Session Identity Protection for Consumers
Prevent ATO caused by session hijacking
Protect vulnerable accounts from ATO and fraud
SpyCloud is the only provider operationalizing malware-siphoned authentication data for fraud and account takeover prevention – recapturing millions of malware records from the criminal underground each week, at a speed and scale that cannot be matched.
Decrease business loss
Reduce losses from hard-to-detect fraud involving malware-stolen data
Prevent ATO
Prevent criminals from exploiting your users’ stolen browser sessions for account takeover
Stop targeted attacks
Stop bad actors from impersonating trusted devices to bypass MFA
Strengthen account security by prioritizing high-risk accounts
Safeguarding your organization and customers from “next-generation” account takeover requires a new and proactive approach to account security – which starts by identifying malware-infected users and the still-active authentication cookies in criminal hands.
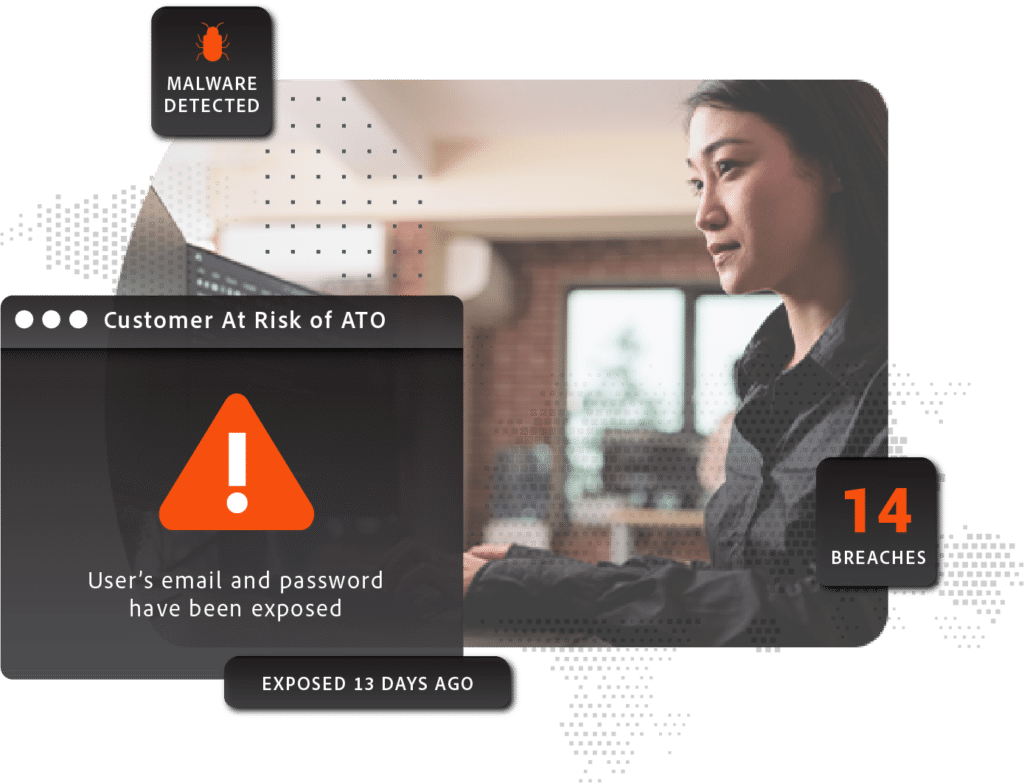
Identify malware-infected customers
By identifying customers associated with compromised devices, security teams can flag the accounts and subject future logins and transactions to increased scrutiny or additional authentication measures, providing an extra layer of protection.
Additionally, organizations can proactively reach out to customers to inform them of their exposure, offering guidance on how to remediate their device and building trust by ensuring that their account will be monitored for suspicious activity.
