Session Identity Protection for Employees
Prevent ATO caused by session hijacking
With SpyCloud’s Session Identity Protection for enterprises, security teams can detect when your employees’ authentication cookies are stolen by malware and intervene to prevent session hijacking and MFA bypass.
Stop bad actors from using your users’ stolen browser sessions for account takeover
A stolen browser session from your enterprise’s single sign-on provider or developer tool can allow bad actors to bypass passwords, passkeys and even MFA, access corporate resources, or even just identify an infected device’s owner as a potential entry point to your organization.
Stop account
takeover
No other provider leverages recaptured malware data for account takeover prevention, let alone at the speed and scale SpyCloud can deliver
Lock out
bad actors
Level the playing field with criminals with alerts when employee’s active web sessions have been compromised so they can be invalidated
Secure third-party workforce services
Prevent unauthorized access when cookies from critical workforce services are stolen from infected personal or corporate devices
Detect compromised cookies that put your users at risk
When you query the Session Identity Protection API, SpyCloud returns compromised cookie data associated with your domains, including the information you need to identify which accounts are vulnerable and determine how to intervene.

Prevent unauthorized access
Malware-siphoned cookies allow bad actors to bypass MFA and hijack users’ accounts. Many sites use cookies to remember “trusted devices” so that MFA and/or passwords aren’t required at a user’s next login. Criminals have been abusing this feature for account takeover.
By giving enterprises access to stolen session data for their domain, SpyCloud enables enterprises to address this type of unauthorized access proactively. Enterprises can protect employee accounts from targeted attacks by cutting off the ability for bad actors to bypass MFA, as well as flag users with known compromised devices for future logins or access, even if the session has already expired.
Safeguard employee productivity
Using malware, criminals can steal all the digital clues enterprises use to identify users. Malware can siphon all the same data authentication solutions use to validate users’ digital identities, making it easy for a criminal to take over an infected user’s accounts – and nearly impossible for enterprises to detect.
SpyCloud uses recaptured malware data to level the playing field, alerting enterprises when employees’ web sessions have been compromised so they can invalidate active sessions and lock out bad actors – including when an employee logs into your corporate SSO provider from an infected personal device.
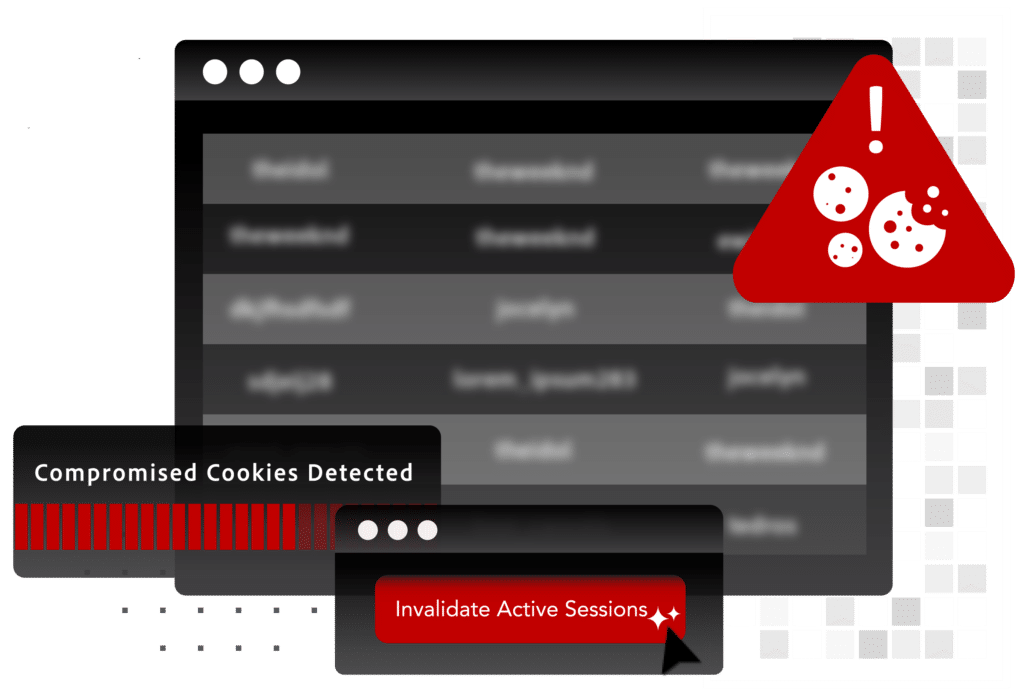
Stop more ATO using data no other provider has
No other provider leverages recaptured malware data for account takeover prevention the way SpyCloud does.
Using recaptured data from SpyCloud, enterprises can:
- Protect high value accounts from bad actors using stolen cookies to mimic trusted devices and sidestep MFA
- Invalidate active sessions identified by a compromised cookie
- Flag vulnerable accounts with known compromised devices for increased scrutiny of future logins/access (regardless of cookie expiration time)
SpyCloud Session Identity Protection for Employees FAQs
Session hijacking occurs when a user’s web session is taken over by an attacker. When you log into a site or application, the server sets a temporary session cookie in your browser. This lets the application remember that you’re logged in and authenticated. Some cookies may last only 24-48 hours, while others last for months.
Leveraging malware-siphoned web and device session cookies, bad actors can perpetrate session hijacking which bypasses the need for credentials (username + password combo), multi-factor authentication (MFA) and even passkeys altogether. Session hijacking is an increasingly prevalent precursor to fraud, and even more frightening to the enterprise, ransomware attacks.
