Cybercriminals often operate in ways that aren’t easily detectable with traditional enterprise security measures. This extends to their pre-attack efforts, from the very first illicit gathering of information to then executing more involved cyberattacks.
In this article, we explore cybercriminal behavior relating to two phases of the MITRE ATT&CK framework – Reconnaissance and Resource Development – and discuss why it’s critical to account for stolen data in your larger detection and attack prevention strategies. This is part one in a series about the role stolen data plays in the MITRE ATT&CK framework.
Pre-attack phases and targeting your organization
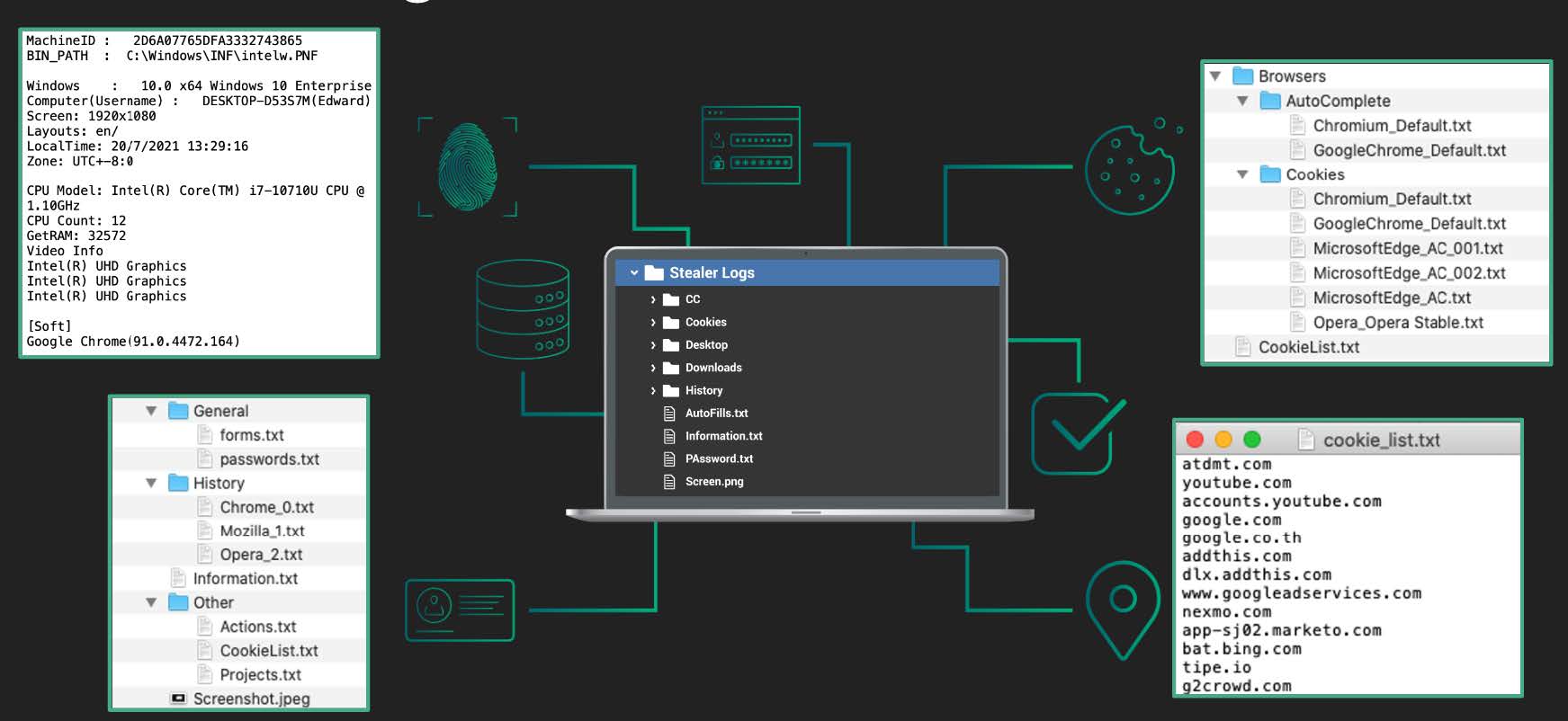
Example of stolen data a criminal might gain access to via an infostealer malware log.
