Whitepapers

Inside the Criminal Mindset: Sidestepping Authentication in a Passwordless World
Examining the state of password security today and the challenges facing passwordless solutions, this SpyCloud report offers clear guidance on protecting your user accounts without having to reinvent the wheel.
Cybercrime Analytics
Learn about the new way to disrupt cybercrime with automated analytics that drive action. Discover why market leaders across all industries are choosing Cybercrime Analytics over threat intelligence, how this approach boosts anti-fraud solutions, and its use cases and benefits in detail.

Reducing Identity Fraud in Ecommerce
How can merchants best balance the customer experience and fraud prevention? Our report offers a new approach for merchants to differentiate between low- and high-risk customers.

Reducing Identity Fraud While Improving the Digital Customer Experience in Financial Services
FIs must strike a balance between prevention controls and fraud mitigation while ensuring a quality customer experience. Our report delves into a new framework for understanding the risk that each individual consumer presents at key points in their journey.
Identity Theft 101
SpyCloud and the Communications Fraud Control Association (CFCA) created this consumer education document to help you understand what identity theft is & how to prevent it.

Business Email Compromise 101
As stolen credentials have become more accessible on the dark web, so has the ability to compromise legitimate business email accounts to commit fraud.
MFA Bypass 101
Understand how hackers combine attack methods and stolen credentials to sidestep multi-factor authentication.

Credential Stuffing 101
We tap our expertise in helping organizations recover exposed credentials to help you understand the anatomy of credential stuffing attacks, why they persist, and what you can do to prevent them.
Understanding the SolarWinds Supply Chain Attack
The SolarWinds supply chain compromise will have repercussions for years to come. Using witness testimony from the February 23, 2021 Senate Select Committee on Intelligence hearing, we broke down the timeline of the attack and examined how SpyCloud could have helped at each stage.
Account Takeover 101
You can’t stop ATO until you understand it. Get this plain-English primer on the latest attack methods, bad habits that increase ATO risk, and strategies for prevention.
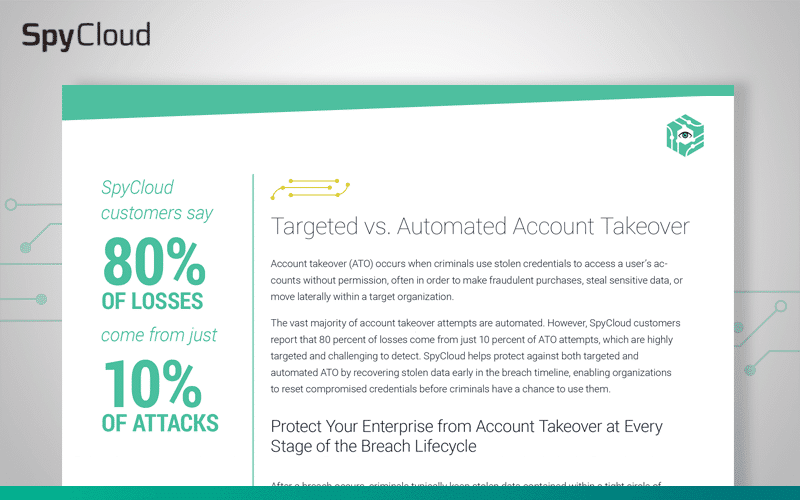
Targeted vs. Automated Account Takeover Attacks
Account takeover can be highly-targeted, sophisticated, and manual, or it can be high-volume and automated. Learn how to protect your enterprise from both types of ATO.
