SpyCloud Blog
Breaking down identity threats & prevention strategies
Sign up to get the latest cybercrime research, insights, and best practices in your inbox
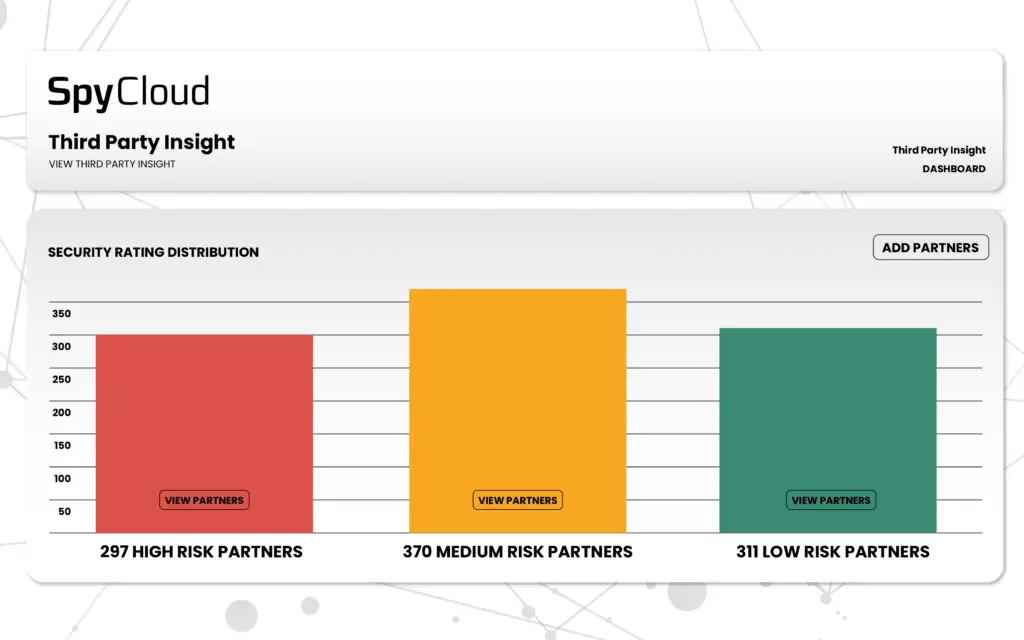
SpyCloud now gives your teams continuous, evidence-based visibility into the identity exposures affecting third-party partners & vendors in your ecosystem.
Compare the top third-party risk management platforms in 2026 and learn why identity exposure visibility is critical to supply chain security.
SpyCloud’s updated list of cybersecurity statistics highlights the most common types of cyberattacks, along with how to protect employees, vendors, & consumers.
New Year, new threats. See what’s stirring in the criminal underground this month, and read up on concerning malware attack chains that could be putting your org at risk.
Chinese-speaking cybercriminals have developed scams, fraud, malware, and money laundering schemes tied to the Lunar New Year red envelope tradition.
Cybercriminals are posting stolen credit card info & sensitive personal data on the Threads platform. Read the SpyCloud Labs analysis & get recommendations to prevent financial fraud.
SpyCloud has released a new Compromised Credit Card API – allowing credit card, gift card, & loyalty issuers to automatically monitor and detect exposed card numbers.
We dug into the ripple effects of Operation Endgame's takedown of the Rhadamanthys stealer, including rumors of its revival & the stealer that's seemingly taken its place.
From big data leaks to cyber underground insights, SpyCloud tracked some of the top threats in 2024. Read our recap & 2025 predictions.
Account opening fraud is a top-priority concern, especially for financial institutions. Being able to distinguish between legitimate users and fraudsters is critical to Know Your Customer (KYC) requirements.
Criminals are ramping up to take advantage of retailers and customer accounts during peak holiday shopping season. Here’s what to have on your radar.
Scattered LAPSUS$ Hunters weaponizes stolen credentials and session tokens from Salesforce breaches to fuel downstream account takeover attacks – here's how this federated cybercrime group operates and what security teams must do to stop them.
Traditional insider threat detection tools miss identity compromises that happen before criminals enter your network. Discover how dark web monitoring and AI threat detection expose malicious insiders, synthetic identity fraud, and negligent employees before behavioral anomalies surface.
SpyCloud Investigations with AI Insights transforms cyber threat intelligence work by automating identity correlation and threat actor attribution—delivering finished intelligence in seconds instead of hours of manual analysis.
The YYlaiyu phishing-as-a-service (PhaaS) panel is just one example of how the Chinese phishing ecosystem is fueling Western financial fraud. Read our analysis.
Use this checklist for optimizing your insider threat program. Learn how to integrate identity intelligence from SpyCloud for full-spectrum protection.
As Cybersecurity Awareness Month kicks off and everything starts to get pumpkin spice flavored, the cybercrime continues. See what the big news is in cyber this month, as well as new research from our team.
Crypters hide malicious payloads. See what we found when we analyzed Asgard Protector, a malware crypter recommended by the sellers of LummaC2.
SpyCloud has released a new & improved version of Active Directory Guardian that identifies more exposed employee passwords and resets exposed passwords automatically.
Get insights from SpyCloud’s latest insider threat report. Learn what 100 CISOs say about their biggest insider risk challenges in 2025.
The 2025 SpyCloud Identity Threat Report reveals a dangerous paradox. Read the report recap for a summary of findings, trends, and key benchmarks.
