Corporate Account Takeover 101
When we think about the compromise of corporate assets, we most likely think of data breaches. Corporate account takeover (ATO) may not be a threat as well known as a data breach, but data breaches can often lead to corporate account takeover if the appropriate remediation steps are not taken.
The American Bankers Association defines corporate account takeover (ATO) as “a type of fraud where thieves gain access to a business’ finances to make unauthorized transactions, including transferring funds from the company, creating and adding new fake employees to payroll, and stealing sensitive customer information that may not be recoverable.”
ATO is a scary and dangerous threat that is only growing. With so many entry points into cloud-based systems and networks, corporate account takeover presents one of the greatest risks in our connected, digitized world. Criminals use sophisticated technologies and methods to breach firewalls and other security measures intended to protect the enterprise. Even with all of the corporate efforts to prevent a breach and account takeover, the needle is moving in the wrong direction.
Why Corporate Account Takeover Is So Alarming
Part of the problem is that corporate account takeover comes in many shapes and sizes. Ransomware, for example, is malicious software that corrupts and deletes files unless a ransom is paid. It is usually inadvertently downloaded through an emailed link or attachment that looks legitimate. Employees who get these emails believe they are opening up files from a known source. While these emails usually come from a recognized account owner, the account has actually been taken over by a criminal who sent the email on the real owner’s behalf without the real owner’s immediate knowledge. Ransomware payments have doubled since 2016, costing companies $2 billion.
Related: Verizon 2021 Breach Data Report
These and other email breaches often target higher-level employees, executives, and system administrators with privileged access to sensitive data. Such compromised business email scams are predicted to top $9 billion by the end of 2018.
Criminals are after corporate data that they can steal and sell. They extort money, drain accounts, and fraudulently represent corporate executives. We hear about the big breaches in the media, but behind every public breach are dozens, if not hundreds, of smaller breaches we may never discover. While organizations may not be able to prevent every breach, how and when they respond to that breach will dictate how much they may lose.
Preventing Corporate Account Takeover – What Not to Do
Companies are spending time, resources and plenty of dollars to fight cyber attacks. Some methods are more effective than others, but many organizations are combining several tools to create a complete solution. Unfortunately, even the most well-designed solution is often lacking ways to actually prevent corporate account takeover.
Related: Six Reasons for a False Sense of Security – ATOs
Multi-factor authentication is an effective extra step companies can take to make sure the person logging into an app, system or network is who they say they are. There’s only one problem: 63 percent of companies say employees won’t use it. It adds friction to the login process and employees avoid it. Some don’t even know what it is.
Another issue with multi-factor authentication is that it often relies on personally identifiable information (PII) to verify a user. Cybercriminals can obtain this information from breached accounts, such as social media accounts. If a criminal finds social media posts about a victim’s pet, for example, it’s easy for them to plug the pet’s name into the corresponding security question.
Password Rotation
Asking employees to regularly change their passwords sounds like a great idea, yet many people reuse old passwords or make only slight modifications. If they are reusing a password from an account that has already been compromised, criminals will find it. They will use those stolen credentials to attempt logins to hundreds of sites, including the victim’s work sites, for months or even years after the credentials were stolen. Threat actors use reused passwords to log into third-party services attached to corporate accounts, such as DropBox and Google Drive. This can quickly lead to corporate account takeover.
Behavior and Heuristic-Based Solutions
These products contain machine-learning technology that uses algorithms that vendors claim will detect account takeover before it begins. They only work if they are tipped off of an account takeover attempt. Criminals are smart and so are the technologies they utilize. They are often able to function covertly.
Scanners, Crawlers and Scrapers
These technologies aim to find compromised credentials on the dark web. They do detect them much of the time but usually only after they have been posted to dark web forums where they’ve been discovered by hundreds of criminals. If an organization is basing their ATO prevention strategy on automated scanners, crawlers and scrapers, they will soon realize they are too late to the game. Accounts have already been taken over and damage has likely already begun to snowball.
Preventing Corporate Account Takeover – Solutions that Work
Early Detection and Fast Remediation
The key to preventing corporate account takeover is to identify stolen credentials early, before criminals have time to use them to log into other accounts or sell them on the dark web. The only way to do that is to have access to a comprehensive, constantly updated, real-time database of breach data. The best method to get that data is to hire an ATO prevention specialist that combines automated technologies with human intelligence to gather as much data as possible, cleanse it and make it actionable.
Security leaders must be able to automatically compare new breach data with their directory of employee accounts per domain. If a match is found, they are instantly alerted so they can take immediate action, such as locking the account and forcing a password reset.
Employee Education
It is critical for security leaders to educate all employees, including executives, on the importance of choosing strong passwords that have never been used with any other account, work or personal.
