Most security professionals already have a general understanding of Zero Trust concepts, and many organizations have already taken significant steps to implement basic Zero Trust practices. Often these first steps include implementing standard Identity Access Management (IAM) and starting to implement Network and Micro segmentations. Such implementations provide the initial building blocks of a strong overall program.
Unfortunately, organizations often take these initial steps and then lose focus before reaching the level of a Continuous Zero Trust implementation. Implementations that only test the validity of users and devices when they first access the network are leaving their organizations open to significant risk as threats evolve and change.
To reach a sufficient Zero Trust implementation, it’s critical that each user and device be continuously evaluated – and that evaluation has to take into account the full scope of identity, device, and access information criminals have in hand.
So long story short, yes, we think teams should invest in Continuous Zero Trust.
In this blog we’ll cover:
Why security teams need Continuous Zero Trust
At SpyCloud, we are firm believers in Continuous Zero Trust because the nature of modern the threat landscape necessitates it – cybercriminals are constantly working to infiltrate or sidestep our security barriers, and we need to shift our checks and balances accordingly as adversaries pivot their attack TTPs. To do that effectively, you need to continuously monitor and remediate employee identity exposures that can bypass your authentication systems, like MFA and SSO.
In order to properly secure your environment, and adhere to Zero Trust principles, you have to constantly evaluate whether the risk to any of your users and devices has increased. There are many inputs available to support this evaluation, including details like a user’s status within the company, their adherence to security hygiene protocols, or even their current geographic location. That said, the most powerful input is the data that criminals have collected about your users and systems.
If your Zero Trust implementation fails to account for inputs, including darknet telemetry, then you’ve fallen short of adequate protection for your enterprise.
How to define expanded digital identity profiles in your Zero Trust model
Most enterprises define their identities by mapping to a user within their identity provider system, such as Active Directory. While this creates the groundwork for the authentication and authorization of a user, it can be limiting if your definition of an identity does not include a broad enough view of their digital identity.
With the addition of SpyCloud cybercrime telemetry to your Zero Trust policy engine, you can expand the digital identity of each user to include attributes taken from third-party breaches and malware infection – the same sources that threat actors would use to target a specific digital identity.
Building a dynamic policy that responds to this expanded digital identity profile is critical to applying the proper level of authorization to each of your users.
Protecting applications and networks from session hijacking
In your Zero Trust implementation, it’s important to recognize that threat actors have added a new attack vector to their capabilities that allows them to gain access to your applications and networks: hijacking your authenticated sessions.
If an actor can gain access to active session cookies, they can take over your user’s sessions after they have been authenticated, completely bypassing MFA and passkey implementations. Continuous Zero Trust implementations must also consider whether the criminal underground may have gained access to cookies that could be used to emulate an authenticated user.
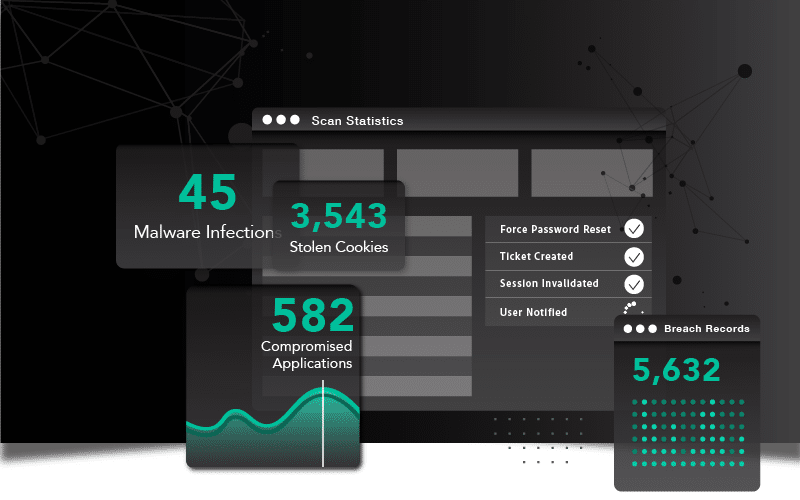
Case in point – SpyCloud recaptured more than 20 billion cookie records in 2023 alone, or an average of about 2,000 per malware-infected device. This indicates that bad actors see the value in leveraging session cookies for next-generation account takeover, and we expect to see this method escalate.