From the BreachForums takedown to Warlock ransomware, ShinyHunters chaos & GenAI malware, our August update covers the month’s top cybercrime news.
Traditional tools miss identity-driven insider threats. Learn how SpyCloud’s insider threat detection solution uncovers risks before it’s too late.
SpyCloud's continuous delivery model processes breach data in 2 hours, malware in 1 hour – giving cybersecurity teams the speed to detect and remediate threats before attackers weaponize stolen data.
From the XSS forum takedown to the Tea app data leak & Tycoon 2FA attacks, our July cybercrime update breaks down the biggest threats and news.
SpyCloud analyzed 150K stolen credentials from Tycoon 2FA phishing attacks. See what the data reveals about targeted victims.
SpyCloud Investigations customers now get access to AI Insights, rich source context & flexible graphing for a faster and more valuable analyst experience.
We analyzed 1 billion leaked Chinese national ID numbers from the 2022 Shanghai National Police database breach – this is what we found.
IBM’s 2025 Cost of a Data Breach Report is here and identity threats take center stage. See what’s shaping breach costs, attack trends, and security priorities for the year ahead.
From the “16 billion passwords” leak to trends in the Chinese criminal underground, our June cybercrime update breaks down the biggest cyber threats and news.
SpyCloud Labs analyzes sample data from the VenusTech and Salt Typhoon data leaks as well as overall trends in the Chinese cybercriminal underground.
With over 4 billion records, it’s being dubbed the biggest leak of Chinese personal data ever. Here's what to know.
From the LummaC2 takedown to the BreachForums void, our May cybercrime update breaks down the biggest cyber threats & news.
ULP combolists often contain fresh infostealer data. Here’s what to know about ULP combolists, including how to defend your organization from credential theft & attacks.
From the Twitter/X breach to Atomic macOS Stealer infection trends, our April cybercrime update breaks down the biggest cyber threats and news.
Explore key takeaways from the 2025 Verizon DBIR. See how identity threats, ransomware, and third-party risks impact your defenses.
See how malware infection logs can help organizations spot fake North Korean IT workers engaging in employment fraud.
Scattered LAPSUS$ Hunters weaponizes stolen credentials and session tokens from Salesforce breaches to fuel downstream account takeover attacks – here's how this federated cybercrime group operates and what security teams must do to stop them.
We analyzed the nearly 200K leaked Black Basta chats and this is what we learned about their use of exposed credentials for ransomware operations.
Detect and remediate infostealer malware with SpyCloud’s EDR malware detection integrations, powering SOC teams with high-fidelity alerts for rapid response.
A deep dive into March’s cybercrime trends, including GhostSocks, North Korean IT workers, and pesky smishing campaigns.
LummaC2’s link to GhostSocks reveals stealthy proxy access, long-term persistence, and advanced evasion—posing a serious threat to enterprise defenses.
Uncover the latest identity security threats in the 2025 Identity Exposure Report. Learn how cybercriminals are exploiting stolen data and what you can do to stop them.
Redefining threat protection is crucial as attackers weaponize stolen identities. In this blog, learn how to go beyond user accounts to secure today’s expanding identity perimeter and reduce risk.
Cybercriminals target government agencies to steal credentials and sensitive data. Learn five essential identity protection strategies to defend against cyber threats.
Discover the biggest wins from 2024 against cybercrime—from major infostealer takedowns to global ransomware crackdowns—and what they mean for the future of cybersecurity.
Headline-making breaches in 2024 exposed millions of records, compromising sensitive data. This blog explores what was stolen and the impact that has on security strategies to stay ahead.
A deep dive into February’s cybercrime trends, including Black Basta ransomware insights, stolen credit card databases, and the latest threat actor activities.
Bad actors use phishing gateway pages to screen and validate stolen data. Learn how they work and how to protect yourself from these attacks.
The end of 2024 and start to 2025 had no shortage of cyber security hot topics to cover. Dig into our latest findings and insights in this blog.
The cybercrime industry today features specialists who offer cybercrime enablement services for anything a criminal doesn’t want to do – or can’t do – themselves. Learn more.
Phishing campaigns continue to rise in popularity and effectiveness for cybercriminals. Here’s a breakdown of how it works and what.
Discover how LummaC2 has evolved with new stealth tactics, enhanced theft capabilities & novel evasion techniques in our latest SpyCloud Labs analysis.
This month, we’re breaking down the latest in cyber – from hot topics like Telegram, Operation Magnus, LockBit, and the arrest of USDoD to new research from SpyCloud Labs.
Explore SpyCloud's revamped Enterprise Protection Dashboard, offering security teams powerful visibility and tools to combat identity threats.
Legacy infostealer malware like Redline Stealer & Raccoon Stealer are still fueling cybercrime and threatening organizations. Here’s how to stay protected.
Learn about the TTPs China-based threat actors refer to as SDK & DPI, as well as SGKs, which house exfiltrated data about Chinese residents.
The impacts of account takeover can affect your customer base and business long into the future, which is why prevention is so key. Here’s how SpyCloud helps organizations reduce ATO fraud.
SpyCloud Investigations with IDLink analytics is the ultimate force multiplier for analysts. See what’s possible and get a demo today.
The MC2 data breach contains extensive PII on customers and individuals who had their backgrounds screened with the service. Here’s what to know about the leak.
