Enterprise Protection
Secure your enterprise from cyberattacks with SpyCloud’s Enterprise Risk Protection – acting on known points of compromise before they can be used by cybercriminals.

TRUSTED BY HUNDREDS OF GLOBAL INDUSTRY LEADERS
Take action with confidence – automated solutions for maximum SOC efficiency
Protect
employee identities
Continuously monitor for compromised credentials from breaches and successful phishes and safeguard employee identities to protect corporate data
Reduce
enterprise risk
Prevent account takeover, ransomware, session hijacking, and other costly, significant cyberattacks
Optimize
SOC efficacy
Proactively detect exposures and automate remediation of malware-infected devices, applications, and users
Comprehensive identity threat protection
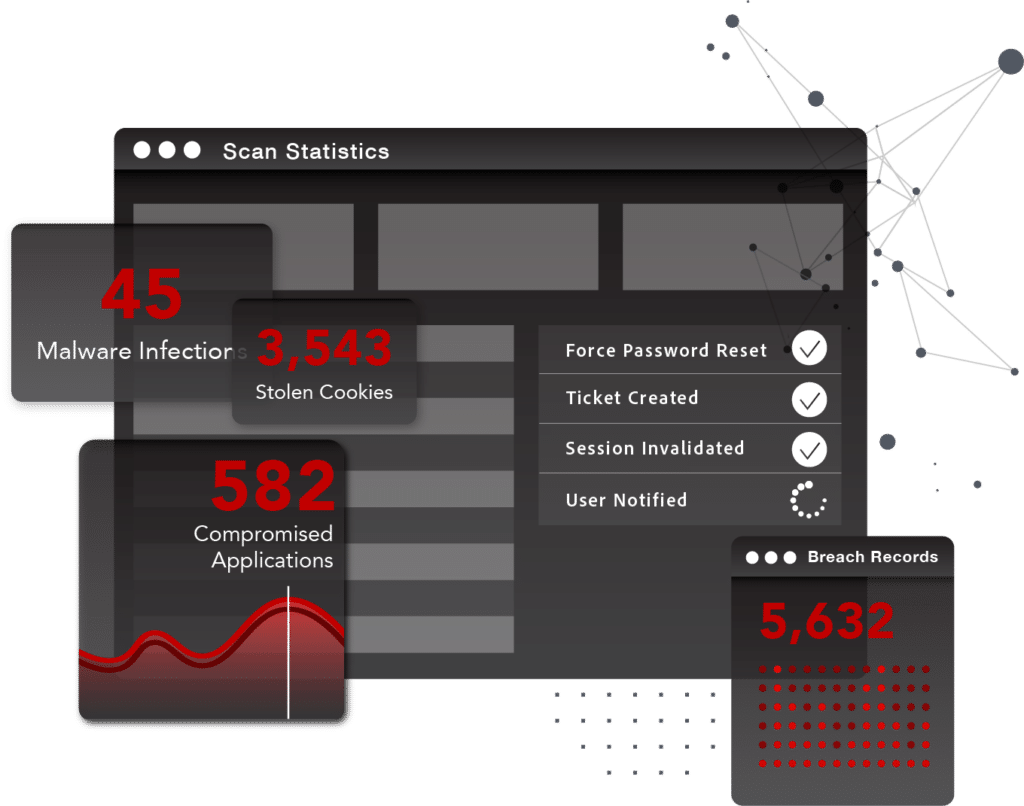
Empower your SOC team
Reduce the amount of resources needed to monitor, identify, and remediate employees’ identities and credentials exposed by malware infections, data breaches, successful phishes and other sources in the criminal underground.
SpyCloud offers an easily extensible solution that scales not only with business needs but with the threat landscape – allowing for maximum interoperability and providing coverage of gaps from legacy tools. With access to continuous, enriched, contextualized underground data, your SOC team benefits from high fidelity alerts that drive action with confidence.
