Protect high-profile executives and VIPs from targeted account takeover
SpyCloud VIP Guardian extends employee account takeover prevention to key executives’ personal accounts for an added layer of protection, without invading their privacy – giving VIPs visibility into their exposed credentials and empowering them to protect their digital identities.
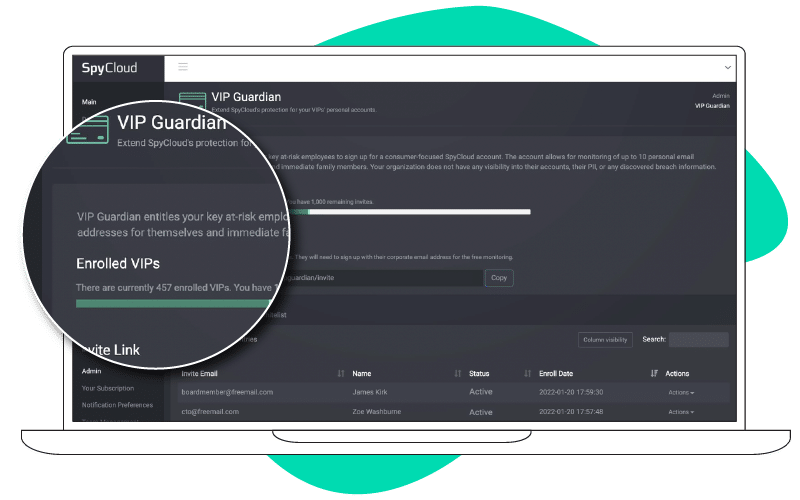
Empower your VIPs to secure their personal accounts from targeted cyber attacks
Executives and high-visibility VIPs are vulnerable to account takeover when using exposed passwords for personal logins not monitored by security teams. SpyCloud VIP Guardian reduces security risks by detecting any time credentials and PII that have been exposed through a data breach or malware infection, improving overall corporate security posture.
Prevent security
breaches
Identify and safeguard against cyberattacks and stop compromised personal credentials from serving as potential entry points
Enhance cybersecurity awareness
Provide visibility of personal security posture for executives and VIPs to drive awareness about the importance of strong password security
Improve password hygiene
Guide VIPs to create and manage strong passwords and eliminate weak or reused passwords across their personal accounts
Secure your executives and VIPs' digital identities
Executives, board members, and developers with high levels of systems access may fail to recognize the serious consequences of password reuse until it impacts them directly. VIP Guardian provides these high-risk employees with visibility of their breach data and malware infections, so you can open their eyes to the importance of strong security practices.
Close security gaps outside corporate control
While your enterprise can monitor corporate credentials for breach exposures and malware infections to keep attackers out of enterprise accounts, executives may reuse exposed passwords across personal accounts that your security team can’t monitor. Any of these accounts could provide a stepping stone into your enterprise resources.
With SpyCloud VIP Guardian, your high-risk employees can monitor their personal and family accounts for compromised credentials that can put their personal data and identities at risk. And securing their vulnerable accounts bolsters your corporate security in ways your security team couldn’t do alone.
