
PRODUCT: CYBERCRIME INVESTIGATIONS
UNCOVER THE ACTORS BEHIND CYBERCRIME FASTER
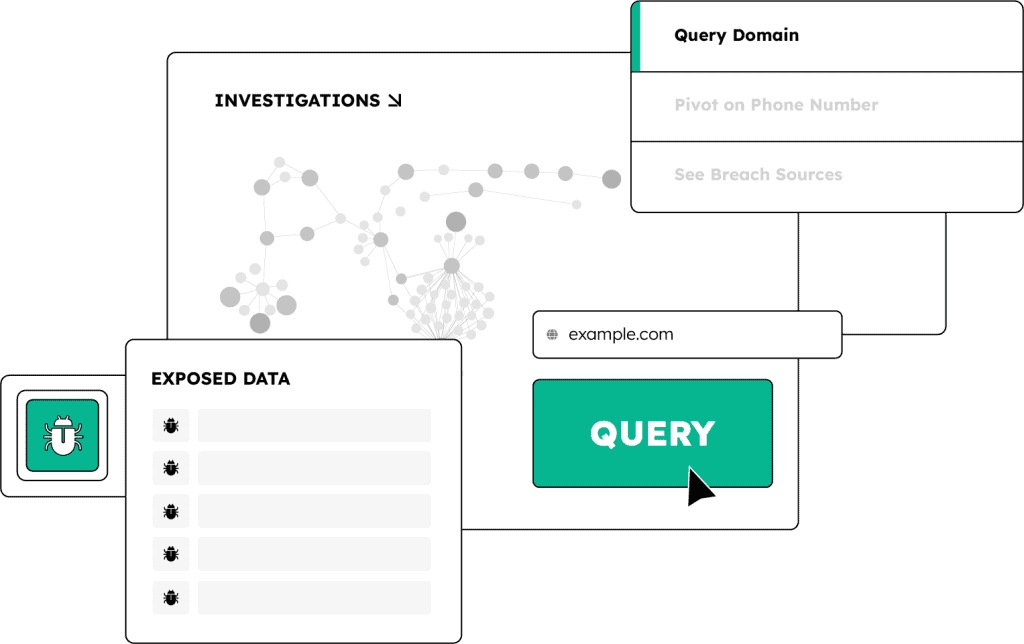

Investigate cybercrime, starting at the identity level
Cybercrime investigations stall when identity data is fragmented, incomplete, or buried in noise. SpyCloud Cybercrime Investigations brings identity to the center of your investigations, connecting breach, malware, and phishing exposures to reveal who’s involved, how they’re connected, and where to act next.
Start with a single selector – like an email address, username, phone number, domain, or IP – and pivot to uncover hidden relationships, alternate personas, and infrastructure tied to cybercrime activity.
Identity-centric investigations surface patterns of life and attribution signals that help analysts understand who’s behind the activity, not just what happened.
Raw data doesn’t stop threats – decisions do. Automated analytics and AI-driven insights transform complex identity exposure data into clear investigative findings.
Explore powerful workflows & capabilities to aid your cybercrime investigations
SpyCloud Investigations powered by AI is really a paradigm shift because now investigators can do investigations at scale with AI driving the analytics. It lowers the sophistication and threshold that an investigator needs to have. It takes away the mundane portion of the investigation and speeds that part up. SpyCloud Investigations is meant for analysts and investigators, both public and private, all skill levels, to look for attribution of actors, and also understand communities of actors and their infrastructure. SpyCloud augments every single analyst within a SOC with an AI expert, turning what could take hours into seconds in a report that they can share out with their team. SpyCloud data can be used to uncover malicious, so witting insider threat, as well as unwitting or innocent victim, insider threat examples. SpyCloud gives visibility into fraud campaign infrastructure and insider threat in a way that no other tool does. Ready to expedite your investigations? Go to spycloud.com.
