SpyCloud introduced Compass Malware Exposure Remediation last year to shine a light on hidden vulnerabilities tied to malware infections, revealing the extent of a given employee’s stolen credentials, including third-party hosted applications. But as cybercriminals continue to evolve their tactics to steal new forms of authentication like cookies, SpyCloud is evolving too. In our latest product update, we’ve improved Compass Malware Exposure Remediation to give you visibility into your stolen cookie data – in addition to compromised credentials – so you can correlate exposures and take further action.
This new visibility helps you fully understand the extent of an employee’s exposure so that you can complete comprehensive Post-Infection Remediation steps. No more guessing if wiping a device and resetting passwords is enough to fully block criminal follow-on attacks like session hijacking. Now you have evidence that access is indeed in the hands of criminals.
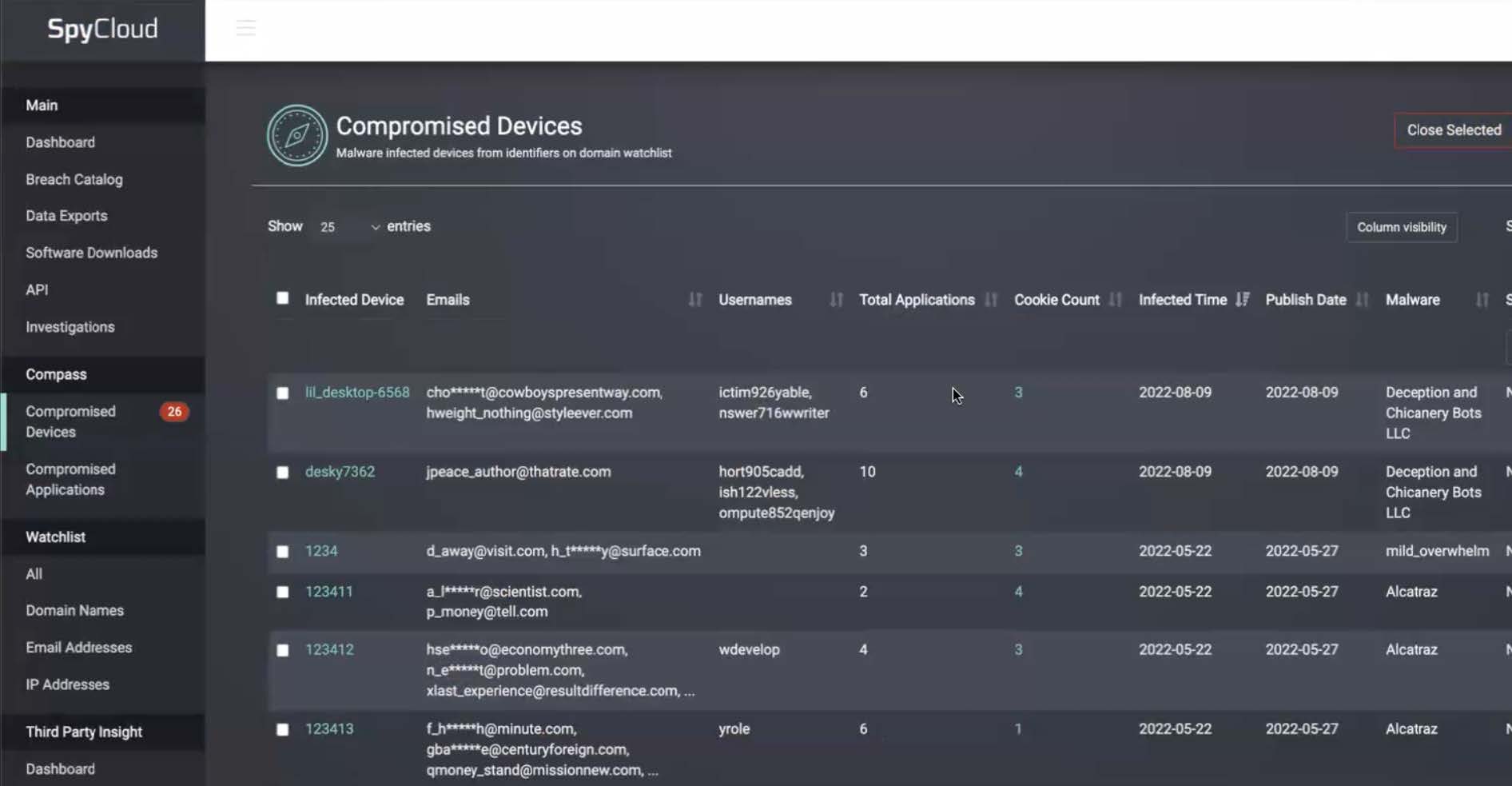
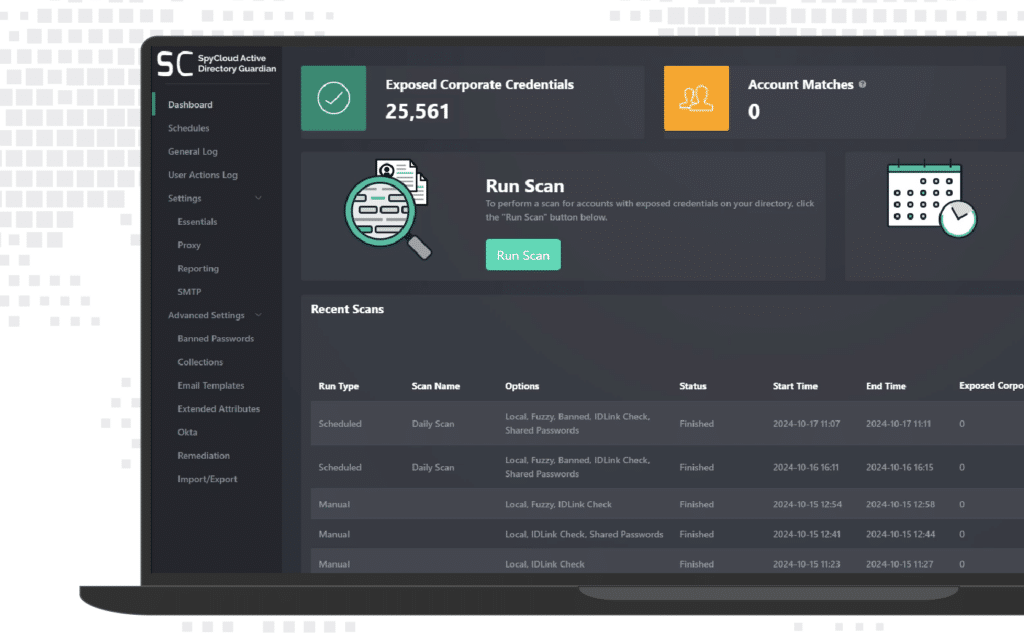
SpyCloud Compass Malware Exposure Remediation shows the count of stolen cookies associated with your monitored subdomain for the affected applications.
How SpyCloud Compass Malware Exposure Remediation Cookie Indicator works
Compass Malware Exposure Remediation makes it easy to connect stolen cookie data to the infection. By simply adding which application subdomains you want to monitor in your watchlist, SpyCloud checks for any recaptured cookie data that matches malware records. If SpyCloud identifies a match, you can see the unique count of cookies and the recaptured cookie name when viewing records for compromised devices or compromised assets.
This powerful information helps your security teams assess the severity of the exposures to take appropriate action to protect your employee identities and prevent session hijacking.
For existing customers, no changes are needed to your existing Compass Malware Exposure Remediation workflows to view this recaptured cookie data. Any new malware notification will automatically include extended cookie information within Compass Malware Exposure Remediation, showing both stolen employee credentials and associated cookies side-by-side within your portal.