SpyCloud integrates with popular SOAR platforms so you can better detect, respond to, and remediate compromised employee identities. See how.
See how cybercriminals are bypassing Google Chrome’s App-Bound Encryption feature with infostealer malware to steal session cookies that can be used in session hijacking attacks.
Learn essential ransomware prevention tips for businesses, including how you can use SpyCloud to better protect your data.
Explore SpyCloud’s 2024 report on ransomware and malware exposure, and learn how security teams can turn the tide with next-gen defense strategies.
In this article, we dig into the alarming rise of mobile malware and what organizations can do to prevent and combat this growing threat.
SpyCloud Labs dissects the capabilities of the open source Phemedrone Stealer, including log encryption, configuration & victim targeting.
The National Public Data (NPD) breach includes nearly 2.7 billion leaked records – and hundreds of millions of Americans’ social security numbers. Here’s what to know.
The cost of a data breach rose again this year. Get the key findings from IBM’s Cost of a Data Breach Report 2024.
SpyCloud Labs digs into new infostealer malware variants like Kemicat and Mephedrone, as well as the resurgence of keyloggers like Snake.
Discover how your team can accelerate threat actor attribution with SpyCloud Investigations.
Infostealer malware specializes at slipping through the cracks. This new approach to malware remediation evens the playing field.
Learn how SpyCloud responsibly discloses breached, leaked & stolen data to victim organizations as part of our mission to make the internet safer.
SpyCloud breaks down key points from the Verizon 2024 Data Breach Investigations Report. ✓ Read our recap of the highlights.
Here we break down two phases of the MITRE ATT&CK Framework – Reconnaissance and Resource Development – and why it’s critical to account for stolen data in your detection and attack prevention strategies.
SpyCloud Labs reverse-engineered Atomic macOS Stealer to get a better understanding of its current capabilities and the threat it poses to the security community. Here’s our analysis.
Here's what we found when we analyzed The Post Millennial data breach, including the types of exposed data assets contained in the 87 million leaked records.
Scattered LAPSUS$ Hunters weaponizes stolen credentials and session tokens from Salesforce breaches to fuel downstream account takeover attacks – here's how this federated cybercrime group operates and what security teams must do to stop them.
See how cybercriminals are bypassing Google Chrome’s App-Bound Encryption feature with infostealer malware to steal session cookies that can be used in session hijacking attacks.
Google announced a new feature called Device Bound Security Credentials (DBSC) for Chrome. Learn how it affects cookie theft and session hijacking.
SpyCloud researchers break down the risk combolists provide to enterprises and security teams combating stolen credentials and how cybercriminals are still leveraging this age-old tactic.
With the shift from passwords to passkeys, security posture stands a chance at optimization. But it's still susceptible to compromise. We examine how.
Passwordless authentication feels like all the rage these days but it doesn’t come without its own challenges.
We explore two-factor authentication (2FA) and multi-factor authentication (MFA) and why these added layers of security are critical to protecting your organization.
Our survey of IT security leaders found organizations are investing in layers of defense against authentication-based attacks, but it still isn’t enough. Here we discuss the issues with passwords, passkeys, and MFA + additional steps beyond these measures security teams can take to close the gaps in their defenses.
Session cookies siphoned from unmanaged devices infected with malware pose a significant threat to enterprises. Learn how criminals use stolen web session cookies to access enterprises and launch cyberattacks.
The problem of password reuse demands a new framework for credential security – one in which users are blocked from choosing passwords that have ever been exposed.
With stolen credentials being the #1 entry point for cybercriminals, password security has never been more critical. We offer five tips for stronger passwords for users and enterprises alike.
The latest version of PCI DSS standards feature more robust requirements for passwords and authentication. We break down some of the requirements and how they could impact your organization.
We'd like to believe that passwords are just a hop-skip-jump away from being obsolete but the truth is, we're still not quite ready for a passwordless world.
Increased adoption of MFA is a good thing for cybersecurity, especially as remote work grows in popularity – and preference – but humans remain the weakest link.
Ransomware has reached crisis levels across all business sectors and across the globe. What's fueling it? Two words: stolen credentials.
MFA keeping you up at night? It probably should. Check out these common MFA bypass techniques and why another layer of account protection is necessary.
Many years’ worth of accumulated best practices have mostly helped strengthen Active Directory security, but a few long-standing beliefs about enforcing password policies are actually outdated.
Understand MFA implementation and adoption challenges and learn steps you can take to strengthen its effectiveness.
Credential stuffing attacks are on the rise. Learn more about how they’re done and what you can do to protect your organization.
Old exposed passwords can do harm long after the initial compromise. Learn why you should be looking at old data, too.
Think your account takeover prevention strategies give you 100% protection? We’ll show you why you should be skeptical.
Compare the top third-party risk management platforms in 2026 and learn why identity exposure visibility is critical to supply chain security.
Traditional insider threat detection tools miss identity compromises that happen before criminals enter your network. Discover how dark web monitoring and AI threat detection expose malicious insiders, synthetic identity fraud, and negligent employees before behavioral anomalies surface.
Use this checklist for optimizing your insider threat program. Learn how to integrate identity intelligence from SpyCloud for full-spectrum protection.
Traditional tools miss identity-driven insider threats. Learn how SpyCloud’s insider threat detection solution uncovers risks before it’s too late.
Scattered LAPSUS$ Hunters weaponizes stolen credentials and session tokens from Salesforce breaches to fuel downstream account takeover attacks – here's how this federated cybercrime group operates and what security teams must do to stop them.
