“The more things change, the more they stay the same.”
In its 15th annual report, the Verizon 2022 Data Breach Investigations Report analyzed 23,896 security incidents, of which 5,212 were confirmed data breaches, to provide key insights into the data breach problem. Not only did this year’s report include the annual analysis, in a nod to the report’s 15-year “anniversary,” Verizon also offered insights from past years, sprinkling the report with throwback references and data points to show how far we’ve come in some regards, but also how things may still be the same in others.
We eagerly anticipated the report drop, and as per usual the analysis did not disappoint. Here are the key takeaways we found most insightful.
Stolen Credentials: The #1 Entry Point
Similar to last year’s report, Verizon reiterated its belief that criminals prefer credentials, as they represent “one of the most tried-and-true methods to gain access to an organization for the past four years.”
We’ve long held that Credentials are the favorite data type of criminal actors because they are so useful for masquerading as legitimate users on the system. There is also a large market for their resale, which means they are truly the ‘gift’ that keeps on giving.
Stolen credentials are pervasive throughout the report, with the need for proper password security highlighted most explicitly with regards to Basic Web Application Attacks (BWAA), or attacks on an organization’s most exposed infrastructure, such as a web server. A whopping 80% of these breaches result from the use of compromised credentials, with exploiting vulnerabilities and brute force attacks a distant second and third, respectively. Closing off this pathway into an organization involves both robust password standards and proactive monitoring for exposed credentials to prevent account takeovers (ATO).
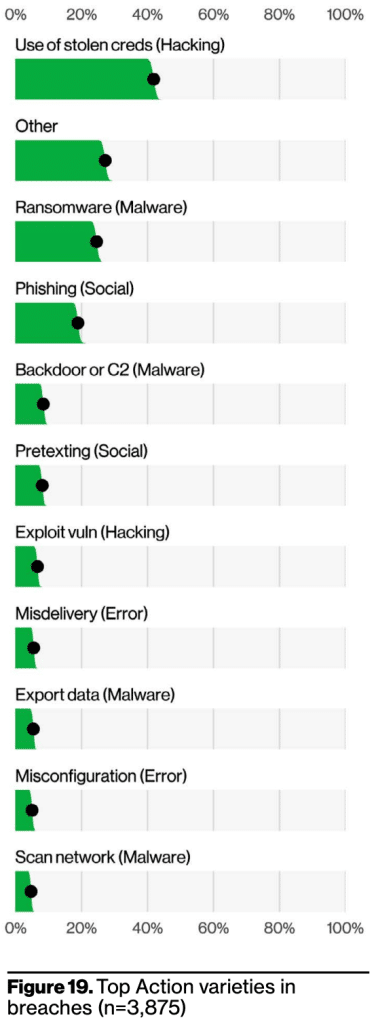
The report indicated an almost 30% increase in stolen credentials since 2017, and we’ve observed the same trend. In our 2022 Annual Identity Exposure Report, we analyzed more than 1.7 billion credential pairs (combinations of email address/username and password) recaptured from the criminal underground and found that credential exposure increased 15% year over year. Exposed credentials fuel ATO, which is often a precursor to ransomware. Therefore the rise in exposed credential data is intimately tied to the rise in ransomware.
Ransomware (and Malware In General) Runs Rampant
According to the report, ransomware has unsurprisingly continued its upward trend over the years. But shockingly in 2021, there was an almost 13% increase, accounting for ransomware being present in 25% of breaches – a jump as big as the last five years combined! SpyCloud’s own 2021 Ransomware Defense Report backs up these findings, with 72% of organizations surveyed saying they have been affected by ransomware in the past 12 months.
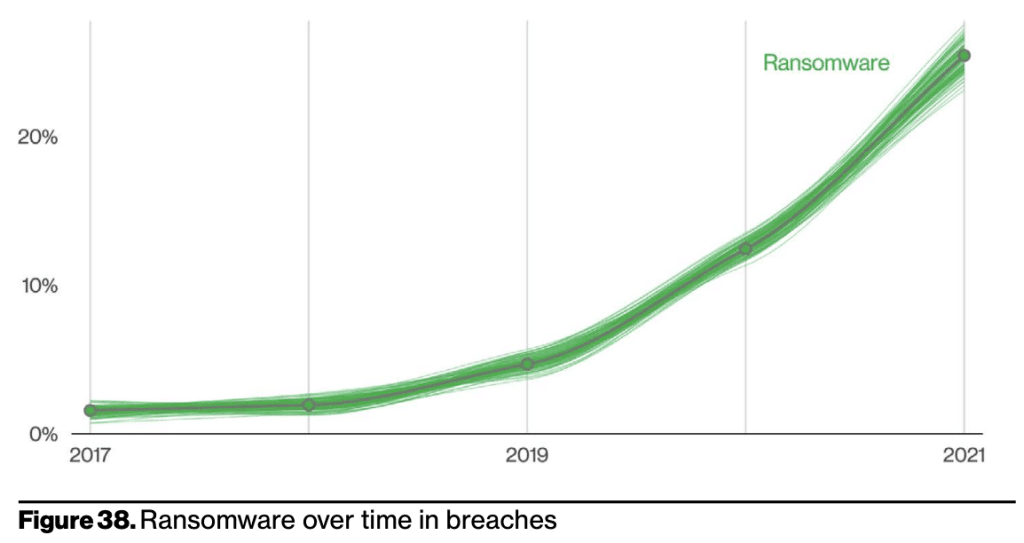
Ransomware was present in 25% of breaches in 2021, according to Verizon’s analysis. Source: Verizon 2022 Data Breach Investigations Report, pg 27.