Close gaps faster with AI Insights
“By combining speed, clarity, and depth of intelligence, SpyCloud Investigations with AI Insights sets a new benchmark for how modern security teams should approach threat investigations.”
– Jacques Chitarra, Sr. Director of Global Security & Privacy, Samsonite
USE CASES
Cybercrime investigations powered by recaptured data
Built for analysts who need direct access to the world’s richest recaptured darknet dataset to use alone or alongside OSINT data sources. SpyCloud powers analyst workflows with the richest darknet data API for cybercrime investigation and identity threat intelligence.
Threat Actor Attribuion
Infected Host Identification
Financial Crimes Anaysis
Supply Chain Exposure Analysis
Insider Risk Analysis
Identity Exposure Analysis
Choose how you deploy SpyCloud Cybercrime Investigations
Same intelligence. Two ways to operationalize it.
Best for teams who want fast answers – no code required.
The Cybercrime Investigations Module delivers analyst-ready workflows that dramatically reduce the time it takes to move from raw exposure data to finished intelligence. Built-in automation, IDLink analytics, and AI Insights help analysts of all skill levels conduct deeper investigations in minutes, not hours or days.
- Up-level your analysts – Investigative workflows automate the process of pinpointing identity exposures, increasing team productivity, discovery, and resolution.
- Reveal hidden connections – Identify linkages and automatically piece together a holistic view of a digital identity in seconds, instead of hours of advanced analysis.
- Act on tradecraft-driven AI Insights – Transform scattered exposure data into finished intelligence in seconds. AI Insights applies tradecraft expertise to detect suspicious patterns and surface attribution signals.
- No-code investigations
- Automated identity pivoting
- Automated identity pivoting powered by IDLink analytics
- Visual link analysis to uncover hidden connections
- AI Insights that transform complex exposure data into finished intelligence
- Start with a single selector (email, username, phone number, etc.)
- Automatically pivot across identity assets using IDLink analytics
- Visualize relationships and uncover hidden connections
- Visual link analysis to uncover hidden connections
- Generate finished intelligence with AI Insights
The Cybercrime Investigations API provides direct access to SpyCloud’s recaptured darknet intelligence for teams that need full control over how investigations are conducted. Integrate SpyCloud data into existing tools, automate enrichment at scale, and perform advanced analysis across custom workflows.
- Gain speed & efficiency – Drastically shorten the timeline of your cybercrime investigations with deep results off a single data point.
- Correlate multiple data sources – Connect SpyCloud’s Investigations API with other data sources like VirusTotal and Whois for even more context.
- Illuminate the previously unknown – Reveal threat actors, alternate personas, criminal campaigns, and new angles of investigation.
- Programmatic access to recaptured identity data
- Flexible querying across emails, usernames, IPs, domains, and more integrations with tools like Maltego, Splunk, and Jupyter Notebook
- Query SpyCloud data programmatically
- Correlate identity data with internal or third-party sources
- Automate enrichment, attribution, and analysis
- Power custom workflows, dashboards, and investigations
What analysts achieve with SpyCloud
"SpyCloud Investigations with IDLink has drastically reduced our investigation time, turning 2 hours of SOC work into just a few minutes."
SOC Manager, Global Airline
“SpyCloud Investigations delivers a level of comprehensive threat analysis that previously took our most experienced analysts hours to achieve.”
Senior Director of Global Security & Privacy,
Samsonite
"With SpyCloud Investigations, we have been able to uncover and address gaps we would have never known about in our suppliers' cybersecurity practices. Now we can enforce higher security standards across our entire supply chain."
Senior Director of Global Security & Privacy, Global Manufacturing and Retailer
EXPLORE MORE PRODUCTS
Know more, do less
Trusted by CTI, SOC, identity, and fraud & risk teams to expose hidden risk, accelerate investigations, and stop identity-based threats.
Workforce Threat Protection
Prevent account takeover attempts by identifying exposed employee credentials
Endpoint Threat Protection
Next steps
Pick a better starting place for your next investigation.
Request a demo today.