Zero Trust & Account Takeover Prevention
With account takeover and Business Email Compromise (BEC) attacks on the rise, enterprises looking to more tightly control data access and prevent breaches have found a principle to get behind: Zero Trust. In practice, the Zero Trust security model means never trusting, always verifying users’ identities in an effort to combat fraud, and only granting access once proof has been established that users are who they say they are.
While motive is noble, in reality, the required authentication measures can mean your employees, consumers, and partners end up feeling like criminals. But it doesn’t have to be this way.
SpyCloud has become an essential component of Zero Trust, giving you confidence in your users’ identities and protecting their accounts (and your enterprise’s sensitive corporate systems and data) without creating unnecessary friction for your users or extra work for your security team.
Credential Monitoring for More Secure Identity and Access Management
SpyCloud performs automated login checks against the world’s largest repository of recovered, previously stolen credentials and PII to assess whether or not the username, password or other personal information has been exposed to threat actors. This continuous verification provides extra certainty that users’ account credentials are secure and uncompromised.
If login credentials are determined to be exposed in a breach — even a very recent breach, since SpyCloud gains access to stolen data within days of a breach occurring — users are sent through a stronger, secondary authentication process to log in, thwarting criminal attempts at account takeover. Without forcing a password reset, your enterprise is able to verify that users are who they purport to be (for example, by asking additional “secret answer” questions), without introducing more friction into the login process.
Should you choose to force a password reset, you can feel confident that you have remediated compromised user credentials before or very soon after account takeover attack cycles begin, preventing the fraud, business email compromise attacks and illegitimate network access that cybercriminals perform with hijacked accounts.

If you're an organization that's not running on a Zero Trust model, then you have no idea what threats you're allowing into your environment.
FINANCIAL SERVICES
Learn How a Fortune 100 Financial Services Company Supports Their Zero Trust Policy with SpyCloud
Ensure Employee Logins Aren’t Compromised
We all know that hackers don’t break in anymore; now they just log in. A criminal who gets ahold of an employee’s password can do serious damage to your bottom line. How can you distinguish between a criminal logging in with a stolen password and your employee logging in legitimately? The best method of defense goes well beyond MFA — it’s proactive ATO prevention. Match employee logins against the world’s largest repository of compromised credentials and when a login is flagged as part of a breach, automatically force a reset of the users’ password.
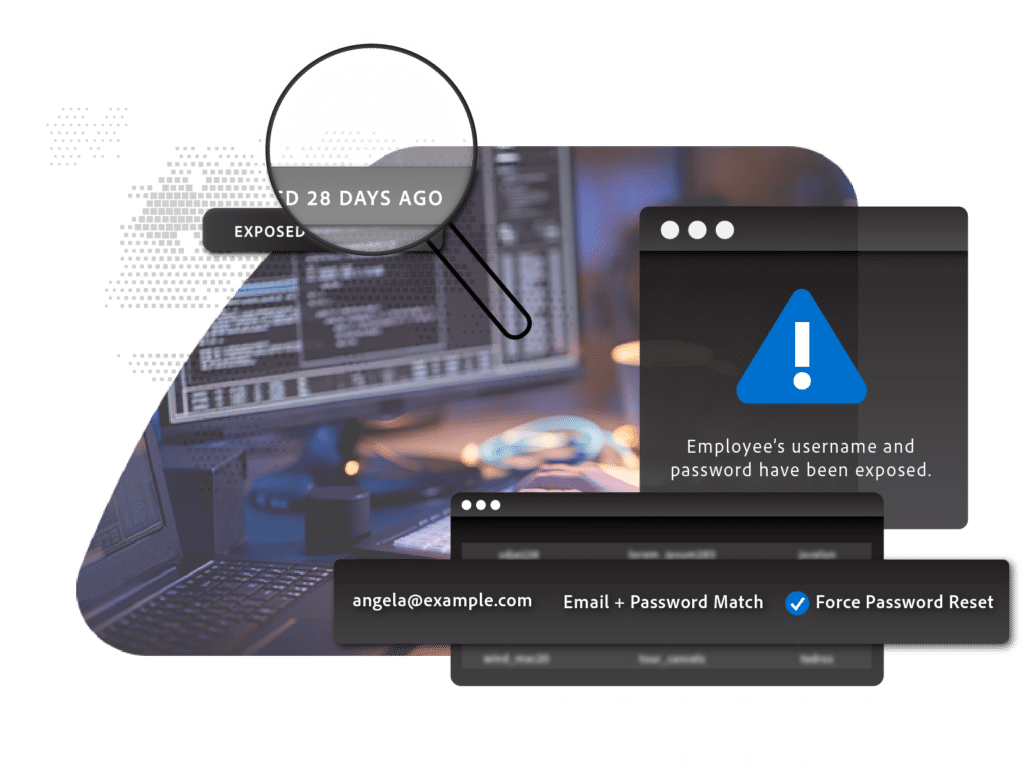
Protect Your Executives & Board Members, Too
SpyCloud can also detect when your board members’ and high profile executives’ personal passwords are compromised online, and help you prevent these passwords from being reused to gain sensitive entry to your company — reinforcing your Zero Trust policies.
