Digital identities are embedded in our lives, and their expansiveness makes it harder and harder to protect our accounts and business systems from attacks. The body of data stolen by criminals and traded between bad actors has continued to scale dramatically, year over year.
To further complicate an already complex threat landscape, malicious actors are moving beyond the traditional use of stolen username and password pairs to perpetrate crimes against consumers and organizations. In targeted attacks, actors have developed the capability to search for information about their victims across many distinct stolen datasets.
Using expanded datasets, criminals have dramatically increased the scope of their attack patterns, based upon identity records that come from different sources and that can be linked together using PII, like social security numbers or social handles. In this way, users now have to worry about their combined digital identity, which can be formed by cross-referencing all of the information that has been stolen about them from dozens or hundreds of sources.
To make matters even worse, criminals have responded to improved authentication technologies by sidestepping user authentication methods altogether. Bad actors can access stolen session cookies and 2FA secrets to impersonate their victims, making it extremely difficult to differentiate between legitimate users and criminals.
Cybercriminals are clearly cashing in on this opportunity, which is why the global cost of cybercrime is forecasted to nearly triple by 2027, from $8.44 trillion in 2022 to $23.84 trillion.
We see this exponential growth reflected in our repository of data recaptured from the darknet, which totals more than 560 billion stolen assets as of the publishing of this report.
As you’ll see in this report, we’ve observed an increase in next-generation identity attacks that force us to expand our definition of digital identities and the measures we use to protect ourselves.
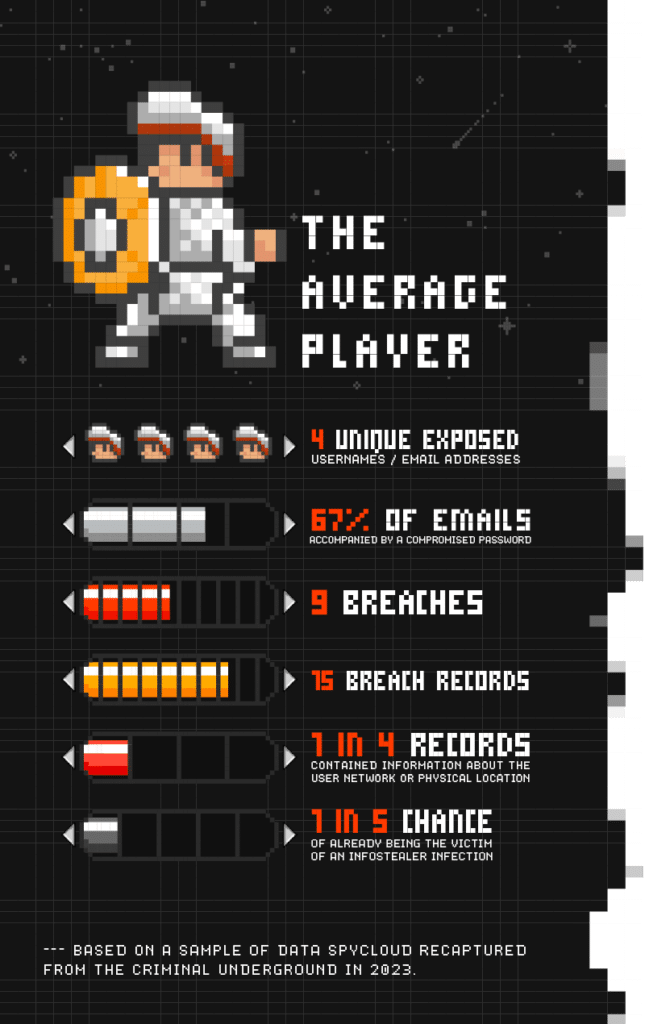
Based on our analysis of the average digital identity exposed and traded in the criminal underground last year:
Threats to digital identities are nothing new. However, the fast pace and stealthy nature of a dynamic criminal underground make it hard for security teams to keep up and proactively defend against new threats.
SpyCloud researchers and data scientists examine the trends related to identity exposure in the criminal underground every year. We keep a tight pulse on darknet activity to understand how stolen data exposes organizations and consumers to cybercrimes like account takeover, session hijacking, fraud, and ransomware.
