For a more recent analysis and set of predictions from our team, read:
The Identity Security Reckoning: 2025 Lessons, 2026 Predictions >
2024 has been busy for SpyCloud and security practitioners everywhere. From monumental data leaks to new insights into how the cyber underground operates, SpyCloud tracked some of the top threats shaping the security world.
In this month’s security recap, we’ll cover recent happenings, recap big events from the past year, and spend a little time musing over industry predictions for 2025.
Arrests and charges against “the Com” hackers
Over the past month, law enforcement agencies announced new arrests and charges against multiple individuals tied to “the Com,” a loosely affiliated group of criminal hackers from Western countries like the US, UK, and Canada, mostly in their teens and early 20s. Researchers tracking the Com have spoken about how it serves as a radicalizing environment for young people, many of whom are introduced to the community through gaming platforms. In addition to criminal hacking, these communities have also been linked to coordinated harassment campaigns in which they threaten, bully, dox, and harass minors to coerce them into producing violent content and harming themselves. CrowdStrike tracks multiple threat actor groups within the Com ecosystem under the now well-known “Scattered Spider” intrusion cluster name.
The first set of charges were announced against key figures in “Star Fraud,” a smaller group within the Com that is responsible for many high-profile intrusions over the past few years, including sim swapping, ransomware attacks on casinos, and data theft and extortion attacks against cloud service accounts
Canadian authorities arrested Alexander Moucka (a.k.a. Connor Riley Moucka) on October 30. Moucka is a 25-year-old Canadian man who is a central figure in Star Fraud; he goes by the handles Judische and Waifu. On November 5, he appeared at a court hearing as part of his extradition process to the United States; he had not yet retained a lawyer. Following Moucka’s arrest, US authorities unsealed their indictments against Moucka and another Star Fraud-affiliated hacker John Erin Binns (a.k.a. IRDev, IntelSecrets), who was arrested in Turkey in May and remains in Turkish custody. Unlike Canada, Turkey does not extradite criminals to the United States. On November 26, journalist Brian Krebs also published a blog post identifying a third individual, who goes by the handle Kiberphant0m, as a U.S. Army soldier who is or was recently stationed in South Korea.
On November 20, the FBI unsealed criminal charges against five more hackers tied to “the Com.” Four of the charged individuals (Ahmed Hossam Eldin Elbadawy, Noah Michael Urban, Evans Onyeaka Osiebo, and Joel Martin Evans) reside in the United States, and the fifth (Tyler Robert Buchanan) resides in the United Kingdom. All of them are currently between the ages of 20 and 25. These five individuals were part of the group responsible for the 0ktapus phishing campaign, which impersonated legitimate identity and access management services to phish users and compromise their corporate accounts. A sixth hacker associated with the group – a 19-year-old teenager – was also arrested a few weeks later in December.
Telegram content crackdown continues
As we covered in last month’s cybercrime update, Telegram founder Pavel Durov was arrested by French authorities in August for hosting illegal activity on the Telegram platform and allegedly not complying with law enforcement data requests. Since then, we have observed a marked increase in the rate that Telegram channels related to crime and fraud are being taken down. Still, the vast majority of channels discussing fraud, scams, malware, hacking, and cybercrime tracked by SpyCloud continue to exist on the platform.
On October 31, we also observed the deactivation rate of channels we actively track – measured as the number of channels deactivated on a single day as a proportion of all channels that have been deactivated year to date – rise to approximately 20%, indicating that substantially more channels were removed on that day than on previous days. A review of the channels deactivated on this date revealed that the overwhelming majority involved the distribution or discussion of infostealer malware logs.