Have Confidence in Your Consumer Logins
Criminals who have gained access to your consumers’ accounts perpetrate fraud that costs your business — and your consumers themselves — time, effort and money. Prevent illegitimate purchases, unauthorized funds withdraws, and users’ PII. Protecting their accounts is your priority, but you don’t have to interrogate them at every login in order to do so. Zero Trust and a great customer experience aren’t mutually exclusive concepts with SpyCloud.
To protect consumer accounts and personal data, login attempts from users whose information SpyCloud determines to be at risk are automatically prompted to complete an additional authentication measure. Financial institutions, for example, using SpyCloud can also proactively monitor for account compromises and notify customers of the risk or exposure, helping secure accounts, prevent fraud and create trust between you and your customers.
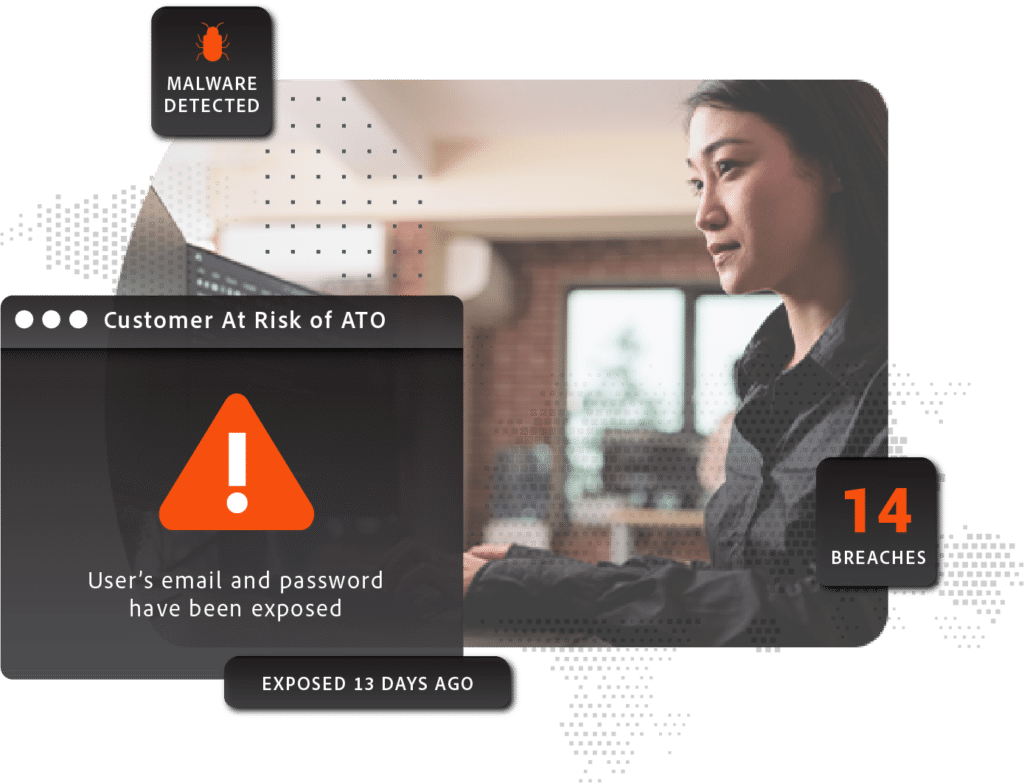
Prevent Your Partners from Compromising Your Enterprise
Your partners, vendors and suppliers introduce risk to your business. Think about the number of third parties who have access to your HR, finance, and marketing systems via logins that are as susceptible to breaches and malware infections as any other employee or consumer account under your purview. With SpyCloud, you can pass your Zero Trust enforcement onto them and share their exact exposure details with them so they can shore up security measures for those accounts. SpyCloud enables you to know which partners pose the highest risk to your business and which vendors are most susceptible to BEC fraud.

