Getting Password Security Right
Because of widespread password reuse, account takeover (ATO) attacks have become an extremely lucrative business for cybercriminals. Organized crime rings are performing ATO attacks on a massive scale by leveraging botnet-infected armies to attempt credential stuffing attacks against various web and mobile applications.
Educating users to select not only strong, but UNIQUE passwords from the start is only so effective. There’s more that can and must be done.
In June 2017, the National Institute of Standards and Technology (NIST) released its 74-page updated Special Publication 800-63B on Digital Identity Guidelines. The updated guidance is counter to the long-held philosophy that passwords must be long and complex. In contrast, the new guidelines recommend that passwords should be “easy to remember” but “hard to guess.” According to the new guidance, usability and security go hand-in-hand.
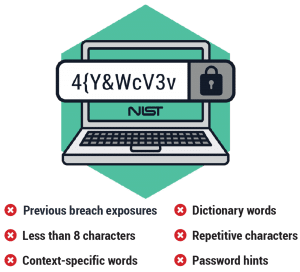
In short, the new NIST guidance recommends the following for passwords:
- A minimum of eight characters and a maximum length of at least 64 characters
- The ability to use all special characters but no special requirement to use them
- Restrict sequential and repetitive characters (e.g. 12345 or aaaaaa)
- Restrict context specific passwords (e.g. the name of the site, etc.)
- Restrict commonly used passwords (e.g. p@ssw0rd, etc.) and dictionary words
- Restrict passwords obtained from previous breach corpuses
For more detail, download our whitepaper, Understanding the Latest NIST Password Guidelines: Security Meets Usability
Easy to Remember, Hard to Guess
In an interview with NPR, NIST’s senior standards and technology advisor, Paul Grassi, who oversaw the revision, claimed the traditional guidance was “producing passwords that are easy to guess for bad guys are hard to guess for legitimate users.” The frustration of keeping track of passwords that are just as hard to remember as they are to guess was duly noted by the agency. The agency even nixed suggested use of special characters, uppercase and lowercase characters, and allowed spaces. In addition, password need not be replaced after a set expiration period.
“If you can picture it in your head and no one else could,” said Grassi, “that’s a good password.”
Needless to say, this is good news for us mere mortals who can’t memorize long and complex passwords or are stubbornly refusing to use password managers due to multiple vulnerabilities in the most popular services. Understandably, people are skeptical. Most recently, cloud-based password and identity management service OneLogin was compromised on June 1 of this year, including information which could be used to decrypt stolen passwords. What are consumers supposed to do?
Security Guidance for The Rest of Us
The importance of choosing passwords that are both easy to remember and hard to guess does not change in light of this new guidance, and the use of multi-factor authentication does not reduce the importance of choosing a good shared secret. Rather, the new “relaxed” guidance on password length and complexity simply aims to make them easier to remember and use for consumers.
The addition of this language has everyone buzzing. Within it, NIST considers the human factor in federal and industry guidance. It not only includes language on the risk it adds but recommends organizations consider usability as part of their entire risk assessment, given that people “struggle to remember” passwords and carry multiple devices.
NIST concludes that length and complexity requirements beyond those they’ve recommended only “increase the difficulty of memorizing secrets” as they “increase user frustration.”
Threat actors are well aware of the most commonly-used passwords. They use technology to scale and prolong their hacks.
The screenshot below is taken from a site that hosts combolists or pre-assembled lists of username/password pairs. These are often sold on underground markets or traded on online “cracking” communities. Threat actors load these lists into automated credential stuffing tools and, with the help of botnets, test the stolen credentials against many sites at once (such as banking sites or streaming content services). These lists are often uploaded into “cracking” tools such as Sentry MBA or Vertex.
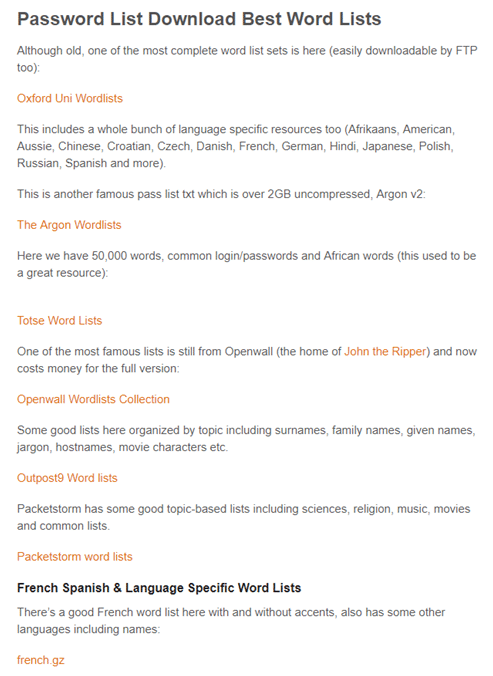
As shown, many of these dictionaries available for download contain common passwords in several languages. These are the types of situations that the new NIST guidelines hope to alleviate. The trick is to choose passwords that only you know so they don’t end up on lists like these.
How SpyCloud Can Help
In order to fight the good fight, you must use modern, sophisticated technology to stop the account takeover before it happens. Integrating with SpyCloud can help. Unlike a static list, SpyCloud’s database includes combolists like these, and over 100 billion recovered breach assets (and adding 1B new assets/month).
SpyCloud maintains one of the largest repositories of decrypted compromised credentials in the world. Many of these credentials are found in the the same combolists that criminals are using today in successful credential stuffing attacks.
Our NIST Password Screening solution allows you to match vulnerable passwords within your environment to compromised passwords in our database. SpyCloud also prevents your users from choosing those which area already compromised. They cannot proceed with registration until a healthy password is chosen.
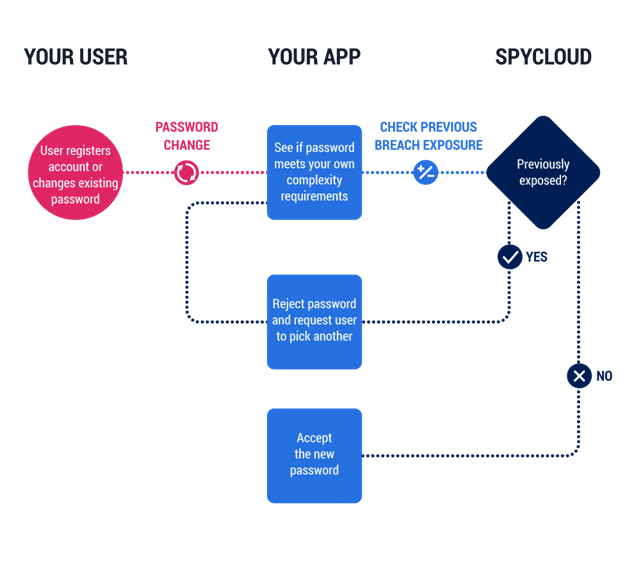
The new NIST guidelines are a reflection of the current threat landscape. A solution like SpyCloud’s NIST Password Screening is key to preventing account takeover and gives organizations more control over their own security.
Interested in learning more?
- Contact us to set up a demo or free trial.
- Read our solution brief to learn how Active Directory Guardian can help you align with NIST password standards.
- Check out our whitepaper Best Practices for Implementing NIST Password Guidelines.