And the reality is, either you’re already a target, or you will become a target at some point.
- If you are already a target, any information available about your organization is advantageous for a bad actor’s plan of attack. Threat actors will select their tactics based on data they’re able to get their hands on and will select an attack technique that presents the lowest likelihood of detection.
- Alternatively, if an actor happens to get their hands on darknet data, such as employee details exposed via a third-party breach or infostealer infection, then your company automatically becomes a target. Cybercriminals will use this data in multiple stages of an attack lifecycle and there is rarely a predictable structure in the order of how it’s used.
How stolen data aligns with the MITRE ATT&CK framework
Threat actors will typically take the most effective path to a target, opting for cost-effective methods or ways that offer low resistance. Actors may be able to simply gain access to an organization’s public-facing system, cloud services or applications, or other exposed systems due to human error. Or, an infected system could become their route into an organization’s internal infrastructure where remote access or VPN details have been exposed. Long story short, they can and will take advantage of stolen data whenever possible along their way.
MITRE Reconnaissance Techniques
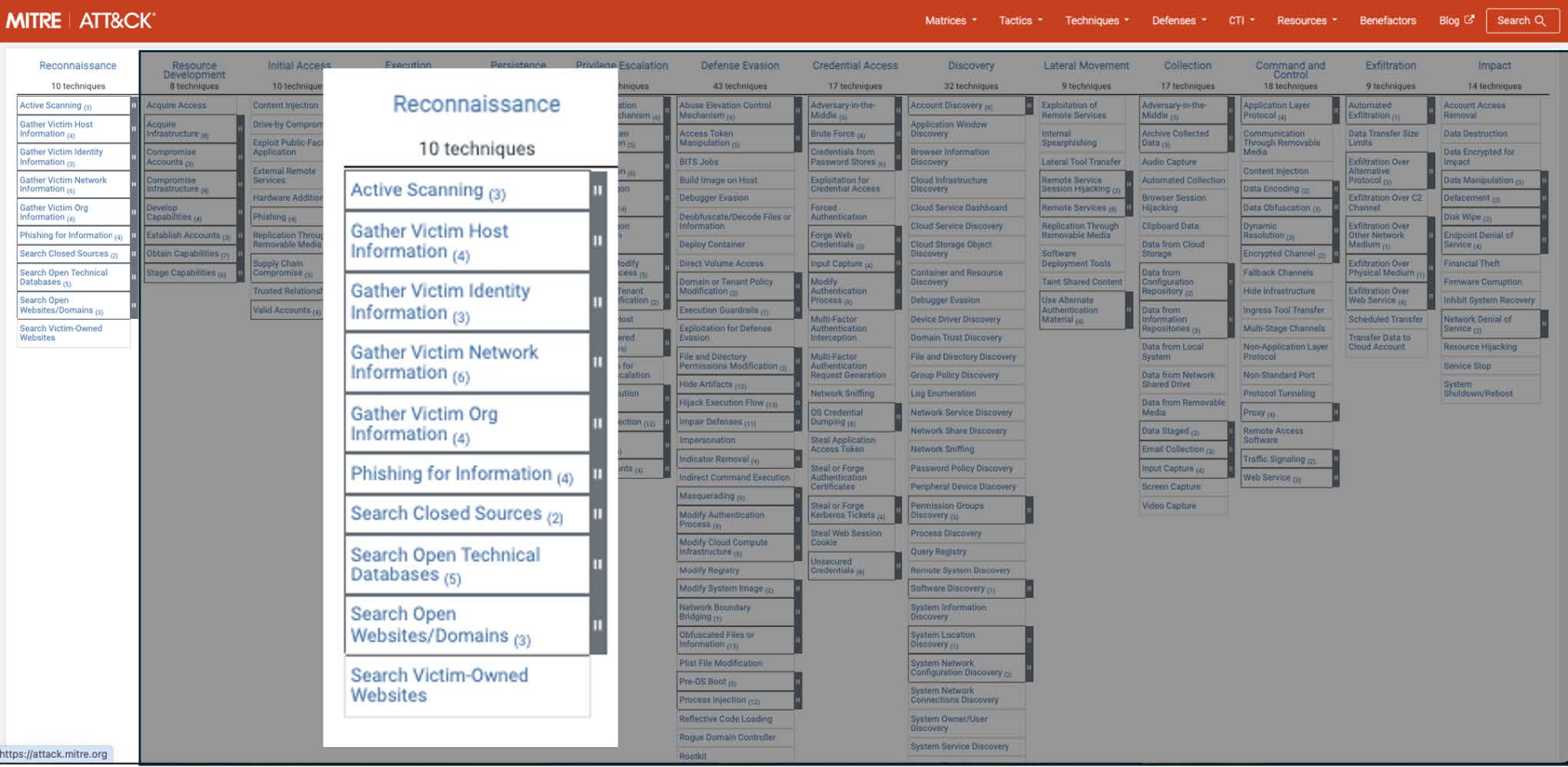
The techniques included in the MITRE ATT&CK Reconnaissance stage.