So what makes ransomware so prevalent? We’d argue the minimal cost of access has a lot to do with it. Credentials, vulnerabilities, and botnet access needed to execute ransomware attacks can be purchased from initial access brokers relatively cheaply, and successful attacks can garner six- or seven-figure profits.
“Once attackers are inside the victim’s network they often install malware, which violates the Integrity of a system (as does any other illicit change)…The installation of malware was already quite common back in the day, and our data shows that this year is no exception, with over 30% of breach cases involving some type of malware.”
Malware remains the second highest breach action, coming behind only hacking via stolen credentials, a trend that has remained steady since the initial 2008 report’s findings. The key difference today is that malware has now evolved to the point where it can siphon all the data that’s needed to impersonate an employee beyond credentials, including browser fingerprints and web session cookies – and when malware is on a personal device the employee is using to access work applications, it poses an invisible threat to enterprises.
To Err is Human
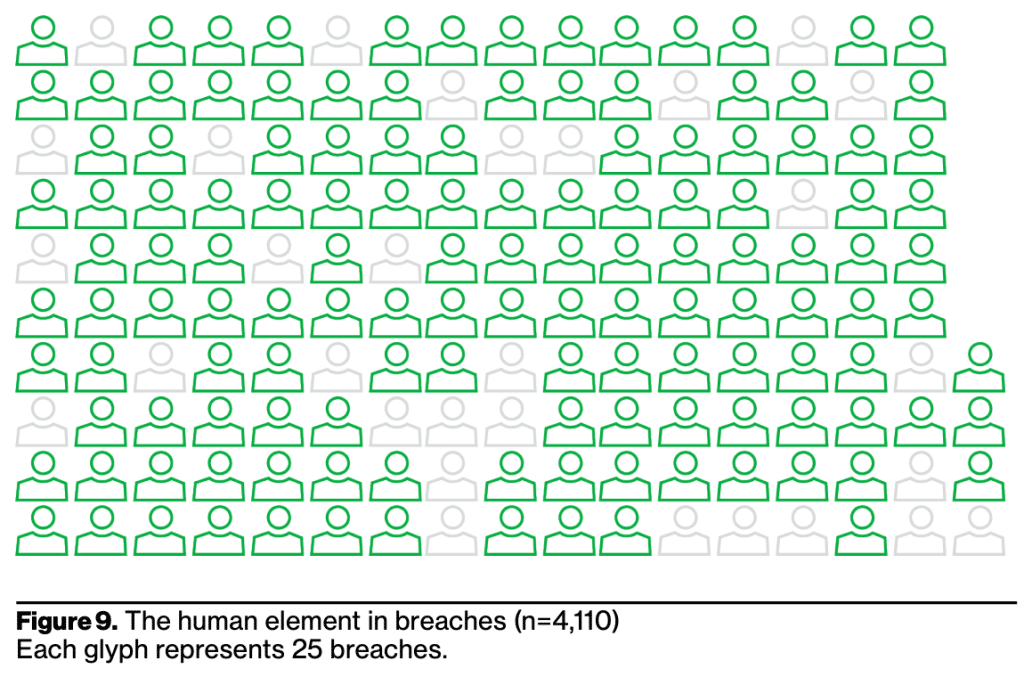
Source: Verizon 2022 Data Breach Investigations Report, pg 8
The human element remains a significant driver for breaches: “This year 82% of breaches involved the human element. Whether it is the Use of stolen credentials, Phishing, Misuse, or simply an Error, people continue to play a very large role in incidents and breaches alike.”
People and their unfortunate poor habits, that is. Bad password hygiene makes it all too easy for criminals. Our analysis found a 64% password reuse rate for users with more than one password exposed in the last year.
Despite an organization’s best efforts to empower employees with enhanced password requirements and robust security training, the fact remains that people continue to be a weak link in an organization’s security framework.
The supply chain is no exception. Within third-party breaches, the use of stolen credentials was the top action variety (followed by ransomware). Our take? It’s not enough for enterprises to monitor and remediate only their own employees’ risk of account takeover; they must also have an eye on their partners’ ATO risk.
Conclusion
The report is clear: stolen credentials, ransomware (and malware in general), and human behavior all pose problems when it comes to preventing data breaches. But there’s hope. This year’s report offers proactive steps to protect your organization and enhance your security posture that we can get behind:- Use antivirus and anti-malware solutions
- Implement patching, filtering and asset management to prevent exposed vulnerabilities
- Standardize multi-factor authentication (MFA) and password managers to minimize credential exposure
- Enable email and web filtering, along with security awareness training

