Mitigate supply chain ATO risks with Third Party Insight
SpyCloud Third Party Insight monitors for supply chain security risks from exposed credentials. Prevent employee ATO and help vendors remediate and protect their data.
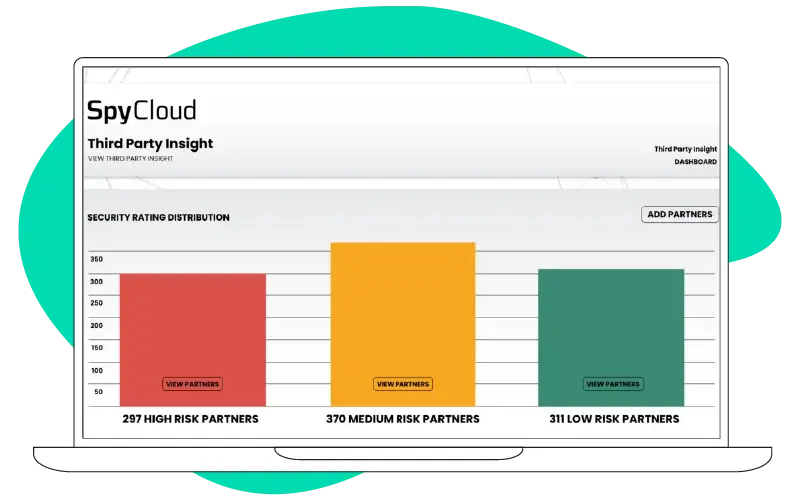
Protect your enterprise from unauthorized access and simplify your vendor risk management
Third-party vendors with privileged access to your data and systems pose risk of third-party vendor data breaches and access to your sensitive data. Mitigate supply chain vulnerabilities with SpyCloud Third Party Insight, which draws from our largest repository of breach and malware records to give visibility into critical exposures within your supply chain.
Reduce third-party
ATO risk
Shield your organization from cyberattacks by identifying high-risk partners with exposed passwords and potentially infected employees
Simplify vendor risk remediation
Gain holistic insights into your vendor ecosystem by continuously evaluating the security posture of your third party vendors with SpyCloud’s comprehensive security rating and reporting
Accelerate partner remediation
Empower your partners’ remediation with granular access to SpyCloud’s exposure data for their own affected employees, including usernames and exposed passwords
Take control with supply chain risk mitigation
