Account takeover attacks are on the rise, which creates plenty of headaches for businesses – like the nearly $13 billion in losses suffered each year. But did you know that four out of five consumers say they would completely stop shopping on a business’ website where they had been a victim of account takeover? So when it comes to consumer risk, we can’t just talk about short-term consequences. The impacts of ATO can affect your customer base and business long into the future, which is why prevention is so key.
This blog post explores the current state of consumer account risk as it relates to stolen identity data – particularly those risks associated with account takeover attacks – and how SpyCloud helps organizations reduce account takeover fraud while maintaining customer safety and loyalty.
Understanding the growing threat of account takeover
How criminals steal your customers' data
Security and fraud teams face the difficult and often time-sensitive task of determining if a user is a legitimate customer or a criminal using stolen data to masquerade as a user.
Understanding the root causes of the “customer or criminal?” dilemma is essential in building and maintaining a strong security framework and a seamless user experience. Here are some examples of how stolen data ends up in criminal hands, enabling regular customer activity to then be mimicked by criminals.
| Criminal steals data via: | How it happens: |
| Infostealer malware | Customer clicks a malicious link or downloads what looks like a real file and becomes infected with malware, allowing vast amounts of information to be exfiltrated from their device including credentials, valid session cookies, and PII. |
| A phishing campaign | Criminal tricks a customer into clicking on a malicious link (on a website, email, or text message) and providing things like PII or financial information that will enable the criminal or other bad actors to commit account takeover or fraud. |
| A data breach | Criminal gains unauthorized access to an organization’s accounts and/or systems and is able to steal customer information like credentials and PII. |
And with stolen data in hand, bad actors can capitalize on it by selling, trading or using the data themselves to commit costly cyberattacks like account takeover and fraud.
| Your business sees a customer: | With stolen data a criminal can: |