The impacts of account takeover can affect your customer base and business long into the future, which is why prevention is so key. Here’s how SpyCloud helps organizations reduce ATO fraud.
SpyCloud integrates with popular SOAR platforms so you can better detect, respond to, and remediate compromised employee identities. See how.
Your Zero Trust policy engine is only as good as the data it receives. Find out how to best fuel it to achieve Continuous Zero Trust.
Scattered LAPSUS$ Hunters weaponizes stolen credentials and session tokens from Salesforce breaches to fuel downstream account takeover attacks – here's how this federated cybercrime group operates and what security teams must do to stop them.
The SOC plays a crucial role in protecting employee identities and access to corporate data – but to do so they must overcome these common obstacles.
As threat actors pivot to next-gen tactics, traditional threat intelligence alone isn’t sufficient for safeguarding your critical assets and data.
Key tenets of the government’s zero trust strategy include MFA and secure password policies. With identity at the core of zero trust, we offer recommendations for successful strategy implementation.
When you’re alerted that your password was included in a data breach, what can you do to protect your accounts? Learn the implications of exposed credentials and 4 steps to exposed passwords.
With stolen credentials being the #1 entry point for cybercriminals, password security has never been more critical. We offer five tips for stronger passwords for users and enterprises alike.
We dig into key findings from our annual survey of more than 300 security leaders, including the role malware plays in ransomware attacks and the missing piece of incident response.
The start of a new school year is the perfect time to freshen up on cybersecurity awareness. We offer insights on cyberattacks and breaches targeted at children and four back-to-school security tips.
A survey of CISOs found key insights on challenges facing top security leaders, including protecting against ransomware, implementing Zero Trust models, and the need for automated solutions.
The stakes are high when it comes to protecting critical infrastructure. See the latest thinking on thwarting ransomware attacks against Utilities – and the ATO that often precedes them.
The latest version of PCI DSS standards feature more robust requirements for passwords and authentication. We break down some of the requirements and how they could impact your organization.
Leaders in fraud prevention share insights and experiences about how fraud teams enable revenue and foster collaboration from our MRC 2022 panel discussion.
Stolen data helps criminals sidestep fraud prevention measures. Now, SpyCloud can help enterprises use that same data to stop hard-to-detect fraud.
For years, criminals have stolen and exploited consumers' personal data. It’s time we make that same data work for us in the fight to prevent fraud.
Enterprise leaders and boards of directors are constantly juggling the multitude of responsibilities they have to the business. Our CEO, Ted Ross, explains why cybersecurity should be at the top of the list.
We'd like to believe that passwords are just a hop-skip-jump away from being obsolete but the truth is, we're still not quite ready for a passwordless world.
In an interconnected business world where organizations depend on hundreds of separate technologies and vendors, third-party access offers a reliably weak spot in any security posture.
Questions to ask yourself as you prepare breach prevention & response plans, based on our conversations with CISOs who have survived major breaches that exposed customer data.
The cost of a data breach in the healthcare industry is now at an all-time high: $7.13M. Roy Mellinger, former Anthem CISO, shares his perspective & lessons learned from their 2015 breach – takeaways that are relevant for security leaders from all industries.
To commemorate National Cybersecurity Awareness month, we’re sharing 9 practical tips from enterprise CISOs on how to increase participation in security awareness programs.
According to a recent study, many security leaders are focused on the wrong risks. Account takeover is a primary risk that deserves more attention.
BYOD has its benefits, but it can also have serious implications. Learn how to defend your organization from the risks.
Corporate account takeover is growing at an alarming rate. Find out what you should and shouldn’t do to prevent it.
As CISO, your job may keep you up at night worrying about your employees’ and customers’ leaked credentials. There’s plenty to worry about, but you can take proactive steps to find more restful sleep.
What Is ATO and Why Should You Care? Because of widespread password reuse, Account Takeover (ATO) attacks have become an extremely lucrative business for cybercriminals.
SpyCloud’s updated list of cybersecurity statistics highlights the most common types of cyberattacks, along with how to protect employees, vendors, & consumers.
Account opening fraud is a top-priority concern, especially for financial institutions. Being able to distinguish between legitimate users and fraudsters is critical to Know Your Customer (KYC) requirements.
Criminals are ramping up to take advantage of retailers and customer accounts during peak holiday shopping season. Here’s what to have on your radar.
The 2025 SpyCloud Identity Threat Report reveals a dangerous paradox. Read the report recap for a summary of findings, trends, and key benchmarks.
See how malware infection logs can help organizations spot fake North Korean IT workers engaging in employment fraud.
Uncover the latest identity security threats in the 2025 Identity Exposure Report. Learn how cybercriminals are exploiting stolen data and what you can do to stop them.
Redefining threat protection is crucial as attackers weaponize stolen identities. In this blog, learn how to go beyond user accounts to secure today’s expanding identity perimeter and reduce risk.
Headline-making breaches in 2024 exposed millions of records, compromising sensitive data. This blog explores what was stolen and the impact that has on security strategies to stay ahead.
Phishing campaigns continue to rise in popularity and effectiveness for cybercriminals. Here’s a breakdown of how it works and what.
The impacts of account takeover can affect your customer base and business long into the future, which is why prevention is so key. Here’s how SpyCloud helps organizations reduce ATO fraud.
