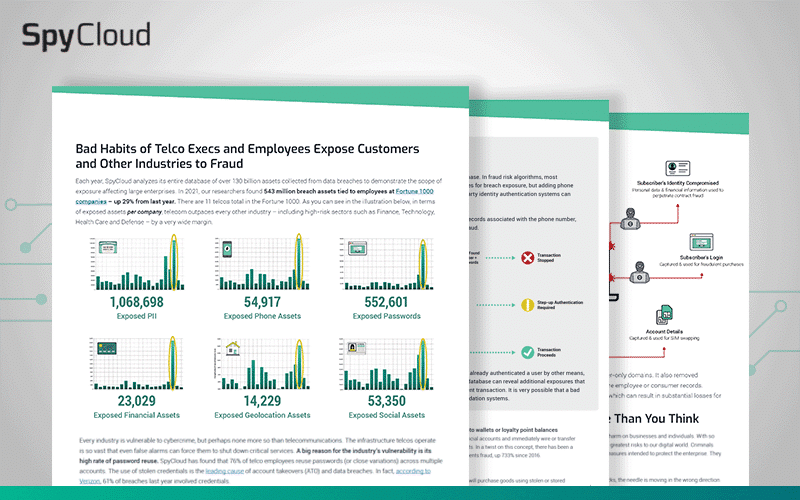
Every industry is vulnerable to cybercrime, but perhaps none more so than telecommunications. Telcos are responsible for securing a huge number of mobile subscribers’ accounts as well as their personal data, and yet 76% of their employees are reusing passwords across multiple accounts.
Once a cybercriminal knows the password for one account, they will test it on other accounts, and if the account owner has reused the password, the criminal has easy access. That makes it extremely important for telco security teams to identify vulnerable accounts early so they can lock them down, force password changes, and remediate malware infections before they can be compromised.
Examining the unique security challenges of this vital sector, this SpyCloud report provides guidance for shoring up defenses and preventing bad employee habits from leading to further damage:
- Learn why the bad habits of telco employees expose customers to fraud
- See why subscriber malware infections are a telco’s problem
- Understand why stolen phone numbers have become increasingly valuable to cybercriminals
- Discover how simple preventative measures can limit the effects of employee & subscriber data exposure
Solution:
Account Takeover Prevention
Trusted by market leaders
With 500+ customers around the world, including half of the Fortune 10, SpyCloud is the leader in operationalizing Cybercrime Analytics to protect businesses.
We’re on a mission to make the internet a safer place by disrupting the criminal underground. Together with our customers, we aim to stop criminals from profiting off stolen data.
#1 Global
Streaming Service
#1 Global
Airline
#1 Global Software
Company
Leading
US Banks
#1 Global
Online Retailer
#1 US Crypto Exchange
Check Your Exposure
See your real-time account takeover exposure details powered by SpyCloud data.
