Cybersecurity threats come in waves just like any other trend – their popularity rises and falls based on the amount of short-term gains that opportunistic groups can obtain from vulnerable people. Account takeovers (ATOs) are no exception. It just so happens that most of us fall into the “vulnerable” category based on our own bad habits.
Those of us in the cybersecurity industry know that weak and stolen credentials have been the leading attack vector for the last 4 years. We know that the cost of account takeover fraud has tripled year over year, and a single attack on one of our personal accounts will cost us an average of $290 and 15-16 hours to resolve. Yet how many of us have a few old passwords in our rotations? (Hold, please, while I go replace that one lingering password from 2008 that I forgot about until now.) How many of us aren’t using MFA because it’s kind of a pain?
Human nature makes us vulnerable to account takeover. Let’s dig into 3 very common bad habits and how they play into criminals’ hands.
Bad Habit #1: Choosing Weak, Common Passwords
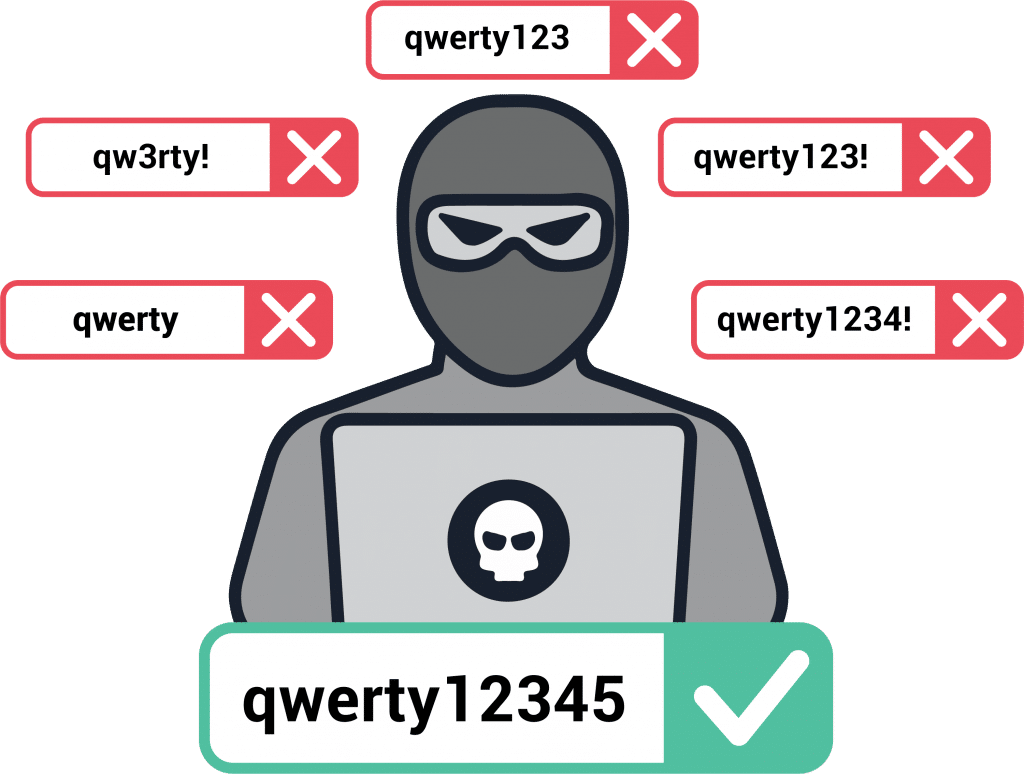
When given the option, users will choose weak passwords that are easy to commit to memory. Regardless of all the advice out there about the importance of strong passwords, without enforcing NIST password guidelines, users will choose sequential numbers and dictionary words. Among the millions of passwords SpyCloud recovered from breaches last year alone, “123456789” was found over 35 million times. “querty123” was found over 13 million times, “iloveyou” 3 million times, and “football” 1 million times.How Criminals Exploit It: Password Spraying
Bad Habit #2: Reusing Passwords
In a Google study, 66% of people admitted to reusing the same password across one or more accounts. SpyCloud’s own research showed that over 76% of Fortune 1000 and FTSE 100 employees are reusing passwords across work and personal accounts. No one – even the most sophisticated user – is immune from this common bad habit.How Criminals Exploit It: Credential Stuffing
