What is the LummaC2 infostealer?
LummaC2 is an infostealer believed to be the creation of a Russian threat actor who goes by “Shamel.” It was first observed in the security community around August of 2022 and is offered up to prospective buyers via Telegram and other darknet forums as malware-as-a-service (MaaS).
The seller currently offers buyers three pricing levels: Experienced, Professional, and Corporate, which were most recently advertised at a discount during a subscription sale in August 2023.
The official Telegram channel for LummaC2 boasts over 1,800 members as of the time of writing, and the channel administrator(s) regularly post updates to the malware alongside offers for partner criminal groups offering services – ranging from crypto wallet password guessing to phishing kits for sale. While members of the channel are prohibited from posting, by sampling members’ accounts and cross referencing their user IDs with those found in other channels, we found that many members also participate in Telegram channels that offer tips for conducting financial fraud and deploying infostealer malware (including LummaC2), as well as channels that sell software used to obfuscate malware for the purpose of anti-virus evasion.
A LummaC2 attack: What it can do
Before we get into the data surrounding the recent uptick in recaptured LummaC2 infection records, it’s important to note that the Lumma Stealer introduced several new features that were not previously available in other commodity infostealers.
In our analysis of LummaC2, we’ve seen evidence of local password manager vault exfiltration, stolen config files from remote desktop software including AnyDesk, and even unsuccessful yet fully automated attempts towards exfiltration of browser-based 2FA. These features are in addition to the more historically common traits of infostealing malware, including the ability to exfiltrate local files, steal saved credentials and cookies, and the parsing of local cached browser data like autofills. At as little as $225 a subscription, that’s a lot of features and functionality considering its pricing is on-par with other commodity malware stealers like Raccoon or RedLine.
It’s also important to note that many attacks employ several different malicious programs, each with a different purpose and scope of features. While LummaC2 is dangerous on its own, its combination with other commodity malware and open source tools have been observed as part of numerous successful infection chains, based on our research at SpyCloud.
How LummaC2 works
LummaC2 steals extension data from a variety of Chrome-based browsers including Opera, Brave, Chrome, Chromium, and more. The malware accomplishes this by locating the “Local Extension Settings” for each browser, which stores the internal extension information for many extensions.
While LummaC2 has a large list of targeted extensions that includes 2FA code managing extensions, through our tests, LummaC2 does not actually extract most 2FA code secrets, as these secrets are not stored in “Local Extension Settings” for Chrome browsers. However, LummaC2 does steal passwords and PII stored in extensions for a wide variety of crypto tools. Additionally, as LummaC2 does programmatically decrypt Chrome’s internal .ldb database storage files, LummaC2 could in the future begin extracting 2FA code secrets that are stored locally on a victim’s device, just like passwords or crypto wallets.
From an analysis of logs collected by SpyCloud, we found that LummaC2 also targets remote desktop applications, likely as a means of gaining persistence into a device. LummaC2 logs are helpfully tagged with the configuration hits found in a specific log, such as “[Authenticator]” or applications found on the victim device, such as crypto wallet software, enabling quick identification by the malware deployer similar to how popular checker software changes the log folder names to reflect the types of data available for exploitation.
LummaC2 is actively being maintained by its developer, who most recently released an update in September 2023 promising buyers infrastructure and stability improvements.
Based on our findings and the frequent updates released by the malware authors, it is likely that future versions of LummaC2 will introduce additional features capable of extracting additional sensitive information from victim devices.
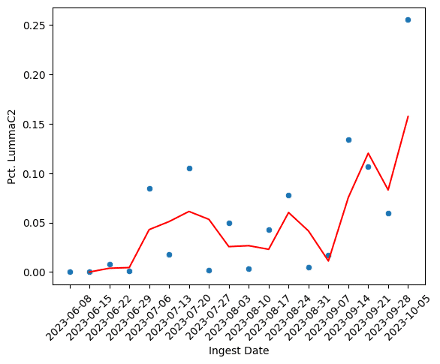
LummaC2 analysis: A look at its exponential growth trend
Over the past six months, we’ve observed a rapid uptick in LummaC2 malware records in the SpyCloud recaptured database. As shown here, the total count of unique LummaC2 malware records went from nearly nonexistent to making up almost a quarter of SpyCloud’s weekly ingest by identified variant – representing a 2000% increase. Topping LummaC2 were only RedLine, Raccoon, and Vidar, with StealC, another full-featured stealer, also gaining popularity during the same time period.
Additionally, we analyzed data exfiltrated by LummaC2 by total size, and found that, on average, a log derived from a successful LummaC2 infection was nearly three times as large as a comparable log from other infostealers. During the period above, logs derived from LummaC2 infections had a median size (including all metadata and exfiltrated files) of 1.13MB, while logs from RedLine, Vidar, and Raccoon, had a median size of 394.77KB.
What does all this mean for security teams?
At this time, we can’t be conclusive on causation for the rise in LummaC2 infection records, but we can say that security teams should be paying extra attention to it as a rising threat.
Because of the amount of information-stealing features and potential scope of impact, we recommend actively monitoring for LummaC2 infections to identify infected employees or customers, and taking the necessary Post-Infection Remediation steps to close potential entry points to your organization.
How to protect your organization: LummaC2 infostealer remediation steps
Once you’ve determined an exposure(s), time is of the essence to remediate siphoned authentication details that can open up access to the applications and data most important to your business. Get guidance on best practices for malware remediation in our Post-Infection Remediation Guide.
SpyCloud alerts security teams each time a malware infection arises on a device accessing your workforce applications. Check your organization’s known exposures today.