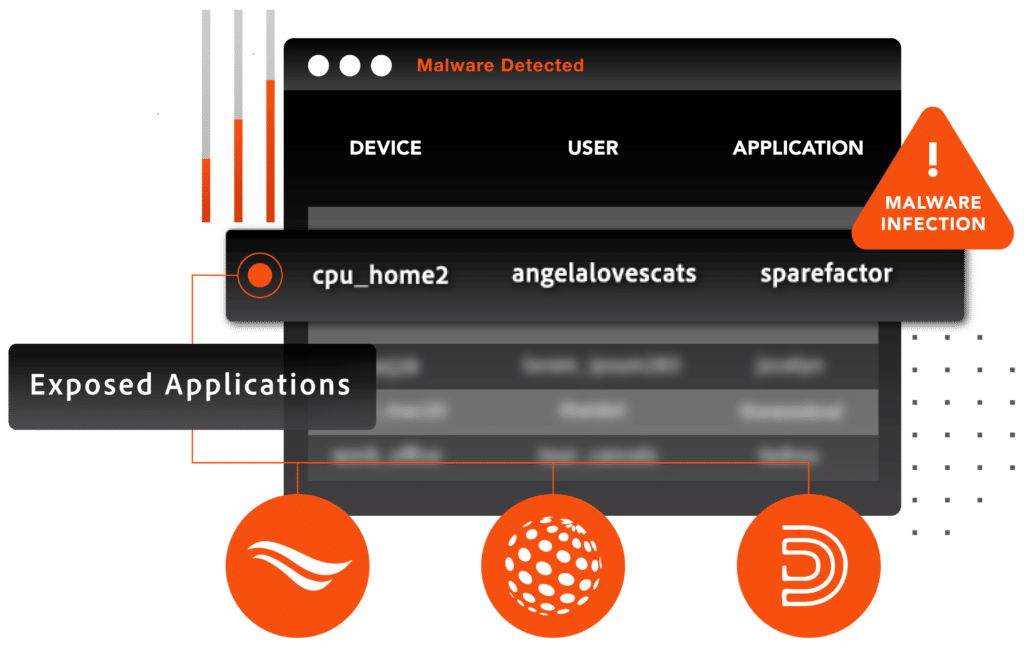
Full coverage visibility to decrease MTTD and MTTR
SpyCloud provides a single source of truth for ransomware prevention and remediation of malware-infected devices, users, and applications. Having the scope of each threat at-a glance decreases both dwell and response times – and coupled with Post-Infection Remediation, security practitioners of all levels can take a proactive approach to mitigate exposures and ensure security efficacy in the SOC, and beyond.
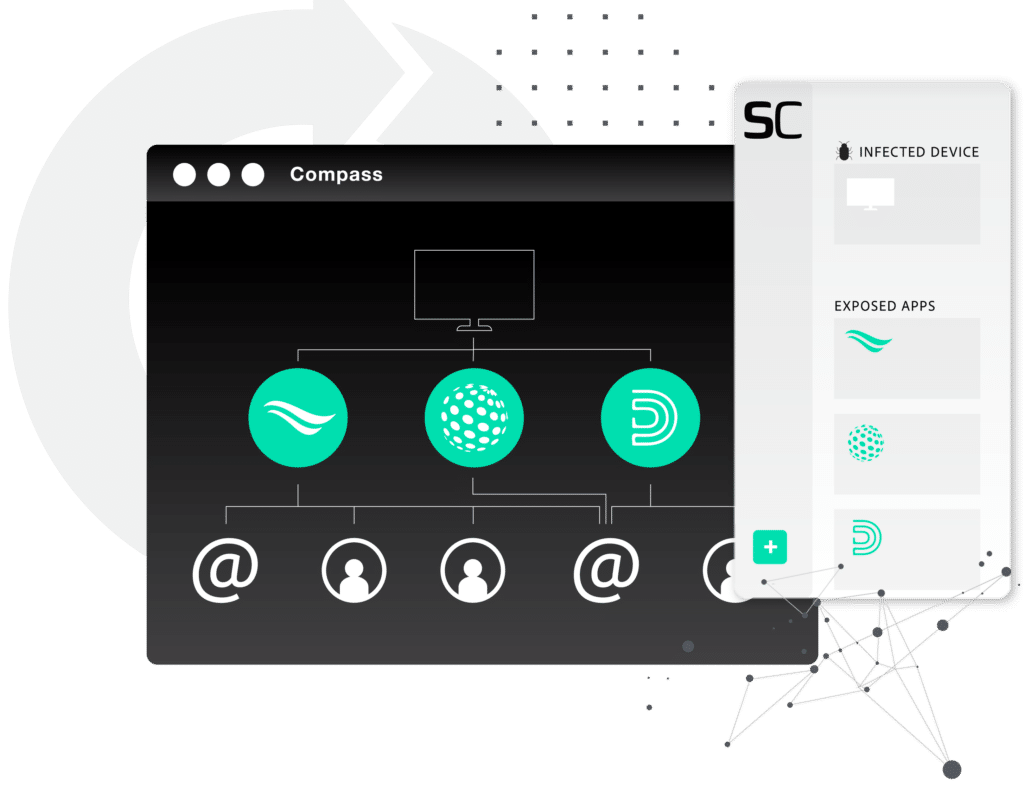
Go beyond the device with an identity-centric approach to protection and prevention
A machine-centric approach is no longer enough to prevent ransomware. An identity-centric approach allows for maximum coverage of risk exposure across all managed and unmanaged devices, corporate applications, and shadow IT.