While we consistently see the number of exposed identities growing, in recent years we’ve also detected a shift in the type of data that malicious actors rely on to compromise identities. In response to this shift, we continue to expand our data sets to explore how emerging and evolving threats put consumers and organizations at further risk.

1
Cloud applications, remote work, mobile device use, and online services have placed digital identities at the heart of our personal and professional lives. Consequently, the digital identity has become a top attack vector – 90% of surveyed organizations reported an identity-related breach in the past year.
Stolen credentials are still a popular tool for criminals to gain initial entry to systems and applications. But digital identities have evolved well beyond the traditional username and password combination, and all signs point to malicious actors exploiting each piece of data they can steal.
SpyCloud’s data shows that the scale of identity exposure today is massive. Our analysis of random email address samples recaptured in 2023 found that for a given person’s digital identity, there is, on average:
With malicious actors gathering and using data across many stolen datasets, this type of information and associated access details and PII provide a slew of opportunities for malicious actors to gain access into an organization or application.
2
The rapid rise of malware, specifically infostealers, is one of the biggest trends we continue to observe. In 2023 alone, infostealer malware use tripled. We saw stealers skyrocket in our recaptured data lake, with as many as 1 in 5 people already the victims of an infostealer infection.
The reasons behind infostealers’ climb to stardom are clear. They are cheap, highly effective in exfiltrating a treasure trove of useful data, and yield a high return on investment. The shift to malware-as-a-service models is an additional boon – and research suggests that 24% of malware distributed as a service is from infostealer families.
SpyCloud’s data illustrates how pervasive and considerable the infostealer threat is. Of the 3,478 breaches we analyzed, 2,115 – 61% of total breaches – were malware-related and included 343.78 million stolen credentials. With valid credentials in hand, cybercriminals have a fast shortcut into employee and customer accounts.
3
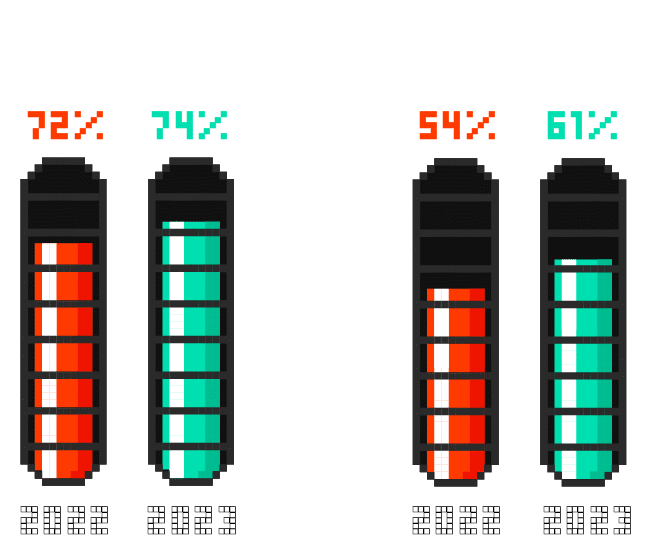
Password reuse rates remain incredibly high among users.
We found a 74% reuse rate for users exposed in two or more breaches in the last year, an uptick from the previous year’s 72%. The all-time historical reuse rate – indicating continued reuse of old, previously-exposed passwords – has climbed as well: from 54% for all years through 2022, to 61% through 2023.
Organizations are spending a lot of effort and resources to change user behavior through security awareness and training, as well as the implementation of password policies. Our research unfortunately shows that those programs are not significantly improving password hygiene.
Every year, it comes as no surprise to see “123456” and its variations at the top of the common passwords list, but commonly used passwords also give us a glimpse into burning topics that dominate pop culture. What preoccupied our collective minds last year?
SpyCloud recaptured a total of nearly 1.38 billion passwords circulating the darknet in 2023, an 81.5% year-over-year increase from 759 million in 2022.

The hottest pop culture trend is fantasy football. As of 2023, an estimated 29.2 million Americans play it, which perhaps explains why football/fantasy football/ffl/NFL showed up over 1.1 million times on our list of most commonly exposed passwords.
Other pop culture topics that wormed their way into hearts and passwords last year included:
halo / master chief / xbox
4
Digital identity exposure may have even bigger implications for the government sector, given that nation-states and other sophisticated actors target critical infrastructure agencies. Yet SpyCloud data shows that government identity exposure has not improved.