| Create a new account | Create a synthetic identity – pieces of legitimate identity data stitched together to perpetrate as a real user – or perform identity theft to set up an illegitimate account. |
| Log into an existing account | Login with compromised credentials or bypass login altogether, using other stolen data to authenticate. |
| Browse an authenticated session | Bypass login and directly access an already-authenticated session. |
| Complete a transaction | Use a compromised credit card, loyalty card, or gift card to make purchases. |
The numbers behind the rise of account takeover
According to a recent SpyCloud study, 33% of organizations reported an increase in ATO incidents over the past year, while another 22% saw consistent attack rates. This trend highlights the urgent need for businesses to implement robust security measures that go beyond traditional defenses.

How user behavior contributes to ATO risk
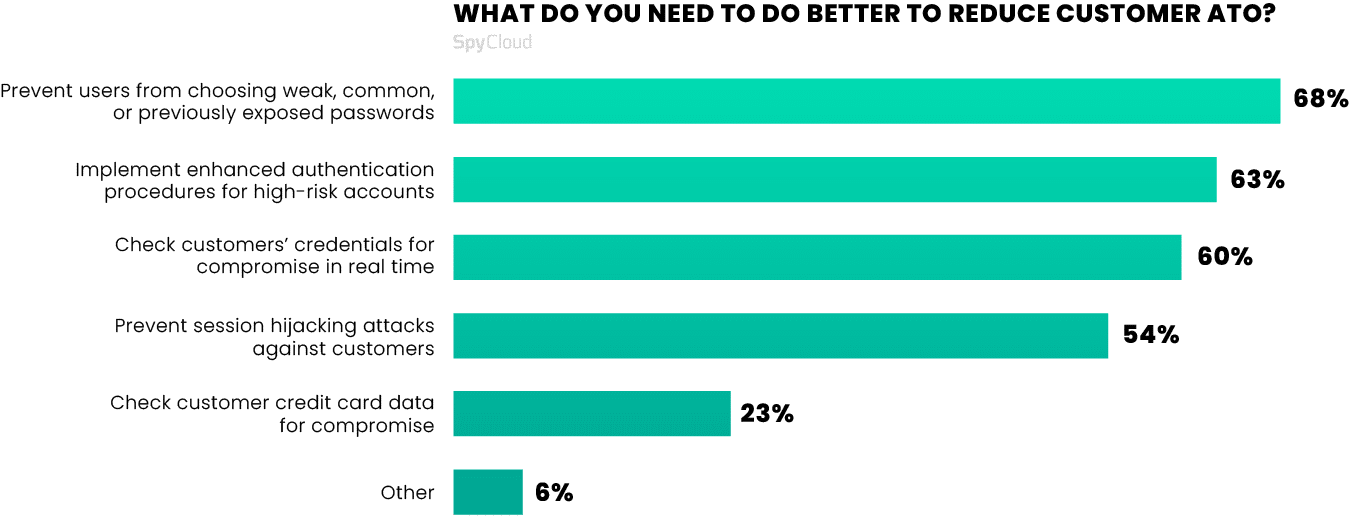
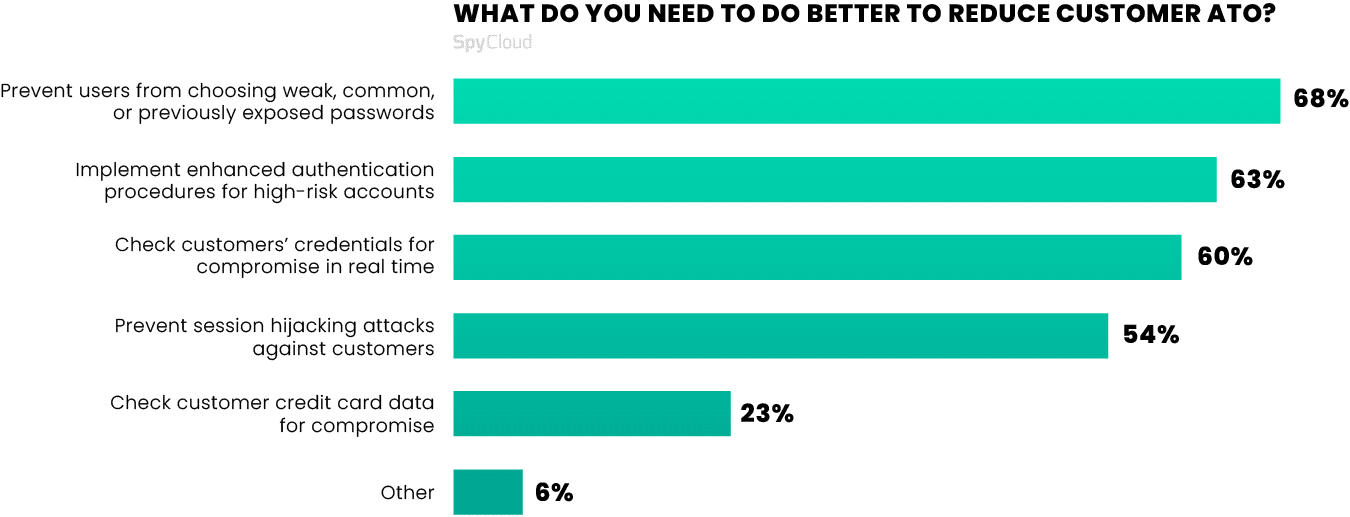
Effective tools and techniques for preventing ATO
SpyCloud research reveals the most commonly used tools teams report using to detect compromised credentials and prevent ATO today:
- Anomaly detection solutions (74%): These tools monitor for unusual activity patterns that may indicate an ATO attempt. By analyzing user behavior and network traffic, anomaly detection solutions can identify and respond to threats in real time.
- Customer reporting of unusual activity (61%): Encouraging customers to report suspicious activity on their accounts is a valuable component of ATO prevention. Organizations can use these reports to identify compromised accounts and take appropriate action.
- Fraud detection algorithms (60%): Machine learning algorithms analyze patterns in user behavior and transaction data to detect potential fraud. These algorithms can identify anomalies that may indicate an ATO attempt, enabling organizations to respond quickly.
Despite these efforts, many organizations struggle with the effectiveness of their ATO prevention measures. According to the survey, nearly 44% of respondents are very concerned about increasing ATO rates, while another 42% are somewhat concerned. This high level of concern reflects the growing threat posed by sophisticated cybercriminal tactics and the need for continuous improvement in risk protection strategies.