Access is the new currency for cybercriminals – gain full visibility around efficacy of security policies to continue to strengthen governance. From improving password hygiene and preventing password reuse to enforcing acceptable use policies and deactivating sessions, SpyCloud’s Enterprise Protection offers automated solutions to prevent account takeover and ransomware.
EXPLORE PRODUCTS
SpyCloud identity threat protection solutions put the power back in your hands to prevent cyberattacks.
Enterprise Protection
Detect stolen employee authentication cookies and prevent session hijacking
React to malware-compromised devices, users, and applications
Empowering security teams to act on what matters
Identify threats to your business from compromised credentials, malware-infected employees, and stolen cookies
Actionable malware data and analytics
Identify your employee’s malware-infected devices, managed and unmanaged, and the applications exposed as a result.
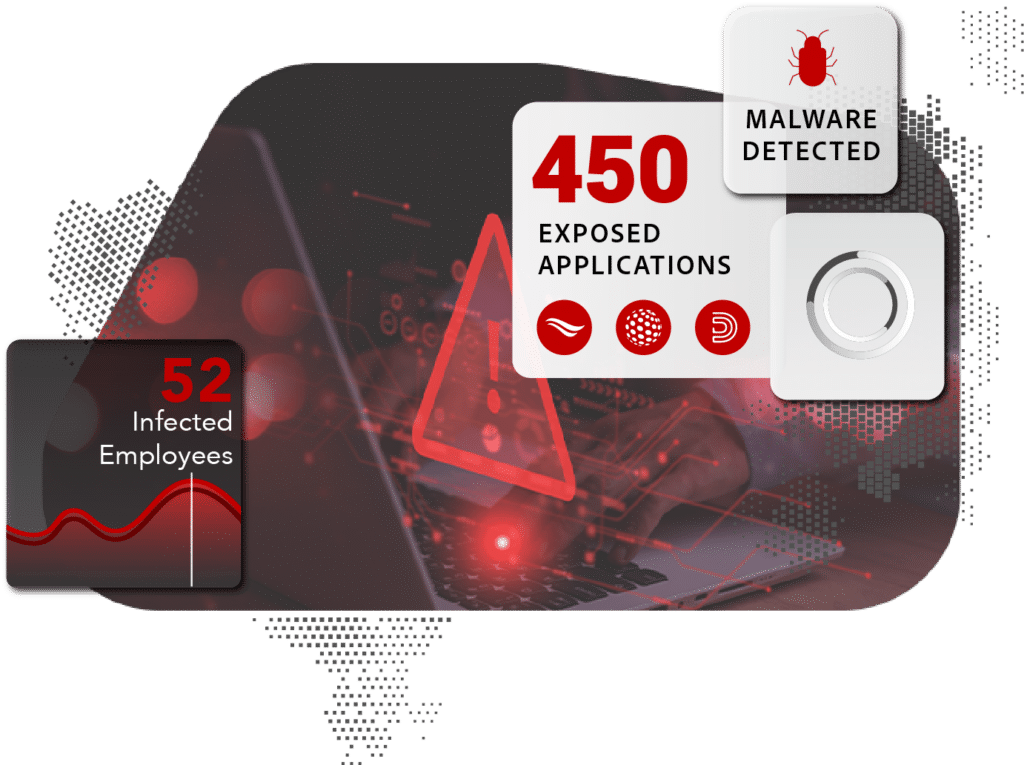
Continuous monitoring of compromised credentials available on the darknet
Monitor multiple domains for exposed employee logins, checking credentials against the largest repository of recaptured data from the criminal underground.
