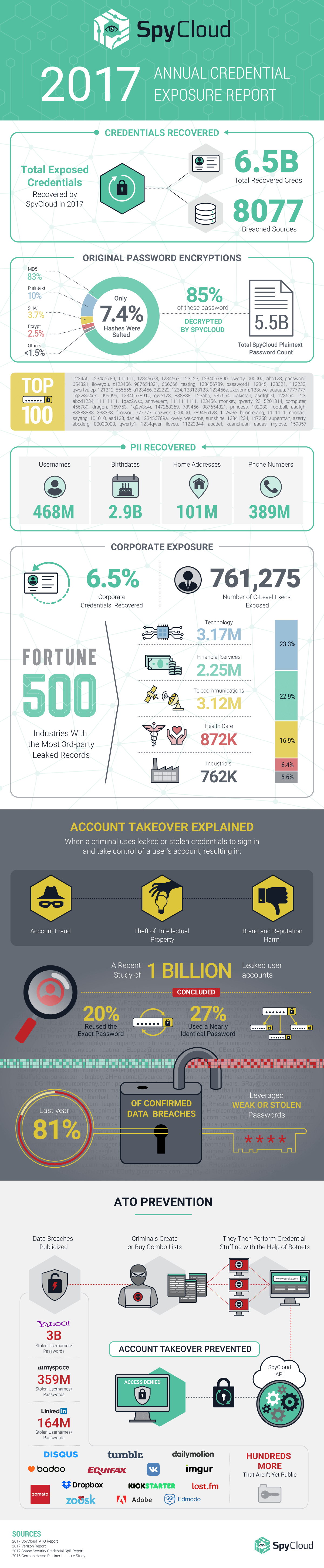
Account Takeover (ATO) by the Numbers
Account takeover is exactly as it sounds: when a user’s account is taken over by someone other than the original user. In a study of one billion leaked user accounts, 20 percent were due to password reuse and 27 percent were attributed to using nearly identical passwords on multiple accounts.
Cyber-criminals steal passwords and usernames by exploiting vulnerabilities to dump databases of online sites, and then sell the credentials to teams of hackers and underground thieves. These bad actors multiply quickly, exploiting their stolen assets using botnets to perform credential stuffing to find as many related accounts as possible. Their actions, which can last for years, result in account fraud, theft of intellectual property, and brand and reputational damage.
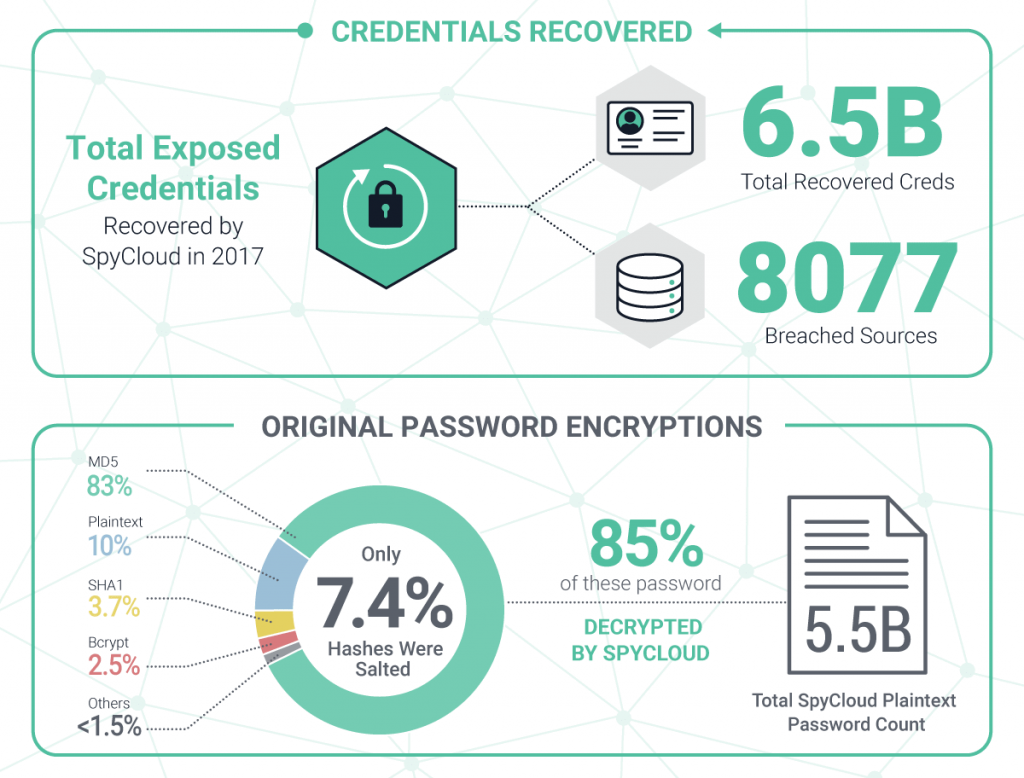
What SpyCloud Has Recovered in 2017

Our team of experts recovered data from a number of breaches that have not yet been made public. Our proprietary method of gathering breached records to prevent ATO uses automated technologies, such as scanners, but relies heavily on human intelligence to find what less comprehensive solutions fail to discover. Our process gives us more data than anyone in the industry.