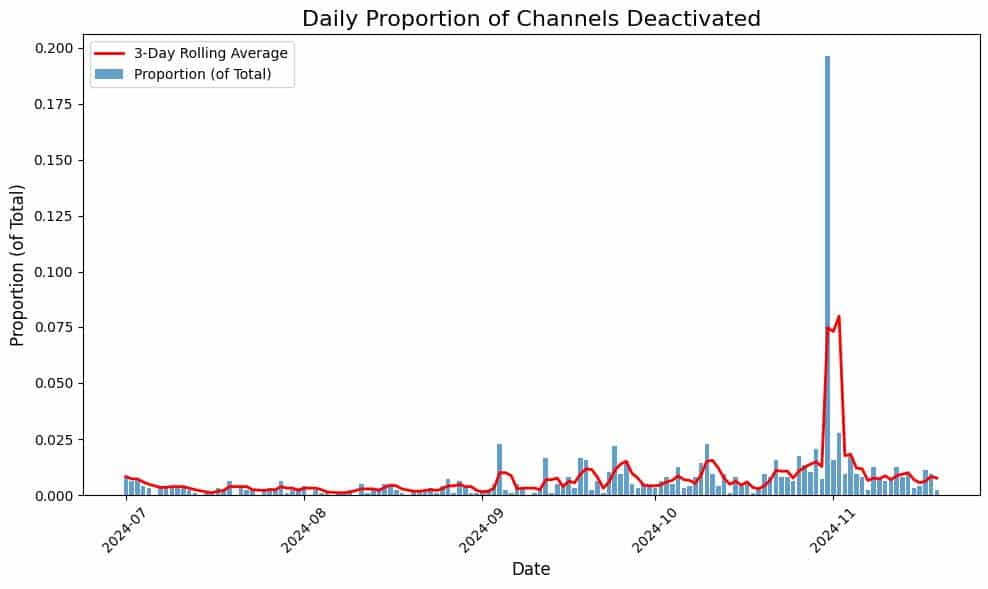
Telegram began cracking down on illicit channels in September of 2024, with a significant spike in channel deactivations occurring on Halloween (October 31). This chart shows the proportion of channels deactivated by day, measured based on the total number of channels deactivated year-to-date.
We have also noticed that some search terms related to cybercrime appear to be shadow-banned by Telegram. Users now need an exact channel name or link to surface some of these crime-related channels, instead of being able to search for relevant keywords and return all of the public channels with those terms in their names and descriptions via Telegram’s search feature.
SpyCloud Labs has observed actors moving to different platforms to advertise their crime-related offerings, many of them still linking back to Telegram accounts or private Telegram groups to make sales. We believe that this is likely a response to the increased content moderation on Telegram including the measures that they took to shadow-ban key crime-related search terms from Telegram search. Earlier this month, SpyCloud Labs published a blog detailing how cybercriminals appear to be posting stolen credit card information to Threads (Meta’s X competitor). Many of these accounts appear to be posting stolen cards to Threads as advertisements for premium stolen financial data offerings that they still sell and distribute on Telegram.
Nam3L3ss reposts old MOVEit data
Beginning on Friday, November 8, a threat actor with the handle Nam3l3ss began reposting data from old Cl0p ransomware breaches to the BreachForums data leak and hacking forum. Thus far, this account only appears to have posted data from previous data leaks. The majority of the data appears to have been originally hacked and leaked by the Cl0p ransomware gang in May 2023, when they mass exploited a vulnerability in the MOVEit file transfer software and posted data from hundreds of organizations on their data leak site.
On November 12, the actor also posted a “manifesto” to BreachForums, which stated that they were reposting this data for ideological reasons, to motivate “Governments to take PII data seriously and hold Companies liable.”
Some organizations that were not explicitly named by Cl0p during the MOVEit breach appear in these data reposts because their data was contained in breaches of third parties. Most of the data reposted thus far, including employee data for high-profile organizations like Delta and Amazon, are actually from just two Cl0p breaches: Jones Lang LaSalle (JLL) and Pension Benefit Information (PBI) Research Services. These reposts underscore how important it is for organizations to monitor their third-party breach exposure (i.e. when an organizations’ sensitive data is compromised through a third party vendor, supplier, or contractor).
Phishing campaigns leverage Google Docs and Weebly website builder
Over the past few months, SpyCloud has observed a phishing campaign in which threat actors are leveraging the Weebly free website builder service to host phishing landing pages. These pages all appear to take advantage of Weebly’s free subdomain option, meaning that they appear in the following formats: <subdomain>.weeblysite[.]com or <subdomain>.weebly[.]com. Most of the phishing pages that we have observed appear to impersonate portals for North American and European telecommunications providers and banks.
