From Clues to Clarity: How SpyCloud Investigations with AI Insights Saves Analysts Hours
SpyCloud Investigations customers now get access to AI Insights, rich source context & flexible graphing for a faster and more valuable analyst experience.

SpyCloud Investigations customers now get access to AI Insights, rich source context & flexible graphing for a faster and more valuable analyst experience.
IBM’s 2025 Cost of a Data Breach Report is here and identity threats take center stage. See what’s shaping breach costs, attack trends, and security priorities for the year ahead.

With over 4 billion records, it’s being dubbed the biggest leak of Chinese personal data ever. Here’s what to know.

From the LummaC2 takedown to the BreachForums void, our May cybercrime update breaks down the biggest cyber threats & news.

ULP combolists often contain fresh infostealer data. Here’s what to know about ULP combolists, including how to defend your organization from credential theft & attacks.

From the Twitter/X breach to Atomic macOS Stealer infection trends, our April cybercrime update breaks down the biggest cyber threats and news.

Learn about the latest NIST password best practices and SpyCloud solutions that prevent employees & consumers from using passwords exposed on the dark web.

We analyzed the nearly 200K leaked Black Basta chats and this is what we learned about their use of exposed credentials for ransomware operations.
Detect and remediate infostealer malware with SpyCloud’s EDR malware detection integrations, powering SOC teams with high-fidelity alerts for rapid response.

A deep dive into March’s cybercrime trends, including GhostSocks, North Korean IT workers, and pesky smishing campaigns.

LummaC2’s link to GhostSocks reveals stealthy proxy access, long-term persistence, and advanced evasion—posing a serious threat to enterprise defenses.

Uncover the latest identity security threats in the 2025 Identity Exposure Report. Learn how cybercriminals are exploiting stolen data and what you can do to stop them.

Discover the biggest wins from 2024 against cybercrime—from major infostealer takedowns to global ransomware crackdowns—and what they mean for the future of cybersecurity.

Headline-making breaches in 2024 exposed millions of records, compromising sensitive data. This blog explores what was stolen and the impact that has on security strategies to stay ahead.

A deep dive into February’s cybercrime trends, including Black Basta ransomware insights, stolen credit card databases, and the latest threat actor activities.

Bad actors use phishing gateway pages to screen and validate stolen data. Learn how they work and how to protect yourself from these attacks.

The end of 2024 and start to 2025 had no shortage of cyber security hot topics to cover. Dig into our latest findings and insights in this blog.

Phishing campaigns continue to rise in popularity and effectiveness for cybercriminals. Here’s a breakdown of how it works and what.

Discover how LummaC2 has evolved with new stealth tactics, enhanced theft capabilities & novel evasion techniques in our latest SpyCloud Labs analysis.

From big data leaks to cyber underground insights, SpyCloud tracked some of the top threats in 2024. Read our recap & 2025 predictions.

Cybercriminals are posting stolen credit card info & sensitive personal data on the Threads platform. Read the SpyCloud Labs analysis & get recommendations to prevent financial fraud.

This month, we’re breaking down the latest in cyber – from hot topics like Telegram, Operation Magnus, LockBit, and the arrest of USDoD to new research from SpyCloud Labs.

Legacy infostealer malware like Redline Stealer & Raccoon Stealer are still fueling cybercrime and threatening organizations. Here’s how to stay protected.

Learn about the TTPs China-based threat actors refer to as SDK & DPI, as well as SGKs, which house exfiltrated data about Chinese residents.

The impacts of account takeover can affect your customer base and business long into the future, which is why prevention is so key. Here’s how SpyCloud helps organizations reduce ATO fraud.

SpyCloud Investigations with IDLink analytics is the ultimate force multiplier for analysts. See what’s possible and get a demo today.

The MC2 data breach contains extensive PII on customers and individuals who had their backgrounds screened with the service. Here’s what to know about the leak.

SpyCloud integrates with popular SOAR platforms so you can better detect, respond to, and remediate compromised employee identities. See how.

See how cybercriminals are bypassing Google Chrome’s App-Bound Encryption feature with infostealer malware to steal session cookies that can be used in session hijacking attacks.

SpyCloud Labs dissects the capabilities of the open source Phemedrone Stealer, including log encryption, configuration & victim targeting.

The National Public Data (NPD) breach includes nearly 2.7 billion leaked records – and hundreds of millions of Americans’ social security numbers. Here’s what to know.

SpyCloud Labs digs into new infostealer malware variants like Kemicat and Mephedrone, as well as the resurgence of keyloggers like Snake.
Here we break down two phases of the MITRE ATT&CK Framework – Reconnaissance and Resource Development – and why it’s critical to account for stolen data in your detection and attack prevention strategies.

SpyCloud Labs reverse-engineered Atomic macOS Stealer to get a better understanding of its current capabilities and the threat it poses to the security community. Here’s our analysis.

