Leverage SpyCloud’s out-of-the-box, native integrations to prevent targeted cyberattacks and protect exposed employee and customer identities.






SpyCloud’s integrations with SOARs, SIEMS, IdPs, and EDRs power up your workflows to detect and prevent targeted cyberattacks.
SpyCloud integrates with popular identity access providers like Active Directory, Entra ID, and Okta to continuously monitor for and identify compromised credentials, allowing you to quickly remediate identity exposures.




SpyCloud integrations with SOAR platforms like Palo Alto Cortex XSOAR, Tines, and Microsoft Sentinel come with ready-to-use incident response playbooks and curated intelligence. This means you can quickly and easily tackle identity-related exposure incidents.

SpyCloud integrations with SIEM tools like Splunk, Elastic, Google Chronicle, and Microsoft Sentinel help you prioritize alerts and take fast action to protect your employees.
Combine SpyCloud-normalized OSINT with other valuable third-party data in a single repository. Gain better insight into the threats facing your organization and exponentially increase the accuracy and speed of investigations.
See how to integrate SpyCloud’s recaptured identity data within your existing security workflows.
SpyCloud’s API integrations work with leading technology vendors, delivering identity protection at scale to prevent next-gen threats.
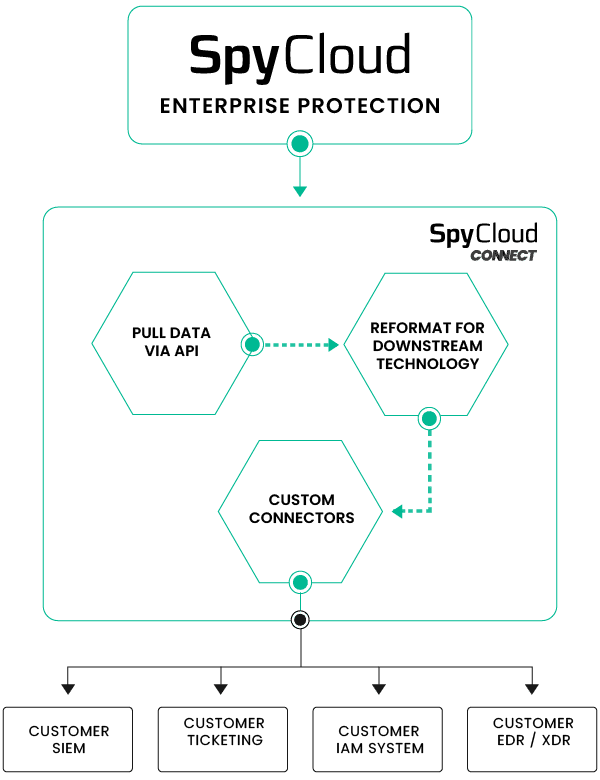
SpyCloud Connect is a hosted custom automation solution that allows SpyCloud products to be seamlessly integrated with a wide variety of security tools and processes – enabling rapid remediation and scalable automation of compromised identities within a customer’s preferred tech stack.
Whatever you want, whenever you want it – SpyCloud Connect builds out the workflows for your desired integrations to send SpyCloud data where and when you need it, all in the tools you are using today without needing to burden your existing resources with custom development work.
The SpyCloud API was super easy to integrate. It took a day and a half for our engineers, and then it was just up and running. We’ve had the integration in place for a year now and had zero issues, zero downtime. On the technology side, it’s an enterprise-grade API for us.
SpyCloud Enabled a Global Fintech Company to Protect Thousands of Vulnerable Accounts Representing Tens of Millions of Dollars
3.5
MONTHS
AVERAGE PAYBACK PERIOD FOR SPYCLOUD CUSTOMERS
UP TO
60%
LENDINGTREE SAVES 60% OF SOC TEAM’S TIME AND RESOURCES WITH ACTIONABLE DATA & AUTOMATION
2130 S Congress Ave
Austin, Texas 78704
Call: 1-800-513-2502
©2024 SpyCloud, Inc. All Rights Reserved
Check Your Exposure has been expanded with more recaptured data. See Your Results Now
Thank you for submitting the form