People – employees, third-party vendors, and customers – and their expansive digital identities have exponentially multiplied entry points for attacks on organizations. The average person has four unique usernames or email addresses exposed on the dark web, along with countless amounts of related information that can open up unauthorized access to your network and systems.
Due to the scale of this exposure, automation is an essential component of today’s cybersecurity workflows, but it alone doesn’t fully shield employees from next-generation identity threats. And in some cases, automation may not even be the best course of action, especially in risky situations where nuanced decision-making is critical.
As SOAR tools evolve, they sometimes emphasize automation over orchestration. However, preventing unauthorized access to your networks and systems requires a balance of both components. SpyCloud makes sure that your security teams are not only alerted when employees are compromised, but can also respond appropriately with their preferred tools.
In this blog, we’ll explore how SpyCloud’s cybercrime analytics and enriched employee records integrate with your SOAR platform – like Tines, Microsoft Sentinel, Palo Alto Cortex XSOAR, and more – in workflows that help you detect, respond to, and remediate compromised employee identities.
How SpyCloud supports your incident response
Many threat intelligence vendors provide feeds indicating potential compromised identities, but the challenge for many teams lies in verifying those alerts and assessing the actual extent of an exposure.
SpyCloud’s role in combating identity threats
SpyCloud simplifies this process by automatically correlating all recaptured data from breaches, successful phishes, and malware infections to map out the larger picture of a compromised employee identity for you. The result is definitive evidence of compromise you can act on.
Integrating SpyCloud with your SOAR Platform
SpyCloud’s native integrations can be installed directly from the respective SOAR platform’s marketplace. Each integration includes enrichment commands and workflow playbooks designed to prevent next-generation identity threats. SpyCloud’s enriched and deduplicated analytics are pushed daily to your SOAR platform, ensuring little noise or false positives when raising an alert for compromise.
SpyCloud’s enriched breach and malware records also give your team a holistic view into the exposed employee identity – not just a username or password – but a comprehensive view of all exposed data assets and PII that can be used for unauthorized access, extending to compromised credentials and active session cookies, even for SaaS apps outside your domain.
Workflows for combating identity threats
Now that we’ve covered how SpyCloud contributes to your incident response, let’s explore three common integration workflows:
Data enrichment for incident prioritization
Identity exposure response
Continuous identity monitoring
SOAR workflow #1: Data enrichment for incident prioritization
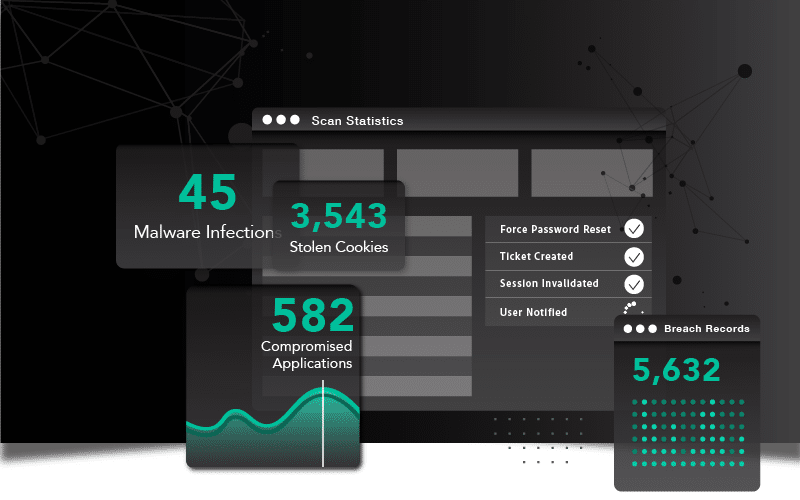
SpyCloud automatically creates high-priority incidents in your SOAR for new data from breaches, malware-infected devices, and successful phishes, making it easy to correlate with other employee records through direct API integrations or SIEM integrations. This ensures that the alerts you see in tools like Microsoft Sentinel or Palo Alto Cortex XSOAR are based on evidence of compromise that is both relevant and timely.