Session hijacking examples
Here are some recent real-world examples of session hijacking that started with an active stolen cookie, giving bad actors access to corporate environments and escalating privileges to launch full-scale attacks:
An employee of a large company synced their corporate and personal Chrome profile. When the employee’s identity was compromised, the bad actor was able to access the employee’s customer service account, find session tokens for admin logins, and hijack several customer sessions.
An infostealer bypassed antivirus software and successfully snatched a valid 2FA SSO session cookie from an employee laptop. A bad actor then used it to impersonate the employee and generate production access tokens and steal sensitive data.
Cybercriminals paid just ten dollars for stolen cookies on Genesis to access corporate Slack instances and then social engineered new MFA tokens from IT to get access to the company’s internal network.
As adversaries sidestep traditional security measures to impersonate or assume a valid identity within the network, it confirms the need for security teams to have definitive evidence of compromise that they can act on before criminals go to leverage that same stolen information to carry out attacks.
Continuous Zero Trust helps satisfy your compliance requirements
Actionable and relevant darknet telemetry from SpyCloud provides critical inputs for your Continuous Zero Trust implementation. Your policy engine is only as good as the data it receives, and with the growing threat of session hijacking, that means fueling it with next-generation breach and malware intelligence to prevent identity-based attacks.
SpyCloud empowers your security and identity teams with continuous identity exposure monitoring so they can identify risk with known exposures, inform your policy engine, and block access with automated remediation.
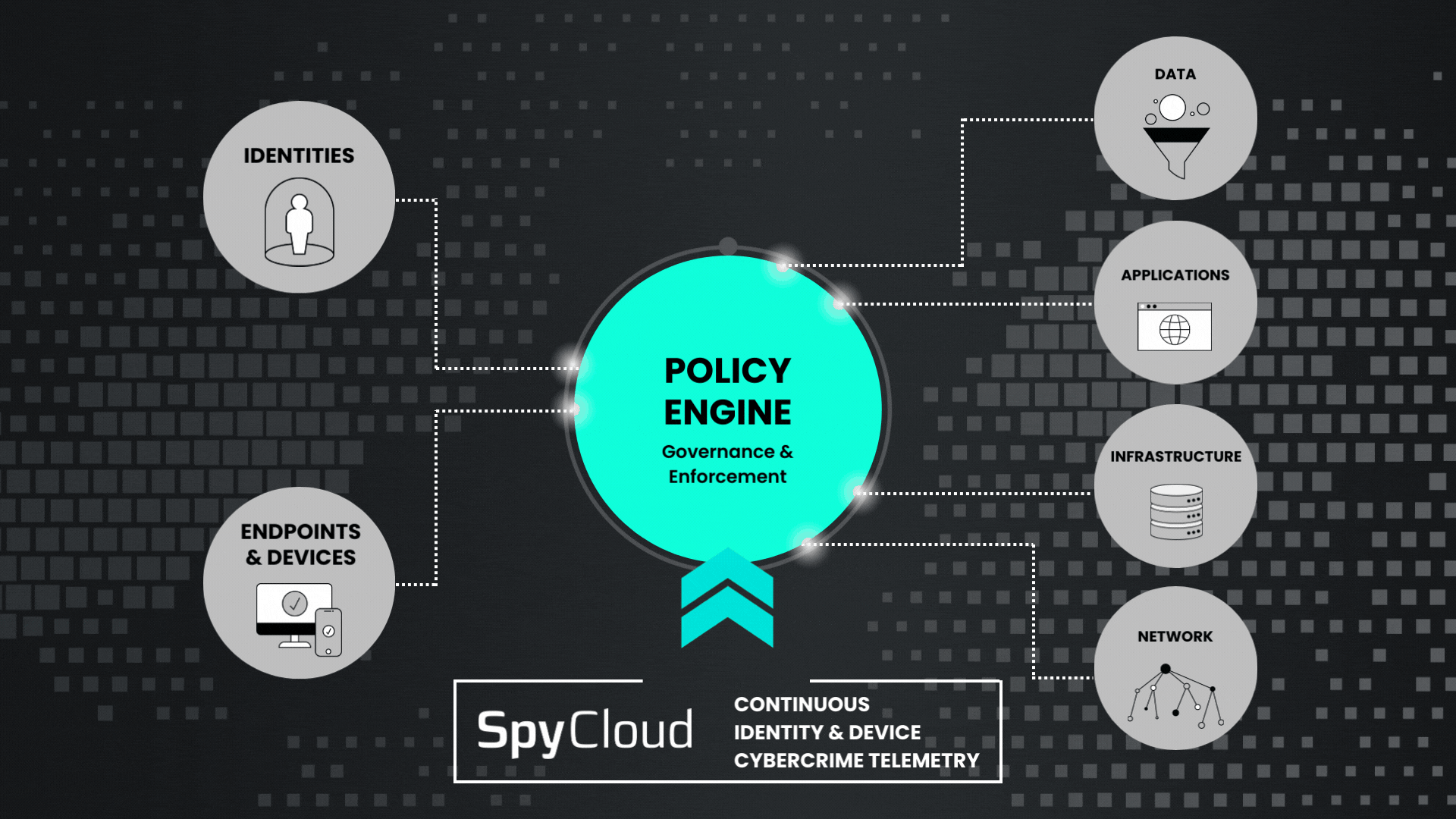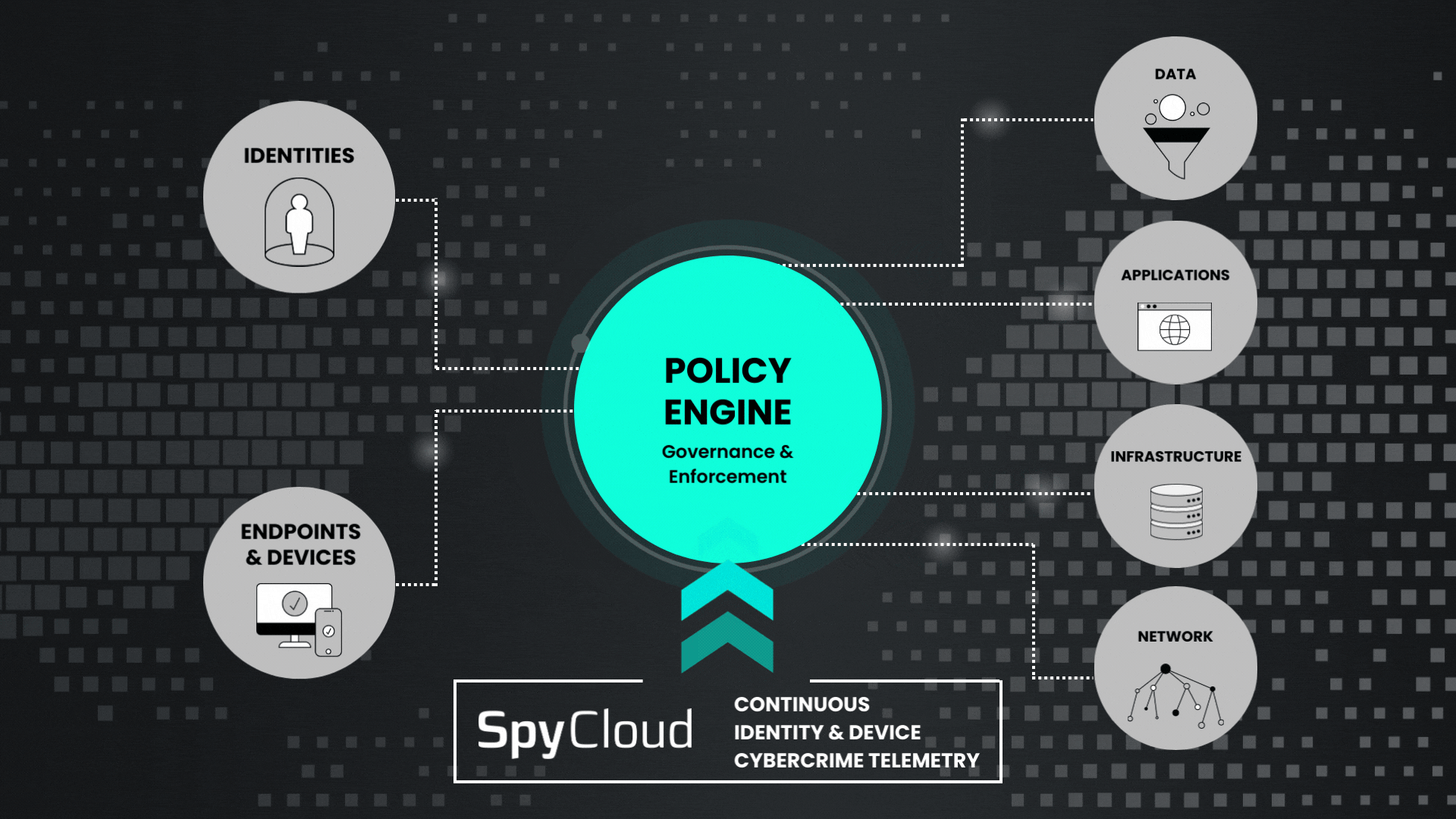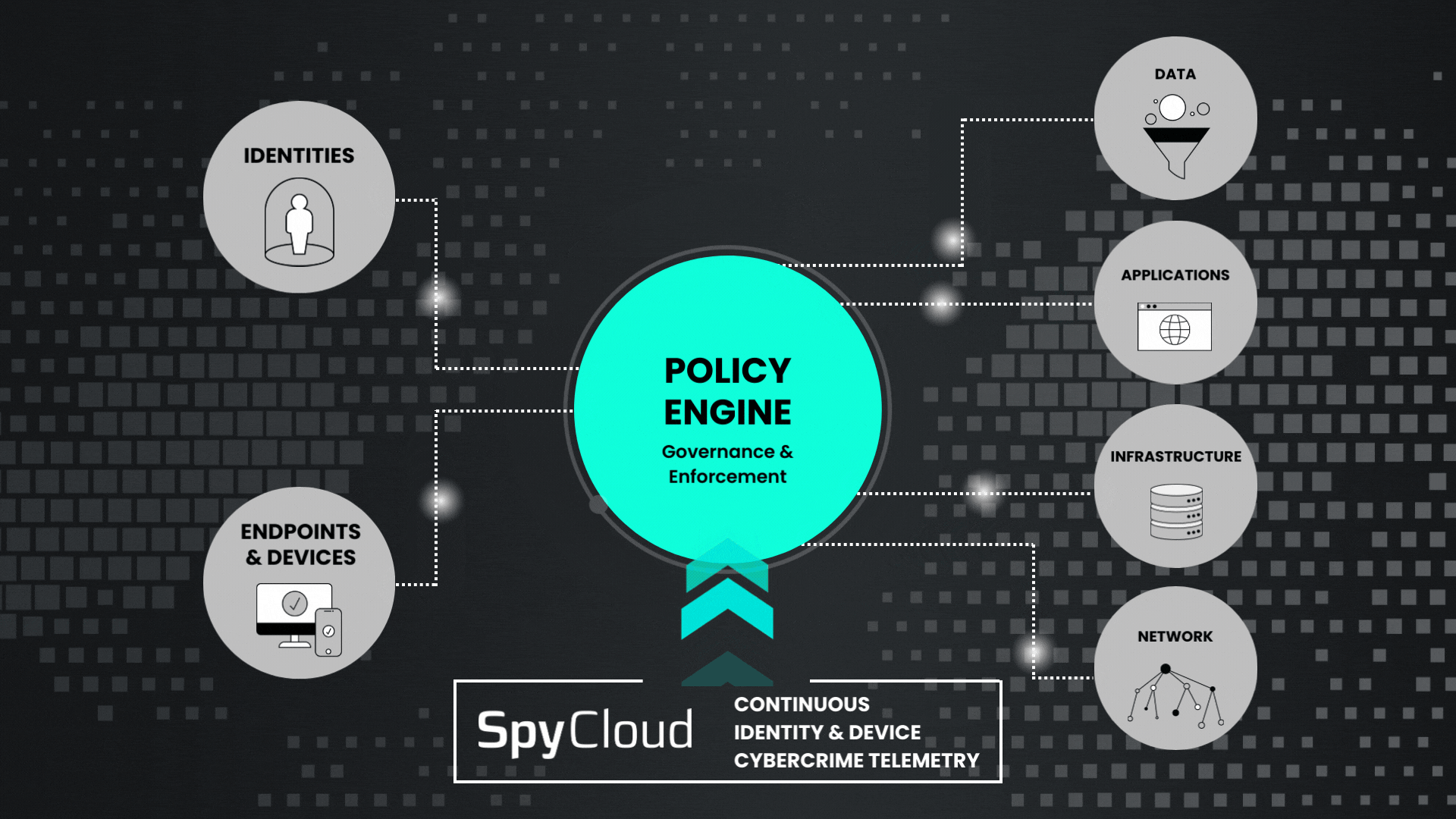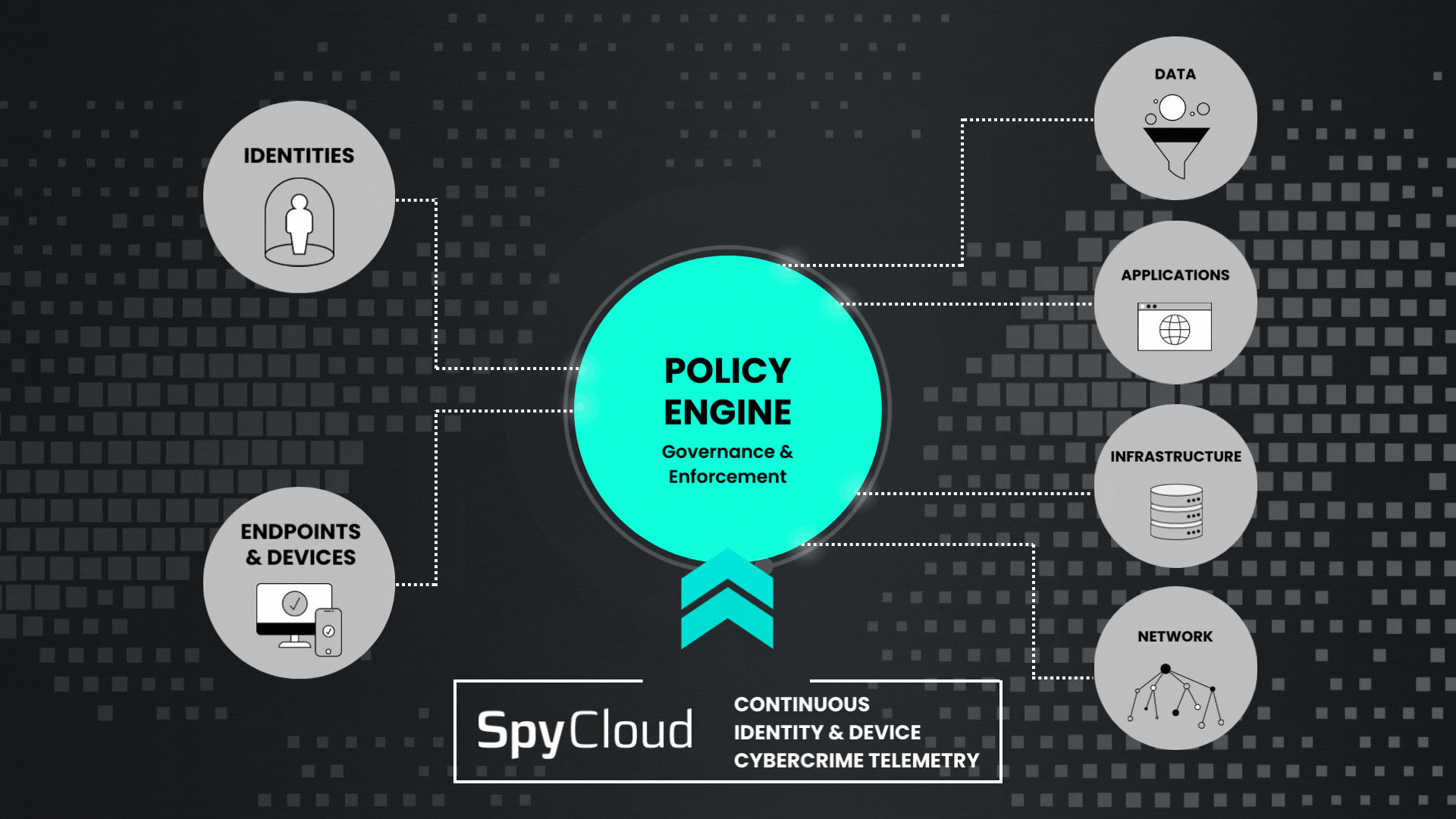
Feed definitive evidence of compromise from SpyCloud into your policy engine to better control and protect access to everything within your network.
The takeaway
There are plenty of pieces to the Zero Trust puzzle, so remember: Zero Trust is a journey, not a final destination. But you’ll be helping your organization out in a big way by leveraging darknet telemetry to fuel your program’s success. It’s a necessity in a world where bad actors have increasing access to vast amounts of stolen authentication data.
Prevent next-gen threats by enhancing your Zero Trust policy engine with SpyCloud.