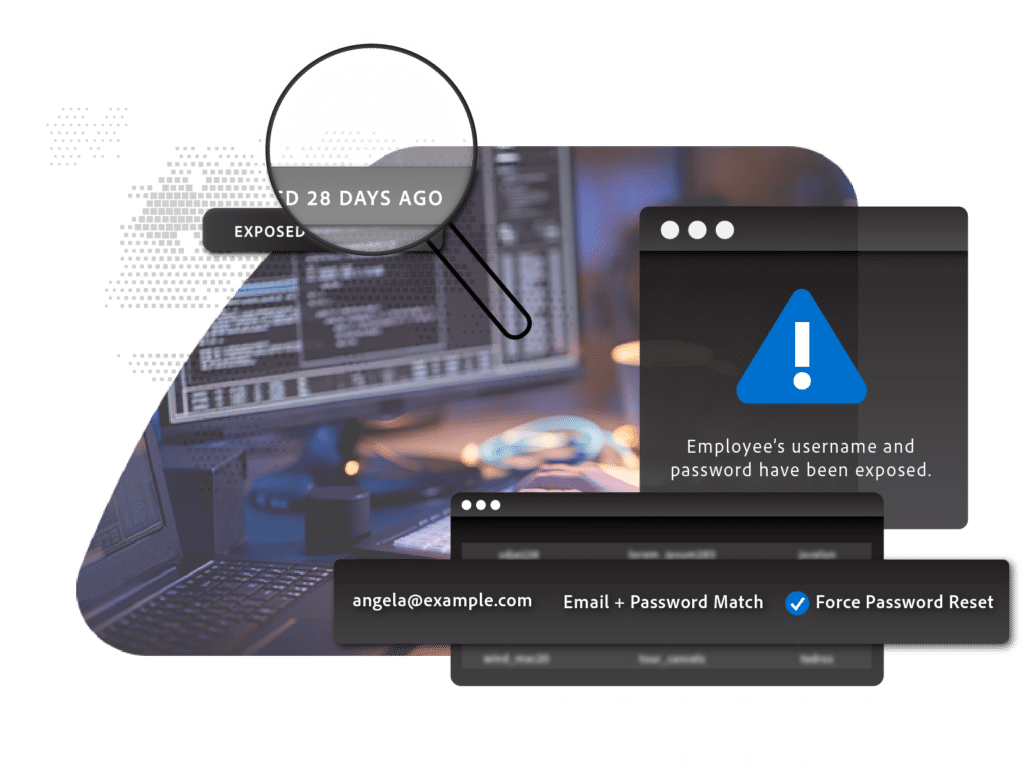
Alerts that you actually want more of
Save time on discovery and manual correlation with rich context for every alert to support prioritization, investigation, and remediation. Eliminate points of friction and empower your analysts to maximize productivity on innovation, automation and other high priority initiatives.
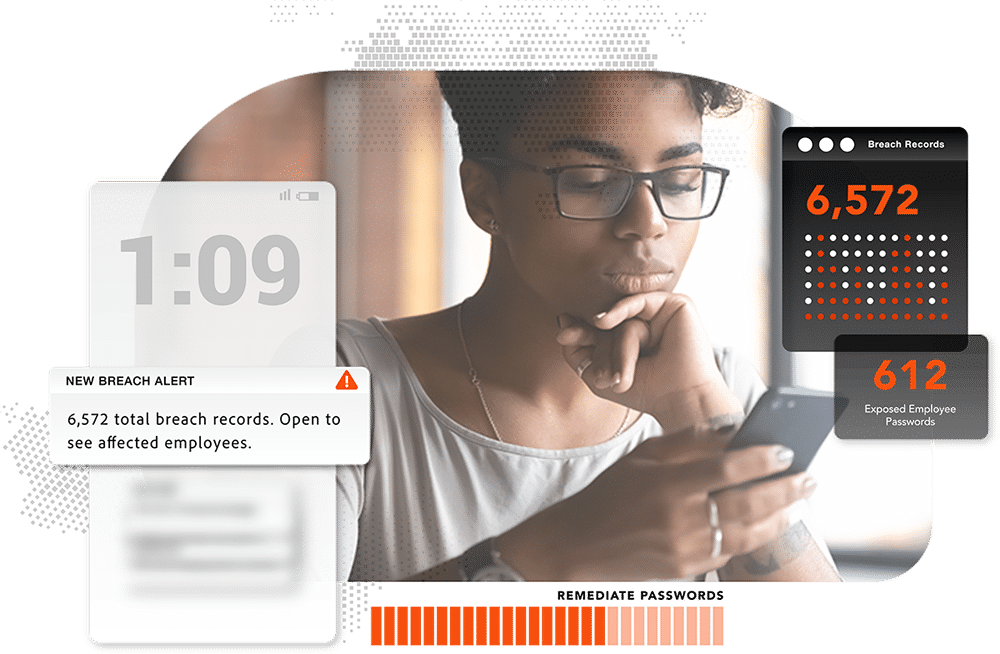
Improve security posture with automated remediation
Post-Infection Remediation covers gaps from both antiquated incident response processes and limited visibility and scope of EDR/EDP tools. With full access to origination and impact of compromised credentials, SOC teams can benefit from setting up effective workflows that tackle tasks that would be otherwise tedious and incomplete when it comes to remediating malware-infected devices, users, and applications.