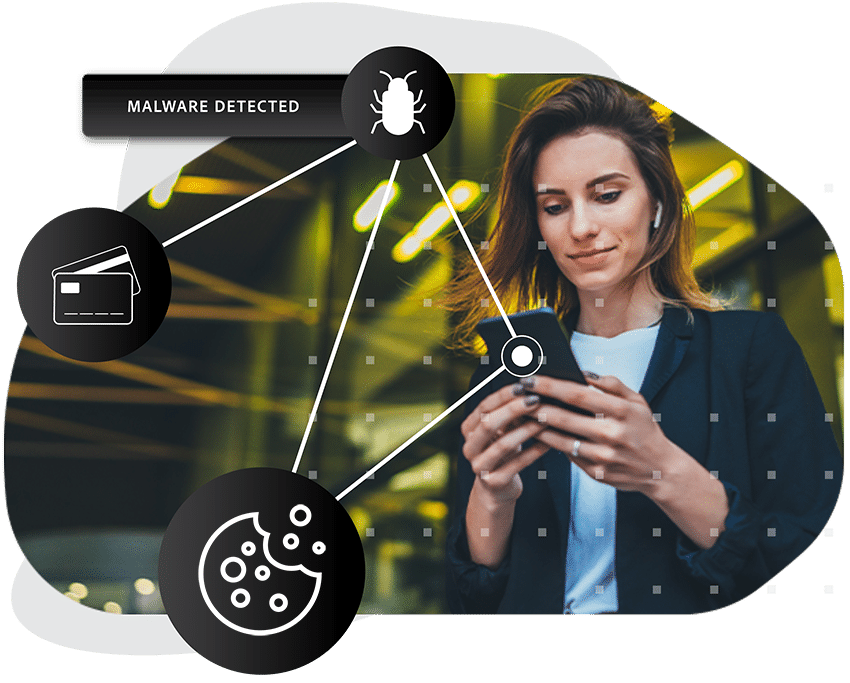
Protect high-value accounts
Criminals often single out high-value account holders for sophisticated, targeted attacks, knowing that gaining access will yield substantial benefits.
SpyCloud understands the risk that exposed session cookies can have on your loyal customers and ensures your security teams can act swiftly to secure their accounts, sensitive information, and funds – preserving trust and mitigating potential financial losses or reputation damage.
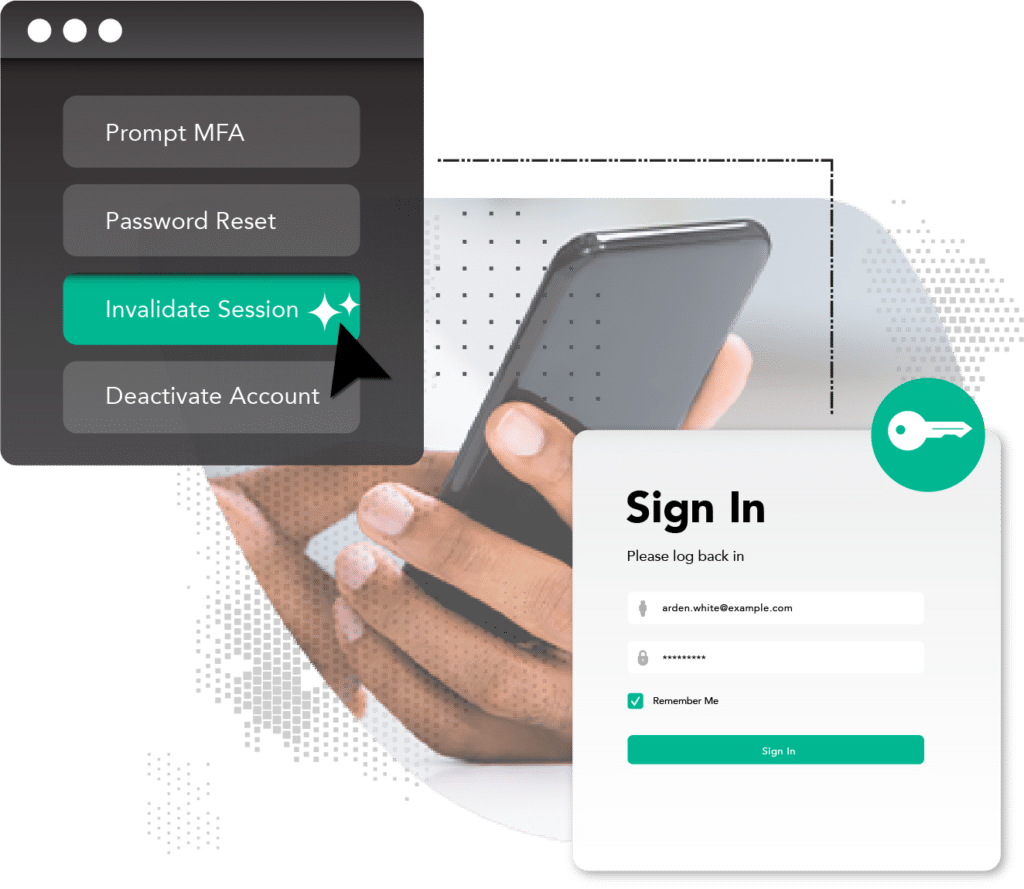
Prevent authentication bypass
Criminals have discovered ways to bypass all forms of authentication by using malware-exfiltrated cookies in an anti-detect browser to mimic a trusted user’s device – defeating the need for a password, passkey, or any form of MFA. As long as a cookie stays valid, the gate to that user’s account remains wide open.
SpyCloud’s Session Identity Protection provides your business with the exact cookies in criminal hands and the supporting information your team needs to invalidate active sessions and lock criminals out of accounts immediately, negating them before fraud can occur.
“This was amazing. We were able to respond quickly, invalidate cookies, and protect millions of customer dollars.”
– Financial Services Company
SpyCloud Session Identity Protection for Consumers FAQs
Session hijacking occurs when a user’s web session is taken over by an attacker. When you log into a site or application, the server sets a temporary session cookie in your browser. This lets the application remember that you’re logged in and authenticated. Some cookies may last only 24-48 hours, while others last for months.
Leveraging malware-siphoned authentication cookies, bad actors can perpetrate session hijacking which bypasses the need for credentials (username + password combo), multi-factor authentication (MFA) and even passkeys altogether. Session hijacking is an increasingly prevalent precursor to fraud.
Easily (unfortunately).
Step 1: Trick user into clicking on a dangerous link or downloading a malicious attachment to infect their device with malware.
