A 2020 update to this article is available here:
The New Cracking Tools That Automate Credential Stuffing & Account Takeover
Account Takeover at the Push of a Button
Custom-built “cracking” tools are making it easier than ever for criminals to automate credential stuffing. Credential stuffing is the act of testing large sets of stolen credentials against a targeted interface. Criminals load lists of breached credentials into these tools to test them at large scale against targeted web or mobile authentication interfaces.
The proliferation of stolen or leaked databases has resulted in a recent surge in automated credential stuffing. Custom tools that have been circulating the underground “cracking” scene in recent years automate this process. These tools make the process so easy, anyone can do it.
On average, attackers are seeing up to a 2% success rate for gaining access to these accounts simply due to password reuse. This may sound like a relatively insignificant proportion, but it equivocates to billions of dollars worldwide in automated fraud losses.
Credential stuffing attacks typically follow some form of the following timeline:
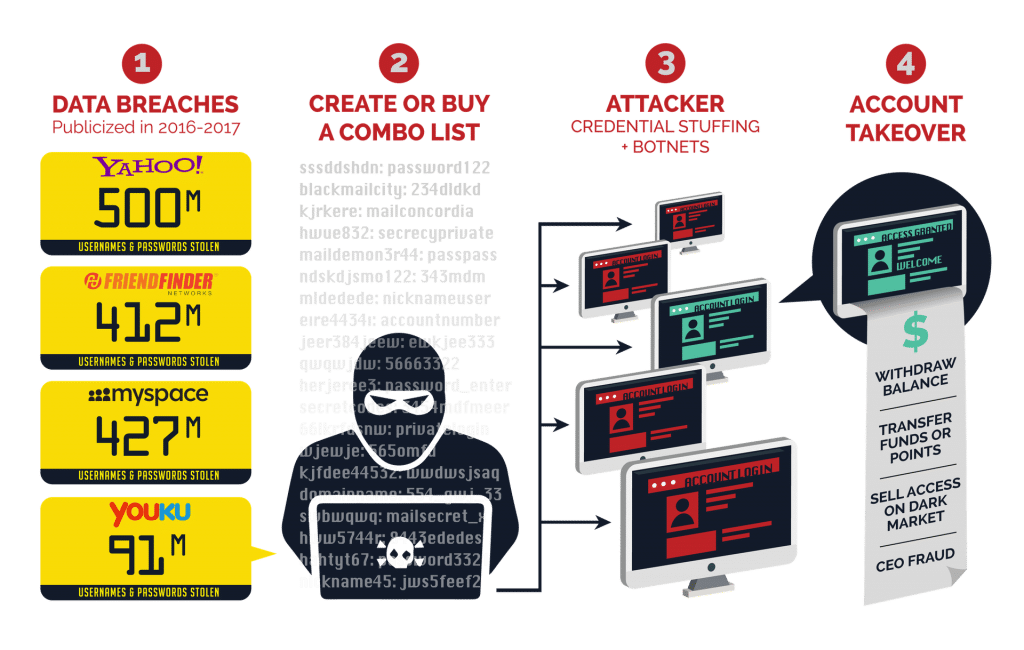
1. A 3rd party breach occurs, credentials are leaked, or site is compromised in some way. The breached data is then posted to public paste sites, sold in bulk on underground marketplaces, and/or traded and advertised in underground forums.
2. A threat actor acquires leaked username and credentials directly from the breach or from purchasing/trading in the underground. Some underground websites even advertise the expected success rates of their credential lists.
3. The attacker uses automated credential stuffing tools, sometimes via botnets, to test the stolen credentials against many other sites (to name a few: social media sites, retail organizations, loyalty programs).
Choose Your Weapon
So what about these tools? What are they and what exactly do they do?
1. Sentry MBA
If you work in INFOSEC, you may already be familiar with the credential stuffing tool known as Sentry MBA (named Sentry 2.0 MBA version by the original developer). The first iteration of this custom Windows brute-forcing application, “Sentry 2.0”, was originally developed by someone using the alias “Sentinel” in underground communities. The tool was later modified by “Astaris” according to Sentry MBA’s opening interface. According to chatter in some cracking communities, Sentinel was actually a security researcher who intended for the tool to be used by organizations against their own interfaces. In fact, the release notes for version 1.4.1 of the tool includes the following disclaimer:
This program is intended ONLY for testing your own sites.
Any other use of this program is forbidden.
The Author does not take responsibility for any improper use of the program.When you start up the tool, you have to agree that you won’t using to test creds against any site or asset that you don’t own.
