Reduce risk with Employee Account Takeover Prevention
SpyCloud Employee Account Takeover (ATO) Prevention enables enterprises to stay ahead of account takeover and targeted attacks like ransomware by detecting and resetting compromised passwords early, before criminals have a chance to use them.
Take control of your corporate breach exposure
SpyCloud operationalizes the world’s largest repository of recaptured breach and malware data to help you detect exposed credentials and automate password resets – delivering a proactive ATO prevention solution for enterprises of all sizes.
Control attack surface
Control your human attack surface – A chemical company identified 2,000 exposed employee records across 65 third-party breaches when they deployed SpyCloud.
Reduce risk
Reduce entry points to your corporate assets – A major airline saw a 90 percent reduction in account takeover cases for internal employees by detecting and resetting compromised passwords with SpyCloud.
Shorten response times
Shorten response times with automation – Oklahoma University secured 1,000 compromised passwords within a single day after integrating SpyCloud into their SOAR platform.
Navigate poor password hygiene & eliminate risk of data loss from account takeover
SpyCloud Employee Account Takeover Prevention enables enterprises to monitor multiple domains for exposed employee logins and PII, checking each set of credentials against the largest repository of recaptured darknet data assets in the world to identify and reset compromised accounts.
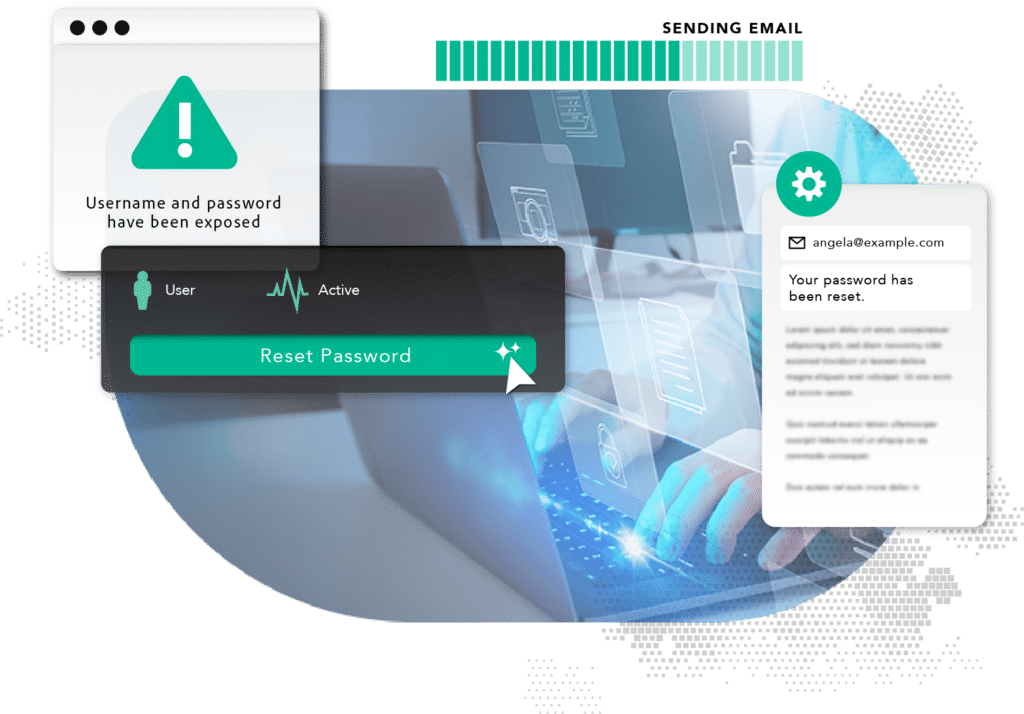
Detect & remediate compromised employee passwords
The use of stolen credentials remains the #1 way criminals gain access to corporate networks and the sensitive information within. Employee accounts provide compelling access to corporate networks and systems, making them attractive targets for criminals.
SpyCloud Employee Account Takeover Prevention helps enterprises safeguard corporate data, funds, and intellectual property by locking criminals out of corporate accounts. SpyCloud checks employee credentials against billions of recovered breach records in the SpyCloud database and alerts security teams to vulnerable accounts so they can take swift action to remediate them.