Screenshot of a phishing landing page at bt-106197[.]weeblysite[.]com which impersonates a customer login page for British Telecom.
EclecticIQ also wrote about this campaign, noting that the threat actors appeared to drive traffic to these landing pages through Google Docs. The threat actors shared presentations hosted on Google Docs with targeted users. These presentations contained embedded links to the Weebly landing pages, which trick victims into entering their login information for their bank or telecommunications carrier.
Earlier this year, SpyCloud Labs expanded our efforts to recapture breached, leaked, and stolen data by collecting data from phishing pages and phishing kits. We are continuing to monitor this campaign as new landing pages continue to pop up every day.
The Real World breaches
On November 21, a group of hacktivists revealed that they had hacked Andrew Tate’s popular “The Real World” platform by flooding its chatrooms with emojis and providing data from the platform’s 221 public and 395 private chat servers to journalists as well as DDoSecrets. The Real World, previously called “Hustler’s University,” is a subscription-based platform that includes course content teaching subscribers how to make money online using methods such as cryptocurrency investing and content creation. Subscribers also gain access to hundreds of public channels on a discussion forum that functions similarly to Discord.
In addition to chat logs, this leaked data also appears to include over 320,000 unique email addresses from a running list of deactivated users that was being maintained in one of the private chatrooms. Most of the users on this list appear to have been deactivated when their subscriptions to the platform expired, but some also appear to have been banned from the platform according to notes kept on this list.
The data breach contains extensive chat logs from both public and private chatrooms; each message is tied to a 26 character user ID. The breach also contains a users table which ties those user IDs to username, but there is no additional data within this breach that allows you to easily connect active account user IDs to real-world identities.
However, SpyCloud researchers were able to identify a less widely reported data breach from The Real World that was discovered on an unsecured MongoDB database in July. By combining both datasets, we have enough information to link users to real-world identifiers such as emails, passwords, and password reset tokens.
What’s new this month with SpyCloud’s recaptured data collection
SpyCloud detects when employee and customer credentials, cookies, PII, and other critical stolen assets are in the hands of cybercriminals and so you can reduce your risk of cyberattacks.
We rigorously cleanse and parse recaptured data assets stolen in data breaches, from malware-infected devices, and via successful phishes – then crack passwords, further enrich the data, and correlate it to individual user identities so you can see and stop threats to your enterprise.
November Monthly Total
Total New Recaptured Data Records for November:
744,883,598
New Third-Party Breach Data
Third-Party Breaches Parsed and Ingested:
291
New Data Records from Third-Party Breaches:
49,376,104
New Infostealer Malware Data
Stealer Logs Parsed and Ingested:
320,100
New Data Records from Stealer Infections:
15,335,937
New Stolen Cookie Records:
680,171,557
New Stealer Family Coverage
AsyncRAT: AsyncRAT is an open source Remote Access Tool created to remotely monitor and control Windows devices; it was originally released in 2019. It is often used maliciously by cybercriminals because it is free, easy-to-use, and includes robust functionality. Using AsyncRAT, attackers can log keystrokes, remotely control the desktop, and load additional malware onto an infected machine. It also encrypts command-and-control (C2) traffic and can be configured to include anti-analysis techniques. While AsyncRAT has been used by threat actors in the wild for nearly five years, SpyCloud has observed a recent uptick in stealer logs from successful AsyncRAT infections.
Blank Grabber: Blank Grabber is another open source stealer written in Python. The system information and running process data within the stealer logs from Blank Grabber are notable because they match whatever system language the infected host is set to use. This appears to be because this data is captured using default Windows commands, such as the “systeminfo” command, instead of relying on the malware itself to parse this data from various locations on the infected host. Thus far, we have recaptured Blank Grabber logs in English, Spanish, French, and Portuguese.