Step 2: The malware siphons all manner of data from the infected device, including credentials, autofill info, and web session cookies without the user being aware of the infection.
Step 3: The criminal can then use a stolen session cookie to authenticate as the user – without the need for a username and password – bypassing security and fraud controls including MFA.
Typically criminals gain access to session cookies by one of two ways: either by deploying malware directly onto a user’s device, or by buying or trading botnet logs on the darknet. Once a criminal acquires the stolen web session cookies, it is scary how quickly and easily they launch account takeover attacks.
The best way to prevent session hijacking is by understanding what it is and how it’s executed, monitoring for stolen web sessions programmatically, and developing a process to invalidate web sessions related to infected users. Reacting quickly ensures criminals stay locked out and prevents them from reaping the benefits of malicious activity.
Since web sessions can be valid for a couple of days or even a couple of months, having early insights about malware-compromised sessions can help organizations act quickly to thwart session hijacking.
Passkeys are certainly more secure than passwords, but they have some of the same problems. Both forms of authentication are easily bypassed by session hijacking, which enables a criminal to take over an already authenticated session. We cover session hijacking and the vulnerabilities of passkeys in this blog article.
You might like:

2024 Annual Identity Exposure Report
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.

Malware-Infected User Response Guide
Handy guide to decipher what it means when employee or consumer information appears on a botnet log, and how to contact infected users with an action plan.
MFA Bypass 101
Understand how hackers combine attack methods and stolen credentials to sidestep multi-factor authentication.

Passwordless May Be The Future, But Is It a Cure-All?
Passwordless authentication feels like all the rage these days but it doesn’t come without its own challenges.
Get ahead of next-generation ATO
Even as authentication methods evolve, you can defend against threats to your customers with SpyCloud.