Regardless, hundreds of cracking communities have sprouted up and thrived upon this rule being broken. Somehow the tool was leaked externally into underground communities–and the rest is history.
Sentry MBA has undergone several revisions since its original release as version 1.02.
If you’ve heard about Sentry MBA before, you probably know that it needs three things “crack” its target:
- Configuration file: This file helps Sentry MBA navigate the unique characteristics of the site being targeted; the URL for the targeted website’s login page, for example, is specified in the config (configuration) file.
- Proxy file: A list of IP addresses (usually compromised endpoints and botnets) to route traffic through, so that the set of login attempts appears to be coming from a large variety of sources (resembling organic traffic) rather than from a single attacker
- Combolist: A database of username/password pairs to be tested against the target site; these lists are typically obtained from the breaches on other websites that can also be sold or traded on certain markets.
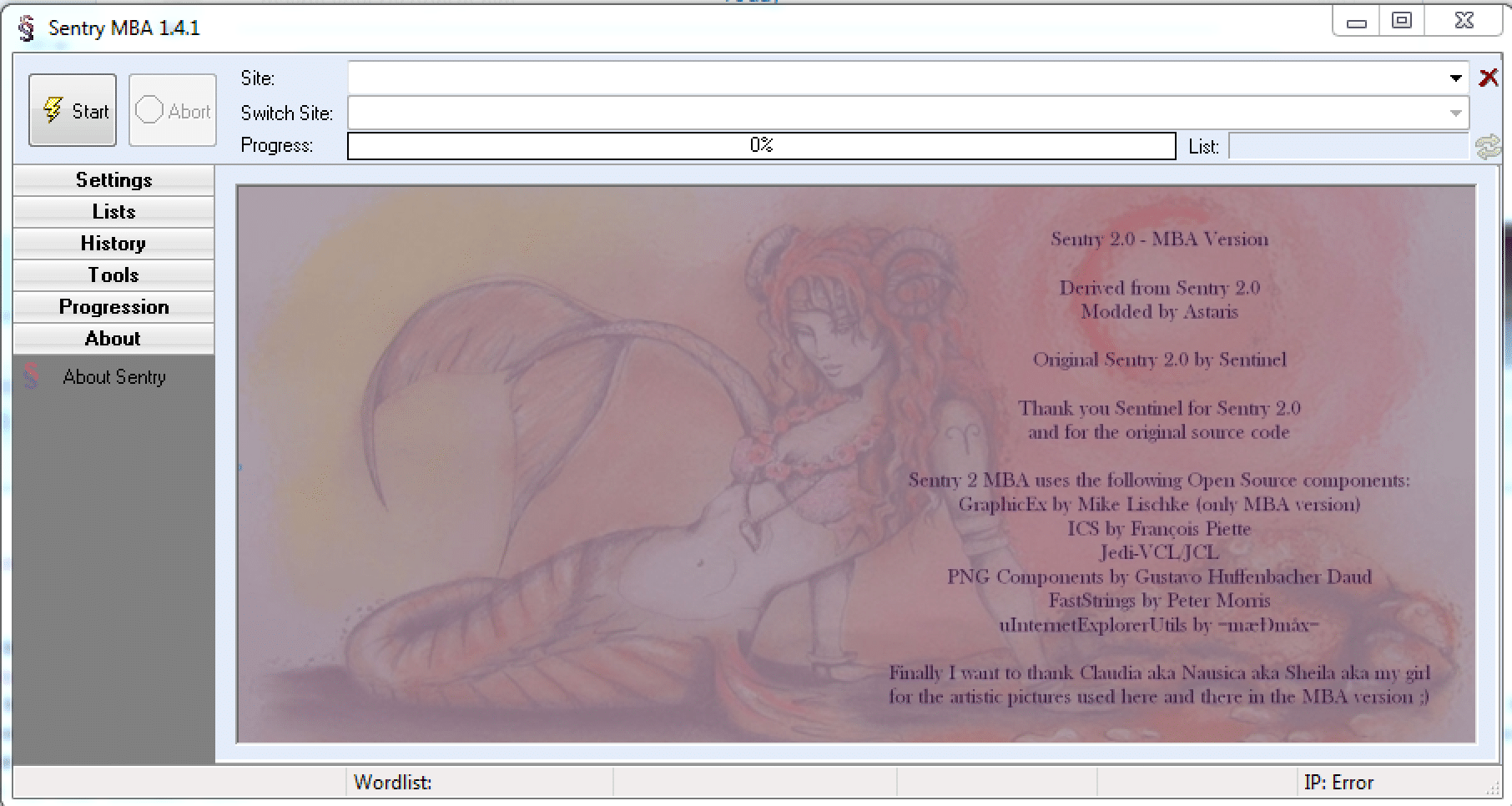
Figure 1: Opening user interface for Sentry 2.0 MBA Version.