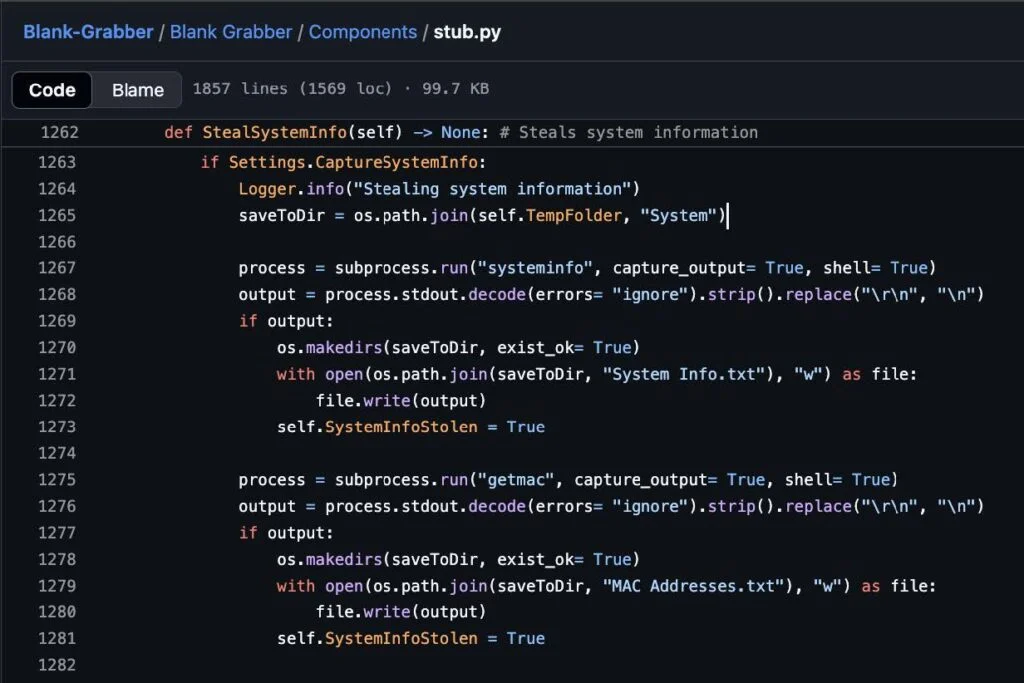
Screenshot of the Blank Grabber source code showing the StealSystemInfo function which uses the default ‘systeminfo’ Windows Command and simply dumps the output stream into the “System Info.txt” file.
Unidentified Eos Stealer (macOS): We have also begun to recapture stealer logs for a new, still unidentified macOS stealer that we are currently tracking as ‘Unidentified Eos Stealer.’ Like the Banshee and Atomic macOS stealers, the Unidentified Eos Stealer appears to pull data from the Keychain – Apple’s native password management system – and is capable of stealing the macOS login password.
Top cybercrime events and trends in 2024 – and what we learned
Here’s a recap of some of the most important stories we covered through our research and analysis in 2024.
This major breach dropped 2.7 billion records, including personal identity data like social security numbers, raising huge concerns about identity fraud and phishing. SpyCloud dug into the risks posed by the exposed NPD info, highlighting how criminals might exploit it for new account fraud and social engineering.
Our takeaway? With criminals exploiting the interconnected web of darknet-exposed identity data, staying vigilant with continuous identity monitoring for both your employees and customers is more important than ever. Incorporating holistic identity threat protection into your cybersecurity and fraud prevention programs gives you the power back to protect your business from exposed identity assets like those leaked in the NPD breach by rendering stolen data useless to criminals.
Chrome’s new app-bound encryption sounded promising, but cybercriminals quickly found ways around it. By exploiting a debugging API, new infostealer malware, including Phemedrone Stealer, bypassed Chrome’s defenses to nab authentication cookies. Our analysis emphasized the need for a defense-in-depth approach to security, so that defenders have multiple layers of protection to continue to catch attackers when they inevitably bypass security mechanisms.
Macs aren’t as untouchable as we historically liked to think. SpyCloud’s reverse engineering of the Atomic macOS Stealer highlighted how sophisticated malware is targeting macOS users, stealing sensitive data and bypassing permissions. The insights gave a peek into the malware’s inner workings, including some of its sneakier features as well as some indicators defenders can use to catch it in action.