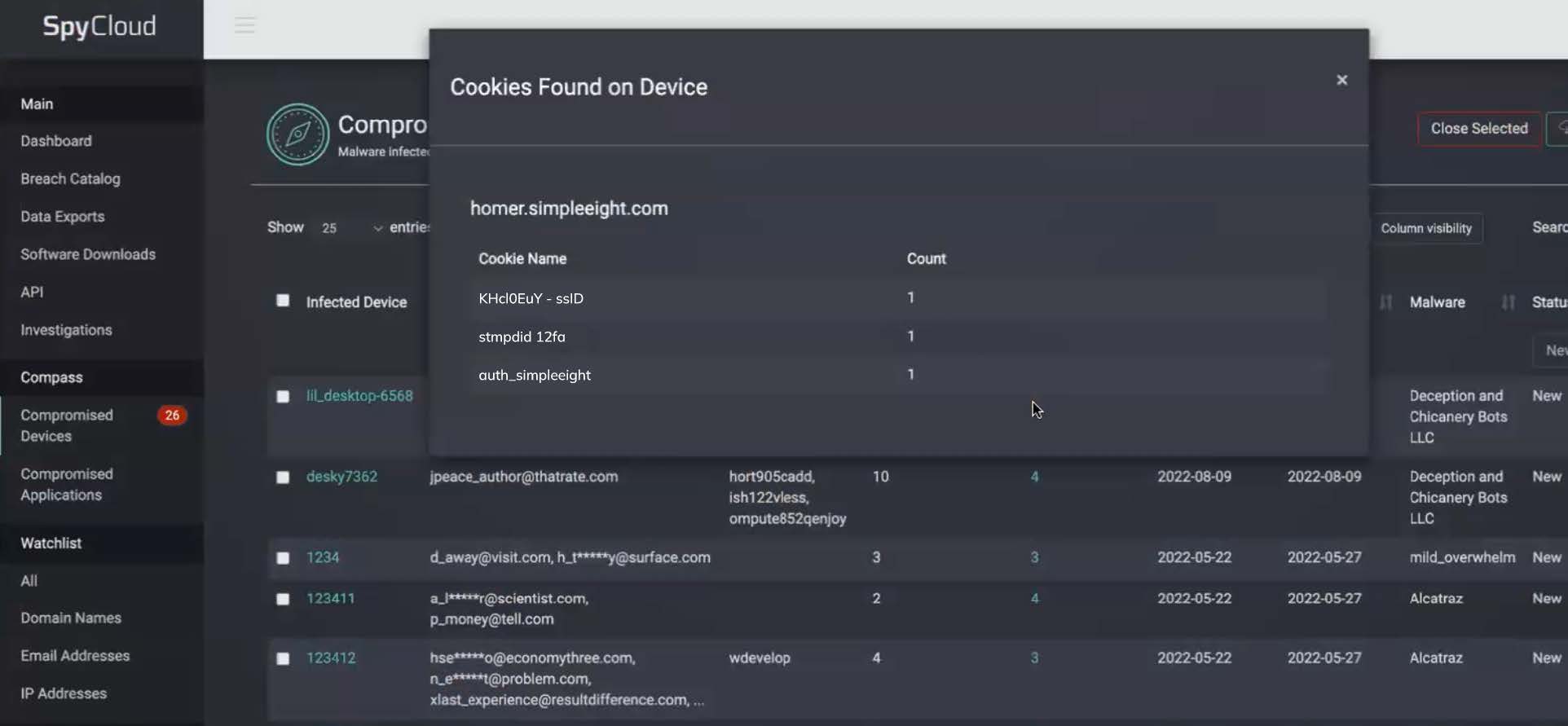
You can see which stolen cookies SpyCloud found from each infected device to determine the extent of your remediation efforts.
How to use SpyCloud Cookie Indicator in your remediation efforts
SpyCloud’s Cybercrime Analytics provides context into which employee credentials are affected by malware. In Compass Malware Exposure Remediation, stolen cookies are linked by combining usernames and email addresses from malware records to the cookie subdomain records that point to the device and employee for remediation.
With this product update, your team can take deeper action to protect your corporate data from follow-on cyberattacks stemming from stolen cookies. You’ll want to confirm the employee is active, then set in motion your appropriate security policy like resetting application passwords, revoking sessions, or flagging the account for additional scrutiny.
With SpyCloud’s combination of credentials and cookies within Compass Malware Exposure Remediation, our goal is to help your teams proactively improve your overall defenses against targeted threats as well as ransomware. Be on the lookout for more Compass Malware Exposure Remediation updates as we work to improve visualizations and further support the connection between stolen cookies and compromised devices to help you defend against next-gen threats.
Read up on SpyCloud Compass Malware Exposure Remediation’ capabilities and workflows for malware remediation.
Get even more exposure information
Need detailed information for all the republished cookies from malware records? Query SpyCloud’s Session Identity Protection to return the full dataset to integrate into your own workflows to identify, flag, and remediate exposed session and cookie data in the hands of criminals.
The new way to fight cybercrime
SpyCloud turns the tables by making darknet data work for you. We detect when your employee and customer credentials, cookies, PII and other critical stolen assets are in the hands of cybercriminals and automate remediation to reduce your risk of cyberattacks.
Assets
Cookie
Records
Botnet
Records