Zero Trust & SpyCloud
Introducing ATO and BEC prevention to your Zero Trust framework seems daunting, but with SpyCloud, it doesn’t have to be. It’s all about:
- Having access to the right data — the most current, relevant, and truly actionable breach data, which only SpyCloud offers
- The ability to detect exposed credentials before criminals have a chance to use them, which only SpyCloud’s early warning breach detection platform offers
- Being able to remediate account exposures automatically, which is effortless with SpyCloud’s Active Directory integration
Featured Products
Our award-winning products enable you to proactively protect your users’ accounts and thwart online fraud.
Employee ATO Prevention
Protect your organization from breaches and BEC due to password reuse.
Third Party Insight
Secure your supply chain by monitoring your vendors and partners for compromise.
Consumer ATO Prevention
Protect your users from account takeover fraud and unauthorized purchases.
Featured Resources
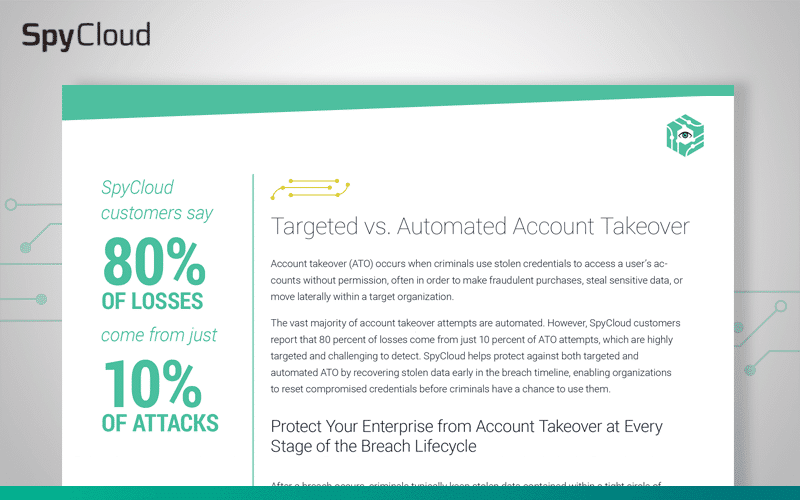
Targeted vs. Automated Account Takeover Attacks
Account takeover can be highly-targeted, sophisticated, and manual, or it can be high-volume and automated. Learn how to protect your enterprise from both types of ATO.

2022 Annual Identity Exposure Report
Our annual reports analyzes the 15.5 billion assets we recaptured from the criminal underground last year, and how enterprises can use this information to protect themselves from ATO, malware, and ransomware, and protect their consumers from online fraud.
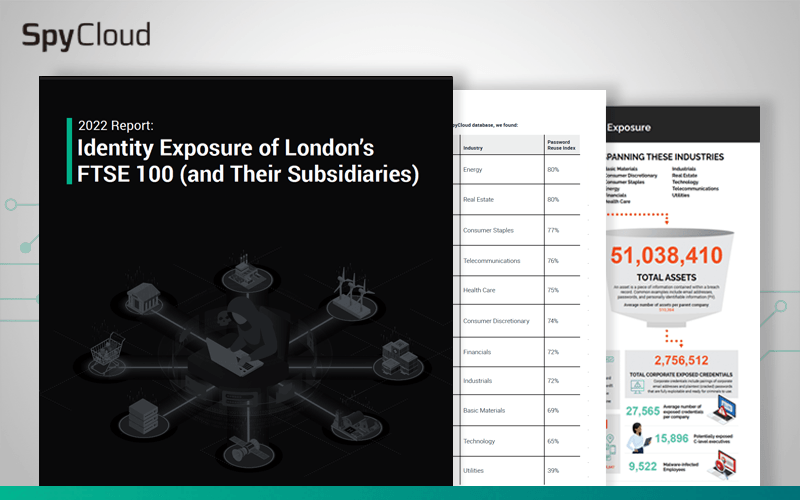
2022 Report: Identity Exposure of London’s FTSE 100
Our annual analysis of exposed credentials and PII tied to London’s FTSE 100 employees uncovered insights about password reuse and malware-infected devices that put these organisations and the companies that rely on them at risk.