There are countless underground forums on both the dark web and clearnet dedicated to the sale and trade of Sentry MBA config files, combolists and proxy files (although sometimes config files are advertised as “proxyless”). These sites vary by language used, technical capability of users and legitimacy. Some of these forums advertise themselves as “cracking” forums or communities in the “cracking scene.”

Figure 2: Screenshot of CrackWarrior, a Turkish-language cracking forum.
Members who use config files (which are often pasted as text files) without giving back to the community are often banned for “leeching.” Many of these communities use reputation scoring for members and enforce disciplinary measures for breaking rules, or for “leeching”too much. Rather than acting as marketplaces, these forums allow members to manufacture, test, and post access to config files, combolists, tutorials, and extra tools for free.
This honor system has helped create self-sustaining micro-markets for the creation and trade Sentry MBA config files and combolists . There are also marketplaces dedicated solely to the sale of Sentry MBA inputs. These often require use of a bitcoin wallet to purchase inputs.
Sentry MBA uses OCR (optical character recognition) functionality to bypass captcha challenges and has many mechanisms to do so. However, Sentry MBA doesn’t support Javascript anti-bot challenges, according to research from F5 Networks.

Figure 3: Screenshot of “Cracking King”
The screenshot below shows some recent threads on a cracking forum dedicated to the trade of Sentry MBA config files. As shown, many of these custom config files are designed by members for popular services such as Spotify, Amazon, Netflix, Hulu, Minecraft, PayPal, Steam, FitBit, and others. It can be confidently assumed that many members of these communities are very young and would otherwise not be able to afford account memberships for these services. Fresh config files for new and existing services are added to these forums on a near-daily basis. And as services adjust their web applications to prevent Sentry MBA attacks, so too do the “crackers” seeking to break them. Sentry MBA inputs are often tweaked, tested, and reposted until they are proven effective.
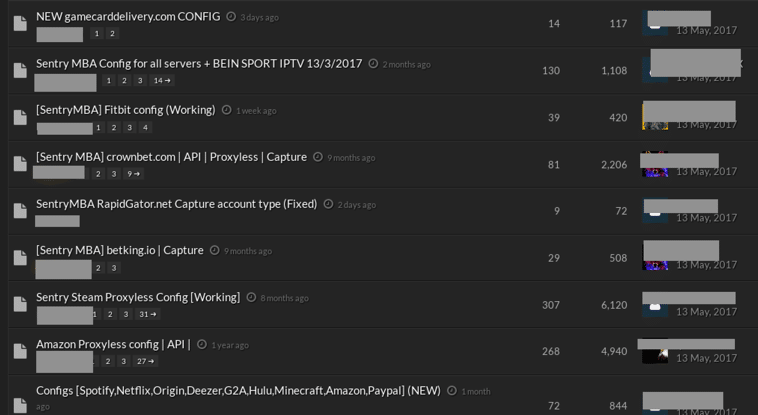
Figure 4: Threads advertising custom-designed Sentry MBA config files for a variety of services on a popular clearnet “cracking” forum.
One of the most trusted config shops is the Sentry[.]mba “Sentry MBA Config Repository”, which has been around since 2015 according the site’s administrators. Sentry[.]mba is primarily a config file marketplace. Users can buy “gold” as a currency on the site using a bitcoin wallet and must use these to purchase configs that have been uploaded by various users.