Why are reused passwords so dangerous? Credential stuffing makes it possible for criminals to profit from even very old breach data that they buy on the dark web and use it to successfully take over multiple accounts. Credential stuffing tools let criminals test credential pairs against a number of websites to see which additional accounts they can take over. Some criminal tools can even test for common password variations, like changing certain letters to numbers (Password vs. P@ssw0rd) or adding numbers or symbols to the end of a word (password123!). If a password has been exposed in one data breach, any other account with a variation of the same password is at risk.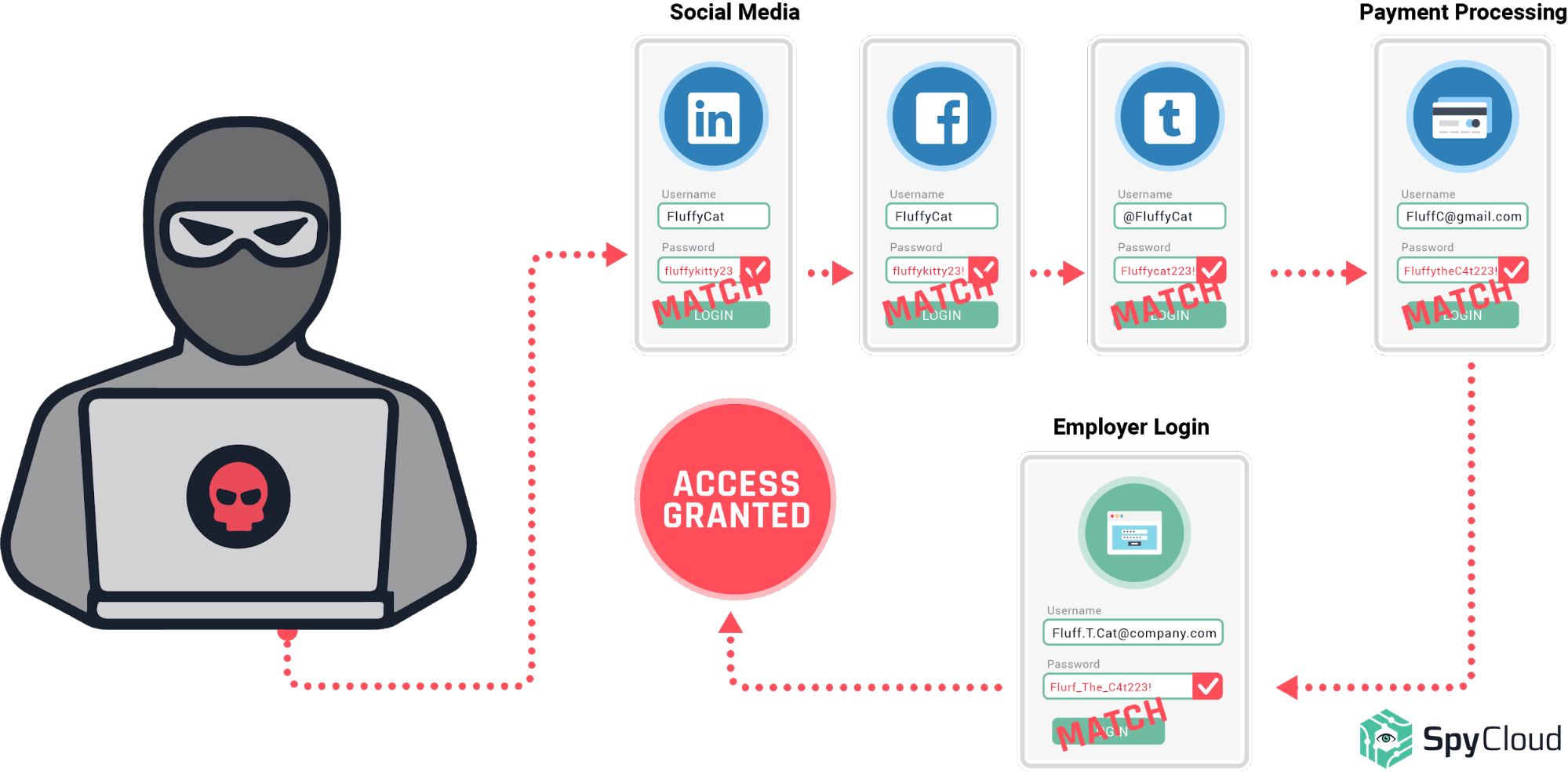
Bad Habit #3: Clicking Unknown Links
To the consternation of security teams everywhere, people will click any link that lands in their inbox, whether they recognize the sender or not. Inevitably, this leads to malware infections, some of which can harvest users’ credentials and other data – putting those users at very high risk of account takeover, identity theft, and online fraud. Total malware deployments increased by 27% in 2020 according to McAfee, fueled in part by pandemic-related campaigns.
How Criminals Exploit It: Keylogger Malware Steals All the Things
Each piece of data a criminal is able to extract from an infected machine – credentials, crypto wallets, credit card numbers, payment service logins, browser fingerprints that let them bypass logging in altogether – it all has a dollar value. Draining a crypto wallet is obviously hugely valuable, but the other pieces can be packaged and sold on the dark web for profit, or exploited by the criminal themselves. Being such a profitable tactic, malware will remain a huge concern for companies for the foreseeable future.Bottom line: educate users to help themselves, but also put proactive defense mechanisms in place.
Conclusion
Human nature is a variable that cannot be controlled. Until cybersecurity solutions focus on eliminating human error rather than enabling it, educating employees is critical – from recognizing suspicious emails to the importance of strong, unique passwords for each account. But so are automated solutions that flag potential compromises before criminals can do harm. After all, accounts that have been taken over using legitimate, stolen credentials don’t always raise a red flag.
Bottom line: educate users to help themselves, but also put proactive defense mechanisms in place.
Wondering if your bad habits have put your accounts at risk?
Check your breach exposure here. It takes 2 seconds and you might be surprised at the data we’ve discovered about you & your domain on the criminal underground.