Here we break down two phases of the MITRE ATT&CK Framework – Reconnaissance and Resource Development – and why it’s critical to account for stolen data in your detection and attack prevention strategies.
As threat actors pivot to next-gen tactics, traditional threat intelligence alone isn’t sufficient for safeguarding your critical assets and data.
SpyCloud Third Party Insight helps you prevent account takeover by monitoring your supply chain for breach and malware exposures and sharing that data to aid remediation efforts.
Our team was busy on the floor at Black Hat 2023, but we also had some time to attend sessions and talk industry with colleagues and friends. Here's what we’re taking away from one of cybersecurity’s best events.
We uncovered a lot in feedback sessions with CISOs, so we offer even more insights around evolving authentication methods and ransomware defense vs. offense in the second blog in our series.
In ongoing conversations with CISOs, several topics stood out as top-of-mind for security leaders. We discuss their emerging concerns, including malware infection response and critical SOC team blind spots.
Despite being one of the oldest tricks in the cybercrime playbook, BEC scams continue to pose a significant threat to organizations, causing 64 times more losses than ransomware last year.
A passwordless world is not one without cyberattacks. Session hijacking is one example that defeats passkeys. We examine its growing popularity.
RSAC’s 2023 theme of Stronger Together rang true throughout the event, with discussions on how to tackle and safely evolve AI’s impact on cybersecurity, third-party risk management, and the path forward for the industry.
Bad actors can target your organization in all sorts of ways. Read on for some of the most common types of cyberattacks that should be on your organization’s radar.
Stolen credentials and malware infections put DIB suppliers at risk for account takeover and ransomware attacks. These organizations must take measures to secure credentials and meet CMMC requirements.
Our resident security research expert discusses malware trends – including why we’re finding screenshots of victims’ desktops among the exfiltrated data.
Unwitting insider threats create vulnerabilities that can lead to ransomware attacks. We discuss how ghost accounts and shadow IT impact enterprises and how to mitigate these risks.
An analysis of the newly launched underground carding marketplace data against SpyCloud’s recaptured data shows the leaked information existed on the dark web prior to its recent disclosure - but does that make it any less powerful in the hands of a criminal?
Fraud experts from SpyCloud and Aite-Novarica tackle recent trends, the rise in ATO, synthetic identities, and malware, and how to level the playing field against fraudsters.
The stakes are high when it comes to protecting critical infrastructure. See the latest thinking on thwarting ransomware attacks against Utilities – and the ATO that often precedes them.
Synthetic identity fraud is a $20B problem, but it's not impossible to prevent. We break down the 2 telltale signs. As it turns out, too much information is just as suspicious as not enough when it comes to detecting constructed identities.
When your password is exposed in a data breach, immediate action is necessary. We offer remediation steps and tips for creating strong passwords to secure online accounts.
Criminals are going omni-channel with Organized Retail Crime. Learn more about this type of fraud and see how the digital and physical worlds can collide to solve ORC cases.
The SpyCloud Research team takes an in-depth look at anti-detect browsers and how they are being leveraged alongside stolen credentials and cookies to bypass MFA and easily log into targeted accounts.
As online shopping continues to boom, both consumers and retailers should be aware of triangulation fraud. Learn more about this tactic, how it works, and how you (and your business) can avoid getting caught up in it.
In an interconnected business world where organizations depend on hundreds of separate technologies and vendors, third-party access offers a reliably weak spot in any security posture.
A look back at the threat landscape that experts were predicting over the last five years to see how the industry has changed – and what could be ahead.
Cybercrime and cybersecurity budgets are both on the rise. And yet, the largest security gaps for most organizations – solving for password reuse and remediating stolen credentials - are left wide open.
When it comes to identity theft, stolen phone numbers are often shrugged off. But the truth is, criminals want your phone numbers just as much as they want your passwords.
Telecom companies are rich in data and have huge numbers of customers, both of which make them valuable targets for fraudsters. They're also heavily exposed in data breaches.
We've noticed a trend where media headlines equate data breaches & credential stuffing. The difference is critical for companies like Zoom, Nintendo, and Spotify, who made headlines in 2020 for the wrong reasons & suffered brand damage as a result.
Human nature makes us vulnerable to account takeover. Let’s dig into 3 very common bad habits and how they play into criminals’ hands.
Dictionaries, combolists, rainbow tables...We explain the terms used within online “cracking communities” and what they mean for us as defenders.
Business email compromise (BEC), has been used to defraud businesses out of over $3 billion. Know what to look for in these types of scams.
Dig into the differences between these two common attack types, and how you can prevent account takeovers that stem from either one.
Here’s what you need to know about popular cracking tools including Vertex, Sentry MBA, SNIPR, and OpenBullet, along with custom and target-specific account checkers – plus how you can protect your users and yourself from attacks.
Displaced darknet communities have found a new home on Discord. See what's being sold and traded – and learn what to do if you happen to come across these activities.
Since early April, attackers have compromised 160,000 Nintendo accounts. SpyCloud researchers have identified source code for an account checker tool that was custom-built to target Nintendo customers.
Shedding light on mobile threats as well as potential solutions including mobile threat defense, zero trust frameworks, and account takeover prevention measures.
The largest dark markets may have been seized, but they always seem to persist. Fortunately, they’re run by humans and humans make mistakes.