See how a large US university finds exposures 10x faster with SpyCloud.
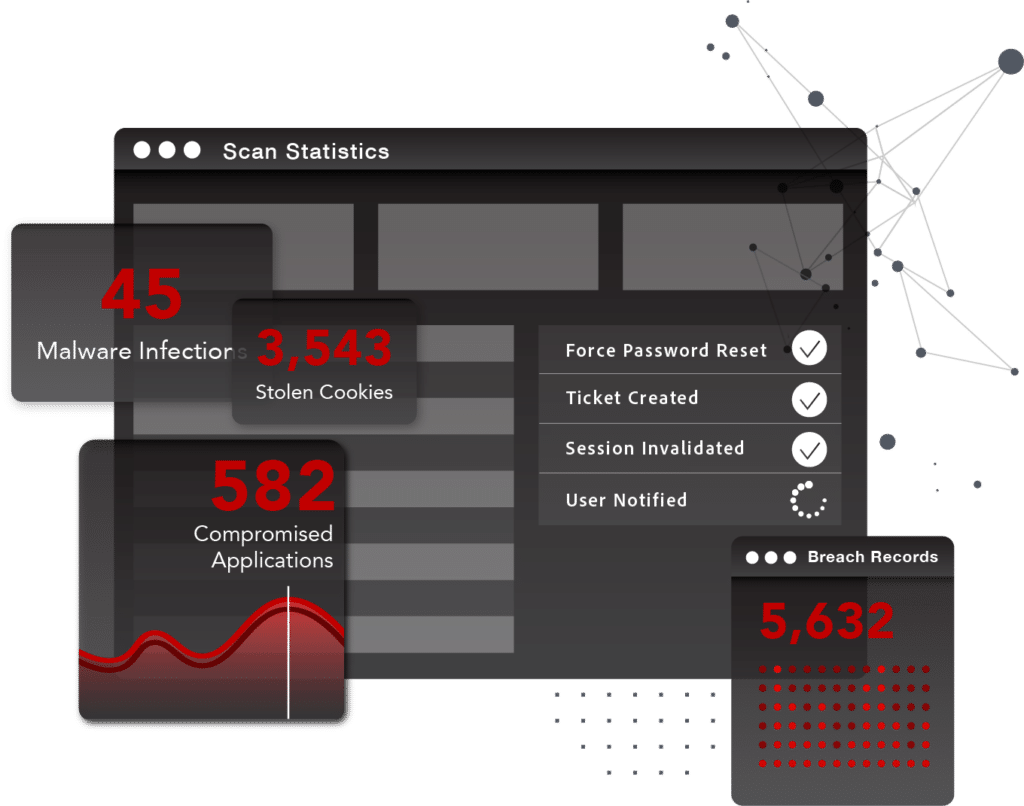
Full coverage visibility to decrease MTTD & MTTR
After a breach takes place, attackers typically keep stolen data contained within a small group of trusted associates while they monetize it, often before the breached organization realizes there’s been an incident. By the time the data leaks to the deep and dark web and the public becomes aware of the breach, stolen credentials have typically already been exposed for 18 to 24 months.
SpyCloud Employee Account Takeover Prevention helps enterprises stay ahead of criminals by recovering exposed credentials early in the breach timeline before targeted account takeover attacks typically begin. SpyCloud security researchers infiltrate criminal communities to recapture data well before it becomes public, helping enterprises take early action to protect vulnerable employees and reduce entry points to the organization.
