In an increasingly interconnected world, data breaches continue to be a major concern for organizations of all sizes. The IBM Cost of a Data Breach Report 2023 analyzes over 550 data breaches across 16 countries and reveals crucial insights about why the costs keep rising despite the growing number of vendor solutions, new security approaches, and employee training intended to mitigate breach threats. Let’s delve into the key findings and explore what they mean for security leaders and teams striving to build better defenses.
Must Be the Money: Cost of Data Breaches Reaches All-Time High in 2023
Most of us know that one of the greatest incentives for cybercriminals is financial gain. However, the costs associated with a breach don’t just line the pockets of the criminal – they also greatly impact the victim organization in terms of direct and indirect costs ranging from forensic experts to in-house investigations to customer turnover.
This year, the cost of a data breach reached an all-time high of $4.45 million. That’s more than a 2% increase from last year’s average cost of $4.35 million, and a 15% increase from 2020 when it was $3.86 million.
Whether you’re looking at the $4.45M average cost, the $5.13M average cost for ransomware-related breaches, or the higher average cost for breaches in specific industries and countries, we’re talking serious money. That’s no small impact for an enterprise-level organization, let alone a smaller business that may have no option but to shutter its operations. While costs and financial implications can scare even the most senior of leaders, it’s important to stay focused on defending initial attack vectors and implementing processes to detect attacks sooner (or at the very least mitigate the damage).
Key Takeaways from IBM’s 2023 Data Breach Report to Guide Your Security Strategy
Here are some interesting insights from the report that can inform your strategies and budget moving forward.
Stolen Credentials Remain a Common Attack Vector
Phishing and stolen or compromised credentials emerged as the two most common initial attack vectors, together responsible for 31% of breaches. This mirrors the findings from this year’s Verizon Data Breach Investigations Report that also highlighted stolen credentials as the #1 way criminals gain access to organizations. According to the report, breaches initiated by stolen or compromised credentials took the longest to resolve – an average of nearly 11 months – while costing $4.62M on average.
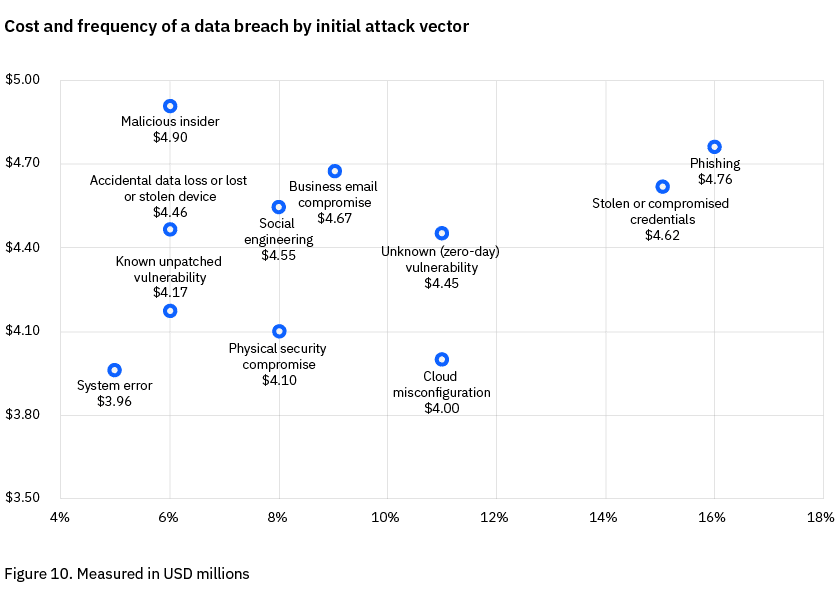
Source: IBM Cost of a Data Breach Report 2023
Moving forward, it’s more important than ever for organizations to recognize the risk of compromised credentials and reinforce their defenses against them. Prioritizing early detection of compromised authentication data, whether credentials or cookies that enable session hijacking, along with automated and rapid remediation, significantly reduces the risk of breaches and other destructive attacks.
Costly Ransomware Attacks
Ransomware accounted for a significant proportion of malicious incidents outlined in IBM’s report – comprising 24% of attacks. And these incidents cost 13% more on average to resolve.
This report doesn’t get deep on the newest ways ransomware is perpetrated – like how it’s often the end result of a longer chain of attacks starting with a malware infection. This report is about the cost of data breaches experienced by an organization, but we do want to take the opportunity to re-iterate that even breaches outside of your own organization can affect your business. When a third-party is breached and your employees’ credentials are exposed, they can be used to access your critical applications that house sensitive corporate data, may be used to move laterally within your network and escalate privileges, and gain the criminal access to additional data that aids a ransomware attack. For more on this, check out our Malware Readiness and Defense Report, which goes into more depth on why ransomware is a malware problem, and what security teams can do to reduce ransomware risks from infected employee and contractor devices.
Attackers Shift Data Breach Focus to Target Vulnerable Small Businesses
It’s more important than ever for security teams of any size in organizations – but especially in smaller organizations – to invest in proactive security measures to mitigate the financial consequences of a breach. Prioritizing security posture improvements by implementing robust security measures, such as employee training, threat detection, and incident response planning can go a long way in not only combating these threats, but in surviving them.
Investing in Security Today to Save Later
Learning from past incidents and investing in measures that can prevent, detect, and respond to future cyberattacks is vital. The report found that 51% of organizations planning to increase their security investments in response to a data breach – somewhat surprising given how purse strings tend to open after security incidents that make a company front-page news, but macroeconomic issues may be at play. What investments are the most critical? What will deliver immediate value, bolster existing investments and tools, and reduce the risk of a breach or its after-effects?
Continuous compromised credential monitoring & remediation: Actively monitoring for compromised credentials and other forms of stolen authentication data (including cookies), API keys, and webhooks, and taking action through existing SOAR tools shortens the exposure window and reduces breach risk substantially without burdening already busy teams.
Next-generation threat intelligence: Organizations that leverage threat intelligence identified breaches 28 days faster, and that’s true even though most threat intel isn’t immediately actionable. Moving beyond raw data and broad context about the threat landscape and instead getting access to the information that criminals know about your business and employees that’s making you a target for data breaches – that is what truly mitigates the risk of a breach from the compromised credential attack vector.
Incident response: IR was called out in the report as instrumental in reducing the impact of data breaches – and identified as a top area of investment post-breach. We have thoughts on bolstering incident response processes to stop one cyberattack from causing a chain reaction that leads to ransomware. Check out more on Post-Infection Remediation, a framework that can make all the difference in minimizing the risk of targeted attacks that leverage stolen authentication data.
The IBM Cost of a Data Breach Report 2023 provides plenty of valuable insights for security leaders and teams to avoid the fate of companies that experienced recent data breaches. By investing in incident response, threat detection, and automation, organizations can significantly reduce breach impact and cost, while maintaining a robust security posture to combat evolving cyber threats. A proactive and comprehensive approach to security will be the key to safeguarding sensitive data and maintaining customers’ trust in an increasingly digital world.