Stay Ahead of SIM Swap Attacks with SpyCloud
A SIM swap attack is a type of account takeover (ATO) attack during which a hacker uses various techniques to transfer a victim’s phone number to their own SIM card. With access to a victim’s password and ownership of their phone number, an attacker can successfully bypass multi-factor authentication and take over sensitive accounts.
SpyCloud helps enterprises stay ahead of criminals by securing your users’ passwords, heading off potential SIM swap attacks before they start.
Understanding the Rise of SIM Swap Attacks, and What Can Be Done About Them
A SIM swap attack is a particularly insidious form of social engineering. All an attacker needs is to know which cell phone company the target uses. They call customer service, posing as the target, and ask that the target’s phone number be switched to a SIM card they own.
Once the attacker has control of the phone number, it’s then easy to bypass multi-factor authentication and get into many other accounts owned by the victim, often due to poor password hygiene like recycling the same password. Once inside, threat actors can use compromised personal identifying information, or PII, to answer security questions and get access to higher value accounts.
SpyCloud helps enterprises stay ahead of SIM swap attacks by checking user passwords against the billions of credentials SpyCloud researchers have recovered from data breaches. By remediating exposed credentials early, security teams can prevent criminals from taking over users’ accounts.
Mitigate SIM Swap Risks with Early Access to Breach Data
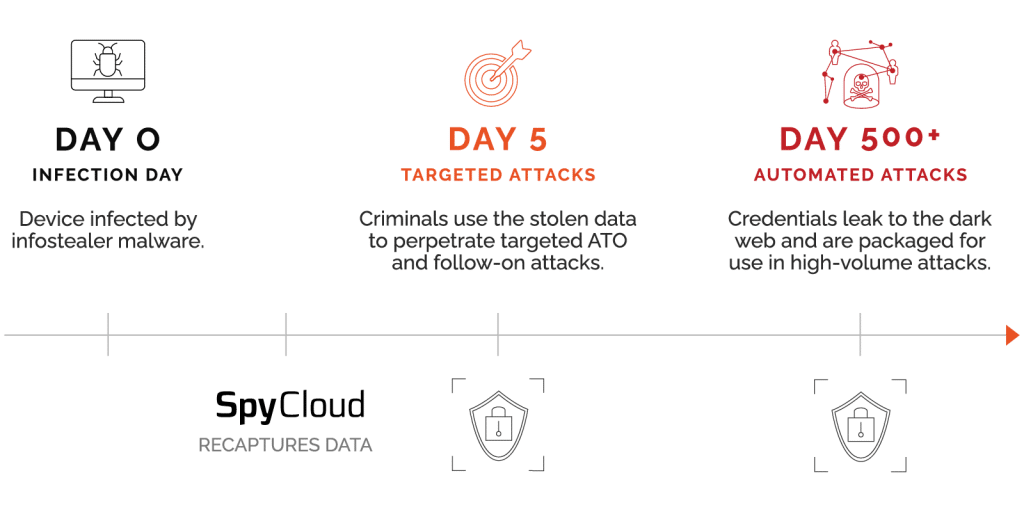
Discovering exposed passwords early in a potential breach timeline is key to limiting damage. That’s because immediately after a breach, criminals first keep stolen data close, cracking passwords and systematically monetizing the information — this includes pinpointing the highest value targets to exploit further through various account takeover tactics such as SIM swapping. The criminals typically monetize the stolen data for 18 to 24 months before allowing it to leak to a broader criminal audience.
SpyCloud helps you stay prevent this damage by identifying stolen credentials and leaked PII early. SpyCloud researchers infiltrate criminal communities to gain access to breach data before it reaches public areas of the deep and dark web, enabling enterprises to reset compromised passwords before criminals have a chance to use them in SIM swap attacks.
Monitor High Profile Users for SIM Swap Attack Risks
Just as with other account takeover schemes, high profile users are at increased risk of SIM swapping, as their wealth, influence, and/or access to corporate assets make them worthy targets of attack.
SpyCloud can monitor your company’s high value employees, such as executives and board members, alerting you in time to prevent compromised passwords from being used to gain sensitive entry to your company.
Featured Products
Our award-winning products enable you to proactively protect your users’ accounts and thwart online fraud.
Account Takeover Prevention
Remediate exposed passwords before criminals have a chance to use them.
Featured Resources
I Put a Keylogger On You, and Now You’re Mine: What Cybercriminals See When They Infect a Host with Malware
See malware from the criminal perspective, including how the data collected from infected machines gets monetized. Learn how to shield your organization from the damage caused by credential-stealing malware.