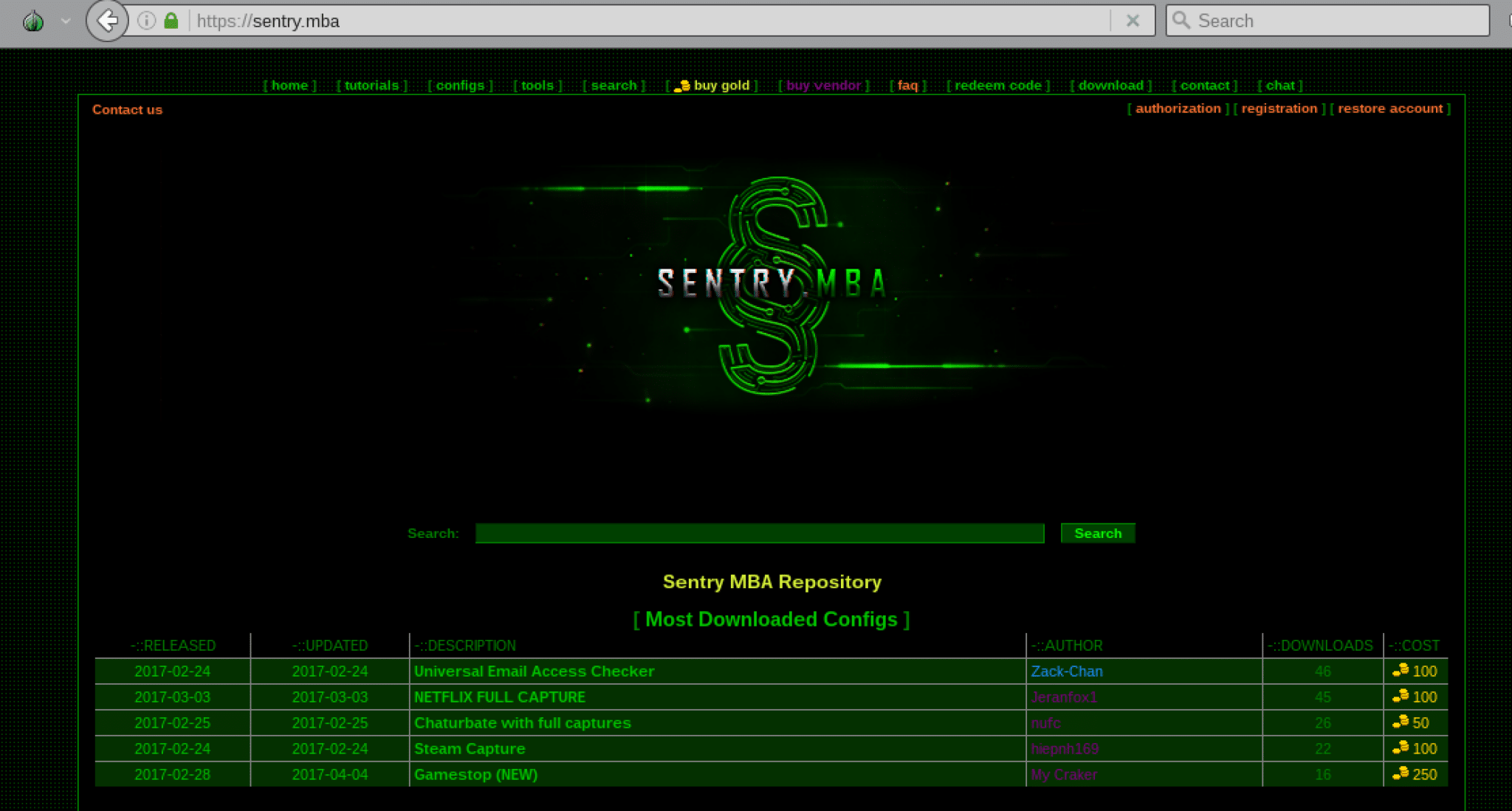
Figure 5: Sentry[.]mba main page.
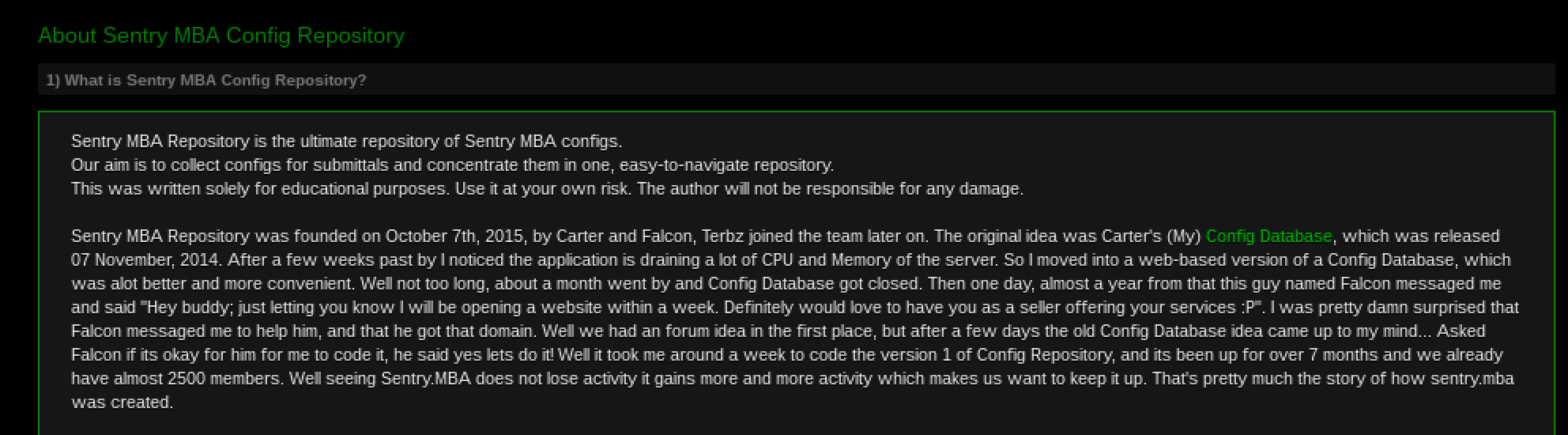
Figure 5: Sentry[.]mba’s description on the site’s FAQ page
The original brainchild of the service, “Carter”, wrote that he originally founded the site as the “Config Databse”. Then, with the help of his buddy “Falcon”, was able to nab the clever “sentry.mba” domain and code the repository that so many “crackers” have come to know and love.