Our survey of IT security leaders found organizations are investing in layers of defense against authentication-based attacks, but it still isn’t enough. Here we discuss the issues with passwords, passkeys, and MFA + additional steps beyond these measures security teams can take to close the gaps in their defenses.
Weak or reused passwords still pose a huge risk factor for account takeover but as newer authentication techniques evolve, criminals are adapting.
Credential stuffing attacks are on the rise. Learn more about how they’re done and what you can do to protect your organization.
Corporate account takeover is growing at an alarming rate. Find out what you should and shouldn’t do to prevent it.
Do you ever wonder how the dark web works? Do you know what tools provide protection from what can happen in the dark web? We’ll break it down.
New markets on the dark web represent a shift in how underground goods are bought and sold. What does history have to say about how new markets will fare?
Legacy infostealer malware like Redline Stealer & Raccoon Stealer are still fueling cybercrime and threatening organizations. Here’s how to stay protected.
In this article, we dig into the alarming rise of mobile malware and what organizations can do to prevent and combat this growing threat.
Infostealer malware specializes at slipping through the cracks. This new approach to malware remediation evens the playing field.
As threats from malware infections slip through security defenses, a new approach to preventing ransomware is necessary. With SpyCloud Compass, security teams can now conduct complete Post-Infection Remediation.
Get the lowdown on botnets, networks of computers infected by malware. See why they're dangerous and how to protect yourself.
Find out what makes infostealer malware a unique threat, and how SOC teams should adjust traditional approaches to fully address the risk it poses.
Key findings and insights from over 300 security & IT leaders and practitioners surveyed by SpyCloud regarding the growing threat of infostealer malware and what companies are missing when it comes to remediation.
The dark web is crawling with compromised credentials and cookies from the largest companies in the US and UK. We cover takeaways from our reports on the Identity Exposure of the Fortune 1000 and FTSE 100.
As malware attempts reach staggering heights, we dive into infostealer malware, including how it executes, the risks it poses, and how it can lead to follow-on attacks like ransomware.
Our resident security research expert discusses malware trends – including why we’re finding screenshots of victims’ desktops among the exfiltrated data.
This year’s report focuses on the growing risk of malware infections. With half of the exposed credentials coming from botnet logs, our recaptured data shows a shift in cybercriminal trends.
Data stolen from consumers’ malware-infected devices fuels account takeover and online fraud. Knowing what criminals know about your customers is the first step in protecting them and your bottom line.
We break down the steps that enable the shift from a machine-focused approach to malware infection response to an identity-focused approach that truly reduces the enterprise’s risk of ransomware.
While money is a common and obvious motivation for malware campaigns, we examine various motivating factors behind malware, including hacktivism and notoriety.
Botnets are one of the tools that enable bad actors to carry out extensive infostealer attacks. We discuss the risks of botnets, infostealers, and malware infections, and how to close ransomware visibility gaps.
Session cookies siphoned from unmanaged devices infected with malware pose a significant threat to enterprises. Learn how criminals use stolen web session cookies to access enterprises and launch cyberattacks.
One of the biggest challenges in ransomware prevention is the lack of visibility into credential-stealing malware. Get insights on how these infections work and why malware causes headaches for SOC teams.
Learn essential ransomware prevention tips for businesses, including how you can use SpyCloud to better protect your data.
Explore SpyCloud’s 2024 report on ransomware and malware exposure, and learn how security teams can turn the tide with next-gen defense strategies.
Read highlights from the 2023 SpyCloud Ransomware Report, including attack precursors, frequency, and costs affecting security teams & organizations.
The cost of a ransomware attack isn’t just a payment - negative brand reputation and loss of customers can hurt the bottom line, while employees mitigating an attack can impact productivity.
As malware attempts reach staggering heights, we dive into infostealer malware, including how it executes, the risks it poses, and how it can lead to follow-on attacks like ransomware.
Ransomware has been a growing cyber threat for several years but with increased sophistication and methods it seems like 2022 was really the year it took off. Here we break down the trends and ways organizations can better prepare in 2023 and beyond!
Monetizing network access is not a new scheme, but the emergence of Ransomware-as-a-Service (RaaS) operators has created a market for specialized actors called Initial Access Brokers (IABs).
We dig into key findings from our annual survey of more than 300 security leaders, including the role malware plays in ransomware attacks and the missing piece of incident response.
Understanding ransomware entry points is critical to preventing attacks in the first place. We examine three common access points for ransomware and discuss how to close gaps in your prevention strategy.
A summary of key findings from 250 U.S. Enterprise Security Leaders about the state of Ransomware Defense. Spoiler Alert: It's not all bad news.
Poor cybersecurity hygiene has made colleges & universities prime targets for ransomware. How can these institutions make security an educational priority?
As the U.S. federal government addresses the ransomware scourge, state and local governments are left unprepared and caught in the crosshairs.
Ransomware has reached crisis levels across all business sectors and across the globe. What's fueling it? Two words: stolen credentials.
Ransomware attacks against local governments and utilities continue to pile up, and hackers are putting pressure on victims by threatening to leak data to the public domain.
Get insights from SpyCloud’s latest insider threat report. Learn what 100 CISOs say about their biggest insider risk challenges in 2025.
IBM’s 2025 Cost of a Data Breach Report is here and identity threats take center stage. See what’s shaping breach costs, attack trends, and security priorities for the year ahead.
Explore key takeaways from the 2025 Verizon DBIR. See how identity threats, ransomware, and third-party risks impact your defenses.
