REPORT
The SpyCloud Malware Readiness and Defense Report
- Trends leading to higher malware risk
- The need for better visibility into malware-exfiltrated data
- Opportunities to improve malware detection and response
- Post-Infection Remediation best practices
Top Threats to Organizations
Working together to produce harmful outcomes for your business
Ransomware
Phishing
Infostealer Malware
Overlooked Entry Points LEAVING ENTERPRISES EXPOSED
allow employees to sync browser data between personal and corporate devices
struggle with shadow IT due to employee adoption of applications and systems without IT’s consent
allow unmanaged personal devices to access business applications and systems
Gaps in Malware Infection Response
don’t routinely review their application logs for signs of compromise
don’t reset passwords for potentially exposed applications
don’t terminate session cookies at the sign of exposure
Survey Says
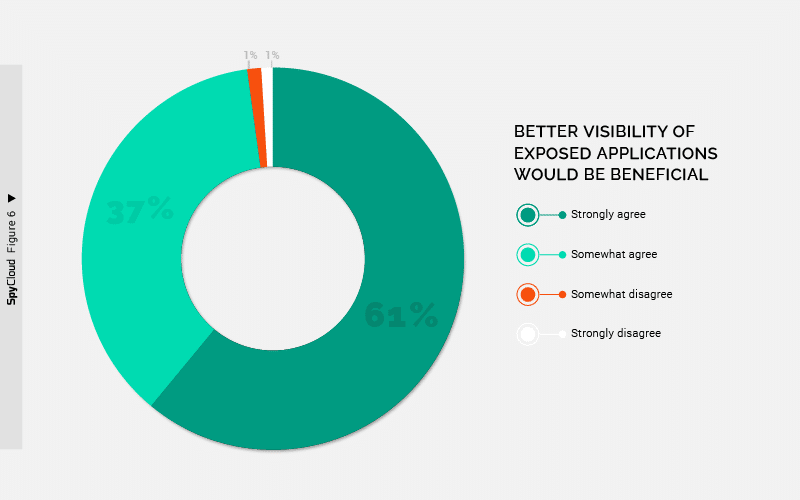
Almost all of our survey respondents agreed that gaining a clear picture of business applications exposed by infostealer infections would significantly improve their security posture.
However, organizations ranked the ability to identify what third-party business applications have had credentials exfiltrated by an infostealer last in their malware detection and response capabilities.
Post-Infection Remediation can help close this gap in malware infection response, illuminating the exact authentication details criminals have in hand and are using to target the business so appropriate action can be taken.
Download this year’s report to see:
- How today's digital environment increases the risk of malware while decreasing security teams’ visibility into a growing attack surface
- How organizations are addressing malware infections and the gaps that exist with machine-centric remediation
- How bad actors are shifting their tactics to access organizations via session hijacking with malware-exfiltrated cookies
- How Post-Infection Remediation reduces the risk of follow-on attacks after a malware infection
Trusted by market leaders
With 500+ customers around the world, including more than half of the Fortune 10, SpyCloud is the leader in operationalizing Cybercrime Analytics to protect businesses.
We’re on a mission to make the internet a safer place by disrupting the criminal underground. Together with our customers, we aim to stop criminals from profiting off stolen data.
#1 Global
Streaming Service
#1 Global
Airline
#1 Global Software
Company
Leading
US Banks
#1 Global
Online Retailer
#1 US Crypto Exchange
Check Your Company's Exposure
See your real-time exposure details powered by SpyCloud.
