SpyCloud customers and partners have 94% existing coverage of the “Mother of all Breaches” – among our recaptured dataset of 500B+ assets
If you have been keeping up with breach-related news, you’ve probably heard about the “Mother of All Breaches”, or MOAB data leak as it’s been dubbed in the press. Basically, security researchers uncovered what’s being referred to as “almost certainly the largest [data leak] ever discovered.” And the hype is reasonable, since we’re talking about more than 26 billion leaked records in the hands of threat actors, collected from 4,144 breaches that have occurred over the last several years.
While the scale of the MOAB data leak is vast and affects a broad list of companies, researchers at SpyCloud Labs have confirmed we have 94% existing coverage in our recaptured dataset of 500+ billion assets, meaning a large chunk of the exposed data was either public, old, unusable to criminals, or otherwise widely-known. A breakdown of the size of the breaches contained in the MOAB data leak is shown here.
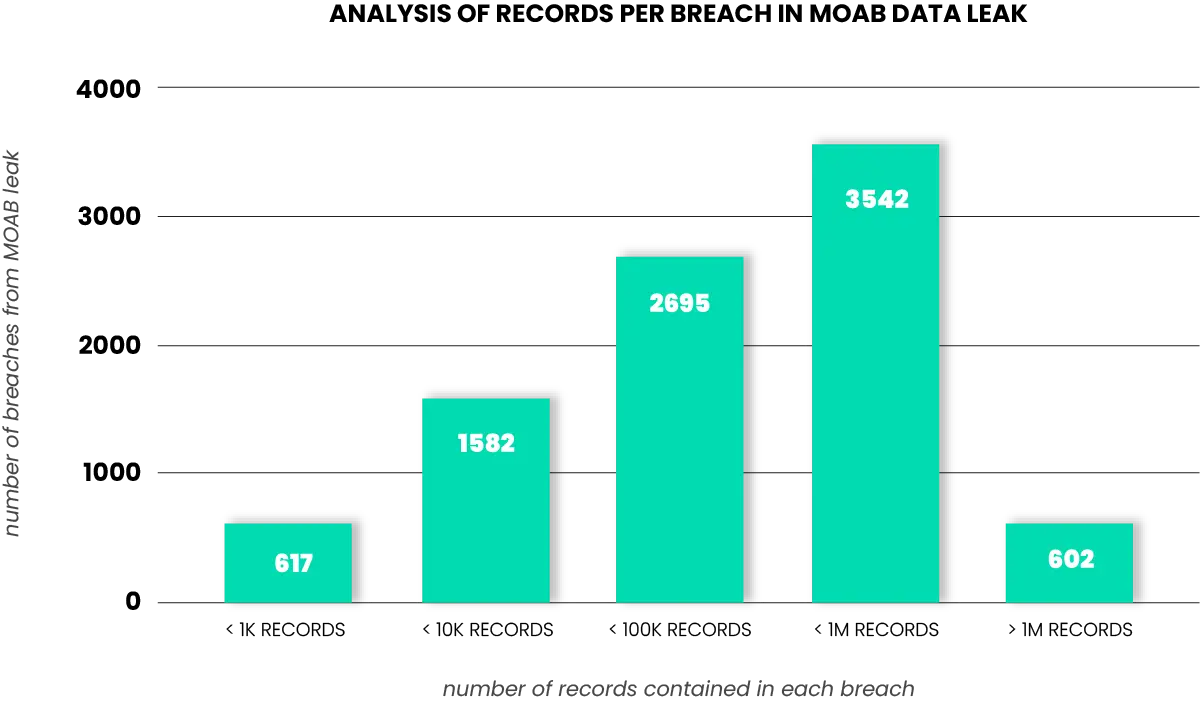
Breach analysis of MOAB
After detailed analysis of the complete MOAB dataset, SpyCloud Labs researchers found that while the vast majority of the breaches disclosed in the data leak already existed within the SpyCloud data lake, 274 individual breaches with a large amount of records – approximately 1.6 billion – appeared distinct, as compared to SpyCloud’s dataset.
SpyCloud Labs findings indicate that some of these previously unknown breaches were either released only in sample format, with the full dataset held for private sale, or previously unreleased publicly. But we also found significant duplication, mislabeling, and/or fabrication of data within the MOAB leak, pertaining to at least 30 of these “new” breaches.
Private sale breaches
A handful of breaches appear to have been either offered for sale or alluded to in forum posts with a small sample of the full dataset. These samples, commonly referred to as “proofs,” serve to prove the threat actors’ claims and tempt individuals into purchasing the full dataset.
One example of this appears to be BTCTurk, a Turkish cryptocurrency exchange, which was allegedly breached in 2023. While a small sample of the stolen data was posted for free by a threat actor on a criminal forum, the full dataset was elusive and may have been sold privately or otherwise traded outside of the public space. By contrast to the several thousand records offered within the sample posted publicly, the version of the breach recorded in the MOAB data spanned over 500,000 records and appears to be the complete set of stolen data.
A screenshot of a “proof” from the Mother of All Breaches (MOAB).
Previously unreleased breaches
The other category – and a significantly larger portion of the breaches – had no record in the public record. This could be due to exclusive access gained by the team responsible for creating the MOAB dataset, or simply that the breaches were released publicly but not yet collected by SpyCloud. It is important to acknowledge that no company has complete coverage of every breach or dataset posted on the internet, and a small portion of the breaches in this category are likely to have been posted in a public or semi-private forum and not identified by our researchers.
An example we’re seeing is a massive breach of QQ.com, comprising nearly 1.5 billion records contained within the MOAB data. The types of assets contained in the MOAB data appear distinct from earlier data breaches, including a widely-publicized breach in 2019 which exposed email addresses and passwords of QQ users. From our analysis, timestamps indicate the breach could have occurred between 2007 and 2021. The amount of high-quality data is vast, with 668,101,892 distinct QQ email addresses, and a total of 719,528,232 email/phone combinations.
Breaches with poor data integrity
As mentioned above, of the previously unknown breaches, at least 30 revealed significant duplication, mislabeling, and/or fabrication of data, totaling over 1.7B records. The extensiveness of poor data integrity contained within the MOAB dataset suggests little care was given in the data collection process. Some examples of this include:
- The Tencent breach, with 1,468,566,171 records, ended up being almost an exact duplication of the QQ breach, save for ~18,000 records.
- A breach called 172.104.90.245_main had 10,856,261 records in the MOAB data leak. After data parsing, we discovered there was a large amount of duplicate data, resulting in only 1,667 net-new records.
- Upon de-duping the data in another breach called city-chat.de with 775,195 records, we again found a much smaller number of unique records: 1,370.
- In another instance, the authors of the MOAB data leak added the clear text equivalent of MD5 hash passwords to data contained in the eHarmony breach, but they added it as the username, with no username or account relation, essentially rendering it useless to criminals.
Impacted by the MOAB data leak? Reach out to SpyCloud today
Our team has ingested 97% of the new MOAB data into our existing data lake of 500+ billion assets so it’s accessible by SpyCloud customers and can be used for automated account takeover prevention. The new breaches are additive to the 25+ billion assets we ingest on a monthly basis, normalize across 240+ fields, and make actionable to prevent further harm. If you’re a SpyCloud customer, please reach out to your customer success manager (CSM) with questions.
In parallel, our Responsible Disclosure team is engaging with organizations identified in the MOAB breach to ensure they have access to the raw data and can remediate any potential user or employee exposure due to the release of this information.




