Threat actor attribution with enriched identity intelligence
SpyCloud empowers analysts to de-anonymize threat actors using their digital exhaust and tie them to financial crimes, exploitation, and attacks threatening national security.
Curated digital identity data recaptured from the criminal underground delivers valuable perspective into threat actors’ identities, behavior, campaigns, infrastructure, and patterns of life.
TRUSTED BY HUNDREDS OF GLOBAL INDUSTRY LEADERS
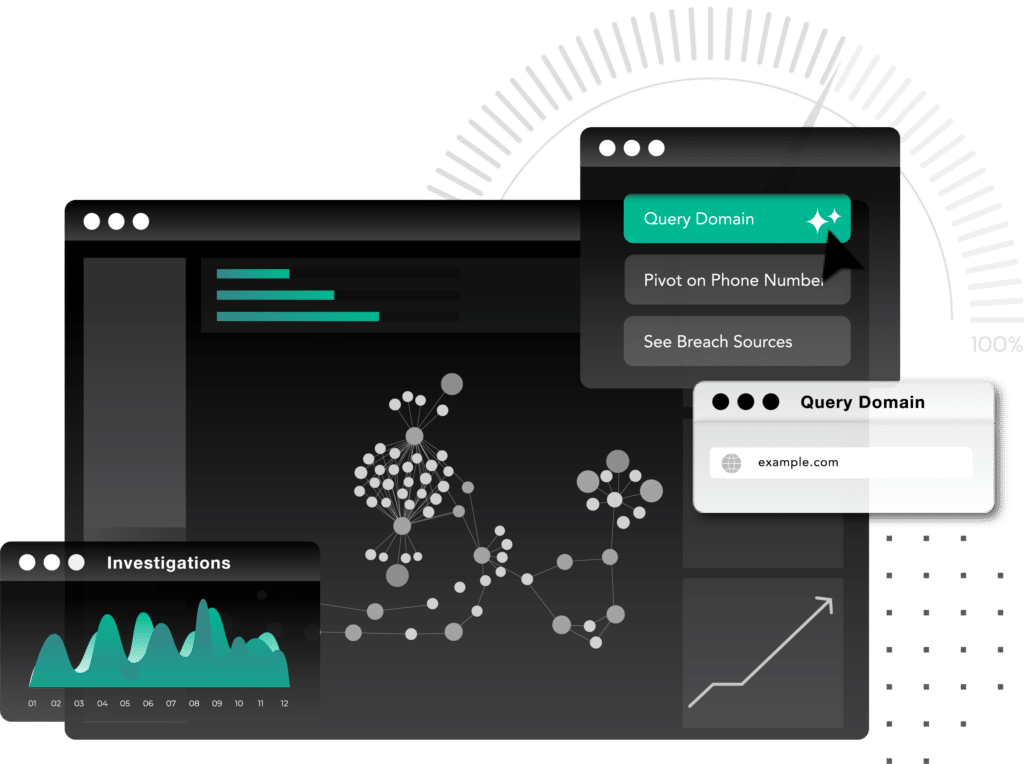
Unmask criminals with recaptured data
Like the rest of us, criminals use online accounts that are subject to data breaches and devices vulnerable to malware. SpyCloud recaptures this data so analysts can piece together decades-worth of criminals’ digital breadcrumbs to reveal the identities of adversaries and provide attribution for malware campaigns, online fraud, and other crimes.
Higher
success rate
Quality data enriches investigations and increases the rate of attribution substantially – one SpyCloud customer reports a 60% attribution success rate increase
Faster
analysis & answers
High fidelity, high efficacy data recaptured from breaches, infected machines, and phish kits illuminates actor identities, starting from a single selector like an email address
Previously-undetectable connections
Deeply investigate cybercriminals and insider threats, even if actors are obfuscating their activities through TOR and VPNs
Stitch together attackers' digital footprints to to reveal real-world identities, alternate aliases – and potentially other crimes
SpyCloud is the ultimate force multiplier for analysts and investigators – delivering automated identity analytics to quickly profile threat actors, verify their identities, and expose their motivations, capabilities and crimes.
Quality data, dynamic searchability
Leverage the world's largest and deepest collection of recaptured data, with 25+ billion assets analyzed and ingested monthly. No other provider offers this scale of high-quality data with a flexible and scalable API for fluid investigations.