Password Encryption
Most modern web applications that you log into don’t store your account password, but rather a hash of your password. There are a variety of different hashing techniques, all basically yielding some random text that is supposed to be hard for hackers to crack. Sadly, all hashing algorithms are not created equal and many weaker algorithms (like unsalted md5 and sha1) are being used en masse on numerous sites today. The resulting database leaks from these sites are easily deciphered and immediately converted back into the readable passwords that can be used to fuel ATO attacks.
Password encryption types
(discounting combo lists)
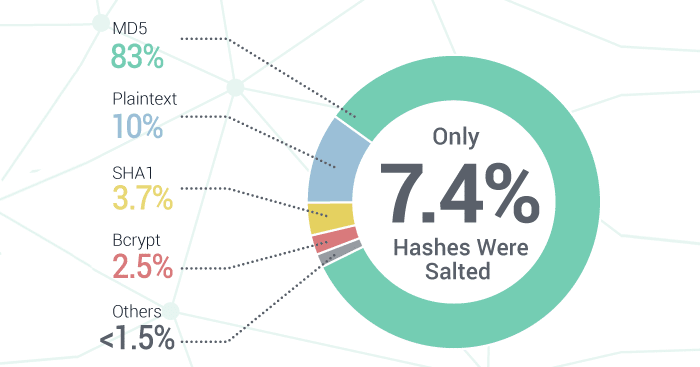
What is “salting?” It’s adding random data to a password before it’s hashed and preserving the ‘salt’ value with the hash. The problem, however, is that it’s not easy to identify how well the stolen credentials were hashed once a password breach occurs. Most companies keep their hashing functions secret.
The dubious website, Ashley Madison, suffered a catastrophic breach in 2015 that involved 36 million leaked passwords. While these passwords were hashed with the bcrypt encryption type, 15 million passwords were less fortunate. Hackers were able to decrypt 11 million of those passwords in only days, thanks to the fact that the hashing wasn’t nearly as strong.
PII Recovered by SpyCloud in 2017:
- Usernames: 468M
- DOBs: 2.9B
- Addresses: 101M
- Phone Numbers: 389M
We Recovered More Than Just Passwords:
- Corporate Credentials: 416M (6.5%)
- Password Reuse Amongst Corporate Users: 10.7%
- C-Level Execs Exposed: 761,275
Global Fortune 500 Exposure:
- TOTAL GLOBAL 500: 8.5M
- Technology: 3.17M (23.3%)
- Telecommunications: 3.12M (22.9%)
- Financial Services: 2.25M (16.58%)
- Health Care: 872K (6.40%)
No company is safe from breaches and the problem is becoming more widespread, affecting organizations in all sectors and industries.
Companies are struggling to keep up with the sophisticated tactics hackers are using to gain access to seemingly secure accounts – and causing significant damage to brand reputations, customer share and revenue.
There are, however, several industries that stand out as having the most third-party record leaks. We took the Global Fortune 500 companies, including all of their subsidiaries, and matched them against their corporate domains. Interestingly enough, the Global 500 industry with the highest overall leaks, technology, was the one industry many would assume would be the most proactive about security.
Leaked Global 500 Credentials by the Numbers:
| Sector | Leaked Credentials in 2017 | Percent in 2017 | Average Leaked Credentials per Company per Month |
| Technology | 3,172,468 | 23.27% | 96,135 |
| Telecommunications | 3,121,715 | 22.90% | 183,630 |
| Financial Services | 2,259,962 | 16.58% | 19,824 |
| Industrials | 762,303 | 5.59% | 36,300 |
| Health Care | 872,352 | 6.40% | 36,348 |
Hover over the map to see the most leaked from your country.
Every country seems to have its own unique set of top passwords that gives a small glimpse into the zeitgeist of the region. In order to find the top passwords from each country, SpyCloud first filtered out the top 100 passwords globally.
Clearly, some countries love their sports more than others. The United Kingdom and Ireland share “liverpool”, “arsenal” and “chelsea” as their top passwords, while the U.S. and Canada have “baseball”, “basketball” and “soccer” within its top list. Many South American countries also included names of their favorite football clubs in the top (“flemengo” for Brazil, “nacional” for Columbia, “riverplate” for Argentina, “alianza” for Peru, etc.).
In many countries, the name of the country itself appears in the most popular choices (e.g. australia, venezuela, bolivia, norway, etc.) and also the most populous cities in each country show up pretty often (e.g. “barcelona” in Spain, “toronto” in Canada, “napoli” for Italy, “kinchasa” for Congo, etc.)
Infographic
We know this is a lot of information, so in addition to this post we put together an infographic that beautifully summarizes all this data and more. We truly believe this is important stuff and unfortunately we can’t predict for certain what 2018 will bring, but we can assume these cracks and hacks will become more brazen, more systematic and more challenging to prevent. Fortunately, companies like SpyCloud are staying a step ahead of the bad actors with methodologies and technologies that help users control their data before the criminals gain access.
Feel Free to Share our Infographic on your Site