The NIS2 Directive, a significant update to the European Union’s cybersecurity legislation, ups cybersecurity requirements for entities within the EU. Building on the original Network and Information Systems (NIS) Directive, NIS2 broadens the scope of sectors considered critical to include the energy, transport, banking, and health sectors, among others.
The new directive mandates stricter security requirements, incident reporting obligations, and introduces heavier penalties for non-compliance. If you’re an organization impacted by NIS2, you know that compliance involves a multi-layered, strategic approach. With SpyCloud, it’s possible to cover a range of NIS2 requirements and see value on day one.
SpyCloud’s solution for identity protection
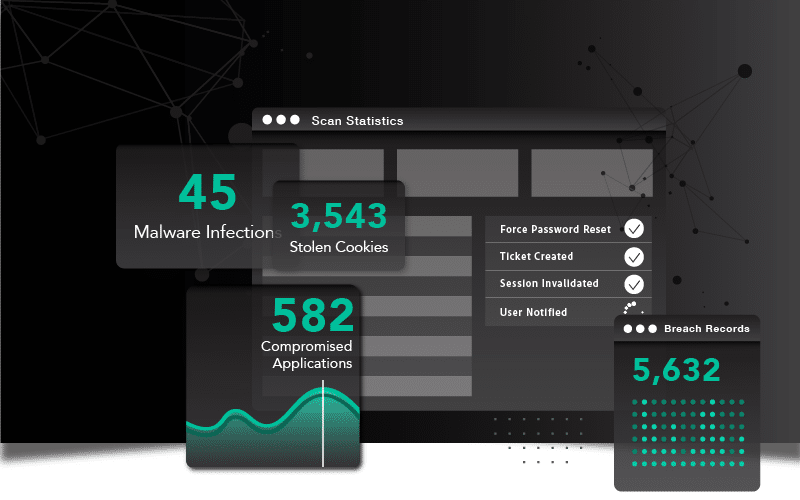
Our mission is to actively protect organizations from targeted identity-centric attacks that rely on cybercrime data being traded on the darknet about the company, its employees, suppliers, and customers. We do it by continuously providing our customers with access to relevant and actionable cybercrime data through products and integrations that enable automated protection from account takeover, data breaches, business email compromise, session hijacking, and ransomware. Our solutions also provide capabilities to detect and respond to infostealer malware infections that have bypassed the organization’s security controls.
Mapping SpyCloud to NIS2 requirements
SpyCloud’s identity protection solutions, powered by Cybercrime Analytics, are a path forward to meeting the requirements of Paragraph 2, Article 21 of the NIS2 Directive – specifically requirements b, d, e, f, i, and j.
For each of the remaining requirements – a, c, g, h – SpyCloud’s alerts support the creation of appropriate policies and/or training.
| Article 21 Section | NIS2 Required Risk Management Measures | SpyCloud provides critical support to entities by: |
|---|---|---|
| 2(b) | incident handling |
|
| 2(d) | supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers |
|
| 2(e) | security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure |
|
| 2(f) | policies and procedures to assess the effectiveness of cybersecurity risk-management measures |
|
| 2(i) | human resources security, access control policies, and asset management |
|
| 2(j) | the use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications and secured emergency communication systems within the entity, where appropriate |
|
Explore SpyCloud’s solutions to support your business’ NIS2 Directive compliance.