Actionable intelligence at scale
Gain access to fresh data as assets are ingested for people and organizations. Maintain a robust investigation lifecycle and connect disparate data sources, including internal data and threat intelligence.
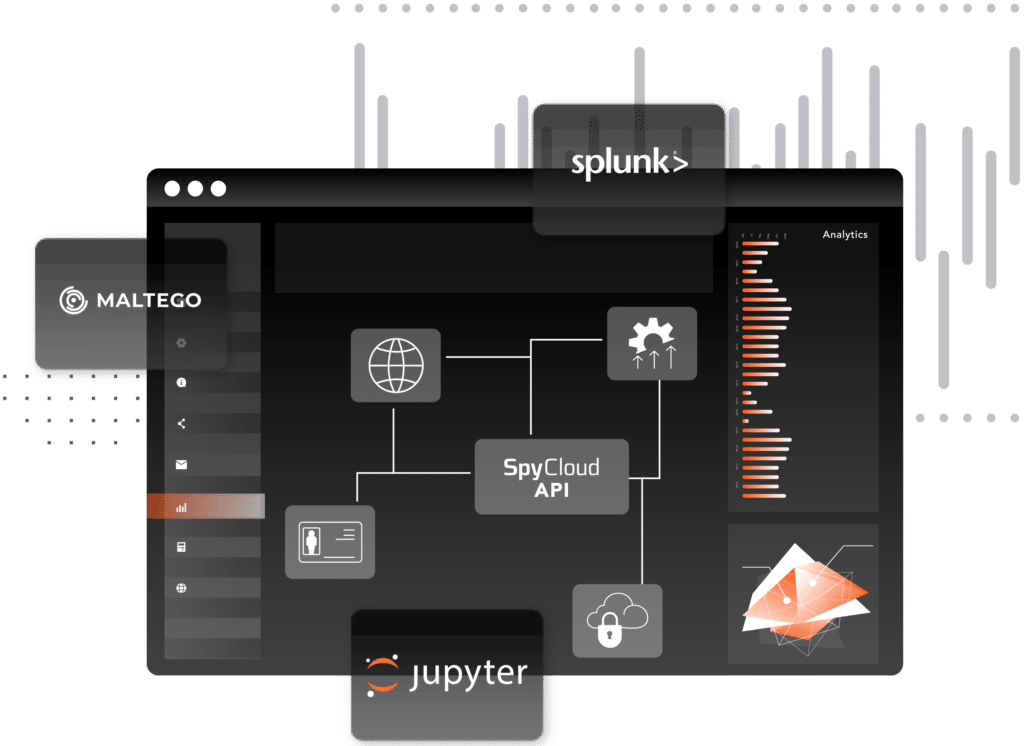
Seamless automation
Optimize workflows and automate repetitive steps with 80+ SpyCloud Transforms for Maltego, and streamline query results with pre-built, web-based Jupyter Notebooks.
Analyst services & training
SpyCloud analysts can train your team on the methodologies for using recaptured digital exhaust for effective pattern-of-life analysis and rapid identification of threat actors.
ANALYSTS TRUST SPYCLOUD TO AID THREAT ACTOR ATTRIBUTION
The world’s largest asset manager uses SpyCloud to investigate threat actors who put their customers at risk of fraud and identity theft.
Explore SpyCloud
Our Data
Enterprise Protection
Reduce your risk of ransomware and other critical attacks – acting on known points of compromise
Learn more
Consumer Risk Protection
Take a proactive approach to combating account takeover and stop high-risk attacks tied to malware
Learn more
Investigations
Efficiently piece together criminals’ digital breadcrumbs to reveal the identities of specific adversaries engaging in cybercrime
Learn more
Data Partnerships
Access comprehensive breach, malware, and phished data to add value to security and fraud detection products and services
Learn more
SecOps
Efficiently secure employee identities and safeguard corporate data and critical IP from cyberattacks.
Learn more
Threat Intel Teams
Investigate and stop threats with insights well beyond raw data and IOCs
Learn more
Check your exposure
Uncover threats to your organization like malware-infected users, stolen session cookies, and recency of breach exposures
See your report
Get a demo
See how the world’s top analysts and investigators use SpyCloud for fast, accurate attribution
Connect with us
Recaptured data + automated identity analytics = the secret weapon for threat actor attribution
See how SpyCloud Investigations make it faster and more efficient to de-anonymize threat actors.