To learn how government agencies fared in breaches last year, we analyzed our recaptured data for emails associated with government domains.
723 breaches containing .gov emails in 2023, compared to 695 in 2022 and 611 in 2021.
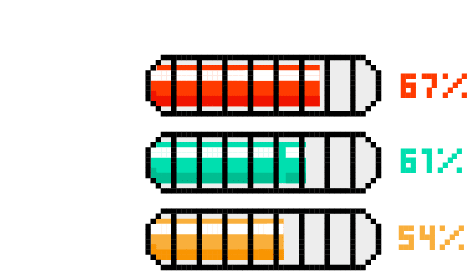
The story got worse when we analyzed password reuse rates among government employees.
We found a 67% reuse rate for .gov users exposed in two or more breaches in the last year, an uptick from the previous year’s 61%. The all-time .gov reuse rate remains high as well at 54% – meaning they aren’t just reusing older passwords but are potentially using exposed passwords from as far back as 2016.
Government employees are just as guilty as their commercial sector peers of using easy-to-guess passwords. The most common passwords associated with .gov emails were:

5
Nearly 70% of surveyed businesses say their fraud losses have risen in recent years. Vast amounts of exposed PII fuel these trends.
SpyCloud recaptured 32.22 billion PII assets in 2023, a nearly 4X jump from 8.6 billion in 2022.
We found nearly 200 types of PII, ranging from everyday details like names and addresses to more concerning types like passport numbers, dates of birth, bank account data, credit cards, and social security numbers.
The categories with some of the largest numbers in 2023 included:
For this year’s report, we doubled down on our efforts to understand the impact of malware, following a notable shift in threat actors’ tactics and the amplified role of underground marketplaces.
Last year alone, we recaptured:
Infostealer logs contain far more than credentials. The breadth of data includes not only everything cybercriminals need to emulate a device fingerprint and take over a digital identity, but also financial information such as credit card information, crypto wallet info, and even device screenshots.
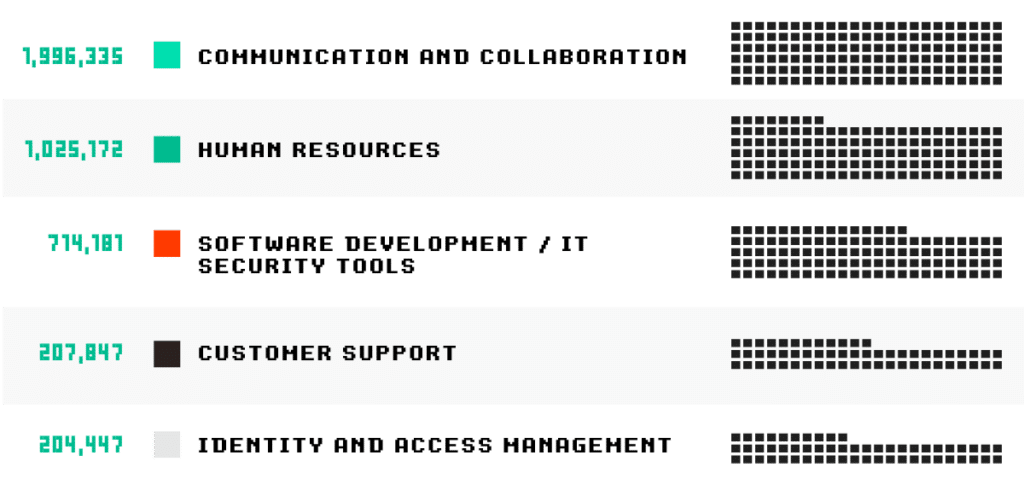
Additionally, SpyCloud recaptured more than 4.7 million third-party application credentials harvested by malware on managed and unmanaged devices, including many popular business tools.
The top five most common categories of third-party tools in our recaptured data included:
The records we recaptured in 2023 were siphoned by 52 infostealer families. Four of these families were new to the scene last year: Atomic Stealer, Mystic, Exela, and Atlantida. Two others, LummaC2 and RisePro, emerged in the second half of 2022 but grew exponentially in 2023. For instance, LummaC2 records in our data lake skyrocketed by more than 2,000% in less than six months.

Our analysis of data exfiltrated by LummaC2 showed that a log from a successful infection was three times as large as from other infostealers, including prominent families like Raccoon and RedLine Stealer.
