The 2025 Annual Identity Exposure Report is now available.
Get your copy here >
It’s the moment of truth we at SpyCloud anticipate every year: the release of our annual Identity Exposure Report. The report dives deep into the fight between organizations and cybercriminals over digital identities, with analysis based on the billions of data assets we recaptured from the criminal underground over the previous year.
Combing through the 2023 data, our researchers found a few familiar trends that feel a bit like déjà vu, including high password reuse rates and vast amounts of stolen personally identifiable information (PII).
There are also plenty of fresh themes, though, that point to new ways malicious actors are gaming the system to gain a leg up on organizations. Most notably, cybercriminals are relying on 1) more types of stolen data, like credit card information, crypto wallet addresses, and IP addresses, to impersonate victims, and 2) new types of stolen data, like master passwords to password vaults and 2FA secrets, stolen with malware that they can then use to compromise identities and carry out cyberattacks.
While the full report is packed with interesting finds (which we also summarize in this webinar), here are some of the main themes.
Digital identity weak spots, exploited
Cybercriminals aren’t just interested in stealing passwords anymore, although we still see plenty of email/username and password combos circulating the darknet to feed credential stuffing attacks. User identities have expanded to include hundreds of data types, like social security numbers and location information, and cybercriminals are leveraging the resulting expanded stolen datasets to dramatically increase the scope of their attack patterns.
They’re also taking shortcuts that negate the need for legitimate authentication. Bad actors are plain ignoring many layers of authentication organizations have put in place, using valid session cookies or API keys to impersonate users and sidestep authentication altogether.
Our recaptured data shows that bad actors have mountains of stolen identity data for the average person, sourced from breaches and malware infection logs that they can piece together to perpetrate cybercrimes like identity fraud and next-generation account takeover (i.e. session hijacking).
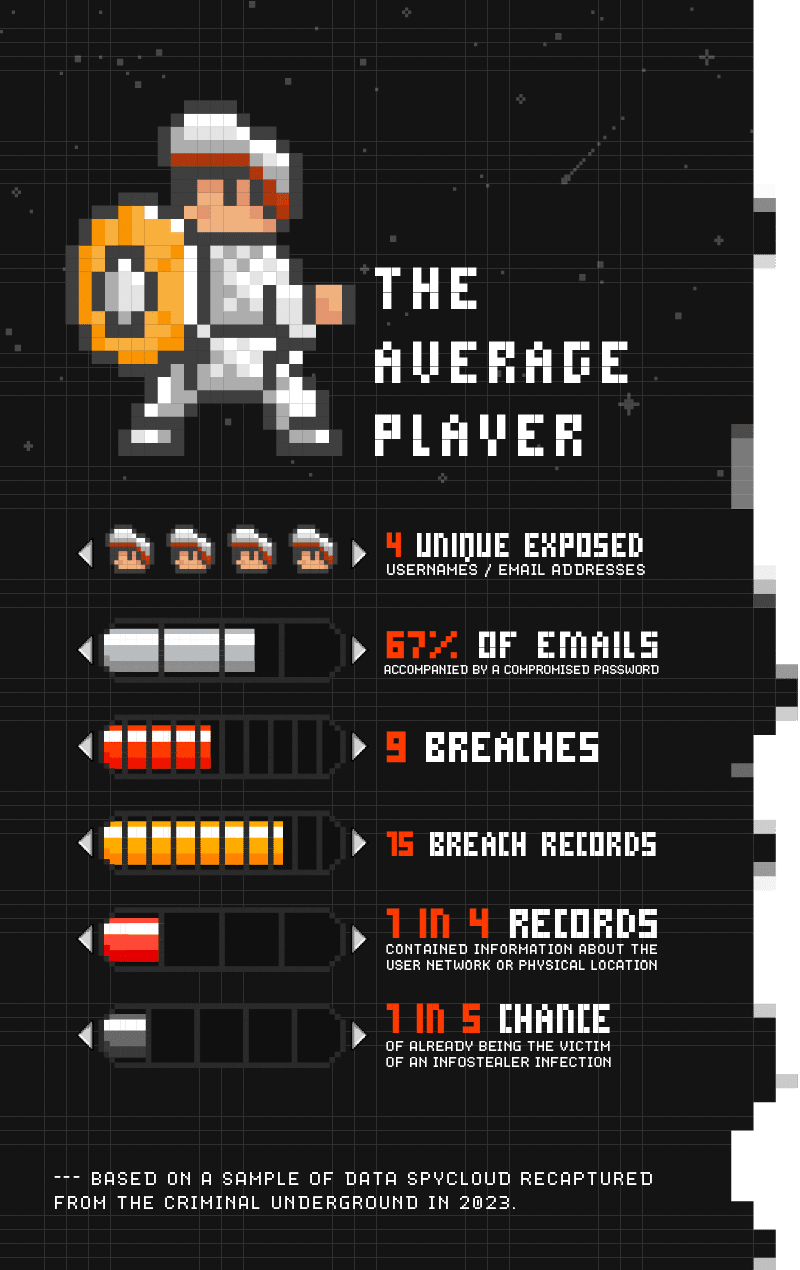
Our analysis of digital identity exposure demonstrates that cybercriminals have a range of opportunities for gaining access to accounts, applications, and organizations overall – and helps explain why the digital identity has become a top attack vector.