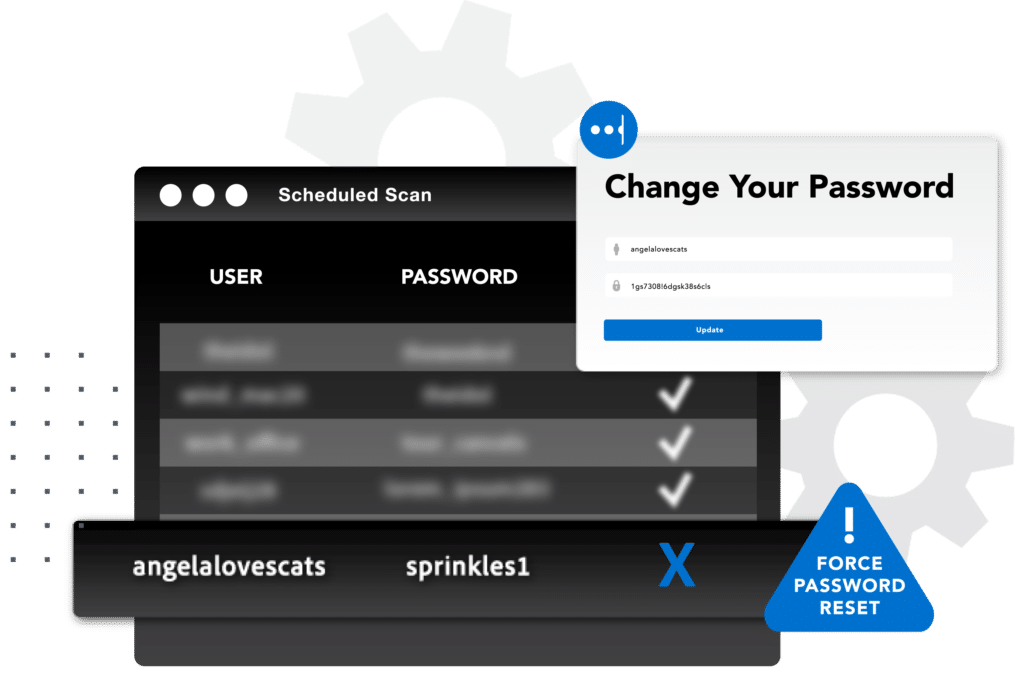
Stay ahead of targeted attacks
In the first 18 to 24 months after a data breach occurs, attackers typically restrict access to stolen data to a select group of associates. While the data is fresh, attackers are likely to use stolen credentials for targeted attacks against high-value victims, which may include your executives.
SpyCloud recovers stolen data as soon as possible after a breach occurs to help enterprises stay ahead of targeted attacks. With SpyCloud VIP Guardian, your executives will find out quickly if any of their personal information or passwords have been exposed in a new breach, giving them time to protect their vulnerable accounts.
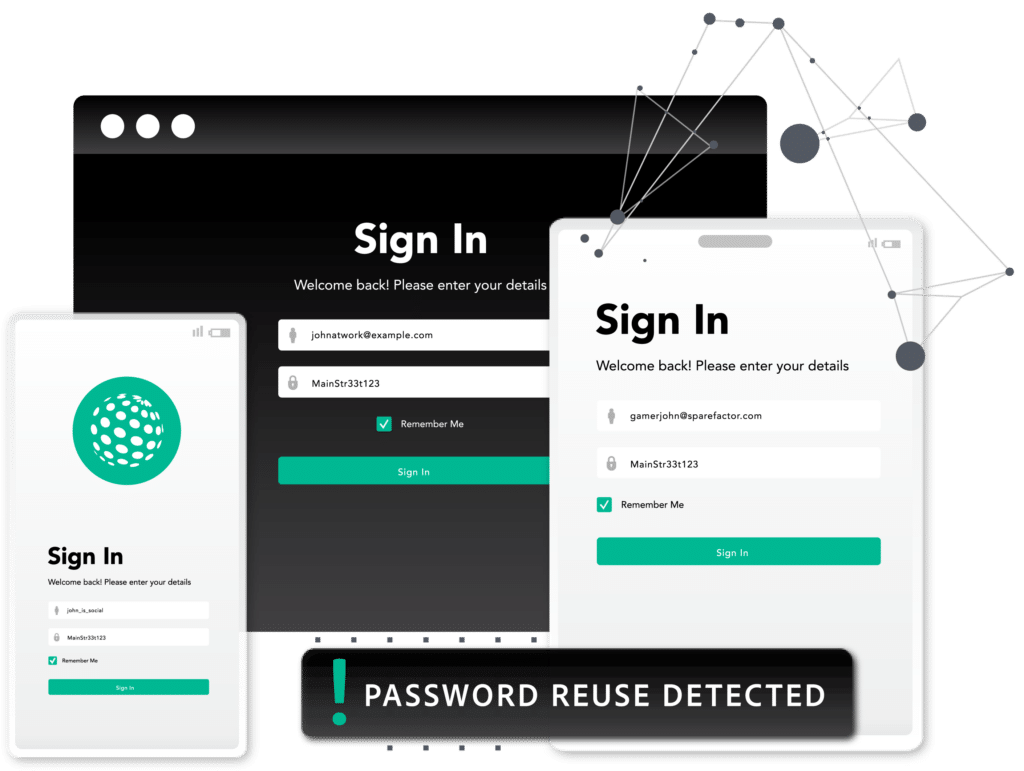
Protect executives without sacrificing privacy
VIP Guardian provides monitoring and protection for executives’ personal information, giving them peace of mind without compromising their privacy. Each executive has their own login and is only alerted if their password have been exposed through a breach or malware infection, and is not visible to their employer.
