Consumer ATO Prevention
Protect your customers and prevent consumer account takeover
SpyCloud Consumer ATO Prevention alerts you when your customers’ data appears on the criminal underground, allowing your organization to act swiftly to lock bad actors out of compromised accounts.
Disrupt cybercriminals' ability to profit
SpyCloud’s operationalizes the world’s largest repository of recaptured breach and malware data to help you detect exposed credential data, automate step-up authentication or password reset, and support your overall consumer ATO prevention strategy.
Reduce consumer
ATO
Prevent criminals from making fraudulent purchases, siphoning rewards points, stealing personal information, and locking legitimate users out of their own accounts
Increase
operational efficiency
Reset passwords or choose an appropriate step-up authentication path for affected users without adding unnecessary friction to the user experience
Preserve
customer trust
From account creation to digital transactions – safeguard your consumers’ digital experiences to ensure brand loyalty and trust
Stay a step ahead of cybercriminals
SpyCloud recaptures data at a scale that cannot be matched – shortening your exposure windows and protecting your customers from the effects of automated and targeted attacks.
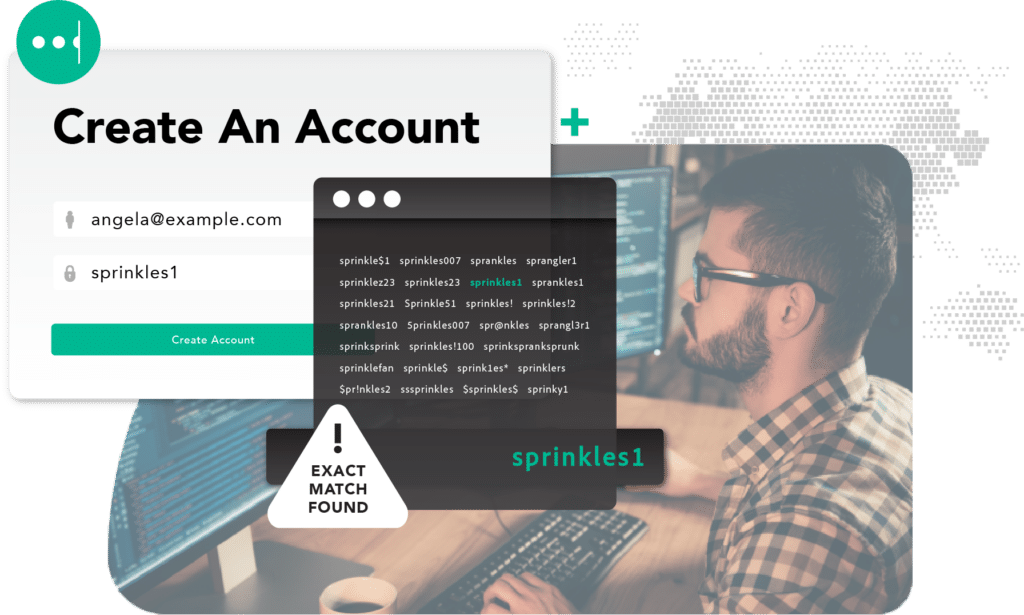