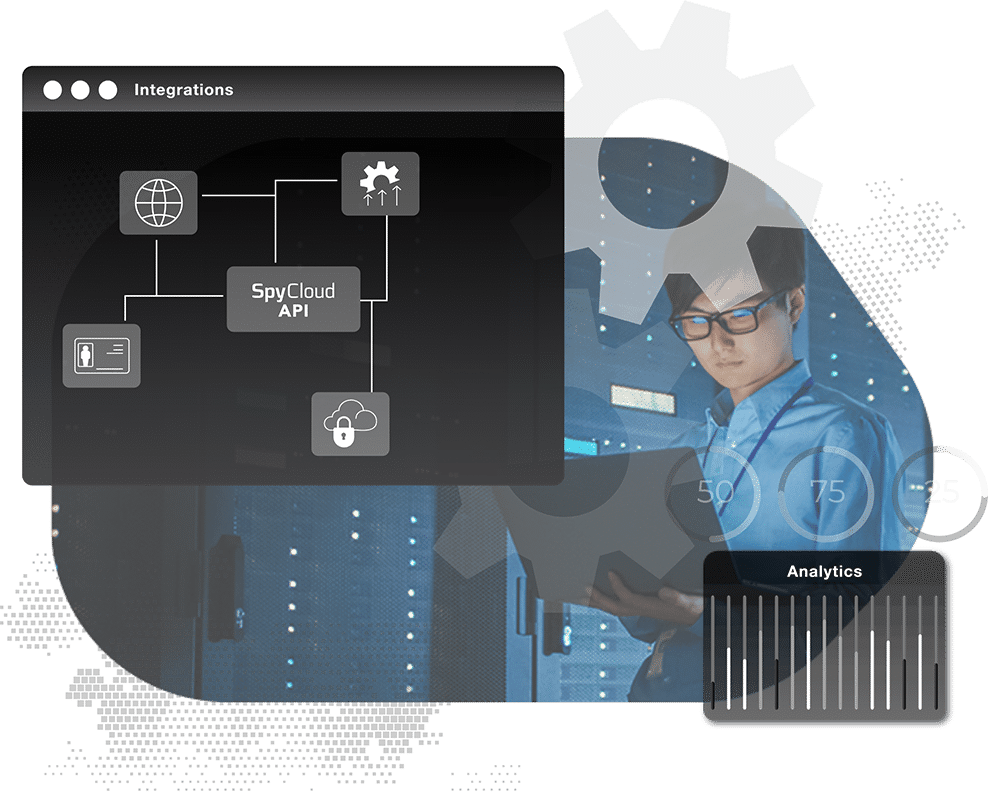
Workflows for employee account takeover prevention
The SpyCloud API makes it possible for security teams to feed SpyCloud data into existing workflows and applications to help prevent employee account takeover in SIEMs and other internal detection tools. Using the SpyCloud API, enterprises can automate password resets and make sure the right teams are armed to remediate vulnerable accounts effectively.
Get more with SpyCloud Employee ATO Prevention
Compromised credential monitoring
SpyCloud monitors your domains, IPs, and emails, checking for exposures against the largest repository of recaptured darknet data
Executive reporting
High-level report exposures and avoided ATOs can be shared with executive leaders – available in the portal or as a monthly email
Data export
Stop password reuse
Prevent employees from choosing passwords exposed in the criminal underground
Granular attribution
Seamless context and correlation of compromised data sources to decrease dwell time and enable rapid response
Real-time alerts
Receive alerts when a new exposure is detected for any of the items in your watchlist
Out-of-the-box integrations
Integrate SpyCloud alerts with your SIEM, SOAR, IdP, or EDR to automate response
APIs
Custom, high-volume APIs with simple configuration to help you integrate our data with your current tech ecosystem
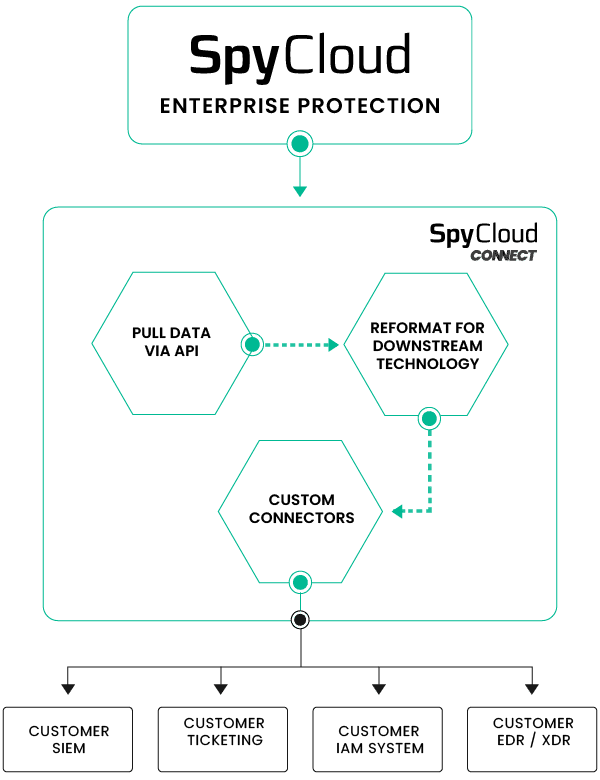
Let SpyCloud build custom automation workflows for your teams
SpyCloud Connect is a hosted custom automation solution that allows SpyCloud products to be seamlessly integrated with a wide variety of security tools and processes – enabling rapid remediation and scalable automation of compromised identities within a customer’s preferred tech stack.