Malware is a formidable opponent for every security team
The biggest trend we continue to observe is the rapid rise of malware, particularly infostealers that exfiltrate valid, plaintext data straight from user devices. In the high-stakes game between cybercriminals and users, cybercriminals have an advantage when they’re using this freshly exfiltrated info, which is increasingly easy – and cheap – to get due to the proliferation of malware-as-a-service and infostealer logs on the darknet.
The use of infostealers tripled in 2023. Consequently, we weren’t too surprised to find that of the 3,478 breaches we analyzed, 61% were related to malware.

The data SpyCloud recaptured came from 52 infostealer families and contained:
- More than 343.78 billion malware-exfiltrated credentials
- More than 4.7 billion credentials for third-party applications, including popular business tools for communication and collaboration, human resources, software development, and IT/security
We also started tracking mobile malware, primarily from banking Trojans, recapturing more than 10.58 million mobile records between August and December of 2023 alone.
Stolen session cookies: Winner takes all
Another critical piece of the modern digital identity extends to session cookies. And session cookies are the ultimate trophy for cybercriminals because they can use them to sidestep authentication mechanisms and seamlessly hijack a session, impersonating a given user’s digital identity to execute account takeover attacks.
We are seeing criminals go all-in on stolen cookies. We recaptured more than 20 billion cookies last year – which speaks to their ubiquity in the criminal underground. This amounts to an average of more than 2,000 records per infected device. Our findings paint a pretty clear picture that malware-exfiltrated session cookies are high-value for criminals, and malicious actors will likely continue to pivot in that direction to sidestep MFA and passwordless authentication.
Following the breadcrumbs of expanded identities
We observed several other trends that show how cybercriminals are taking advantage of the expanding digital identity, too:
API keys & webhooks: Cybercriminals started stealing webhooks and API keys through malware infections, yet SOC teams don’t typically know when this data is stolen and consequently can’t fully undertake proper post-infection remediation.
Crypto addresses: New infostealer families, like LummaC2, now come ready with the ability to steal crypto wallet information, whereas in the past infostealers had to be modified to achieve this.
macOS malware: Infostealer concerns have gone beyond Windows. Our researchers noted an uptick in macOS infections, especially from Atomic macOS Stealer, which entered the scene in late 2022.
2FA tokens: We saw indications that new infostealers like LummaC2 are targeting browser-based 2FA tokens, and we expect these attempts to grow.
All these unfolding tactics further confirm infostealers’ rise to prominence and their impact on identity exposure. For SOC teams, these findings translate into urgency to implement complete post-infection remediation for malware-infected users, so that any identity data stolen with malware can’t be so easily pieced together and used in follow-on attacks
Returning themes that made us nostalgic
While we follow the road to where new developments take us, we continue to keep a close eye on password trends and the always-growing bounty of PII on the darknet. Even as cybercriminals are pivoting to session hijacking, other tried-and-true tactics and stolen data trends contribute to identity exposure and fuel cybercrime year after year.
In 2023, SpyCloud recaptured 32.22 billion PII assets, a nearly 4X jump from 8.6 billion in 2022. But, given our observations in identity exposure dating back to our inaugural 2017 report, we saw this coming.

Also in 2023, we recaptured a total of nearly 1.38 billion passwords, an 81.5% year-over-year increase from 2022. And when looking at password reuse rates within that pool, rates remain incredibly high among users exposed in two or more breaches at 74%, despite organizations pushing user awareness and training in recent years.
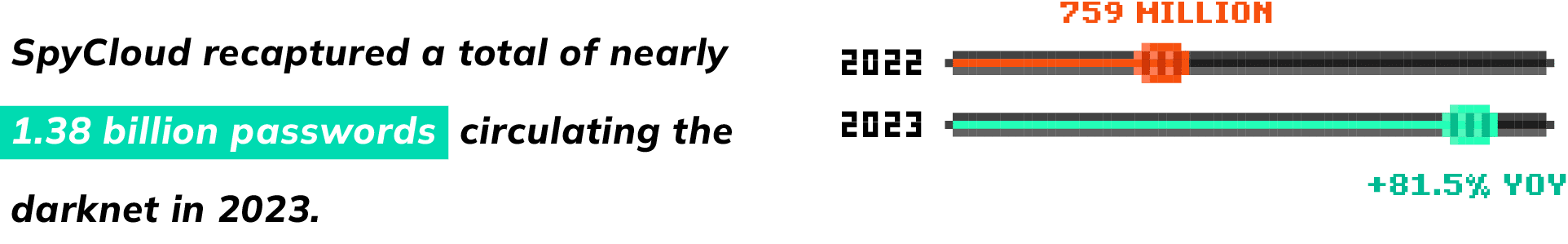
For more proof that no amount of education or training can fully change user behaviors, the most exposed password in 2016 was 123456, and it has remained at the top for another five out of six years that we’ve tracked it, including 2023. Users also continue to lean into pop culture trends for password inspiration, using easy-to-guess base words like football, XBOX, and Hollywood.
Looking to the future: Turn the odds in your favor
This year’s findings, along with our retrospective review, make one thing clear: cybercriminals are pivoting and poking holes to exploit any piece of a person’s digital identity they can get their hands on. In response to this shift to next-generation identity attacks, we at SpyCloud continue to evolve our datasets, analyses, and solutions.
The good news is that there are things you can do to strengthen your defensive toolkit – and outpace bad actors at their game. A big part of a modern approach means remediating exposures from malware-exfiltrated data that’s been made available on the darknet. Arming your team with insights that quickly identify compromised and risky users today is table stakes for turning the odds in your favor.