Reduce fraud losses, without adding friction
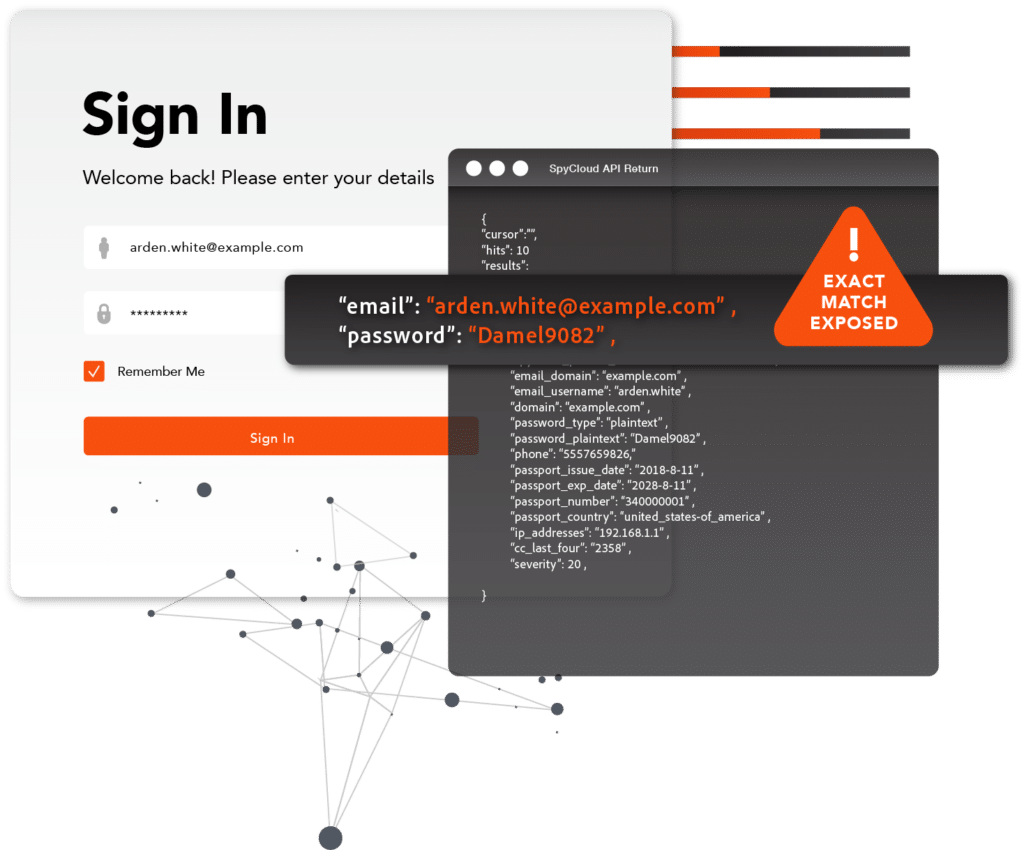
Protect your brand and the customer experience
Act on SpyCloud alerts to shorten your users’ exposure windows, preventing backlash and illegitimate claims that result from successful credential stuffing attacks against your customers.
SpyCloud researchers infiltrate criminal communities to recover breach data early in the breach timeline, giving you as much notice as possible that your customers’ passwords have been exposed – often months or even years before a breach becomes public. By addressing vulnerable accounts early, you can protect your consumers from hard-to-detect targeted attacks that occur early in the breach timeline and account for 80 percent of account takeover losses.
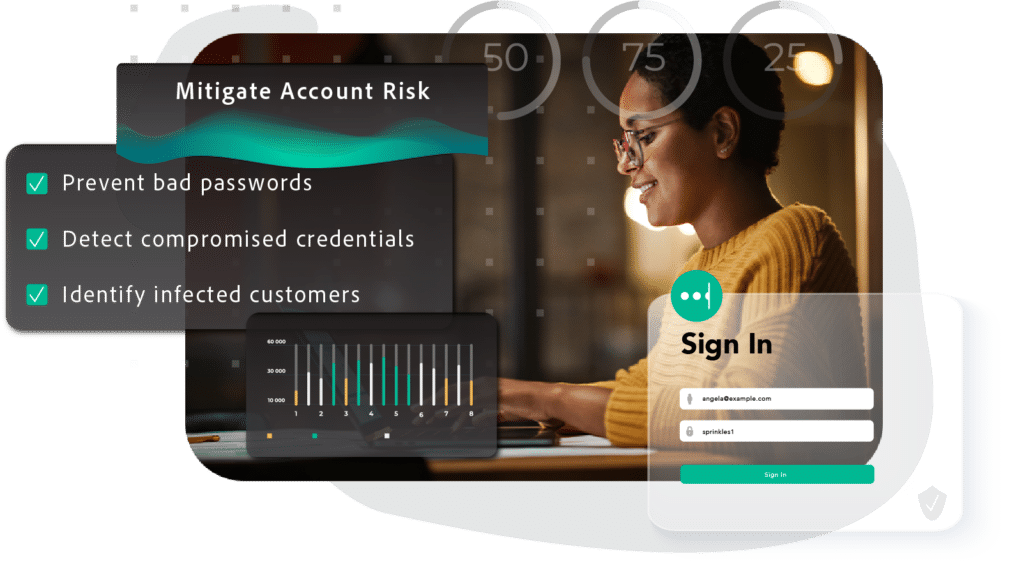
Increase your impact
New breaches happen constantly, presenting a challenge for enterprises that want to keep customer accounts secure without hiring a dedicated team to stay on top of the latest exposures. SpyCloud extends your team’s reach by collecting and operationalizing breach data at scale. Our researchers collect an estimated 25+ billion new breach assets per month and make that data actionable, giving your team the data you need to make sure your users are who they say they are.