Easily (unfortunately).
Step 1: Trick user into clicking on a dangerous link or downloading a malicious attachment to infect their device with malware.
Step 2: The malware siphons all manner of data from the infected device, including credentials, autofill info, and web session cookies without the user being aware of the infection.
Step 3: The criminal can then use a stolen session cookie to authenticate as the user – without the need for a username and password – bypassing security and fraud controls including MFA.
Typically criminals gain access to session cookies by one of two ways: either by deploying malware directly onto a user’s device, or by buying or trading botnet logs on the darknet. Once a criminal acquires the stolen web session cookies, it is scary how quickly and easily they launch account takeover attacks on both personal and work accounts, and then the possibilities of what they can do are endless, and just as shocking. With cookies from corporate applications – even third-party applications like SSO and VPN – criminals can impersonate the employee, gain access to private information, and change access privileges to move throughout the organization with ease.
It is critical that organizations proactively prevent session hijacking because not only does it make you vulnerable to account takeover, it is also an easy way for criminals to launch a ransomware attack from inside the corporate network or a critical workforce service (including SSO). Once criminals have access to corporate applications, they can easily move laterally throughout the organization disguised as a legitimate user and attempt to escalate privileges in order to access and encrypt valuable company data.
An employee with poor cyber habits who clicks on a malicious link or downloads a suspicious document and gets infected with an infostealer – aka an unwitting insider threat – is one of the most exploitable entry points for ransomware.
SpyCloud’s recent survey of more than 300 security leaders revealed that major ransomware attacks in the last two years have heightened malware concerns, causing organizations to further bolster their security framework with additional layers. Solutions that have not been highly considered before, such as monitoring for compromised web sessions, are now among the top countermeasures planned for investment. This suggests that organizations are looking to extend protection to other areas as threat actors, confronted with the more traditional defenses, shift their focus to other vulnerabilities that are less often or less thoroughly protected.
For enterprises, the best way to prevent session hijacking is by understanding what it is and how it’s executed, monitoring for stolen web sessions programmatically, and developing a process to invalidate web sessions related to infected users. Reacting quickly ensures criminals stay locked out and prevents them from reaping the benefits of malicious activity.
Since web sessions can be valid for a couple of days or even a couple of months, having early insights about malware-compromised sessions can help organizations act quickly to thwart session hijacking.
You might like:

2024 Annual Identity Exposure Report
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.

Malware-Infected User Response Guide
Handy guide to decipher what it means when employee or consumer information appears on a botnet log, and how to contact infected users with an action plan.
MFA Bypass 101
Understand how hackers combine attack methods and stolen credentials to sidestep multi-factor authentication.

Passwordless May Be The Future, But Is It a Cure-All?
Passwordless authentication feels like all the rage these days but it doesn’t come without its own challenges.
Ready to combat session hijacking?
Explore the benefits of Session Identity Protection in a demo today
