WHITEPAPER
Targeted vs. Automated
Account Takeover Attacks
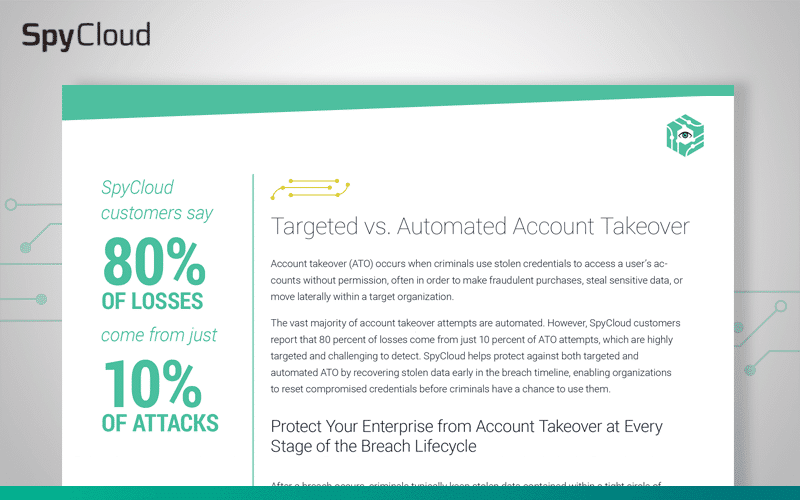
Account takeover (ATO) occurs when criminals use stolen logins to access user accounts without permission–typically credentials that have been exposed in a third-party breach. Using victims’ accounts, criminals can make fraudulent purchases, drain accounts, steal sensitive data, or move laterally within a target organization.
The vast majority of account takeover attempts are automated credential-stuffing attacks. However, SpyCloud customers report that 80 percent of losses come from just 10 percent of ATO attempts, which are highly targeted and challenging to detect.
Read this whitepaper to learn:
- The differences between targeted and automated account takeover attacks and why targeted attacks can cause so much damage
- The five phases of an account takeover attack and the tactics, techniques, and procedures cybercriminals throughout the attack timeline
- How early detection can help you prevent both targeted and automated account takeover
Download the Whitepaper
Targeted vs. Automated Account Takeover Attacks
Solution:
Account Takeover Prevention
Reset stolen passwords before criminals can use them to defraud your users or access sensitive corporate data.
Trusted by market leaders
With 500+ customers around the world, including more than half of the Fortune 10, SpyCloud is the leader in operationalizing Cybercrime Analytics to protect businesses.
We’re on a mission to make the internet a safer place by disrupting the criminal underground. Together with our customers, we aim to stop criminals from profiting off stolen data.
#1 Global
Streaming Service
#1 Global
Airline
#1 Global Software
Company
Leading
US Banks
#1 Global
Online Retailer
#1 US Crypto Exchange
Check Your Exposure
See your real-time account takeover exposure details powered by SpyCloud data.