“We don’t have to do any manual processing of public breaches anymore, which took a lot of time with the constant stream of new breaches. SpyCloud’s amazing API allows us to automate the entire process.”
– Niels Heijmans, Principal Security Intelligence Analyst at Atlassian
What else can I do with SpyCloud Consumer ATO Prevention?
Identify bad passwords
Prevent customers from using weak, common, risky, or previously compromised passwords at account creation.
Compromised credential monitoring
Monitor your users for new exposures over time – ensuring account integrity throughout the customer lifecycle.
User monitoring
Identify non-credential data tied to your user that could facilitate fraud – check for breach exposure tied to your consumers’ email addresses, IP addresses, phone numbers, or usernames.
Detect infected users
Prevent ATO of malware-affected accounts, and customize remediation and notification based on the digital journey.
NIST alignment
Prevent your consumers from choosing passwords that are weak, common, or compromised by checking new passwords against our entire database of billions of previous exposures.
Easy APIs
High-volume access to the SpyCloud dataset helps you detect matches, reset exposed credentials, and support your overall consumer account takeover prevention strategy.
Real-time account login checks
Check credentials in real time as users log into your application, in parallel with a step-up authentication
procedure for high-risk actions.
See how it works
Test any password to see how many times it has appeared on the darknet, meaning it’s unsafe to use.
SpyCloud Consumer ATO Prevention FAQs
In an account takeover (ATO) attack, criminals use another person’s login credentials, most often by leveraging reused or similar passwords from previously breached sites, to gain access to existing accounts. Once inside, they make unauthorized transactions, siphon funds, and steal corporate data or personally identifiable information (PII) to use for other purposes, or simply to sell to other attackers on the dark web.
Criminals are typically taking over accounts for profit, pure and simple. It all comes down to money, and how much of it criminals can extract from what they’ve stolen. Contrary to what you may have heard elsewhere, the first step to monetizing stolen data is not to sell it on the dark web. That’s actually the last step. What happens first is the highest effort, most profitable activities.
With stolen data, criminals will:
- Drain financial accounts, crypto wallets or loyalty point balances
Criminals will take control of financial accounts and immediately wire or transfer the balance from victims’ accounts. In a twist on this concept, there has been a huge uptick in peer-to-peer payments fraud, up 733% since 2016. - Make fraudulent purchases
Another quick scheme: criminals will purchase goods using stolen or stored credit card or gift card data. In fact, 40% of all fraudulent activity associated with an account takeover occurs within a day. - Create synthetic identities
Some criminals are specialists when it comes to creating new identities with a combination of fake and legitimate (stolen) data. The payoff might not come for months, since these identities need to be “warmed up” before they are used to obtain lines of credit. - Exploit victims’ work accounts
Criminals may try to locate and steal corporate IP and deploy business email compromise scams, which resulted in $2.4B in losses in 2021 alone. - SIM swap victims to bypass MFA
In a SIM swap attack, criminals transfer a victim’s phone number to their own SIM card in order to bypass multi-factor authentication and take over sensitive accounts.
SpyCloud Consumer ATO Prevention operationalizes SpyCloud’s extensive database of recaptured darknet assets using high-volume, REST-based APIs. Depending on your organization’s requirements, you can check consumer logins using identifiers (such as email address, username, phone number, or IP address), passwords (partial hashes), or a combination of both.
Alternative solutions are available for organizations that must satisfy a high volume of API calls or specialized privacy requirements.
You might like:

2024 Annual Identity Exposure Report
With nearly half of our data coming from botnets last year, our annual report of recaptured darknet data features key trends about malware and identity exposure.
Mobile Ecommerce Marketplace
An ecommerce marketplace uses SpyCloud Consumer ATO Prevention to reduce ATO fraud, avoid fraud losses, and reduce resources dedicated to ATO prevention.
Best Practices for Notifying Consumers of a Third-Party Breach
When your consumers’ passwords appear in a third-party breach, the language you use to notify them that their passwords must be reset requires careful consideration.
Integrate Consumer ATO Prevention into your existing workflows
SpyCloud data is easily integrated into existing login workflows, password change and reset processes, and common SIEMs and TIPs. Get up and running fast, and see value on day one.
