Transform your threat intelligence capabilities with
actually actionable data
continuous monitoring
automated remediation
SpyCloud goes well beyond IOC feeds to deliver fully enriched breach, malware, and phishing exposure data – empowering CTI teams to investigate and stop threats quickly.

TRUSTED BY HUNDREDS OF GLOBAL INDUSTRY LEADERS
A modern approach to threat intelligence – built for automated protection from critical attacks
Threat intel teams turn to SpyCloud for identity threat protection solutions that stop the threats you face now and those coming your way in the future. With SpyCloud, you get rapid evidence of identity compromises, combined with automated remediation that reduces analyst effort and delivers immediate protection.
Fresh data from the criminal underground
Rapid delivery of the exact data criminals are using to target your users and your business today
Comprehensive threat visibility
High fidelity alerts illuminate compromised user identities, applications, and devices at risk of account takeover and other identity-based cyberattacks
Improved CTI investigations
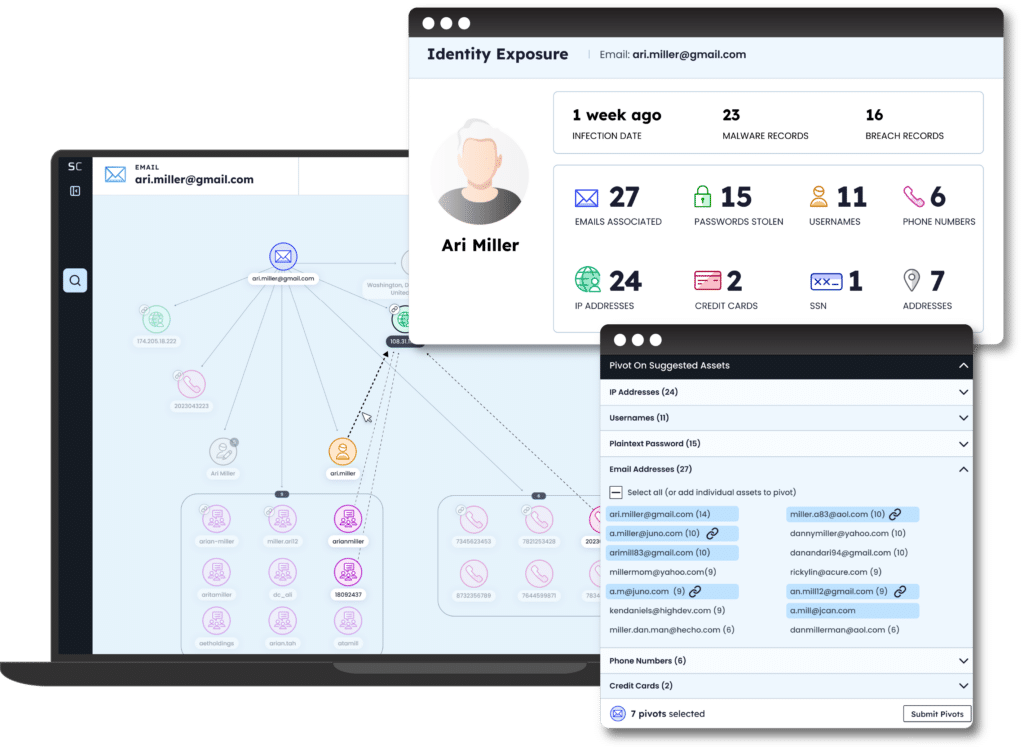
Uncover hidden relationships between assets to accelerate the outcomes of cybercrime investigations and threat actor attribution
Go beyond threat intel feeds & IOCs
High-volume darknet data
SpyCloud is the ultimate force multiplier – delivering quality recaptured data that aids investigations into threats against the enterprise. Leverage the world's largest and continuously updated collection of recaptured data, with 25+ billion assets ingested and analyzed monthly. No other provider offers this scale of high-quality data.
Early detection to stop ransomware
SpyCloud automatically alerts you when actors have stolen access to your environment via infostealer malware, including exposures of critical workforce apps like SSO and code repositories that can facilitate ransomware attacks.
Powerful malware analytics
Reduce enterprise risk and accelerate your investigations with SpyCloud's analytics. Uncover employees' malware-infected devices, managed and unmanaged, and the applications exposed as a result. Profile threat actors and and identify correlating details that aid attribution, and easily unmask insider risk by researching the risk level of specific users based on recaptured malware records.
Vast integrations
Threat intel teams can feed SpyCloud data into existing workflows and applications, including SIEMs, SOARs, EDRs, TIPs, and other internal detection tools to enable automation. Investigations are aided by 80+ Maltego Transforms, and the option to leverage pre-built, web-based Jupyter Notebooks that deliver query results in an easy-to-digest format that enables drill-downs, data exports, and clickable graphs. Explore integrations →






SpyCloud offers out-of-the-box API integrations with top technology vendors across SIEM, SOAR, EDR, TIPs and more to power detection and remediation via automated workflows.
SpyCloud turns the tables by making darknet data work for you
We offer the highest volume, highest quality data from breaches, malware-infected devices, and successful phishes – operationalized for CTI teams to investigate and stop identity-based threats and the actors perpetrating them.
Assets
Breaches
Assets Ingested Monthly
Malware
Families
You might like:

2024 Annual Identity Exposure Report
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.
Post-Infection Remediation Guide
Post-Infection Remediation is SpyCloud’s new, critical addition to malware infection response. This guide goes in-depth on how to stop malware exposures from becoming full-blown ransomware incidents.

Malware-Infected User Response Guide
Handy guide to decipher what it means when employee or consumer information appears on a botnet log, and how to contact infected users with an action plan.