See how malware infection logs can help organizations spot fake North Korean IT workers engaging in employment fraud.
Cybercriminals target government agencies to steal credentials and sensitive data. Learn five essential identity protection strategies to defend against cyber threats.
Discover the biggest wins from 2024 against cybercrime—from major infostealer takedowns to global ransomware crackdowns—and what they mean for the future of cybersecurity.
The cost of a data breach rose again this year. Get the key findings from IBM’s Cost of a Data Breach Report 2024.
SpyCloud breaks down key points from the Verizon 2024 Data Breach Investigations Report. ✓ Read our recap of the highlights.
Here's what we found when we analyzed The Post Millennial data breach, including the types of exposed data assets contained in the 87 million leaked records.
Our 2024 Identity Exposure Report showcases just how big the stolen data problem is today. Here’s what we learned in our annual analysis of recaptured breach & malware data from the darknet.
Learn about the MOAB data leak and find out how much of the exposed data is already known, public, or outdated per SpyCloud Labs research.
The cost of a data breach keeps rising but there are concrete approaches for mitigating costs that work. Read the key findings from this year's IBM report.
Key Takeaways from the Verizon 2023 Data Breach Investigations Report: A Look Back and A Way Forward
New year, same story: Credentials are king, ransomware is rampant, and human error prevails. We dig into the Verizon 2023 Data Breach Investigations Report and shed some light on what the future holds.
We were able to tie more than 412 million breach assets within the SpyCloud database to employees within the Fortune 1000, providing a snapshot of the breach exposure affecting major enterprises.
New Year, new threats. See what’s stirring in the criminal underground this month, and read up on concerning malware attack chains that could be putting your org at risk.
Chinese-speaking cybercriminals have developed scams, fraud, malware, and money laundering schemes tied to the Lunar New Year red envelope tradition.
Cybercriminals are posting stolen credit card info & sensitive personal data on the Threads platform. Read the SpyCloud Labs analysis & get recommendations to prevent financial fraud.
We dug into the ripple effects of Operation Endgame's takedown of the Rhadamanthys stealer, including rumors of its revival & the stealer that's seemingly taken its place.
From big data leaks to cyber underground insights, SpyCloud tracked some of the top threats in 2024. Read our recap & 2025 predictions.
Scattered LAPSUS$ Hunters weaponizes stolen credentials and session tokens from Salesforce breaches to fuel downstream account takeover attacks – here's how this federated cybercrime group operates and what security teams must do to stop them.
The YYlaiyu phishing-as-a-service (PhaaS) panel is just one example of how the Chinese phishing ecosystem is fueling Western financial fraud. Read our analysis.
As Cybersecurity Awareness Month kicks off and everything starts to get pumpkin spice flavored, the cybercrime continues. See what the big news is in cyber this month, as well as new research from our team.
Crypters hide malicious payloads. See what we found when we analyzed Asgard Protector, a malware crypter recommended by the sellers of LummaC2.
From the BreachForums takedown to Warlock ransomware, ShinyHunters chaos & GenAI malware, our August update covers the month’s top cybercrime news.
SpyCloud's continuous delivery model processes breach data in 2 hours, malware in 1 hour – giving cybersecurity teams the speed to detect and remediate threats before attackers weaponize stolen data.
From the XSS forum takedown to the Tea app data leak & Tycoon 2FA attacks, our July cybercrime update breaks down the biggest threats and news.
SpyCloud analyzed 150K stolen credentials from Tycoon 2FA phishing attacks. See what the data reveals about targeted victims.
We analyzed 1 billion leaked Chinese national ID numbers from the 2022 Shanghai National Police database breach – this is what we found.
From the “16 billion passwords” leak to trends in the Chinese criminal underground, our June cybercrime update breaks down the biggest cyber threats and news.
SpyCloud Labs analyzes sample data from the VenusTech and Salt Typhoon data leaks as well as overall trends in the Chinese cybercriminal underground.
With over 4 billion records, it’s being dubbed the biggest leak of Chinese personal data ever. Here's what to know.
From the LummaC2 takedown to the BreachForums void, our May cybercrime update breaks down the biggest cyber threats & news.
ULP combolists often contain fresh infostealer data. Here’s what to know about ULP combolists, including how to defend your organization from credential theft & attacks.
From the Twitter/X breach to Atomic macOS Stealer infection trends, our April cybercrime update breaks down the biggest cyber threats and news.
We analyzed the nearly 200K leaked Black Basta chats and this is what we learned about their use of exposed credentials for ransomware operations.
A deep dive into March’s cybercrime trends, including GhostSocks, North Korean IT workers, and pesky smishing campaigns.
LummaC2’s link to GhostSocks reveals stealthy proxy access, long-term persistence, and advanced evasion—posing a serious threat to enterprise defenses.
Discover the biggest wins from 2024 against cybercrime—from major infostealer takedowns to global ransomware crackdowns—and what they mean for the future of cybersecurity.
Headline-making breaches in 2024 exposed millions of records, compromising sensitive data. This blog explores what was stolen and the impact that has on security strategies to stay ahead.
A deep dive into February’s cybercrime trends, including Black Basta ransomware insights, stolen credit card databases, and the latest threat actor activities.
Bad actors use phishing gateway pages to screen and validate stolen data. Learn how they work and how to protect yourself from these attacks.