MITRE ATT&CK Technique T1589: Gather Victim Identity Information
The most obvious alignment with stolen data is MITRE ATT&CK Technique T1589, Gather Victim Identity Information. For example, exposure from an infostealer infection could arm a cybercriminal with credentials and other user information they could then use to easily impersonate an employee to access a business application. With fresh, accurate identity information like valid user session cookies, criminals can hope to sidestep multi-factor authentication (MFA) controls via a session hijacking attack.
MITRE ATT&CK Technique T1590: Gather Victim Network Information
If a criminal uses Technique T1589 above to gain access to an application – depending on the application – that step alone could be enough for the threat actor to cause a significant security impact on an organization, as was the case with the Orange Espana breach. But it also presents the attacker with an opportunity to gather even more information.
Enter MITRE Reconnaissance ATT&CK Technique T1590, Gather Victim Network Information. In an infostealer record, it’s not uncommon to also see exfiltrated details about a network environment, i.e. routing, switches, firewalls, VPNs, servers, virtualization, network or endpoint security, etc. The domain for the management portals for these technologies is often also exposed. Criminals can gather this information and then use it in a different attack later.
Other ways they can find out more information about the network include using exposed credentials to access corporate ticketing systems. For example, a threat actor could access a ticketing system to view open/closed tickets or see automated workflows from your vulnerability and patch management system that confirm unpatched systems they can then take advantage of. The more attackers know about the status of the network, the more holes they have to poke.
MITRE ATT&CK Technique T1591: Gather Victim Org Information
There are many examples where an initial exposure can lead to further information that is useful to threat actors, and such is the case with MITRE ATT&CK Technique T1591, Gather Victim Org Information.
The data from third-party breaches often expose personally identifiable information (PII) assets, including things like job titles that then tell actors which employees present as high-value targets. If an actor can successfully leverage information about an employee – especially something like a stolen corporate-issued employee ID – to compromise Human Resources tools or employee portals, a wealth of additional information becomes available to them. They also win if they can gain access to internal messaging systems or other third-party applications that often provide real-time information about an organization including processes and planning.
Last year, SpyCloud recaptured more than 4.7 million third-party application credentials harvested by malware on managed and unmanaged devices, including many popular business tools, so it’s fair to say criminals like to explore these routes to gather information.
MITRE ATT&CK Technique T1598: Phishing for Information
MITRE ATT&CK Technique T1598, Phishing for Information, is a technique that criminals can use effectively when they are able to leverage stolen data that is relevant to their target. Threat actors will employ social engineering based on exposed information that appears pertinent, and therefore compelling, to a victim. Exposed employees often see a significant increase in phishing attempts as they become more visible through darknet exposures.
Threat actors may also leverage stolen data for other spear-phishing methods, like using a permutation of the breached domain as a crafted link within a message sent to the breach victim. Compromised phone numbers present the opportunity for vishing and SMShing as additional methods that are included within this technique.
MITRE ATT&CK Techniques T1596 and T1593: Searching for Open Technical Databases and Searching for Open Websites/Domains
Exposed data adds to the pool of information readily available to threat actors, making gathering further information much easier and quicker, which in turn can provide a sense of direction. Third-party breach exposures will often include information about an employee’s job title/department, credentials, and other data assets that may lead an actor to explore MITRE ATT&CK Techniques T1596, Searching for Open Technical Databases, and T1593, Search Open Websites/Domains.