SpyCloud’s data provides many contextual clues about the breach or malware infection within each field, including the date, targeted application, and severity. Exposed PII and even plain-text passwords will appear so you can quickly triage. Additional context surrounding infostealer malware records – like the infected time and infected path – help your team identify affected employees or devices.
Most integrations offer enrichment packages, meaning you can query SpyCloud’s APIs for additional information needed to fully remediate and isolate incidents. The most common enrichment commands include pulling in the IP address, domain, and more information about the infected device itself.
Some enrichment commands within Palo Alto Cortex XSOAR that help your response include:
Email Enrichment:
!spycloud-get-breach-records indicator_type=”email” indicator_value=”${incident.email_address}”
Extracting Additional Information
!spycloud-get-compromised-usernames indicator_type=”username”indicator_value=”${incident.username}”
Associated Malware Data:
Query machine IDs or associated malware data to help with post-infection remediation:
Generate Incident Reports
Use DBot commands to generate detailed reports of the incident using SpyCloud’s enriched dataset:
!create-report type=”PDF” title=”Malware Incident Report” data=”Incident details, enriched data, remediation steps”

Leverage PaloAlto Cortex XSOAR’s enrichment commands to query SpyCloud’s database to add depth to your response and make more informed decisions.
SOAR workflow #2: Identity exposure response
Responding to high-severity breaches or malware infections requires different approaches. Breach response is about speed, and malware remediation is about mapping out the larger attack landscape for potential unauthorized access to your network and SaaS applications.
To address each nuanced remediation path, SpyCloud provides sample automation workflow playbooks within each integration. These playbooks range from responding to exposed plaintext passwords from a breach to checks for the breadth of malware infections, ensuring that the proper actions are initiated within your response and ITSM tools. They also can trigger internal notifications via Slack or Teams to alert and collaborate with other employees.
Responding to high-severity breaches
- VERIFICATION - SpyCloud checks if the breach record matches your domain and employee email, with very few exceptions
- DIRECTORY SERVICE - SpyCloud integrates with directory services such as Active Directory or Entra ID to check if the employee is active, and validates the password meets your organization's security standards and password length.