Here’s what we found when we analyzed The Post Millennial data breach, including the types of exposed data assets contained in the 87 million leaked records.

Our 2024 Identity Exposure Report showcases just how big the stolen data problem is today. Here’s what we learned in our annual analysis of recaptured breach & malware data from the darknet.

SpyCloud’s integration with Cortex XSOAR bridges gaps between identity-related exposure incidents and corresponding incident response and remediation workflows.

Learn about the MOAB data leak and find out how much of the exposed data is already known, public, or outdated per SpyCloud Labs research.

SpyCloud Labs researchers uncovered details about a cybercrime traffer team that is responsible for distributing malware families to victims around the globe.

SpyCloud Compass now includes stolen cookie data for malware infections to help you remediate employee exposures.
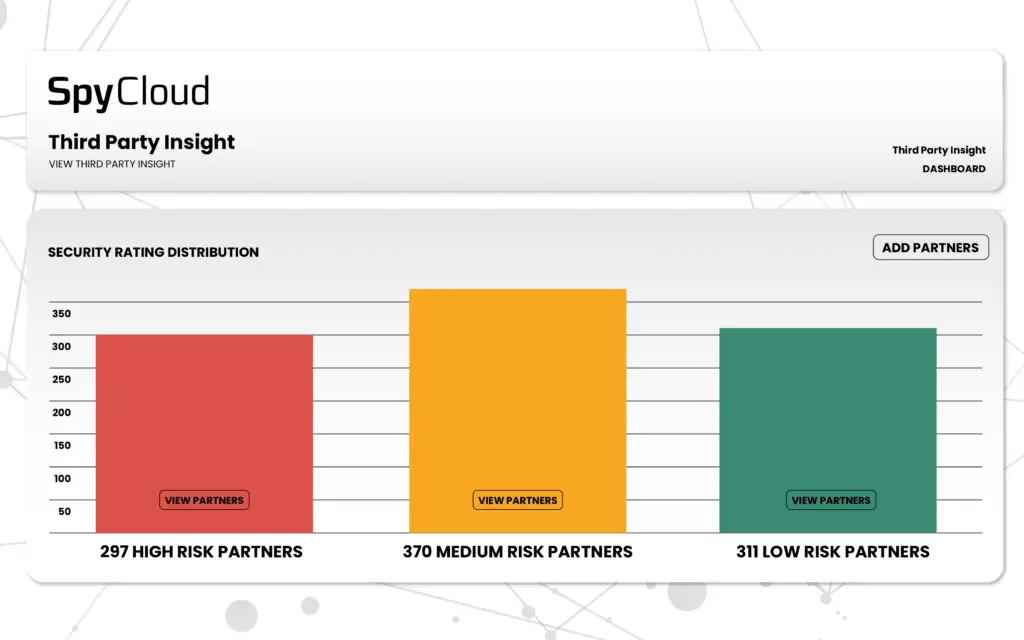
SpyCloud Third Party Insight helps you prevent account takeover by monitoring your supply chain for breach and malware exposures and sharing that data to aid remediation efforts.

As threats from malware infections slip through security defenses, a new approach to preventing ransomware is necessary. With SpyCloud Compass, security teams can now conduct complete Post-Infection Remediation.
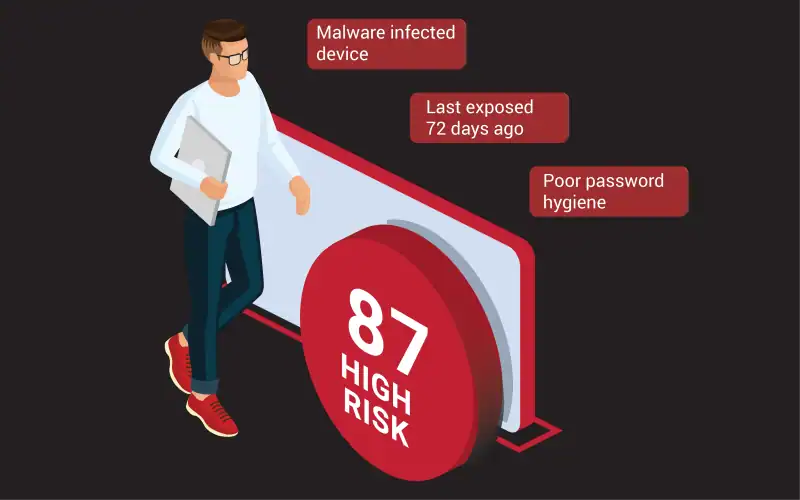
Stolen data helps criminals sidestep fraud prevention measures. Now, SpyCloud can help enterprises use that same data to stop hard-to-detect fraud.
Our development team is constantly pumping out new features, and we’re excited to highlight one that our customers have been asking for: Recent Records Alerts!