A strong password can be enforced via a password manager and/or by requiring unique, long passwords with multiple characters, symbols, numbers, etc. The passwords may be harder to remember, but they will be nearly impossible for threat actors to guess. Employees must understand that even making slight modifications to a password they use on another account, such as changing “ILoveCats” to “ILoveCats2” is not a significant enough step towards security.
Employees should also be trained to recognize suspicious emails. Official accounts that have been taken over don’t always raise a red flag. That’s why finding compromised accounts as soon as they are stolen is critical. At the very least, they must be discovered before they are criminally used.
Corporate Account Takeover Cases
Curious which data breaches cost the most? Take a look at this Biggest Data Breaches chart from CSO:
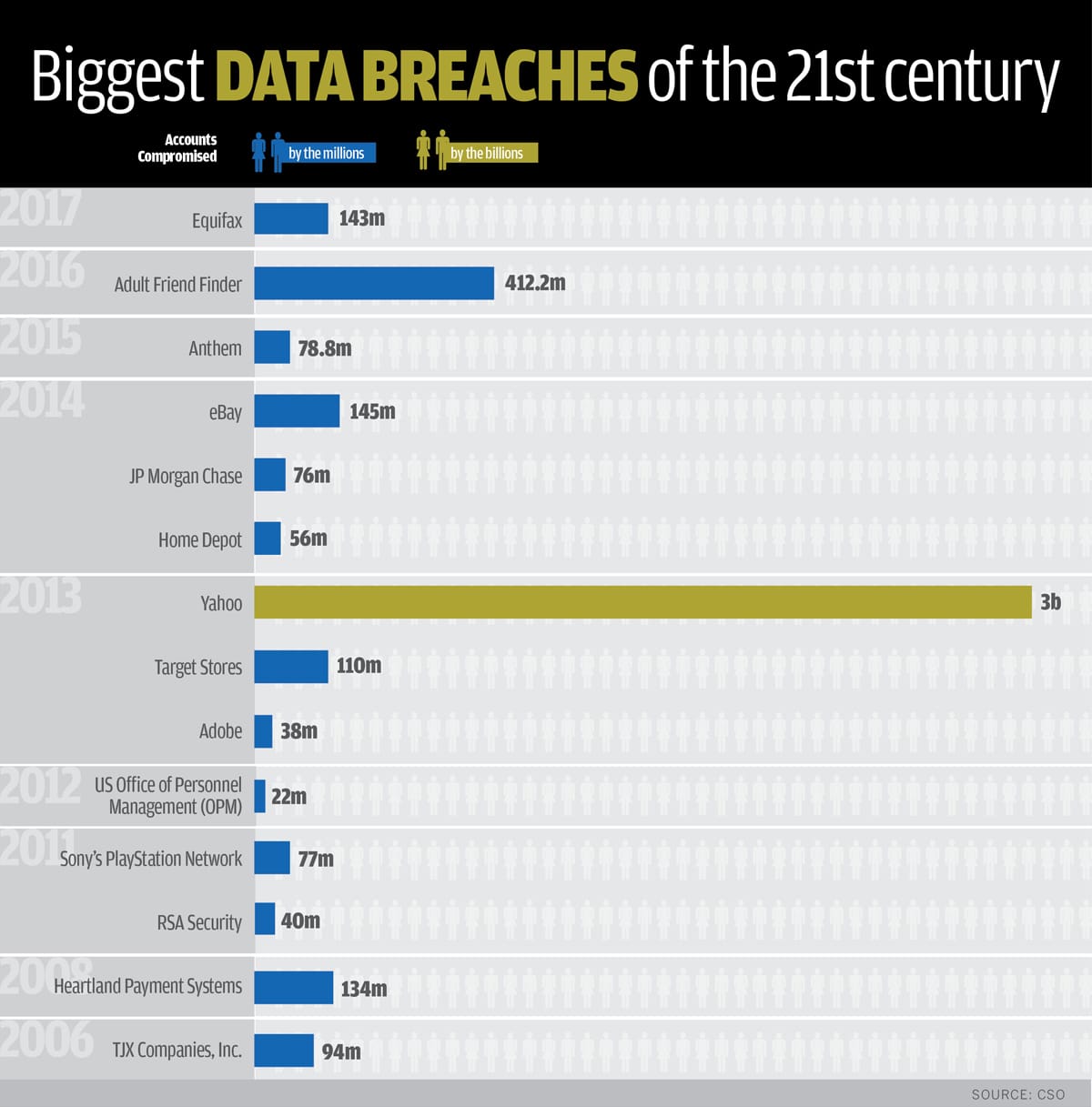
With every breach, we learn more, get smarter, and are more empowered to do better. At least that’s the goal. Unfortunately, cybercriminals get smarter, too. Discovering stolen credentials early in the ATO process and educating employees are the keys to preventing corporate account takeover that can destroy a brand, finances and trust.

