Continuous Zero Trust with SpyCloud
Accelerate Zero Trust initiatives with policy decision points that continuously evaluate employee identities for compromise.
TRUSTED BY HUNDREDS OF GLOBAL INDUSTRY LEADERS
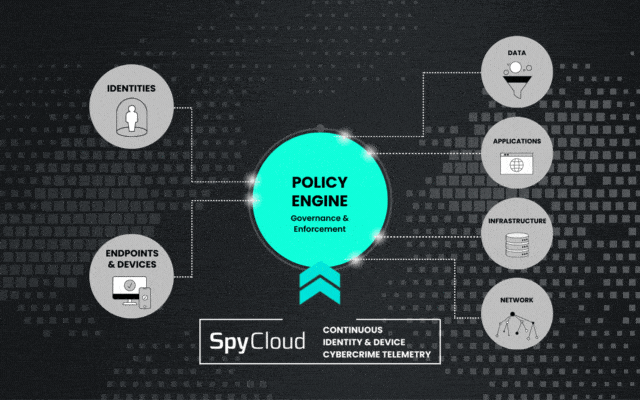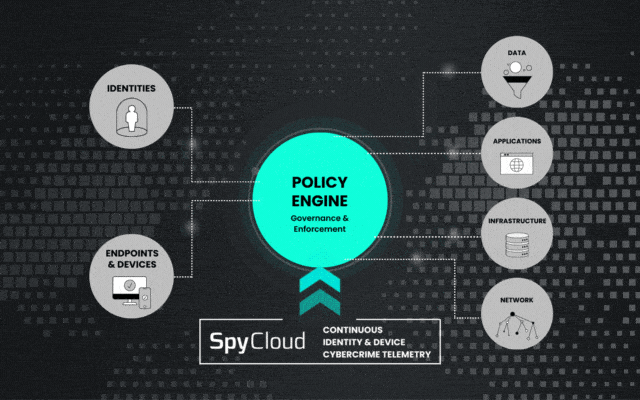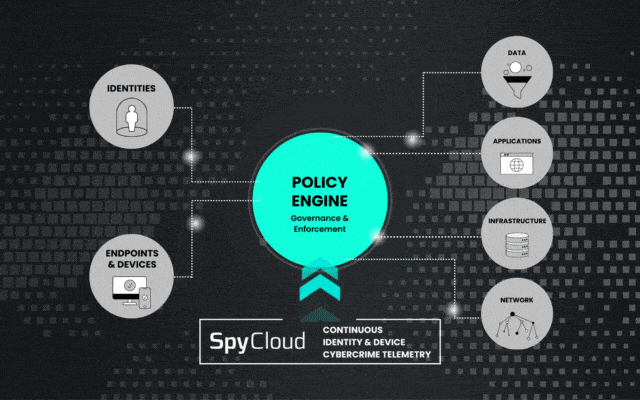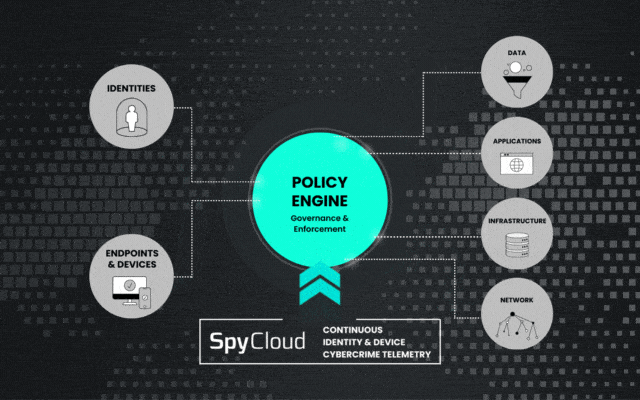
Inform your Zero Trust policy engine with SpyCloud’s advanced cybercrime telemetry
To reach a sufficient Zero Trust implementation, it’s critical to continuously evaluate each user and device. This includes taking into account how your employee identities, devices, and access are perceived by criminals on the darknet. SpyCloud constantly reevaluates and checks employee identity exposures, giving you definitive evidence when an identity is compromised.
Streamline compliance
Augment your policy engine and advance your compliance frameworks with actionable cybercrime telemetry
Optimize resources
Free up critical resources with automated defenses against targeted cyberattacks, reducing the need for additional headcount
Mitigate risk
Automate protection measures against employee identity exposures, significantly lowering the likelihood and impact of costly cyber incidents
The modern Zero Trust challenge
Zero Trust implementations that only test the validity of users and devices when they first access the network leave organizations at significant risk. As organizations shift to a continuous authentication model – one that expands protection against the use of compromised account information and cookies to bypass Zero Trust Architecture Controls – identity exposure monitoring becomes a critical piece of the puzzle. Unfortunately, most organizations’ Zero Trust implementations don’t continuously input high-fidelity darknet telemetry into their policy engine. In those cases, it’s leaving an open door for cybercriminals to sidestep MFA and SSO in session hijacking attacks.
The SpyCloud difference
The most powerful input to your policy engine is the data that criminals have collected from third-party breaches, malware, and phishing attacks about your users and systems. Building a dynamic policy that responds to this expanded digital identity profile is critical for applying the proper level of authorization to each of your users and preventing next-gen identity threats.
Powered by darknet telemetry and combined with automated remediation, continuous identity exposure monitoring from SpyCloud accelerates modern Zero Trust initiatives with always-on authentication.