Beyond acting as a source of reliable configuration files, the site also provides free and accessible training on how to download and use Sentry MBA.

Figure 7: Screenshot of a the Sentry[.]mba “tutorials”section.
The site also offers a free download of the latest version of Sentry MBA. The “downloads” section even includes a link to the tool’s VirusTotal scan, which shows which anti-virus services do and do not flag the file as malicious.
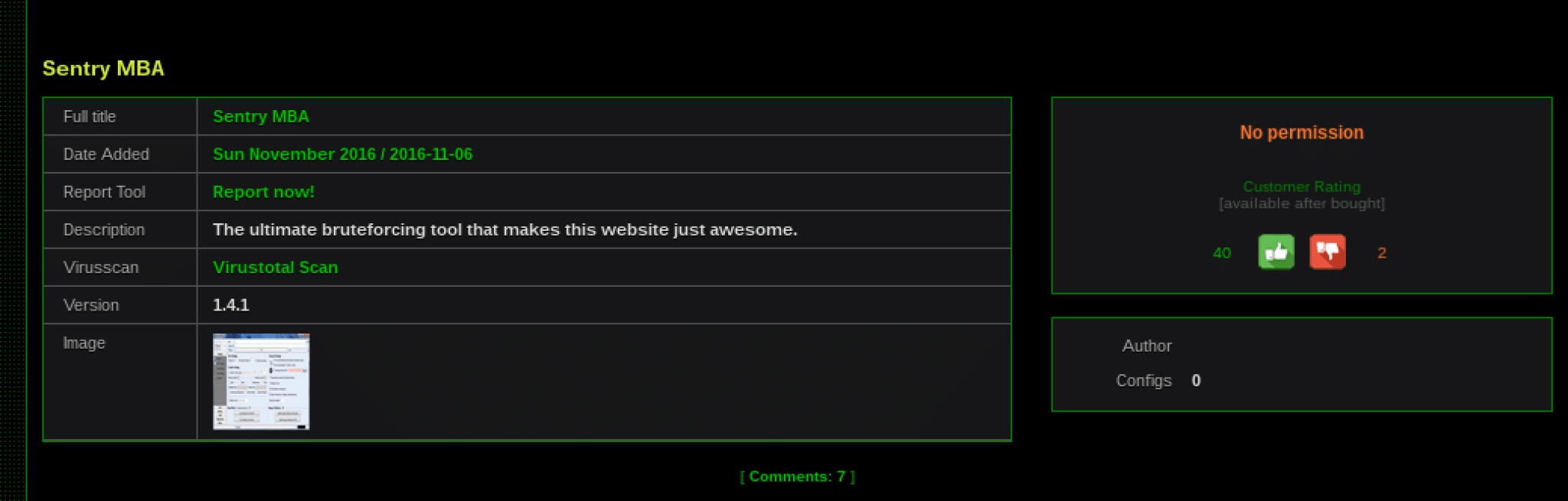
Figure 8: Screenshot of the Sentry MBA download section.
Sentry[.]MBA also offers various tools that members can buy to help them validate e-mail addresses, scrape credentials from dumps on paste sites, and otherwise facilitate the process of “cleaning” their inputs to increase the likelihood that running Sentry MBA against a chosen target will yield a match to crack the targeted application.