We recaptured more than 10.58 million mobile records siphoned by malware between August and December of 2023. The implications go far beyond individual device users – and beyond financial losses. While financial fraud is a major motive behind mobile malware attacks, a successful attack can also lead to sensitive data compromise, disruption of operations, and reputational damage. Yet IT and SOC teams have limited or no visibility into mobile devices and struggle to secure them – leaving a massive gap in exposure.
The emerging trends we observed in 2023 had a recurring theme: malicious actors are taking full advantage of the expanding digital identity. Targeted data now ranges from financial information (easily obtainable via mobile malware) to API keys and webhooks.
API keys and webhooks are of particular concern because they enable service provider abuse that unlocks sensitive data. Cybercriminals steal API keys through malware infections and distribute them to other bad actors. Even if an infected device is remediated, the stolen keys can be used for follow-on attacks for as long as they remain active. But SOC teams usually don’t know when this data is stolen and consequently cannot undertake proper post-infection remediation, like rotating exposed keys.
2FA tokens: Organizations have made strides toward hardening their credentials, adding 2FA/MFA as an additional protection layer. So of course malicious actors are adapting and looking for vulnerabilities in these same tools. As noted earlier, newer infostealer families like LummaC2 are already stealing 2FA tokens. Criminals are also adapting to a passwordless future, developing ways to steal passkeys or sidestepping authentication altogether through session hijacking and other forms of next-generation account takeover.
All infostealer-siphoned data is immensely valuable due to its high fidelity, but session cookies and tokens stored in a browser are a true bonanza. With valid stolen authentication cookies in hand, cybercriminals can simply sidestep any authentication mechanism including MFA and hijack a session in an instant.
Last year, SpyCloud recaptured more than 20 billion cookie records, with an average of more than 2,000 records per infected device. This indicates that leveraging malware-siphoned session cookies for next-generation account takeover is quickly becoming a valued tactic. As more organizations adopt passwordless authentication, we expect to see this method escalate.
Plenty of high-profile data breaches make the news every year. But there are thousands of other large breaches that no one hears about – no one outside of a select group of criminals, that is.
These breaches are first shared only in small, private criminal channels for fast, high-return monetization before they’re offered to a broader darknet audience. SpyCloud recaptures this data as quickly as possible; we ingest it into our data lake daily as a “sensitive source” until the breached organization reports it publicly.
Here are some of the data leaks that caught our attention circulating on the darknet last year:
A massive data leak dubbed MOAB (which stands for “the Mother Of All Breaches”) was reported by security researchers in early 2024. The leak included 12 terabytes of data such as credentials from thousands of “meticulously compiled and reindexed leaks, breaches, and privately sold databases” over the years, as well as some new data. An analysis by SpyCloud found that 94% of the data was already in our repository, but approximately 1.6 billion records were new, meaning they were previously either released in sample format only or had not been released publicly.

2023 was a pinnacle year for malware, particularly infostealer malware, as well as other tactics, techniques, and procedures (TTPs) that cast an increasingly broad net to steal identity-related data. With malware logs and robust stolen datasets now abundant commodities, security teams should brace for ongoing and relentless attacks on digital identities. And as cybercriminals innovate, digital identity exposure will surge further.
The corresponding rise in cybercrime, from account takeover and online fraud to session hijacking and ransomware, means we have to start thinking about next-generation approaches if we hope to keep pace – let alone outpace – cybercriminals.
Today, protecting your organization against attacks that stem from exposed identity data means shifting from a device-centric focus to an identity-centric approach. Security teams need quick and accurate evidence when any component of an employee, contractor, vendor, or customer’s identity is compromised. With early access to recaptured darknet data, teams can negate the value of stolen information by quickly identifying their riskiest users and acting quickly to protect them.
SpyCloud recaptures data at a breakneck pace to power automated prevention solutions that transfer the power back to organizations. Lower your exposure risk and protect your employee and customer digital identities with the power of SpyCloud.
Learn more about how SpyCloud solutions level the playing field against cybercriminals and check your company’s exposure.
2130 S Congress Ave
Austin, Texas 78704
Call: 1-800-513-2502
©2024 SpyCloud, Inc. All Rights Reserved
Check Your Exposure has been expanded with more recaptured data. See Your Results Now
Thank you for submitting the form