Executive Cyber Protection
Corporate account takeover is a type of fraud where thieves gain access to the inner workings of a business to make unauthorized transactions, including transferring funds from the company, adding fake employees to payroll, and stealing sensitive customer information that may not be recoverable. Cybercriminals may launch highly targeted account takeover attacks against senior employees, executives, developers, and system administrators with privileged access to sensitive data and funds.
In order to fight against this brand of cybercrime, it’s critical for organizations to implement a strong executive cyber protection program. SpyCloud helps you protect executives from account takeover by monitoring the criminal underground for their credentials and PII, quickly alerting you when their passwords become available to attackers via a third-party breach or malware infection.
How Executives Are at Risk for Cybercrime
While all employees are targets and bring risk to the organization, executives attract the most attention from savvy cybercriminals. They are well aware that executives and others with high levels of access hold the keys to potentially lucrative data and IP. Once they break into the system through these VIP accounts, they can steal and sell corporate data as well as extort money, drain accounts, and fraudulently represent corporate executives.
Even with common security methods and tools, many organizations are still at high risk for a breach. Executive cyber protection requires more than multi-factor authentication, password rotation, behavior and heuristic-based solutions, and dark web scanners, crawlers, and scrapers. While all of these methods can be effective at some level, they fail to actually prevent corporate account takeover, even when used in combination. The proof is in the fact that while all of these solutions have been in use for many years, the rate of corporate account takeover is only increasing. To protect your executives effectively, you need a more proactive defense.
Executive Cyber Protection for Both Work and Home
Executives’ corporate passwords fall within your security team’s purview, meaning you can monitor them for exposures and force employees to reset weak or compromised passwords. Personal accounts are a whole separate ballgame, and security teams typically don’t have visibility or control over executives’ personal breach exposures. For cybercriminals, a vulnerable personal account can provide a useful starting point for an attack on your enterprise.
In addition to monitoring corporate credentials, SpyCloud helps security teams secure accounts outside of corporate control. Empower your board members, investors, and high-risk executives to protect their personal accounts from cyberattacks with SpyCloud VIP Guardian.
Identify Stolen VIP Credentials & Data Early
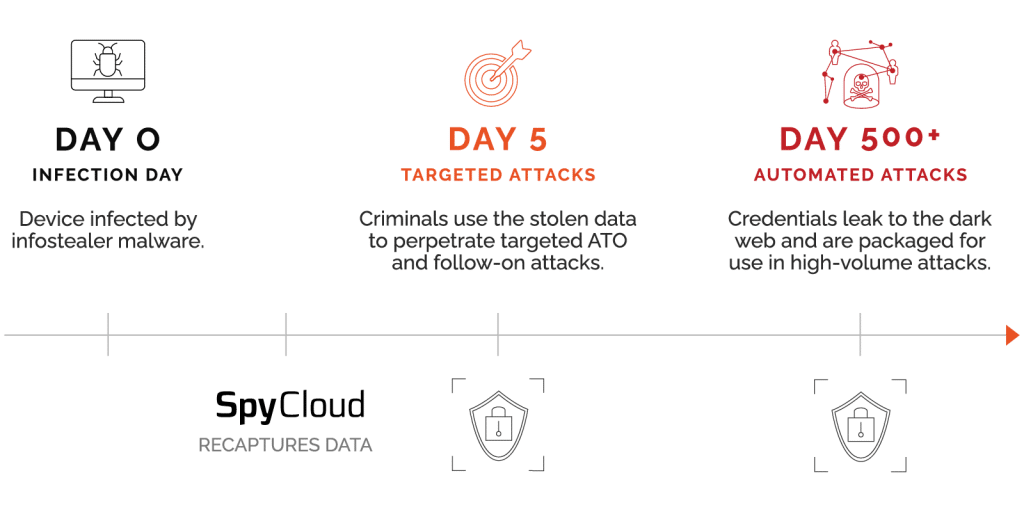
The key to preventing corporate account takeover is to identify stolen credentials as quickly as possible after a data breach, before criminals have time to use them. The only way to do that is to have access to a comprehensive, constantly updated, real-time breach database that security leaders can compare with their directory of employee accounts per domain. The sooner the breach data is discovered, the faster any compromised accounts can be protected.
SpyCloud maintains the largest database of recaptured data in the industry, with over 600 billion recovered assets from breaches, malware-infected devices, and other underground sources. SpyCloud researchers gain access to data early in the attack timeline through a combination of human intelligence and applied research.
Protect VIPs from Targeted Cyberattacks
Because of the valuable assets VIP employees often have access to, cybercriminals may exert substantial effort to infiltrate their accounts. Tactics can include manually testing variations of stolen passwords to avoid raising alarms, bypassing MFA via SIM-swapping or phone porting, and using one compromised account to gain access to others with tighter protections.
SpyCloud gives security teams an advantage by gaining access to breach data as soon as possible after a breach, often before criminals have cracked passwords within the data. SpyCloud also enables security teams to monitor VIPs’ corporate and personal credentials for breach exposures, protecting both personal and professional accounts that may put them at risk.
Protect Your Enterprise from Business Email Compromise
Business email compromise (BEC) defrauds businesses of billions of dollars every year, typically through seemingly-legitimate emails that are anything but innocent. Highly-skilled cybercriminals armed with just enough employee personal data to be convincing can use compromised accounts to trick colleagues and customers into taking risky actions that lead to fraud and data loss.
SpyCloud discovers credential compromises that are a pre-cursor to BEC, alerting security and fraud teams so they can take swift action and reinforce executive cyber protection.
Featured Products
Our award-winning products enable you to proactively protect your users’ accounts and thwart online fraud.
Employee ATO Prevention
Protect your organization from breaches and BEC due to password reuse.
Featured Resources

2024 SpyCloud Malware and Ransomware Defense Report
The 2024 SpyCloud report uncovers today’s malware and ransomware resurgence. See top threats and what security teams are prioritizing to prevent attacks.

SpyCloud Annual Identity Exposure Report 2024
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.
2023 Ransomware Defense Report
As cybercriminals continue to reap rewards from ransomware attacks, how are security teams keeping pace? Download this year’s report for insights on new trends, attack precursors, and critical defense gaps.