The end of 2024 and start to 2025 had no shortage of cyber security hot topics to cover. Dig into our latest findings and insights in this blog.
The cybercrime industry today features specialists who offer cybercrime enablement services for anything a criminal doesn’t want to do – or can’t do – themselves. Learn more.
Discover how LummaC2 has evolved with new stealth tactics, enhanced theft capabilities & novel evasion techniques in our latest SpyCloud Labs analysis.
This month, we’re breaking down the latest in cyber – from hot topics like Telegram, Operation Magnus, LockBit, and the arrest of USDoD to new research from SpyCloud Labs.
Legacy infostealer malware like Redline Stealer & Raccoon Stealer are still fueling cybercrime and threatening organizations. Here’s how to stay protected.
Learn about the TTPs China-based threat actors refer to as SDK & DPI, as well as SGKs, which house exfiltrated data about Chinese residents.
The MC2 data breach contains extensive PII on customers and individuals who had their backgrounds screened with the service. Here’s what to know about the leak.
See how cybercriminals are bypassing Google Chrome’s App-Bound Encryption feature with infostealer malware to steal session cookies that can be used in session hijacking attacks.
SpyCloud Labs dissects the capabilities of the open source Phemedrone Stealer, including log encryption, configuration & victim targeting.
The National Public Data (NPD) breach includes nearly 2.7 billion leaked records – and hundreds of millions of Americans’ social security numbers. Here’s what to know.
SpyCloud Labs digs into new infostealer malware variants like Kemicat and Mephedrone, as well as the resurgence of keyloggers like Snake.
Learn how SpyCloud responsibly discloses breached, leaked & stolen data to victim organizations as part of our mission to make the internet safer.
SpyCloud Labs reverse-engineered Atomic macOS Stealer to get a better understanding of its current capabilities and the threat it poses to the security community. Here’s our analysis.
Here's what we found when we analyzed The Post Millennial data breach, including the types of exposed data assets contained in the 87 million leaked records.
We’ve added three new Windows infostealer malware families to our recaptured data repository. Learn about Xehook, Meduza, and Elusive.
Threat actors are using PPI networks to distribute malware families like LummaC2 and Atomic Stealer. Our researchers analyzed one of them – SpaxMedia – and here’s what we found.
SpyCloud Labs research uncovered unique Chinese threat actor TTPs for persistent data access, data acquisition, and data exfiltration.
Learn about the MOAB data leak and find out how much of the exposed data is already known, public, or outdated per SpyCloud Labs research.
SpyCloud Labs researchers uncovered details about a cybercrime traffer team that is responsible for distributing malware families to victims around the globe.
SpyCloud Labs analysts reverse-engineered LummaC2 Stealer and observed notable upgrades and capabilities to its code.
SpyCloud research shows a recent surge in the prevalence of the LummaC2 infostealer, rising 2000% in 6 short months.
The SpyCloud Research team takes an in-depth look at anti-detect browsers and how they are being leveraged alongside stolen credentials and cookies to bypass MFA and easily log into targeted accounts.
SpyCloud has released a new Compromised Credit Card API – allowing credit card, gift card, & loyalty issuers to automatically monitor and detect exposed card numbers.
SpyCloud now gives your teams continuous, evidence-based visibility into the identity exposures affecting third-party partners & vendors in your ecosystem.
SpyCloud Investigations with AI Insights transforms cyber threat intelligence work by automating identity correlation and threat actor attribution—delivering finished intelligence in seconds instead of hours of manual analysis.
SpyCloud has released a new & improved version of Active Directory Guardian that identifies more exposed employee passwords and resets exposed passwords automatically.
SpyCloud Investigations customers now get access to AI Insights, rich source context & flexible graphing for a faster and more valuable analyst experience.
Detect and remediate infostealer malware with SpyCloud’s EDR malware detection integrations, powering SOC teams with high-fidelity alerts for rapid response.
Explore SpyCloud's revamped Enterprise Protection Dashboard, offering security teams powerful visibility and tools to combat identity threats.
SpyCloud Investigations with IDLink analytics is the ultimate force multiplier for analysts. See what’s possible and get a demo today.
Discover how your team can accelerate threat actor attribution with SpyCloud Investigations.
Discover how Canva safeguards its employees with the powerful combination of SpyCloud Cybercrime Analytics and Tines' automated workflows.
SpyCloud’s integration with Cortex XSOAR bridges gaps between identity-related exposure incidents and corresponding incident response and remediation workflows.
What’s it like to actually be a SpyCloud customer? Here’s how we set our customers up for success from day one.
SpyCloud Compass now includes stolen cookie data for malware infections to help you remediate employee exposures.
Your cybercrime investigations just got an easy button: Introducing the new SpyCloud Investigations Portal for easier, fast cyber investigations.
SpyCloud Third Party Insight helps you prevent account takeover by monitoring your supply chain for breach and malware exposures and sharing that data to aid remediation efforts.
The SpyCloud integration with Microsoft Sentinel helps security teams triage and remediate identity-related exposure incidents to prevent targeted account takeover and cyberattacks.
In honor of International Women’s Day during Women’s History Month, female leaders at SpyCloud discuss their careers in technology and offer advice to other women entering the field.
Greater than 950 percent YoY rise in revenue indicates ATO prevention is a high priority for enterprises.
Our development team is constantly pumping out new features, and we’re excited to highlight one that our customers have been asking for: Recent Records Alerts!