Today’s cybercrime ecosystem offers plug-and-play options – think Malware-as-a-Service – that make it easy for anyone to get into the game. From crypters to residential proxies, the underground market has democratized cyberattacks, putting high-stakes hacking tools in less-skilled hands. Our research unpacked these services, showing the reality of how criminals are scaling up their operations.
Phishing attacks took off this year, not just in volume but in sophistication. SpyCloud tracked evolving phishing techniques, like convincing fake login pages and creative social engineering tactics, that lure people into handing over sensitive information. For businesses, this means a sharper focus on employee training and phishing-resistant security protocols, and having the tools in place to remediate successfully phished data when the inevitable happens.
The findings from our 2024 Identity Exposure Report showed the vastness of the stolen data problem, underscoring a strong shift to identity-based cyberattacks. Sure, stolen credentials are still a popular tool for criminals to gain initial entry to systems and applications. But digital identities have evolved well beyond the traditional username and password combinations. All signs this year point to malicious actors being super scrappy, piecing together each piece of data they steal to exploit it in account takeover, ransomware, session hijacking, and fraud attacks.
Ransomware attacks are continuously on the rise, and they’re targeting everything from big corporations to small businesses. This year, we dived into ransomware trends, the state of security teams’ defenses, and the tactics attackers are using to infiltrate networks. With evidence of infostealers as a precursor to a future ransomware event, our 2024 report emphasized the ongoing need for proactive defense.
Closing out the year – and what’s next – at SpyCloud
Helping businesses prevent cyberattacks – including ATO, ransomware, session hijacking, and online fraud – is always on our mind, holidays or not. And this year we’ve not only included new recaptured phished data to our repository, but expanded the amount of infostealer malware families we’re tracking to over 65, plus we’ve embedded advanced analytical capabilities throughout our products.
The future of threat protection with identity analytics
SpyCloud solutions have been enhanced with automated digital identity correlation capabilities. Basically, these advanced analytics allows security teams to quickly and accurately understand the full breadth of identity exposures across the enterprise, executive team, and supply chains, as well as support threat actor attribution, insider risk analysis, financial crimes research, and more. Keep an eye out for more updates!
2025 security predictions
Last but not least, it wouldn’t feel right to end the year without a little forward thinking. To that end, we asked a few of our in-house leaders what 2025 holds in store for security teams and the broader risk landscape. Here’s what they said:
Bad actors will increasingly rely on cybercrime enablement services:
With the rise of the Cybercrime-as-a-Service ecosystem, which includes things like malware, access brokers, and residential proxy providers, 2025 will continue to see more criminals turn to tooling they can buy instead of build. The availability and sophistication of these services lowers or removes many barriers to entry for those seeking to engage in cybercrime, and increases the risk to enterprises of all sizes. We will continue to see commodity malware – including Malware- and Ransomware-as-a-Service – become cheaper and more widely available, all the while increasing in functionality as new families and affiliates challenge the market to continually evolve.
– Trevor Hilligoss, Senior Vice President of SpyCloud Labs
Identity security will shift under the CISO:
With identity attacks set to exponentially grow from here on out, identity security will be a part of the CISO’s purview. Today, the identity team is often a completely separate organization, and the CISO doesn’t have the ability to make changes in that world. In 2025, we’ll see organizations make the necessary shift to put identity security under the CISO in their quest to truly get ahead of critical identity threats.
– Damon Fleury, Chief Product Officer
Organizations will focus on integrating identity-driven solutions into their security approach
Given how quickly criminals have adjusted to circumventing traditional cyber threat prevention solutions like MFA – combined with the fact that companies are attempting to consolidate solutions into a few platforms – in 2025 and beyond, security practitioners will be forced to integrate best-in-class security solutions within their platforms to prevent the known and soon-to-be compromised attack vectors, like in the case of stolen identity data that fuels attacks like session hijacking, ATO, and fraud. Checking a box as an exercise or merely aligning to a compliance framework will not help in the battle against advanced adversaries
– Ted Ross, CEO and Co-Founder
We’ll leave you with that. Let’s see what we can accomplish together in the new year!