- PASSWORD LOOKUP - SpyCloud determines if the compromised password is in use within your system, if not you can disregard and close the alert
- PASSWORD CHECKS - Otherwise, SpyCloud verifies if the password is in use or shared across other accounts, even scanning for variations with other compromised passwords used by other employees
- REMEDIATION OPTIONS - SpyCloud gives you multiple remediation options – force a password reset, notify the employee to change their password at the next login, or implement other appropriate actions based on your policies
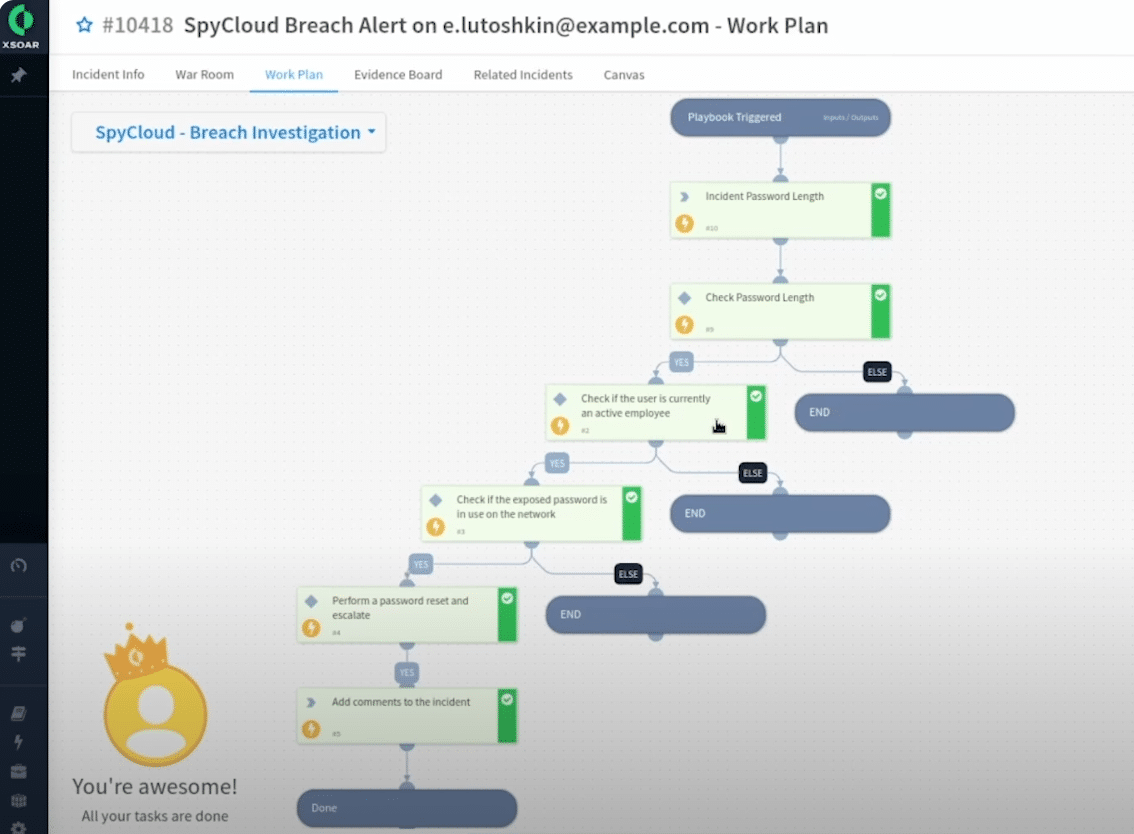
SpyCloud’s sample playbook in MS Sentinel checks for compromised passwords in use, helping to prevent employee account takeover
Malware exposure remediation
For malware-infected devices and employees, SpyCloud delivers SOAR playbooks to help you decide the appropriate response for SOC analysts to take action with better information:
- DEVICE TYPE - Check if the infected device is managed by your organization or if it’s a personal or unmanaged device used by employees or contractors to access SaaS apps
- ENRICHMENT / EVIDENCE COLLECTION - SpyCloud’s integrations combine all records associated with a specific malware infection into a single high-priority incident. Querying records associated with the malware infection pulls more information to help prioritize and update your incident response case
- GROUPING - Group malware records for detailed analysis and response. Even applications outside your primary watchlist are fed into your integration tool of choice to gain visibility of unauthorized criminal access
- THREAT CONTAINMENT - SpyCloud helps identify where to revoke and reissue credentials as necessary. Quarantine the infected device to prevent further spread.
- INITIATE RESPONSE - Use the collected data to determine the scope of the infection. Kick off appropriate response actions within your SOAR and ITSM tools.
- MALWARE POST-INFECTION REMEDIATION - SpyCloud’s SOAR integrations provide critical information needed to remediate at the employee identity level, beyond just the device, to ensure unauthorized access has been cut off from your network
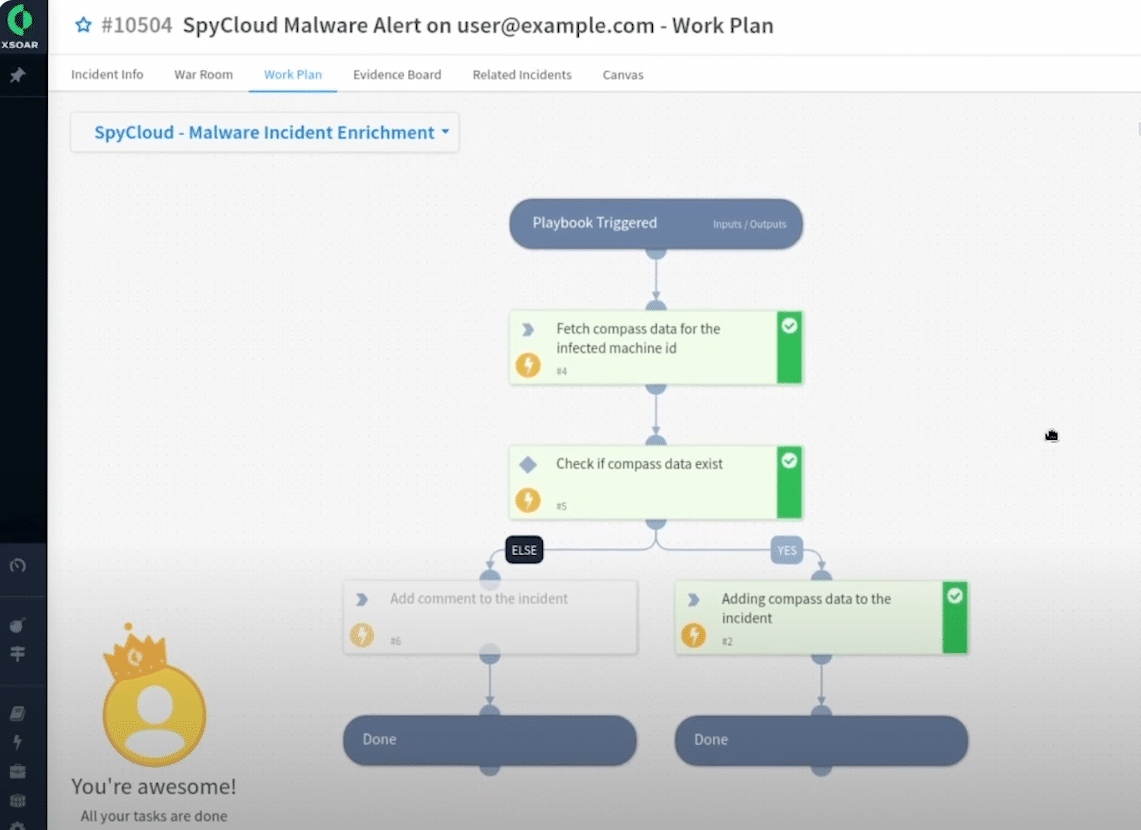
SpyCloud’s malware remediation playbook within MS Sentinel runs the necessary checks to enrich the incident for your SOC analysts
SOAR workflow #3: Continuous identity exposure monitoring