High-risk executives can add up to 10 personal email addresses for different accounts or family members, extending the peace of mind to their entire family. SpyCloud’s portal is protected by SSO, providing extra security when viewing breach activity.
“Our CEO had his email account taken over and the cybercriminal sent out a bogus email to a finance associate claiming the company’s financial officer authorized a wire transfer.”
Secure your VIPs' digital identities – at work, and beyond
Exposure alerts
Give your executives and VIPs visibility and control of their digital identities with real-time password exposure alerts.
VIP privacy
Let executives and VIPs monitor their security without sacrificing privacy, as individual logins and data breach exposure alerts aren’t visible to employers.
SSO portal
Secure access to a user-facing portal to view breach and malware exposure activity for monitored accounts.
Compromised credential monitoring
Rest easy knowing SpyCloud monitors your watchlist domains, IPs, and emails and checks for exposures against the largest repository of recaptured darknet data.
Customer support
Get access to a dedicated customer support team that can help executives and VIPs understand and respond to potential threats.
Executive reporting
Review reports and analytics on account exposure to track progress over time and identify areas where additional security measures may be needed.
SpyCloud VIP Guardian FAQs
No. Employers cannot see the personal email addresses you decide to monitor or any data breach information that may be tied to them. Your employer can see which corporate email addresses have registered SpyCloud VIP Guardian accounts. This helps your organization control their subscription and make sure that accounts are limited to current employees.
If your password has appeared in the SpyCloud database, it has become available to cybercriminals. Most likely, your password was made public via a data breach. Be sure to change the password anywhere you’ve used a variation of it, and never use that password again.
Sites that collect login information typically store passwords in a hashed format, meaning that if someone breaches their database, the attacker won’t have a ready-to-use list of passwords. To use the passwords, the criminal needs to crack them. Short passwords are usually very easy to crack. Long, complex passwords are harder to crack. A strong password won’t help you if a site stores their passwords in plaintext, but it can make things a bit more challenging for cybercriminals if the passwords are hashed.
- Change your password (everywhere you’ve used it). Make sure none of your accounts are still protected by the exposed password, including the site that was compromised and anywhere else you’ve used it. You should also change all variations of the compromised password on any of your accounts and never use it again. It’s not enough to monitor other accounts using the same or a similar password for suspicious activity. If an attacker has even a few characters of your password, they can crack the entire password.
- Inform all relevant parties as soon as possible. For example, if an account related to work was compromised, or if the password is being used to protect any other internal systems, report it. If anyone else has access to the account, such as in the case of a shared family login, make sure that they’re not using the exposed passwords anywhere else. If so, ask them to change passwords for those accounts to something long and strong.
- Enable two factor authentication (2FA) for all of your accounts where 2FA is an option. While this step is not a failsafe against account takeover and doesn’t replace the need for unique passwords, it does substantially increase your account security.
- Implement a password manager so all of your passwords are unique and easily managed. Most password managers auto-generate complex passwords. Any password that is easy to remember is also easy to guess. This is why the strongest passwords are automatically generated. After a breach of your organization, make sure that use of a password manager is mandated for all employees.
- Intended usage for VIP Guardian is not for children.
You might like:

Enterprise Protection
Safeguard your employees’ digital identities and prevent targeted cyberattacks

2024 Annual Identity Exposure Report
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.
2023 Ransomware Defense Report
As cybercriminals continue to reap rewards from ransomware attacks, how are security teams keeping pace? Download this year’s report for insights on new trends, attack precursors, and critical defense gaps
Cybercrime Analytics
Discover why market leaders across all industries are choosing Cybercrime Analytics over threat intelligence – so they can move beyond context and take action.