Survey participants agreed that more is needed – including the measures listed in the chart below:
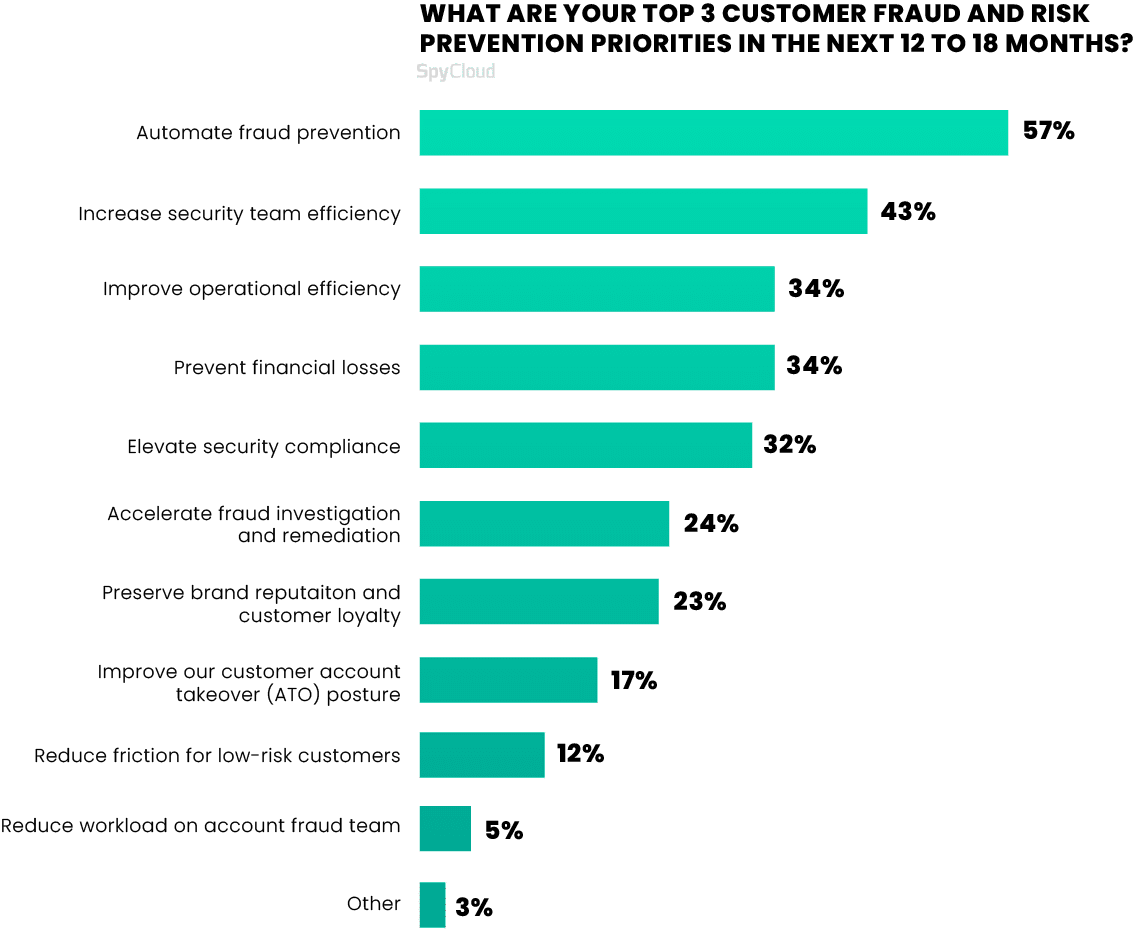
Looking ahead
In the year ahead, surveyed organizations are prioritizing automating fraud prevention (57%), increasing security team efficacy (43%), and improving operational efficiency and preventing financial losses, both cited by 34%.
It’s clear that organizations are lasering in on their strategies to combat rising account takeover and fraud risks, which is good news. For ATO and fraud prevention to be effective, organizations should consider using a solution like SpyCloud Consumer Risk Protection – it gives you the insights you need to shut criminals out before they have a chance to impact your customer accounts and your business.
How SpyCloud solutions can protect your business
By continuously recapturing exposed data from the darkest corners of the web, SpyCloud delivers fresh and actionable intelligence that enables businesses to identify and mitigate risks in real-time. This approach contrasts sharply with traditional solutions that often lag behind by several months, leaving organizations vulnerable to exploitation.
With over 25 billion assets ingested monthly, SpyCloud’s data is unmatched in its breadth and depth. This allows businesses to gain a complete view of their customers’ risk and take decisive action to protect sensitive information.
SpyCloud simplifies consumer risk protection and enhances your ATO and fraud prevention workflows with:
- Actionable intelligence: SpyCloud provides timely and relevant insights into consumer risk by analyzing data from the criminal underground. This allows you to respond quickly to potential threats and make informed decisions.
- Automated ATO prevention: By integrating SpyCloud's APIs into existing workflows, you can automate actions like enhanced authentication, password resets, and session logouts to prevent account takeovers and mitigate fraud.
- Real-time alerts: With real-time alerts on new exposures and breaches, your team can take proactive measures to protect customer accounts and reduce the risk of unauthorized access.
- Tailored customer journeys: A common challenge for security teams is balancing stringent security measures with a seamless user experience. Overly aggressive security protocols can lead to customer frustration and churn, while lax measures increase the risk of fraud and data breaches. SpyCloud's solutions help strike this balance by offering real-time decision-making tools that allow businesses to differentiate between high- and low-risk users. This means you can apply appropriate security measures without disrupting the user experience, ultimately fostering customer trust and loyalty.
See SpyCloud Consumer Risk Protection in action
For businesses committed to securing their customers’ data and safeguarding their brand reputation, SpyCloud’s solutions offer a proven path forward. By adopting a proactive and data-driven approach to consumer risk protection, organizations can effectively reduce the risk of account takeover and create a safer, more secure digital experience for customers.
Fill out the form below to generate a self-serve demo to see how it works.