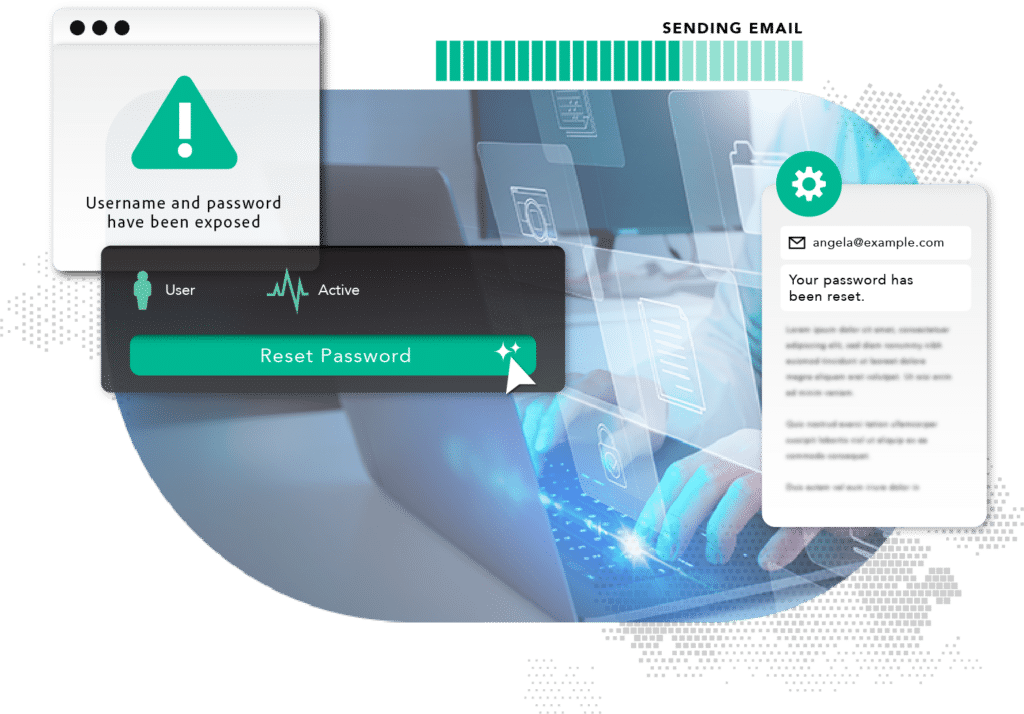
Work smarter, not harder – using the tools you know
Every team operates differently, and use cases are not always one and the same. Leverage your existing tech stack and expand the power of SpyCloud’s Cybercrime Analytics with your preferred SIEM, SOAR, or IAM tool.
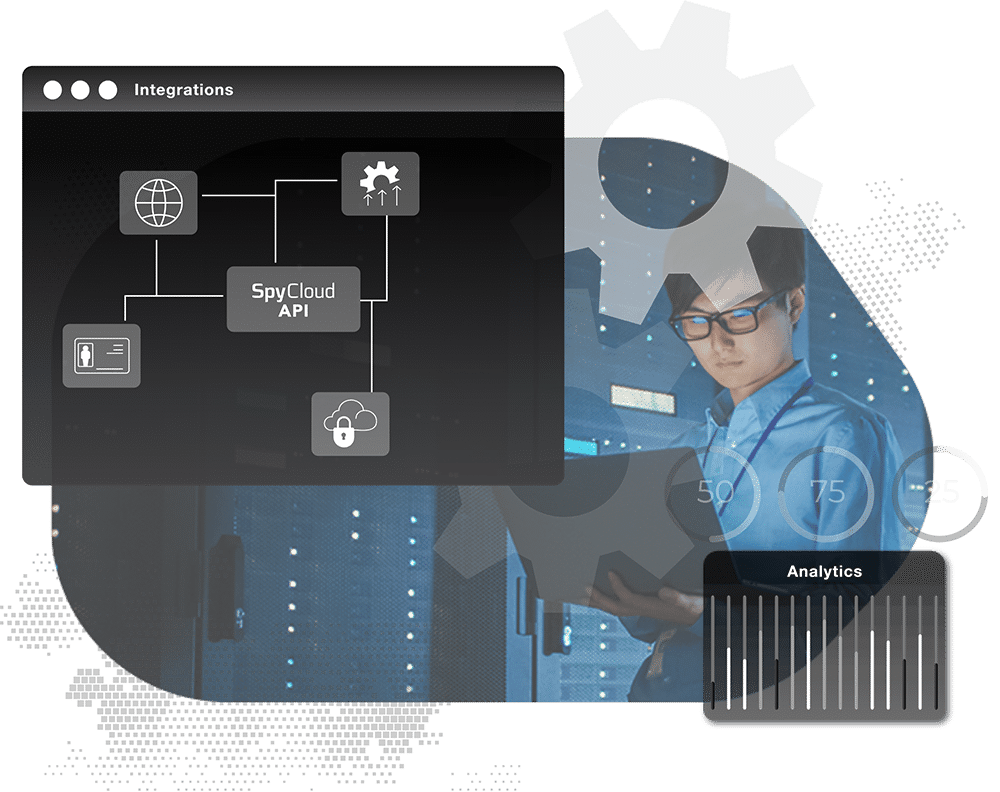
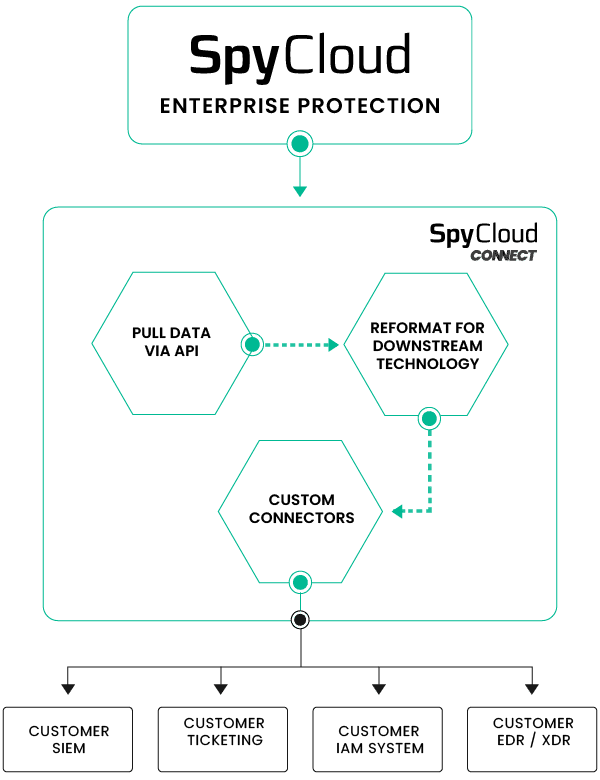
Let SpyCloud build custom automation workflows for your teams
SpyCloud Connect is a hosted custom automation solution that allows SpyCloud products to be seamlessly integrated with a wide variety of security tools and processes – enabling rapid remediation and scalable automation of compromised identities within a customer’s preferred tech stack.
Whatever you want, whenever you want it – SpyCloud Connect builds out the workflows for your desired integrations to send SpyCloud data where and when you need it, all in the tools you are using today without needing to burden your existing resources with custom development work.
ROI CALCULATOR
Trying to imagine your cost savings?
See how SpyCloud can help your business reduce fraud losses, customer churn, and lower operational costs
EXPLORE USE CASES
Use cases for every scenario
Achieving breadth and scale is simple with SpyCloud – with solutions that align to critical business initiatives, delivering outcomes that protect, secure, and prevent.
You might like:

Global Professional Services Firm
A global professional services firm uses SpyCloud Active Directory Guardian to monitor the credentials of over 6,000 employees across all of the company’s global offices, as well as service providers enrolled in their Active Directory.
Post-Infection Remediation Guide
Post-Infection Remediation is SpyCloud’s new, critical addition to malware infection response. This guide goes in-depth on how to stop malware exposures from becoming full-blown ransomware incidents.
Disrupting the Ransomware Market
Malware infections siphon valuable data like fresh credentials and web session cookies, giving bad actors the virtual keys to your enterprise. SpyCloud breaks down malware infections and offers context around the steps criminals take with malware-stolen data, and what can be done to stop this insidious threat.
Annual Ransomware Defense Report
Our annual Ransomware Defense Report covers the costly impacts of ineffective ransomware countermeasures, common entry points for attacks including malware-exfiltrated authentication data, and how organizations plans to improve defenses.