SpyCloud Third Party Insight proactively safeguards your organization from third party ATO risk with at-a-glance reporting within SpyCloud’s centralized dashboard. Go beyond monitoring by providing trusted partners with access to their compromised data, including usernames and plaintext passwords, and pathways for remediation.
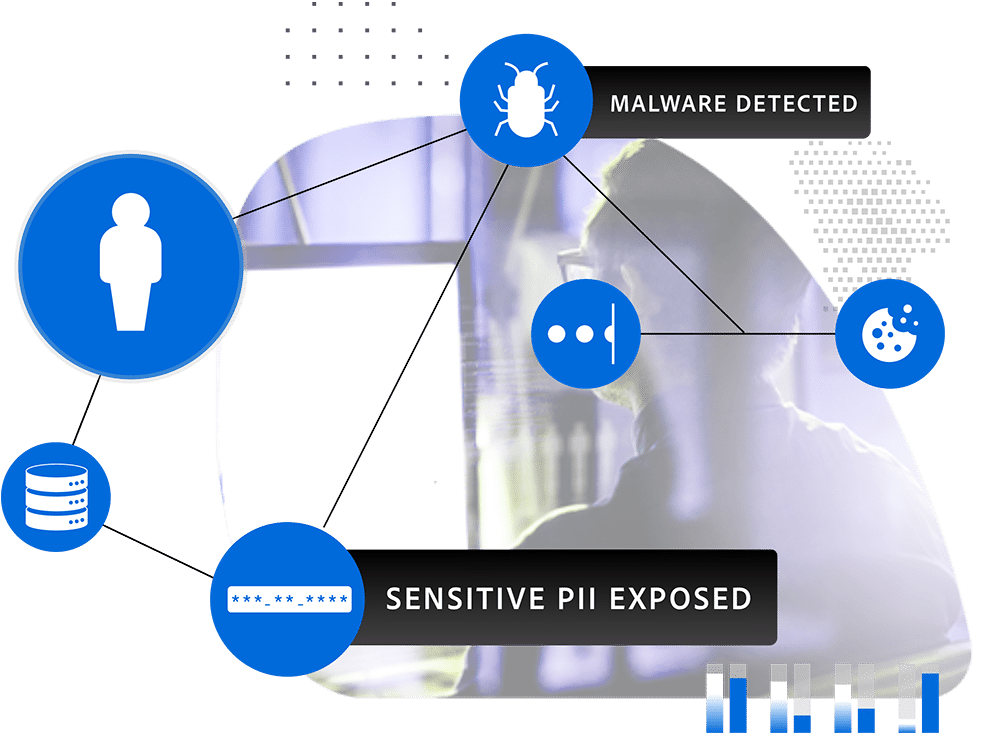
Identify vendor exposures before becoming security risks
Exposed credentials, malware infections, and reusing exposed passwords, among other bad habits, offer criminals pathways for targeted ATO and follow-on costly cyberattacks. Vendors’ lack of visibility leaves your enterprise network vulnerable to criminals siphoning your employee data or sensitive IP. SpyCloud Third Party Insight publishes recaptured darkweb data breach and malware records early in the timeline, enabling you and your partners, vendors, and suppliers to take action to prevent targeted attacks.
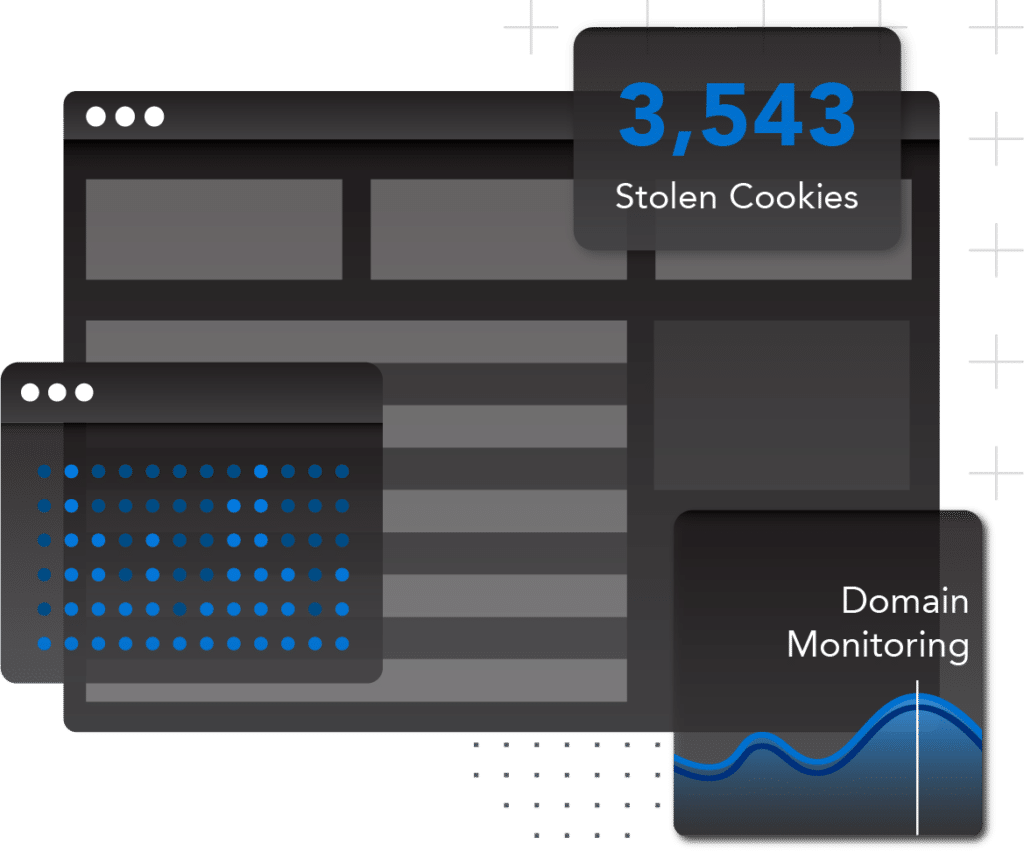
Track trends of third party security risks
Gain insight into your third parties’ exposure, including when and why their security risk level has changed over time. Simplify your vendor risk management with ongoing monitoring of your third parties’ exposures, so you can make adjustments quickly. SpyCloud frequently publishes new breach and malware records and alerts you to new security risks within vendors.