With enough employee data in hand, a threat actor can search online resources to identify linked applications, repositories, websites, social media, etc. to identify even more information about their target. Often, and even more threatening, infostealer logs provide direct details to how employees access a database or website/domain – sometimes even extending to full staging or production systems, enhancing the MITRE ATT&CK technique T1594 Search Victim-Owned Website.
Using active or passive scanning techniques, a threat actor can then gain further knowledge of the system components/widgets and pick out weaknesses beyond authentication.
MITRE ATT&CK Technique T1597: Search Closed Sources
The stolen data and techniques highlighted in the previous section are just a small example of how a threat actor can use stolen data to their advantage. Many of these circumstances tie back to MITRE ATT&CK Technique T1597, Search Closed Sources, which involves the private methods actors use to acquire useful stolen data from other threat actors. The earlier they can acquire compromised data after a breach or system infection, the more valuable the information becomes in contributing to the successful execution of the rest of the attack phases.
MITRE Resource Development Techniques
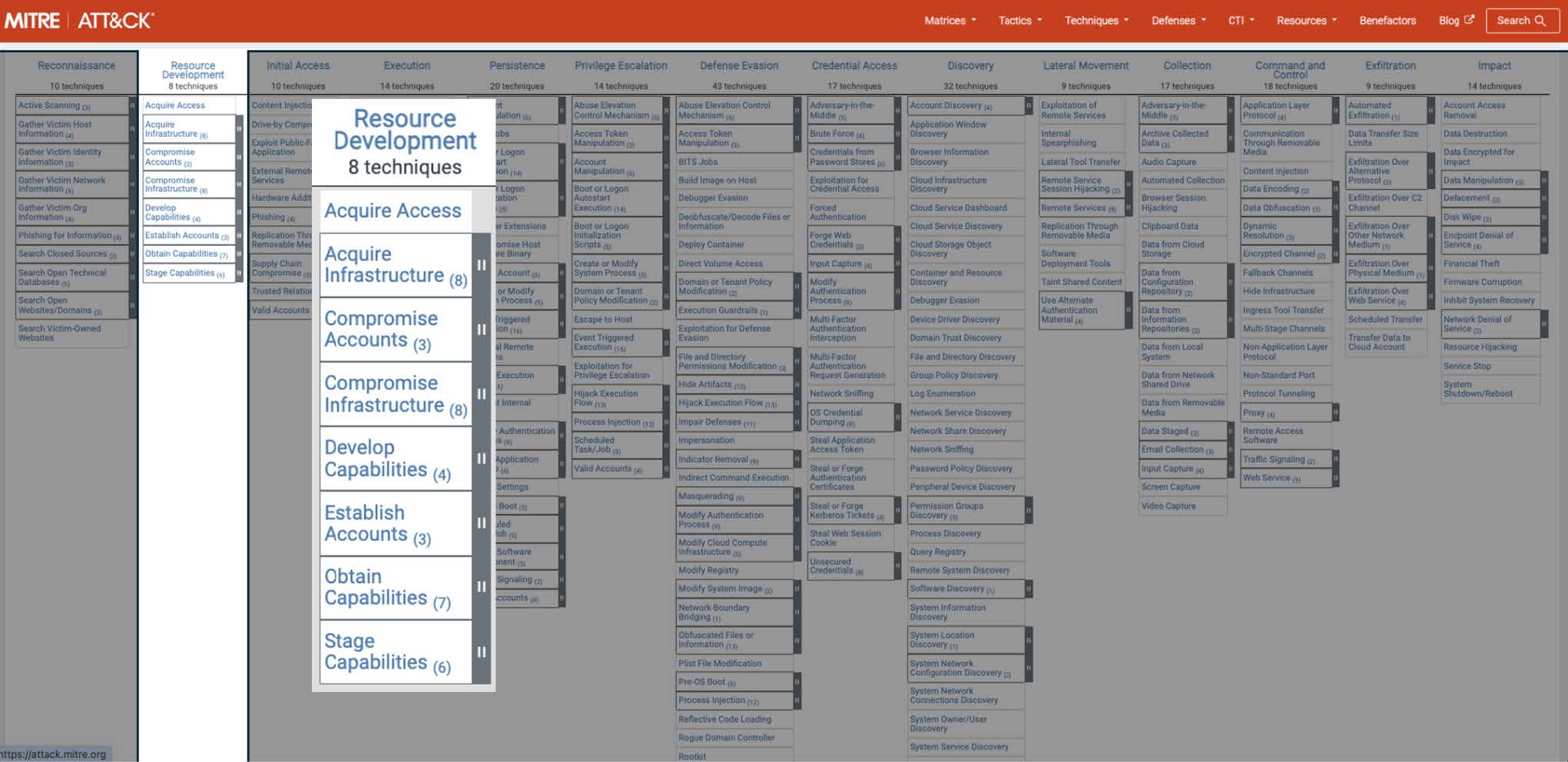
The techniques included in the MITRE ATT&CK Resource Development stage.
