PRODUCT: VIP GUARDIAN
Protect VIPs from Identity-Based Attacks
Without Invading Their Privacy
SpyCloud VIP Guardian extends employee account takeover prevention to key executives’ personal accounts for an added layer of protection, without invading their privacy – giving VIPs visibility into their exposed credentials and empowering them to protect their digital identities.
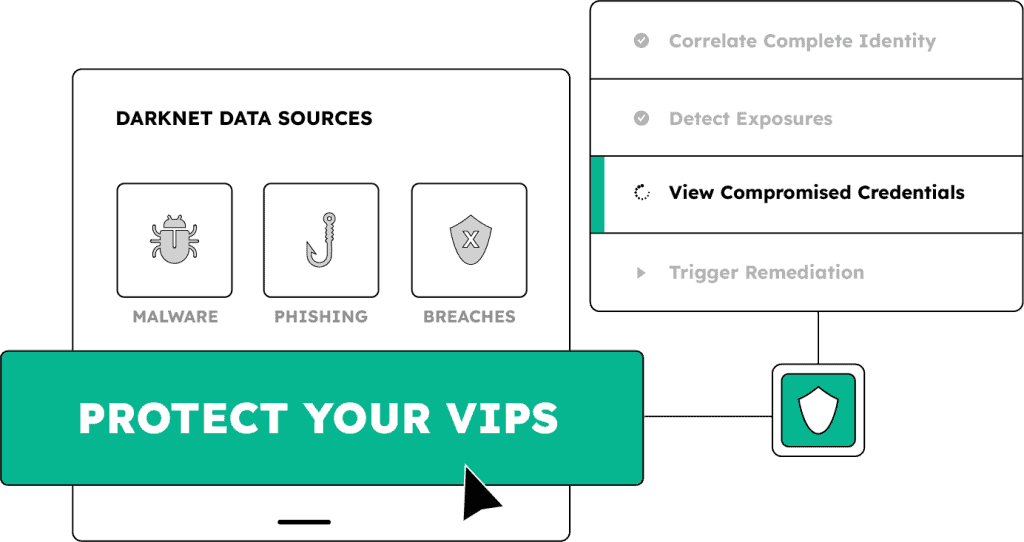
Privacy-first identity monitoring for high-value users
VIP Guardian continuously monitors for identity exposures tied to executives’ personal accounts – including credentials compromised in data breaches, malware infections, or successful phishing attacks – and delivers visibility directly to them, not your SOC.
Use SpyCloud’s recaptured darknet data to track exposures across multiple email addresses for each VIP, including personal, legacy, and family-linked email addresses that often go unchecked
Reduce helpdesk involvement by giving VIPs guided dashboard access to take secure, appropriate remediation steps based on the type of exposure
Enable SSO-based enrollment and privacy-preserving visibility – so your team gets signals and your VIPs get ownership, without friction or overreach
EXPLORE OTHER PRODUCTS
Protect more than your VIPs
Extend identity threat protection across your workforce with early exposure detection and automated remediation.
Workforce Threat Protection
Endpoint Threat Protection
Next steps
Protect your most targeted people – before they become your biggest risk.
Get a demo today.