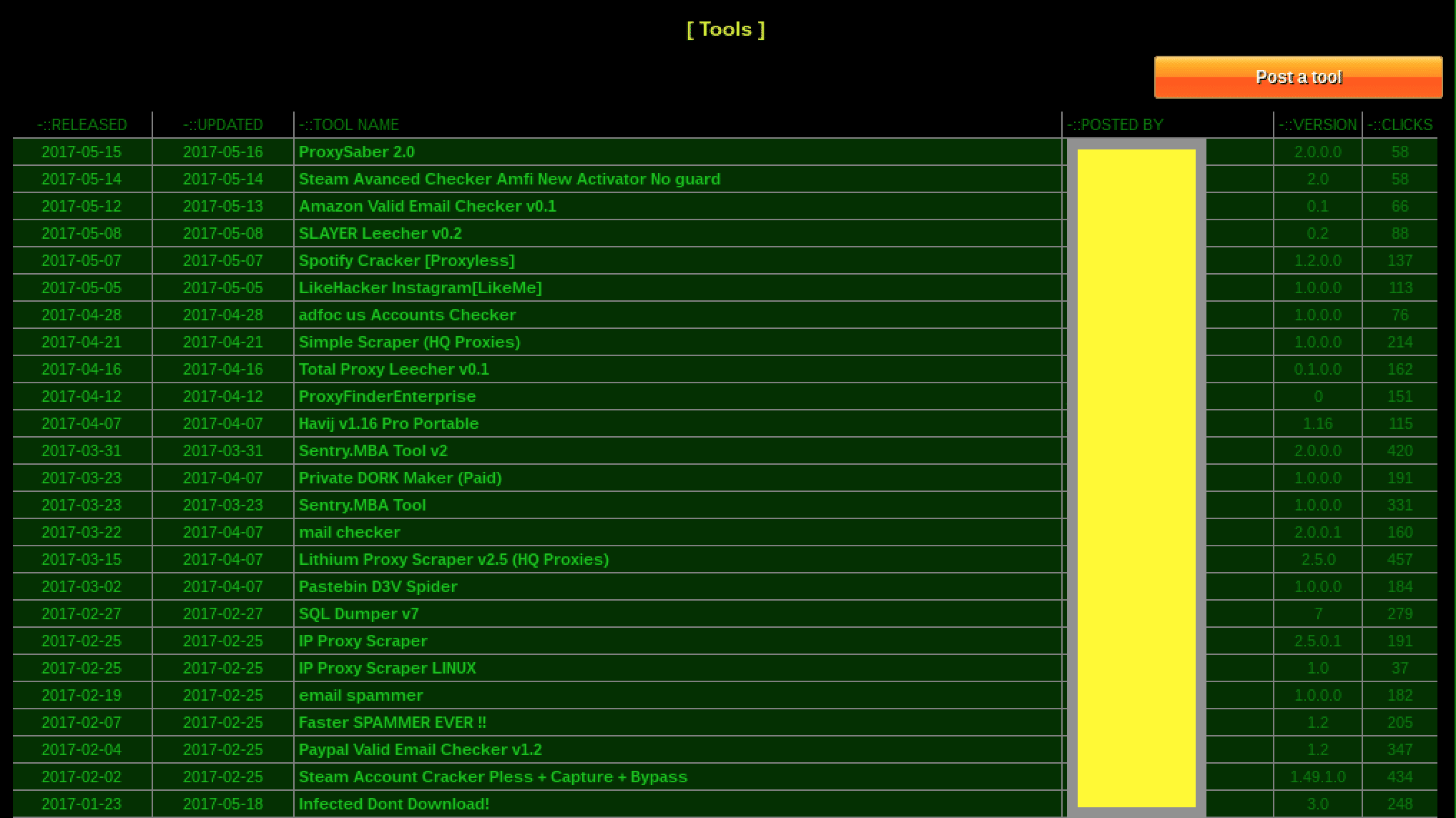
Figure 9: The screenshot above shows various tools that Sentry[.]mba vendors have offered for sale on the site.
2. Vertex
Like Sentry MBA, Vertex requires a config file as well a proxy list—and it can brute-force multiple login interfaces at once. Vertex was also reportedly coded by the same developer as Sentry MBA (Sentinel), though this hasn’t been confirmed. Vertex was released much earlier than Sentry 2.0 or Sentry MBA, but it’s still used in cracking communities and config files and combolists for the tool are still traded and sold.

Figure 10: Original post advertising the availability of Vertex.
Vertex version 1.0.3 was reportedly developed by “Buddah.” Buddah claims to be the same person who developed Sentry.
It appears that Vertex was originally released as “brand new tool” on the clearnet cracking forum “Cracking Arena” on December 16, 2013.
