WEBINAR
How Credential Stuffing Tools Are Made
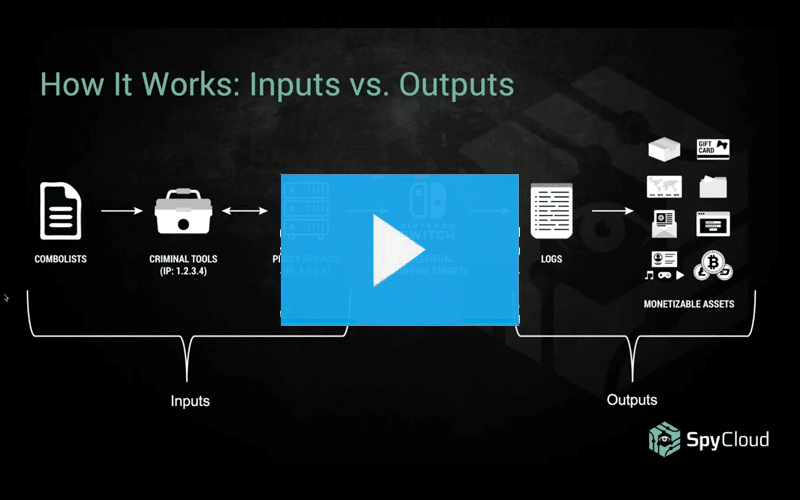
In early 2020, attackers compromised over 160,000 Nintendo accounts via credential stuffing. SpyCloud researchers discovered source code for one account checker tool that was custom-built to help criminals test stolen credentials against Nintendo logins, enabling attackers to access customer accounts and exploit saved payment methods to purchase in-game currency.
With so many people stuck at home, popular consumer services like Nintendo are facing high demand – from both legitimate customers and cybercriminals. Sophisticated crimeware makes it easy for criminals to target these types of organizations in credential stuffing attacks and defraud their customers. To protect consumers from account takeover, enterprises need to take proactive measures.
View this on-demand webinar to learn:
- How credential stuffing works, from the lifecycle of stolen credentials to the crimeware attackers use to automate account takeover
- Why stolen accounts that don’t have obvious monetary value can be profitable for cybercriminals
- How credential stuffing and account takeover fit into the broader criminal economy
- What your enterprise can do to combat both credential stuffing and more advanced types of account takeover attacks
Watch the Webinar:
How Credential Stuffing Tools Are Made

Presenter Info
Chip Witt, Vice President of Product Management
Chip Witt has nearly twenty years of diverse technology experience, including product management and operations leadership roles at Hewlett Packard Enterprise, Webroot, VMware, Alcatel, and Appthority. He is currently the VP of Product Management and oversees the Customer Success Program at SpyCloud. Chip works closely with field intelligence teams specializing in OSINT and HUMINT tradecraft, actor attribution and underground monitoring.
Trusted by market leaders
With 500+ customers around the world, including more than half of the Fortune 10, SpyCloud is the leader in operationalizing Cybercrime Analytics to protect businesses.
We’re on a mission to make the internet a safer place by disrupting the criminal underground. Together with our customers, we aim to stop criminals from profiting off stolen data.
#1 Global
Streaming Service
#1 Global
Airline
#1 Global Software
Company
Leading
US Banks
#1 Global
Online Retailer
#1 US Crypto Exchange
Check Your Exposure
See your real-time account takeover exposure details powered by SpyCloud data.
