WEBINAR
I Put a Keylogger On You, and Now You're Mine
What Cybercriminals See When They Infect a Host with Malware
Emotions about the global pandemic are running high, and attackers are taking advantage. Researchers have observed criminals spreading malware by impersonating official sources, distributing malicious COVID-19 maps and trackers, and malvertising on coronavirus-related news stories.
As security professionals, we try to protect our users from this type of activity by searching for indicators of compromise and writing rules to detect malicious activity. What we don’t see is the criminal perspective – what an attacker actually sees when they infect a host with malware that has keylogging and remote access capabilities.
In this webinar, SpyCloud Head of Product Strategy Chip Witt opens a window into the criminal ecosystem surrounding credential-stealing malware like Azorult, Raccoon, Predator, and Vidar. Chip shares examples of actual malware logs, explains how various actors profit from stolen data, and discusses what you can do to better protect your enterprise from these types of threats.
View this on-demand webinar to learn:
- How criminals distribute credential-stealing malware to victims, monetize stolen information, and continue to profit from infected hosts
- What an attacker managing a malware campaign sees as new systems become infected
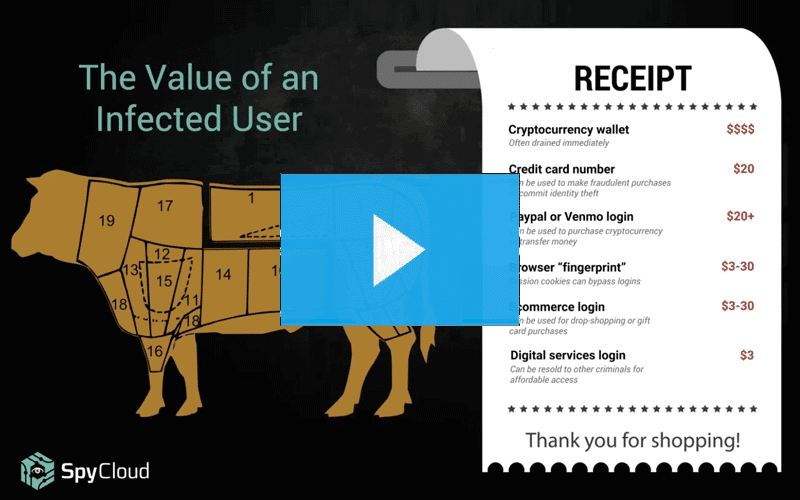
- What’s included within malware log files, from cryptocurrency wallet details to photos of victims’ desktops
- How you can better equip your security organization to handle these threats
Watch the Webinar:
I Put a Keylogger on You, and Now You’re Mine

Presenter Info
Chip Witt, VP, Product Management
Chip Witt has nearly twenty years of diverse technology experience, including product management and operations leadership roles at Hewlett Packard Enterprise, Webroot, VMware, Alcatel, and Appthority. He is currently the VP of Product Management at SpyCloud, which provides cloud-based security services to help businesses of all sizes prevent data breaches and account takeover attacks by alerting when employee or company assets have been compromised. Chip works closely with field intelligence teams specializing in OSINT and HUMINT tradecraft, actor attribution and underground monitoring.
Related Resources

Global Fintech Company
With SpyCloud, this global fintech platform has been able to automate consumer account takeover prevention at scale, protect thousands of users infected with credential-stealing botnets, and enrich their predictive models and investigations.

CISO’s Guide to Surviving a Data Breach
Get advice from CISOs who have been through worst-case scenarios: breaches that exposed customer data. Their experience will help you better prepare your own breach prevention and response plans.

Infected User Response Guide
Handy guide to decipher what it means when employee or consumer information appears on a botnet log, and how to contact infected users with an action plan.
Trusted by market leaders
With 500+ customers around the world, including more than half of the Fortune 10, SpyCloud is the leader in operationalizing Cybercrime Analytics to protect businesses.
We’re on a mission to make the internet a safer place by disrupting the criminal underground. Together with our customers, we aim to stop criminals from profiting off stolen data.
#1 Global
Streaming Service
#1 Global
Airline
#1 Global Software
Company
Leading
US Banks
#1 Global
Online Retailer
#1 US Crypto Exchange
Check Your Exposure
See your real-time account takeover exposure details powered by SpyCloud data.
