Given the explosion of digital services in recent years and the global shift to remote work in 2020, most people are juggling more online logins than ever. It’s no wonder that users commonly fall back on weak and reused passwords that are easy to remember—and just as easy for criminals to exploit.
Bad password hygiene puts enterprises at risk, leaving corporate assets within easy reach of malicious actors. Even at America’s largest companies, a data breach that reveals an employee’s reused password or personal information can help a criminal sidestep sophisticated security measures and gain privileged access to corporate resources. Each new breach provides bad actors with more stolen data to exploit.
For the second year in a row, SpyCloud has identified and analyzed millions of breach assets tied to employees of Fortune 1000 companies to demonstrate the scope of breach exposure affecting large enterprises. To do this, we sifted through our database of over 100 billion breach assets to find records containing Fortune 1000 corporate email domains, excluding “freemail” domains that are available to consumers. For example, if a Fortune 1000 employee used their corporate email address, example@employer.com, to sign up for a third-party site that was later breached, we were able to tie their breached account information to their employer.
Check out a summary of key findings below, and get the full report here (including infographics for all 21 industry sectors).
The volume of breach data tied to Fortune 1000 employees is staggering.
Overall, we found over 543 million breach assets tied to Fortune 1000 employees, a 29% increase from last year’s report. Across all industries, nearly 26 million plaintext passwords belonging to Fortune 1000 employees are available to cybercriminals, which means an average of 25,927 exposed passwords per company (a 12% increase from last year).
From passwords to financial information, each piece of stolen data can help a bad actor take over an employee’s accounts, steal their identity, blackmail them, or trick them into dangerous behaviors. The problem doesn’t stop with employees’ personal accounts; enterprises represent lucrative targets for cybercriminals and stolen employee data can play a key role in enabling bad actors to bypass corporate security measures. Enterprises need to know what breach data can be tied to their employees and take action to mitigate the threat posed by employee account takeover.
Even among Fortune 1000 employees, password reuse across multiple accounts remains rampant.
For obvious reasons, we can’t test exposed passwords to find out which ones have been reused at work. However, across all employees with more than one password exposed, we saw a 76.7% rate of password reuse. If employees reuse passwords this frequently outside of work, it’s likely that many have recycled their corporate logins as well.
Criminals count on password reuse, which enables them to take over accounts by testing stolen credentials against other login portals. This may take the form of automated credential stuffing against a broad range of sites and victims, or targeted attacks that are manual, creative, and tailored to specific individuals or organizations. Even with strong security measures in place, recycled passwords can provide a way for cybercriminals to sidestep corporate defenses and access enterprise secrets. To lock out bad actors, enterprises need to be aware of new breach exposures and reset compromised passwords as quickly as possible after a new breach occurs.
Password reuse isn’t the only bad security habit revealed in our dataset. Fortune 1000 employees are also guilty of choosing weak passwords to protect their accounts. While this may not seem important in the case of a third-party account, bad actors can use one account to pivot to others and increase their access. Plus, bad habits at home often translate to bad habits everywhere.
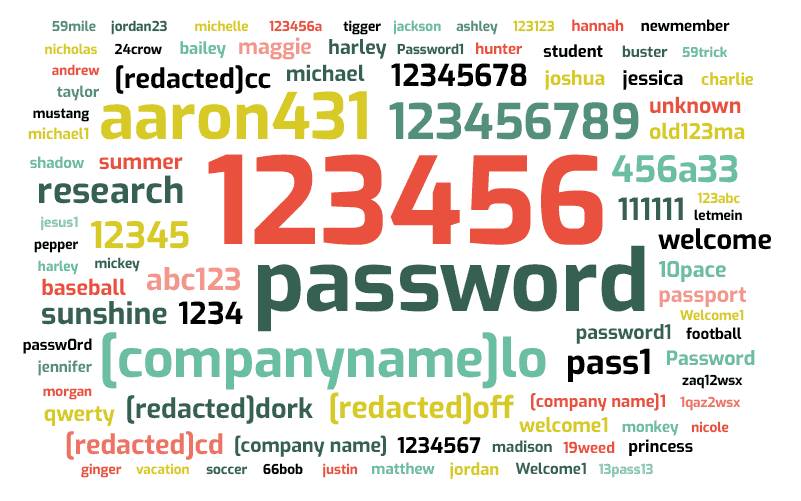
Here are the most popular passwords we found in our dataset tied to Fortune 1000 employee emails:
Telecommunications and Technology companies have the most exposed corporate credentials and potentially infected employees.
In total, the Technology sector has the most exposed credentials (6.7 million) and by far the largest number of potentially infected employees (13,897), meaning employees whose credentials have been captured by malware. Telecommunications comes next by total count (6 million and 2,328 respectively). Averaged out per company, however, the Telecommunications sector fares the worst in both categories, with an average of 552,601 exposed credentials and 212 potentially infected employees per company, compared to 61,747 and 127 respectively per Technology company.
While all exposed credentials can put enterprises at risk, employees using systems infected with malware are particularly dangerous. That holds true regardless of whether the infection is located on the employee’s personal or corporate system, both because of the breadth of data collected and the high likelihood of crossover usage between devices. Within SpyCloud’s botnet data, we regularly see evidence that employees have used infected personal devices to access enterprise resources, a trend that has only been exacerbated by the sudden transition to remote work. If an enterprise identifies an employee using an infected device, it’s imperative to intervene as quickly as possible.
Speaking of infected users, the Technology sector landed at the top of another list: infected consumers. Although the scope of our research excluded consumer-only domains, we were still able to identify over 11 million consumers of Fortune 1000 companies whose credentials were captured by keyloggers. A staggering 7.8 million of these users are consumers of Technology sector companies (about 70%).
To learn why consumer malware infections are problematic and what enterprises can do about them, check out our Infected User Response Guide.
In the context of 2020 supply chain breaches, bad passwords in Aerospace & Defense raised our eyebrows.
Six of the top 10 most popular passwords of the Aerospace & Defense sector include company names. While company names are popular password choices across all sectors, it’s unnerving to see the names of major defense contractors pop up as popular passwords for employees in that sector–particularly when you consider that these breaches come from third-party sites.
If Aerospace & Defense employees are using company names as the passwords of third-party sites, it’s likely that they’re making similar choices at work—and it’s also possible that those third-party accounts are work-related. Easy-to-guess passwords provide little protection for corporate resources and can help facilitate not only illegitimate access to enterprise secrets, but also farther-reaching supply-chain attacks.
Credentials for 133,927 Fortune 1000 C-level executives are available to criminals–and 29% are from the Financials sector.
The Financial sector alone has over 39,328 exposed C-level executives. On average, however, the Hotels, Restaurants & Leisure sector has the most exposed executives per company: 320 per company, versus 243 per company in the Financials sector.
Data from exposed C-level executives can pose more risk to their employers than data connected to other employees, since their high-profile titles and privileged access can make them compelling targets for criminals. Enterprises should monitor high-risk executives closely for new breach exposures, including both their corporate and personal accounts. Resetting compromised passwords quickly can lock criminals out of vulnerable accounts.
Conclusion
Employee breach exposure puts organizations at risk, and even America’s largest enterprises are not immune. Security teams need to take proactive steps to protect against employee account takeover that can endanger critical corporate assets.