MITRE ATT&CK Technique T1650: Acquire Access
In MITRE ATT&CK Technique T1650, threat actors acquire access to stolen data via initial access brokers who circulate the data on the dark web. Often, it’s infostealer data stolen from infected employees, contractors, and supply chains that have privileged access to corporate systems, thus exposing user credentials for direct access. Initial access brokers use the techniques described in the Reconnaissance activities to establish a foothold and maintain undetected access to stolen data they can then sell.
MITRE ATT&CK Technique T1583 and T1584: Acquire Infrastructure and Compromise Infrastructure
In connection with the resourcing of the attacker’s own infrastructure (like we see in this example here), bad actors will use stolen financial data and other stolen information and create synthetic identities to acquire infrastructure as referenced in MITRE ATT&CK Technique T1583. Because the precise use of stolen information often has a high success rate that looks legitimate, it can be very difficult to trace back to the criminal. In this case, the responsibility of security often shifts to infrastructure providers to identify unusual account creation or account takeovers to counter this technique.
For MITRE ATTACK Technique T1584, we again look at the same Reconnaissance techniques that make it easy for bad actors to directly access or further compromise and control infrastructure to use as resources to build a foundation for latter attack tactics, such as MITRE ATT&CK Technique T1608, Stage Capabilities.
MITRE ATT&CK Technique T1586 and T1585: Compromise Accounts and Establish Accounts
As discussed, stolen data from a third-party breach or infostealer infection delivers a treasure trove of compromised account data, including things like credentials for an employee’s corporate email, cloud accounts, and even social media accounts. As identity exposure escalates, threat actors can pick and choose the best accounts to take over and then use them for further operations like phishing. Bad actors look for ways to establish trust with their tactics, and compromised accounts, MITRE ATT&CK T1586, is a preferred technique to fly under the radar.
Employee identity data can be linked to personal data exposure with other identifiers, and can even rope in family data as a vector for gaining more information or access to the primary employee target or organization. This scenario aligns to MITRE ATT&CK T1585, where stolen data can then be used by an actor to create an online persona to establish a trusted identity.
MITRE ATT&CK Technique T1588: Obtain Capabilities
Credential abuse for controlled access to specific resources may contribute to MITRE ATT&CK Technique T1588, Obtain Capabilities – especially when exposure points to a particular resource from a malware-infected system. Actors may be able to acquire commercial tools such as software and licensing at no cost, plus the acquisition of supporting components such as config files, system/network logs, or data retained by a provider of a particular service to be used during targeting.
Stolen data at an actor’s disposal often includes valid cookies or provides access to development environments, such as staging or production environments, where attackers could obtain code, signing certificates, API keys, or user/application tokens. Supply chain exposure may also provide criminals with capabilities for targeted attacks.
Best practices for preventing cybercrime tied to the pre-attack phases
-
Data enrichment: Optimize your SOC
-
Continuous identity monitoring: Staying ahead of threats
-
Post-Infection Remediation: A powerful malware response strategy
Typical malware infection response stops once a device has been cleared of the malware. But with visibility into malware-exfiltrated access details, your team can take additional steps for a more robust response that negates follow-on attacks. For each affected application, Post-Infection Remediation entails invalidating active sessions, resetting passwords, and reviewing access logs for evidence of compromise.
Enhance attack prevention with SpyCloud’s Cybercrime Analytics
Having cybercrime data and analytics available to you can also enhance your detection efforts in the latter attack stages. In a future blog, we will highlight how cybercriminals continuously draw on stolen data throughout attack phases and recommend how to stay ahead with your enterprise security strategy.