OUR DATA
Illuminating Dark Web Data to Disrupt Cybercrime
The largest, most valuable dataset of identity data, recaptured from breaches, malware, and phishes
Every threat SpyCloud helps you stop begins with what criminals know – and we know it first. SpyCloud maintains the world’s largest and most actionable repository of recaptured dark web data, giving your organization unmatched visibility into exposed identities and a proactive approach to identity threat protection.
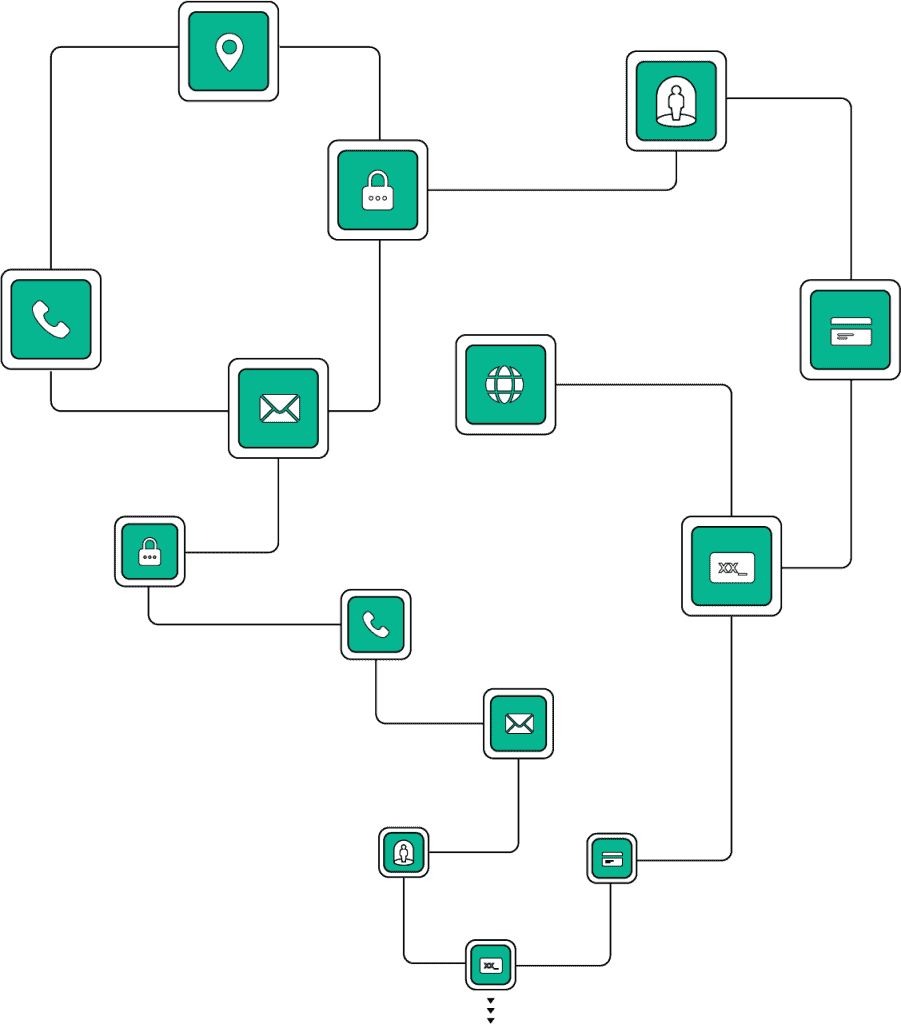
Dark web data, reclaimed from every corner of the criminal underground
What sets us apart isn’t just how much data we have – it’s where it comes from and what we do with it. SpyCloud’s massive darknet data lake grows daily, with identity data sourced directly from criminal communities. We continuously collect and analyze the data, cracking passwords to reduce false positives and applying rigorous data science to correlate exposures across identities.
Unlike stale, breach-only threat intel feeds or services that scrape public forums, SpyCloud illuminates live and latent identity risk.
If the data is interesting to criminals, we recapture and remediate it.
Holistic identity data for
14x
threat protection
coverage
We know two things to be true. The first is that there is way more hidden risk lying in wait in the criminal underground than most organizations realize. The second is that there are also better ways for teams to address these risks.
SpyCloud is built from the ground up to correlate exposed data from an individual’s entire digital footprint – past and present, across managed and unmanaged devices.
The result? Visibility into the entire identity behind an exposure. Better identity matching paired with proactive solutions mean you can close the door on an average of 14x more potential entry points.
24% increase YoY
70% of users still reusing previously exposed passwords
correlating 25B+ darknet assets per month
recapturing millions of infected devices’ data per month

Prevent spending on average $4.81M breach costs per credential-based attack

Reduce detection-remediation cycles from days to minutes


Reclaim hours of analyst time with enriched, pre-correlated alerts

Safeguard your most critical identities and action on exposures across entire digital personas
Intelligence from the inside
SpyCloud Labs, our in-house research team, infiltrates active criminal ecosystems to harvest massive datasets from breaches, infostealers, and phish kits before they’re widely circulated. This broad darknet data set enables:
SpyCloud solutions empower your team to detect earlier and remediate faster – driving proactive protection for security teams of any size.
What makes SpyCloud’s darknet data critical
SpyCloud is the trusted partner for security and identity teams who must protect employee identities to secure corporate access.
This is forensic-level intelligence, delivered automatically – enabling incident response, fraud prevention, and Zero Trust enforcement to work off truth, not assumptions.
TYPES OF RECAPTURED DATA
Plaintext credentials
THE SPYCLOUD ADVANTAGE
Matching user credentials with cracked passwords reduces false positives, facilitating rapid remediation for exposed accounts that require intervention
TYPES OF RECAPTURED DATA
Session cookies
THE SPYCLOUD ADVANTAGE
TYPES OF RECAPTURED DATA
Device fingerprints
THE SPYCLOUD ADVANTAGE
TYPES OF RECAPTURED DATA
PII
THE SPYCLOUD ADVANTAGE
TYPES OF RECAPTURED DATA
Credit card & financial data
THE SPYCLOUD ADVANTAGE
TYPES OF RECAPTURED DATA
API keys & webhooks
THE SPYCLOUD ADVANTAGE
Action, not just alerts
With SpyCloud, you get the benefit of deep tradecraft, human intel, and advanced analytics for a big data approach that fuels automation at your pace.
Get automation-ready dark web identity intelligence delivered via native integrations or out-of-the-box connectors to:
IdP


EDRs


SIEMs

SOARs