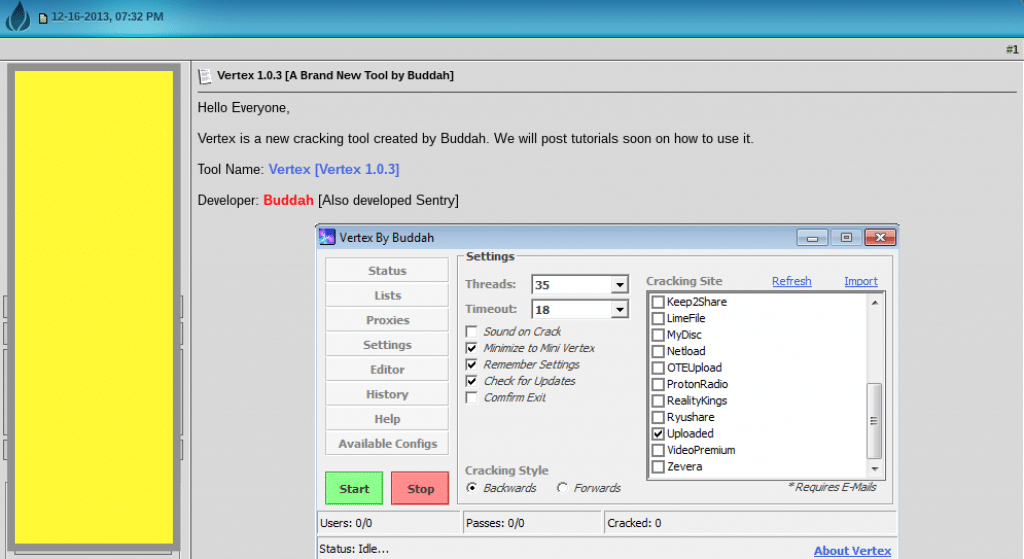
The image below shows the tool in action as it cracks a targeted site, processing a combolist which must first be uploaded by the attacker. According several tutorials posted to cracking sites, users of Vertex follow these basic steps to run the tool against a targeted site to “crack” user accounts:
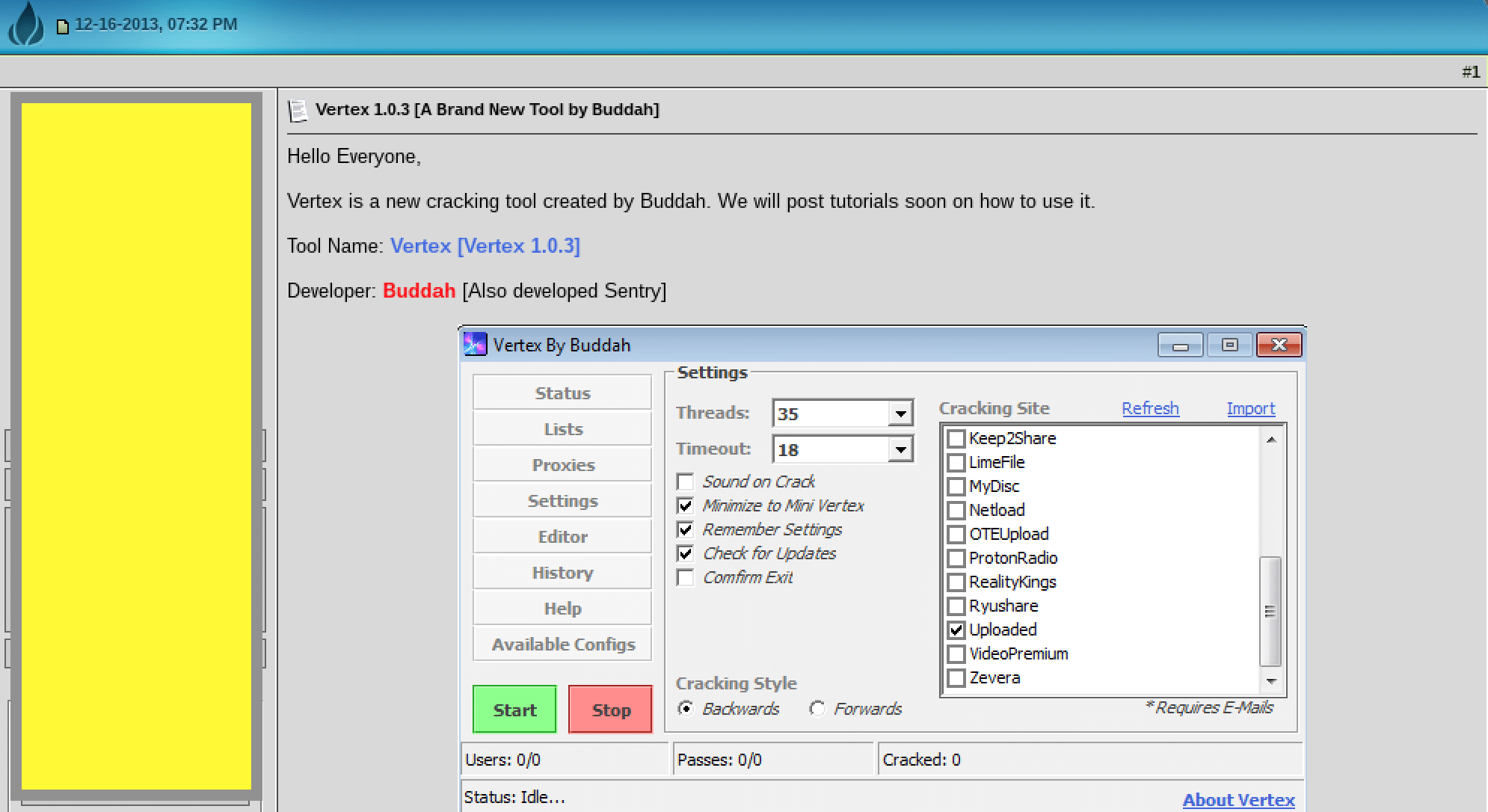
Figure 11: Vertex tool in use
- After downloading the Vertex tool, the attacker must download a combolist, a proxy list, and obtain a configuration file for the targeted site.
