SpyCloud Solutions
We offer automated solutions that protect enterprises from cyberattacks, safeguard consumer identities, and power cybercrime investigations.
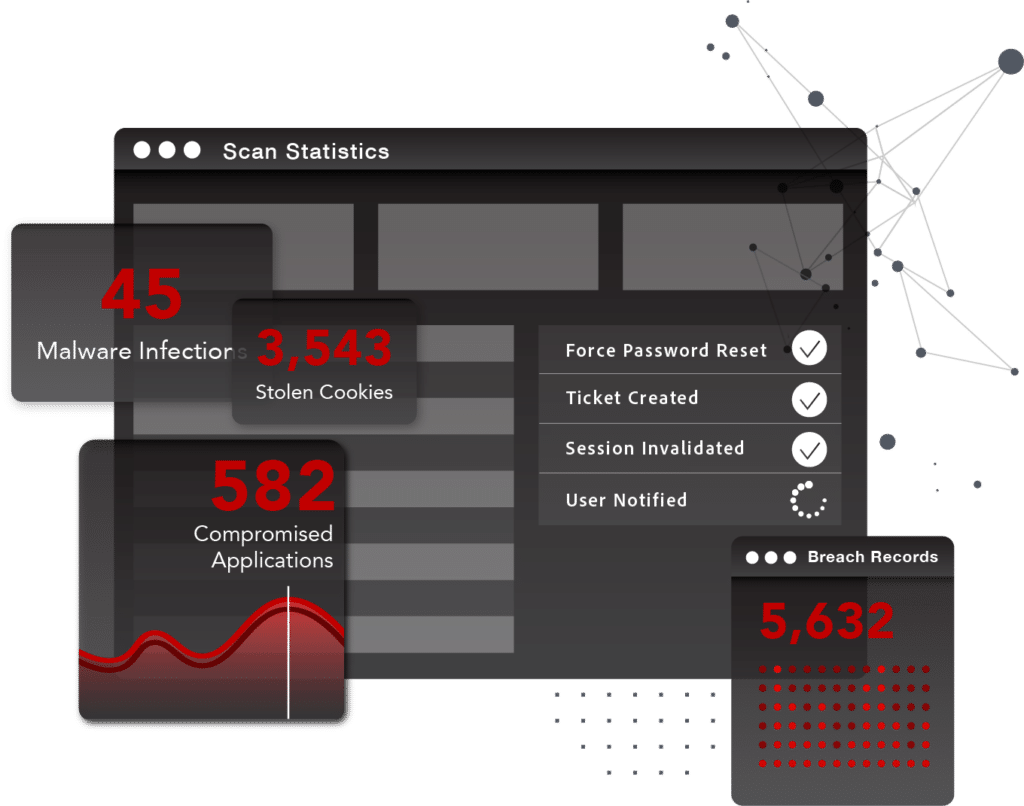
SpyCloud empowers security teams to take action on malware-infected devices, compromised users, and exposed applications to stop account takeover, ransomware, and online fraud from affecting your business.
TRUSTED BY HUNDREDS OF GLOBAL INDUSTRY LEADERS
The SpyCloud Difference
3.5
MONTHS
AVERAGE PAYBACK PERIOD FOR SPYCLOUD CUSTOMERS
UP TO
60%
LENDINGTREE SAVES 60% OF SOC TEAM’S TIME AND RESOURCES WITH ACTIONABLE DATA & AUTOMATION
Explore ways to disrupt cybercrime with SpyCloud
EXPLORE USE CASES
Use cases for every scenario
Achieving breadth and scale is simple with SpyCloud – with solutions that align to critical business initiatives, delivering outcomes that protect, secure, and prevent.
WHO USES SPYCLOUD?
Powering security teams worldwide
INDUSTRIES
Solutions for every industry
Here is just a sample of the kinds of companies disrupting cybercrime with SpyCloud.
EXPLORE SOLUTIONS
Our solutions are built on insights no other provider can achieve thanks to our ability to curate, enrich, and analyze darknet data – delivering automated solutions to disrupt cybercrime.
Reduce your risk of ransomware and other critical attacks – acting on known points of compromise
Learn more
Take a proactive approach to combating account takeover and stop high-risk attacks tied to malware
Learn more
Uncover hidden relationships between assets – improve outcomes of investigations into financial crimes, insider risk, ransomware attacks, and more
Learn more
Access comprehensive breach, malware, and phished data to add value to security and fraud detection products and services
Learn more
WHAT CAN SPYCLOUD TELL YOU?
Uncover threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures

Power Your Products with SpyCloud Data
Partner with the industry leader in the recapture of darknet data
SpyCloud provides product teams with fast, easy access to the world’s most comprehensive repository of breach, malware-siponed and success phished data, enabling you to create offerings that protect consumers and businesses – and bring them to market quickly.
By integrating SpyCloud data into security, dark web monitoring, identity theft, fraud detection, and payment solutions, you can accelerate customer acquisition, improve retention, generate new revenue, and truly differentiate yourself from the competition.