Streamline regulatory compliance
Continuous Zero Trust with darknet telemetry helps satisfy your compliance requirements. Use actionable and relevant darknet telemetry as a critical component of your risk management frameworks. SpyCloud fits in with:
- 800-207 Zero Trust Architecture - Telemetry to enhance identity governance and trust algorithm
- NIST CSF 2.0 - Darknet intelligence for threats and potential likelihoods
- NIST 800-053 - Continuous monitoring and threat awareness
- NIST 800-063-3 - Digital Identity Guidelines
- CIS Top Controls v8 - Restrict unauthorized access and remediate malware-affected applications

Continuous identity exposure monitoring
Continuously refresh your policy engine inputs with fresh identity exposure data from SpyCloud. You’ll maintain an adaptive security environment, where policy updates are automatically applied as new threats are identified, so your organization’s defense mechanisms evolve in step with the threat landscape.
- Early Detection and Action: Act on recently exposed credentials to shut down entry points and prevent targeted account takeover
- Remove Exposure Bindspots: Expand visibility into malware-infected employees to uncover unauthorized access across business applications, credentials, and stolen session cookies
- Convert Darknet Data to Defense: Respond on actionable insights with prompt action on exact-match compromised passwords and identities, with contextual information into the breach source or malware infection
- Real-Time Policy Updates: Continuously refresh your policy engine with the latest exposure data, ensuring dynamic and effective threat response
Always-on access authentication
Implement always-on access authentication using SpyCloud’s enriched telemetry, including the severity and relevance of every exposure record, so you can modify access based on signs of identity compromise.
- Enhanced Session Visibility: Broaden security oversight beyond devices and applications, focusing on compromised user sessions to safeguard identities at their most vulnerable points
- Prevent Lateral Movement: Block cybercriminals from exploiting trusted devices by remediating the hidden scope of malware infections, including compromised third-party cloud applications
- Secure User Sessions: Defend against criminals exploiting authenticated sessions, bypassing MFA and passkeys to take over employee accounts, and stop targeted attacks where criminals impersonate employees to escalate privileges and access sensitive information
- Get Daily Identity Checks: Automatically scan directory services to identify compromised or weak credentials among active employees, flagging or resetting risky accounts
Automated exposure remediation
Use automated daily scans with your directory service of choice to find compromised data, and automatically reset passwords for active employees and disable high-risk accounts. Or, leverage SpyCloud’s SIEM/SOAR integrations to quickly adjust policies based on compromised credentials from third-party breaches and malware infections.
- Reduce Alert Fatigue: High-fidelity alerts that prioritize investigations to remediate compromised credentials and shorten the attack window
- Decrease Mean-Time-to-Remediation (MTTR): Dynamic data enrichment for unparalleled insights into potential threats for a comprehensive understanding of identity exposures
- Streamline Operational Workflows: SIEM/SOAR integrations take quick action on compromised credentials from third-party breaches and malware infections to adjust policies accordingly
- Optimize Incident Response: Take an identity-centric approach to shut down entry points and invalidate active sessions to reduce risk across all employee devices and applications
SpyCloud offers out-of-the-box API integrations with top technology vendors across SIEM, SOAR, EDR, TIPs and more to power detection, analysis, and remediation via automated workflows.
Why Customers Choose SpyCloud
3.5
MONTHS
AVERAGE PAYBACK PERIOD FOR SPYCLOUD CUSTOMERS
UP TO
60%
LENDINGTREE SAVES 60% OF SOC TEAM’S TIME AND RESOURCES WITH ACTIONABLE DATA & AUTOMATION
You might like:
How Darknet Telemetry Fuels Continuous Zero Trust
Your Zero Trust policy engine is only as good as the data it receives. Find out how to best fuel it to achieve Continuous Zero Trust.

The Missing Ingredient in Your Zero Trust Recipe
Listen to this webinar for how to reduce session hijacking risk & accelerate your Zero Trust initiatives with SpyCloud darknet telemetry.

SpyCloud Annual Identity Exposure Report 2024
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.
Reach Continuous Zero Trust with SpyCloud
Fuel your Zero Trust policy with actionable cybercrime telemetry to constantly evaluate employee identities and prevent next-gen threats.