- The attacker opens Vertex and selects the configuration file for the targeted site, although Vertex allows for the selection of multiple sites.
- The attacker loads their proxy list.
- The attacker loads their combo file.
- The attacker presses “start” and the application brute-forces the targeted site,
Needless to say, this is not a particularly difficult task, even for those with limited technical abilities.
Unlike Sentry MBA, Vertex does not appear to have a captcha bypass feature. But it does have other advantages. Discussions in some cracking forums suggest that the tool was originally developed to “crack filehosts”, but it cracks and captures data from all form-login sites (given that they don’t include a captcha challenge). Vertex also comes with six standard configs since its release, and has been hailed as a relatively fast credential stuffing tool. Vertex is not as sophisticated as Sentry MBA, but many members of the cracking scene have written that it’s easy to use.
- BitShare
- FreakShare
- Keep2Share
- LimeFile
- Uploaded
- WIP Files
3. Apex
The Apex account cracking tool was also developed by “Buddah” earlier than SentryMBA or Vertex, possibly before 2010. Although Apex is older, it has been described a reliable tool, although it can’t crack SSL or HTTPS or, like Vertex, bypass captcha challenges.
The tool was originally released on MediaFire on April 7, 2013 and advertised on several cracking sites. Like Sentry MBA and Vertex, Apex Cracker also requires a config file, combolist and proxy list in order to work.
Apex also supports the use of standard HTTP and SOCKS5 proxies. According to some members of the cracking community, it can also handle database format cracking (id:pass formatting).
Figure 12: Download page for Vertex
4. Other Tools
Not every bruteforcing tool out there has been developed by “Senintel” or “Buhhda.” There are several other less popular tools that target only specific applications, or have accessory uses to cracking tools like Sentry MBA or Vertex. Some of these tools act as account checkers only for specific targeted services while others are designed to grab credentials from paste sites.
Figure 13: Screenshot of various custom tools advertised on a popular cracking forum.
Prevention is Crucial
Unfortunately, it’s virtually impossible to hinder the development of these tools their inputs and accessories. It’s also impossible to disrupt the thriving international online communities that continue to improve, trade and sell them.
However, organizations can prevent compromise by enforcing multi-factor authentication, use JavaScript anti-bot verification, and monitoring credential dumps. It’s especially important to monitor for dumps of third-party services that may be reused in combolists for cracking tools like the ones we described.
Criminals have adapted and will continue to adapt to new security mechanisms put in place by targeted organizations. A prime example is Sentry MBA’s captcha bypass mechanism, which was an adaptive update to Sentry 2.0. Given their ability to adapt, the only way to win against cyber criminals is to outpace them. Each time a new security feature is added, criminals must scramble to code new features into their tools, and this process takes time.
SpyCloud’s breach monitoring service can alert customers or employees to change their passwords immediately—this means that criminals who scrape public breaches for their combolists will find them no longer effective against a target that would have been otherwise cracked. These types of preventative measures can help mitigate account takeover attacks in your organization.
Sources:
- https://devcentral.f5.com/articles/mitigating-sentry-mba-credentials-stuffing-threat-24723
- https://leakforums.net/thread-74440+&cd=3&hl=en&ct=clnk&gl=us
- https://crackingspot.com
- https://blog.shapesecurity.com/2016/03/09/a-look-at-sentry-mba/