When 2020 came to a close, it’s safe to say most of us said, “Good riddance!” For the majority of last year, while the rest of the world was busy trying to wrap its head around this strange pandemic reality and new ways of doing business, criminals were having a field day finding countless ways to exploit our collective vulnerability. And they were highly successful.
Each year, Verizon releases a much-anticipated deep dive into the overwhelming data breach problem. For the Verizon 2021 Data Breach Investigations Report (DBIR), the group examined “79,635 incidents, of which 29,207 met our quality standards and 5,258 were confirmed data breaches, sampled from 88 countries around the world.” That’s a third more breaches than the previous year. The analysis shows alarming trends in cybersecurity and proves that humans are still the weakest link. As long as we fail to protect ourselves from ourselves, criminals will prevail.
Criminals Want Credentials
For four consecutive years, Verizon’s report spotlighted stolen or compromised credentials as the top cause of all data breaches. While the 2021 DBIR marks a shift in how it classifies breaches (now categorizing them by ‘action varieties’) and citing “the human element” as the top cause – the use of stolen credentials obtained from other breaches and/or credential reuse was a consistent thread throughout most criminal activity.
We’ve said it before, and we’ll say it again—everyone loves credentials. Credentials are the glazed donut of data types.
- Verizon 2021 DBIR
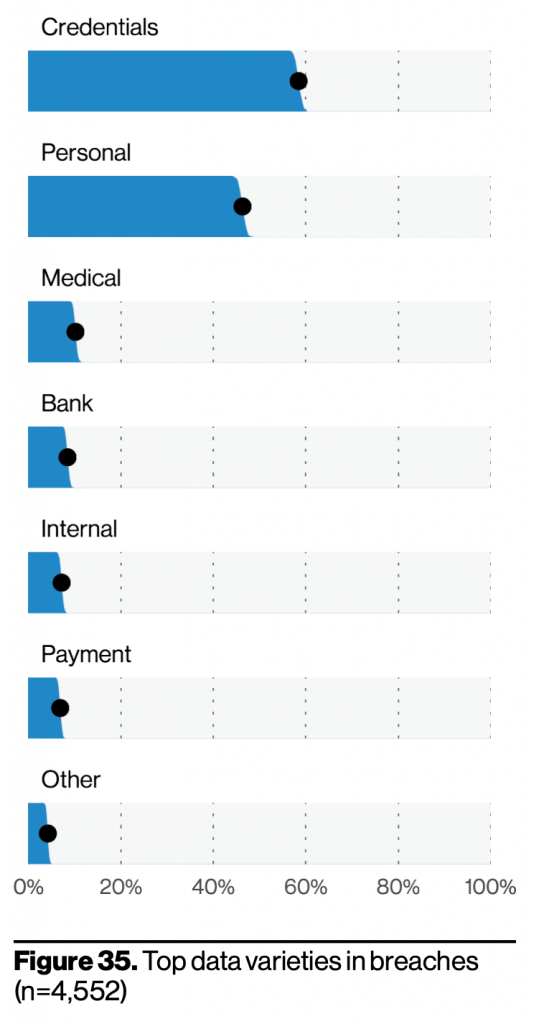
According to Verizon, 61% of breaches involved credentials, and the use of stolen credentials was present in 25% of breaches last year. This doesn’t mean they didn’t factor into the other 75% of breaches in some capacity.
Credentials also remained the most highly sought-after data type. Whether driving the surge in phishing and business email compromise (BEC) attempts, inspiring criminal innovation through credential stuffing, or playing a role in MFA bypass, having our credentials makes life easier for criminals.
Stolen Credentials Fuel Rise In Ransomware
Ransomware has been growing steadily since 2016 – and 2020 was no different. More than doubling its frequency from 2019, ransomware as an action was present in 10% of breaches last year. Again, bad actors seem to prefer the use of stolen credentials or brute force as a tactic; 60% of the ransomware cases Verizon observed involved direct install or installation through desktop sharing apps.
Merging Tactics
Just as there is no one-size-fits-all solution for cybersecurity, there is no one-size-fits-all approach for perpetrating attacks.
Many tactics may be chained during a breach; for example, “a threat actor might perform a use of stolen credentials or phishing action to Infiltrate a victim organization, but then deploy malware in order to exfiltrate the data they had their sights on.”
In other words, successful attacks are usually a packaging of various attack types, which on a large scale was demonstrated by the SolarWinds supply chain attack last year. That was perpetrated with a combination of password spraying, malware deployment, and MFA bypass, to name a few techniques.
One attack type examined in the Verizon report is BEC, which in itself is a combination of tactics: A bad actor can impersonate an executive by using compromised credentials (account takeover to dupe an employee (social engineer) via email (phishing) into opening a malicious link (keylogger malware), allowing them to collect funds and exfiltrate data.
"When examining breaches that included a reported loss, 95% of BECs fell between $250 and $985,000 with $30,000 being the median."
System Intrusion
Speaking of merging tactics, Verizon’s analysis spotlighted system intrusion incidents, a new pattern of “more elaborate, ‘human-operated’ attacks,” that leverage malware and hacking (i.e. the use of stolen credentials and brute force attacks), and often result in ransomware deployment. 966 breaches fall into this category, with over 70% involving malware. 30% of the malware was directly installed by the actor, reflecting a similar pattern to ransomware deployments, requiring the use of stolen credentials or brute force.
Curious about credential-stealing malware? Check out our webinar, I Put a Keylogger on You & Now You’re Mine
Social Engineering
The arrival of the global pandemic and subsequent stay-at-home orders were ripe for social engineering tactics. As early as March, there was an onslaught of activity that leveraged COVID-19 to manipulate users through various threat types, such as phishing campaigns in which bad actors impersonated public health officials, or BEC attacks in which criminals posed as trusted vendors seeking information related to an organization’s COVID protocol.
Phishing has long been a persistent threat, but Verizon observed its presence in 36% of breaches in 2020 (an 11% bump from the previous year). In addition, BEC was the second most common social engineering tactic. All told, 85% of social engineering attempts resulted in credential loss.
Brute Force/Credential Stuffing Attacks
This year’s DBIR spotlights the attacks being made as more and more businesses move critical functions to the cloud: 39% of all breaches were attacks on web applications. In the early days of cloud migration, criminals exploited security gaps in the application. These days, passwords open most doors, and credential stuffing helps fuel criminal success rates.
“We found that 23% of the organizations monitored had security events related to [brute force and credential stuffing attacks], with 95% of them getting between 637 and 3.3 billion(!) attempts against them.”
As SpyCloud has observed, criminals have access to gigantic troves of stolen credentials – and chances are, you use the same or similar passwords across multiple accounts. When your stolen credentials are fed into credential stuffing tools, criminals can easily test which usernames/passwords unlock doors.
As always, the Verizon 2021 Data Breach Investigations Report is positively stuffed with statistics to prove that, once again, criminals are not slowing down and their behaviors are only getting more complex. Sure, their methods and tools are very creative and sophisticated, but their success is the result of our failure to protect ourselves – aka the “human element.” We reuse passwords, we access corporate applications on unprotected personal devices, and we refuse to adopt multi-factor authentication. All of these actions have consequences, yet reversing them is painless compared to the damages we leave ourselves and our organizations open to.
We’re in the business of preventing data breaches that result from weak & stolen credentials and password reuse. Check out our workforce account takeover solutions & get a demo to see how SpyCloud can reduce your risk.