Organizations need to continuously monitor for and remediate employee identity exposures – otherwise, bad actors can bypass your authentication systems, even MFA. SpyCloud monitors for identity exposures and detects new signs of compromise around the clock so you can understand how your identities, devices, and access are perceived by criminals on the darknet.
These insights from SpyCloud integrate with your SOAR to create comprehensive incident response cases, visualizing the full breadth of infections, identifying unauthorized access to applications, and facilitating appropriate communication to prevent next-generation identity threats.
“SpyCloud is an invaluable tool that reduces administrative overhead in resetting consumer or employee accounts if they are detected on the darkweb…It’s reliable, the time to integrate and onboard is easy and simple, and it just works.”

SpyCloud saves LendingTree 60% of the SOC team’s time and resources with actionable data and automation.
How SpyCloud data supports a Continuous Zero Trust approach
These insights also support organizations on the path to Continuous Zero Trust. With SpyCloud, you’ll augment your static device elements with knowledge of what criminals know about your employees. With this timely identity information feeding your Zero Trust policy engine, you can continuously validate each user and device to make sure they’re not compromised.
Next-gen attack prevention with optimized SOAR workflows
What makes high performing SOC teams stand out? They equip even the least experienced analyst with the best information, enabling them to make the smartest decisions quickly. This approach reduces decision fatigue and speeds up remediation times, effectively combating targeted cyberattacks.
Protecting employee identities from next-generation identity threats requires more than just automation – it necessitates a strategic blend of automation and orchestration, enriched with actionable intelligence.
For teams who want to leverage automation, but don’t feel like they have the time or dedicated resources to do it, SpyCloud can also build and maintain automation workflows for you with SpyCloud Connect.
SpyCloud’s integrations with leading SOAR tools enable your security team to respond quickly and effectively to identity threats. By combining continuous detection of exposed identities with comprehensive incident response and integrating within your existing security tools and workflows, SpyCloud gives you the upper hand.
Protect employee identities from next-gen threats by orchestrating and automating your response with native SpyCloud integrations.