Share detailed findings for vendor remediation
Many vendors risk management solutions fall short with enabling high-risk vendors to close their security gap with exposed employee identities. SpyCloud Third Party Insight takes a different approach. You can provide vendors access to their own SpyCloud portal to review their own compromised data, including affected usernames and plaintext passwords. Vendors can reset exposed passwords, remediate malware exposures, and lower their SpyCloud risk rating.
“One of the best ways of infiltrating a business is to attack the supply chain. If you can’t get to the people within the organization directly, then embedding yourself in lines of communication has to be the next best thing, if not even better… So we use SpyCloud to check on third parties’ security posture.”
– Dan Holland, Global Senior Director of IT Operations at Alvarez & Marsal
Get more with SpyCloud Third Party Insight
Continuous monitoring
SpyCloud continuously monitors domains, IPs, and emails and checks for exposures against the largest repository of recaptured darknet data.
Complete visibility
Quickly identify high-risk third parties with a summary dashboard that groups vendor domains by high, medium, and low security ratings.
Vendor insights
Easily share third-party vendor risk details for vendors to mitigate a supply chain attack and resolve their employee exposures, including exact email credentials and plaintext passwords.
Security alerts
Receive alerts from SpyCloud when your third parties’ credentials are exposed in recaptured breach or malware logs in our dataset.
Vendor management
Select top vendors within the SpyCloud portal to invite to their own version of the portal and access the data they need for validation and remediation.
Risk scoring
Understand SpyCloud’s risk assessment of your vendors categorized by levels of potentially infected employees, exposed executives, plaintext passwords, and other factors.
Changes at-a-glance
View trends in third party risk over time in the SpyCloud dashboards to see which vendors are lowering their exposure.
You might like:

Enterprise Protection
Safeguard your employees’ digital identities and prevent targeted cyberattacks.
Hard Truths About ATO & Strategies To Defend Your Enterprise
Protecting your enterprise from breaches and account takeovers has never been a bigger challenge.
Cybercrime Analytics
Discover why market leaders across all industries are choosing Cybercrime Analytics over threat intelligence – so they can move beyond context and take action.
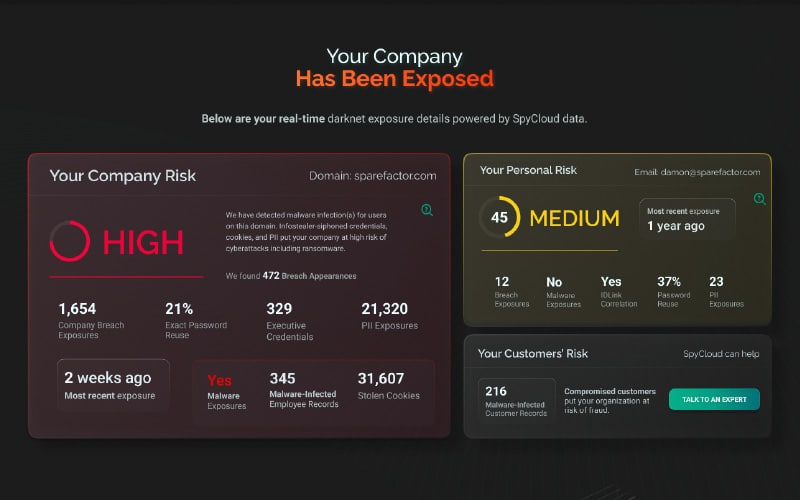
Check your darknet exposure
Check your darknet exposure against SpyCloud’s 500B+ recaptured breach and malware assets.
Protect your enterprise from supply chain risks
Monitor vendor exposures and security risks with Thirdy Party Insight