Whatever you want, whenever you want it – SpyCloud Connect builds out the workflows for your desired integrations to send SpyCloud data where and when you need it, all in the tools you are using today without needing to burden your existing resources with custom development work.
SpyCloud Employee Account Takeover Prevention FAQs
In an account takeover (ATO) attack, criminals use another person’s login credentials, most often by leveraging reused or similar passwords from previously breached sites, to gain access to existing accounts. Once inside, they make unauthorized transactions, siphon funds, and steal corporate data or personally identifiable information (PII) to use for other purposes, or simply to sell to other attackers on the dark web.
Criminals are typically taking over accounts for profit, pure and simple. It all comes down to money, and how much of it criminals can extract from what they’ve stolen. Contrary to what you may have heard elsewhere, the first step to monetizing stolen credentials is not to sell them on the dark web. That’s actually the last step. What happens first is the highest effort, most profitable activities. When it comes to exploiting work accounts, criminals may try to locate and steal corporate IP or deploy business email compromise scams, which resulted in $2.7B in losses in 2022 alone.
Easy-to-remember passwords are also easy for bad actors to guess, making consumers vulnerable to password spraying. Password spraying is a brute force attack where a cybercriminal uses a list of usernames and common passwords to try to gain access to a particular site. Once they get a match, they’ll test that same username and password combination against as many accounts as possible.
There are plenty of news stories about admin passwords that contain the company name. It’s actually a huge problem that we’ve come across too many times to count in analyzing the SpyCloud breach database, and something we recommend customers include on their list of banned passwords.
Credential stuffing makes it possible for criminals to profit from even very old breach data that they buy on the dark web and successfully take over multiple accounts. Credential stuffing tools let criminals test credential pairs against a number of websites to see which additional accounts they can take over; hence why password reuse is so dangerous. Some criminal tools can even test for common password variations, like changing certain letters to numbers (Password vs. P@ssw0rd) or adding numbers or symbols to the end of a word (password123). If a password has been exposed in one data breach, any other account with a variation of the same password is at risk.
Infostealer malware is a form of malicious software used by ransomware operators to slip under the radar and steal information from unsuspecting users’ devices – including credentials, auto-fill data, and OS and device info that enables impersonation without setting off any red flags. This type of malware is typically delivered through phishing emails, malicious websites, and other deceptive tactics. Popular types of infostealers we’ve observed on the darknet recently include RedLine, MetaStealer, Raccoon, and Vidar. SpyCloud Employee ATO Prevention detects when corporate credentials are exposed via an infostealer infection or in a third-party breach.
You might like:
2023 Cybersecurity Industry Statistics
Updated stats on the prevalence and cost of common cyberattacks including ATO, ransomware, and fraud for organizations and individuals.

2024 Annual Identity Exposure Report
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.

Malware-Infected User Response Guide
Handy guide to decipher what it means when employee or consumer information appears on a botnet log, and how to contact infected users with an action plan.
Enterprise Protection Buyers Guide
See how SpyCloud illuminates exposures to prevent next-gen threats, powered by unmatched Cybercrime Analytics and paired with top integrations for automated remediation.
Ready to stop account takeover?
Experience the new way to fight cybercrime with SpyCloud Employee ATO Prevention.
