Malware Intelligence
Botnets, also known as infostealers, are networks of computers infected with malware, and they help cybercriminals steal information at scale.
Information siphoned by malware-infected devices is shared in small criminal circles, private chat groups, and also posted on underground hacking web forums. SpyCloud’s Cybercrime Analytics™ Engine recovers this data and delivers malware intelligence to enterprises – automated insights into malware victims’ credentials and session cookies – in order to help organizations protect themselves before criminals can leverage their stolen data for account takeover, identity theft, and online fraud.
The Most Nefarious Information Stealers
Today’s sophisticated malware is distributed by masquerading as legitimate software, malvertising campaigns, advanced phishing campaigns that trick the user to download the malware, SEO poisoning of popular “free” software titles, or delivered as an email attachment (in fact, 94% of malware is delivered via email). And while antivirus software might provide some protection, oftentimes the botnet delivery methods are sophisticated enough to evade detection even by the best antivirus software.
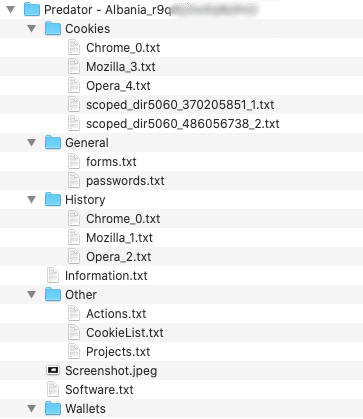
Many users who have been infected with malware have unknowingly had their keystrokes and system information stolen by cybercriminals. Once botnet malware is installed, it steals all manner of information including:
- Usernames and passwords
- Hostnames and saved passwords from browsers & FTP clients
- Session and device cookie
- Autofill data
- Bitcoin wallets
- Files with specific extensions
- Screenshots of the user desktop
- Chat history
- List of installed programs and running processes
- Machine Globally Unique Identifier (GUID) as well system architecture, system language, username and computer name
Disrupting the Ransomware Market: Breaking Down Malware and the Importance of Post-Infection Remediation
Infected User Data from SpyCloud
Customers find tremendous value in SpyCloud’s malware data. SpyCloud identifies your employees’ and consumers’ exposed user credentials and web session cookies that are siphoned from malware-infected devices (whether personal or corporate-issued). When we deliver this data to you, it means that:
- Your employee used an infected device to log into a domain, application or portal and provided a password to that destination, or
- Your consumer used an infected device to enter their username and password on your login page, or saved a cookie for your domain that has been captured by malware.
More than just their credentials have likely been siphoned, and the danger is amplified in our world of remote work, third-party vendors, and offshore contractors. While the risks of an infection on a company-owned system are obvious, infected personal devices can also endanger corporate resources — and they typically aren’t monitored by corporate security. Busy employees often blur the lines between personal and work-related device usage, meaning an infected system at home has the potential to expose work login credentials and data.
More Complete Malware Infection Response With Post-Infection Remediation™
Post-Infection Remediation is a critical addition to malware infection response frameworks that exists only now – because SpyCloud makes it possible to understand and visualize the full scope of threats posed by malware.
PIR offers a series of preventative steps designed to negate opportunities for ransomware by resetting the application credentials and invalidating session cookies siphoned by infostealer malware.
Disrupt cybercriminals attempting to harm your business by effectively stopping malware exposures from becoming full-blown security incidents.
Featured Products
Compass
The enterprise North Star in navigating ransomware prevention through Post-Infection Remediation.
Session Identity Protection
Prevent criminals from using stolen cookies to bypass MFA and access users’ accounts.
Consumer ATO Prevention
Protect your users from account takeover fraud and unauthorized purchases.
With SpyCloud's botnet data, we've protected thousands of accounts representing tens of millions of dollars of funds.
Global Fintech Company
FINANCIAL SERVICES
Learn How a Global Fintech Company Uses SpyCloud’s Botnet Data to Protect Customers from Fraud
Featured Resources
Post-Infection
RemediationTM Guide
Post-Infection Remediation is the missing piece to your ransomware prevention strategy. Read this guide for seven steps to truly remediate malware-infected devices.
2023 Ransomware
Defense Report
Our annual report shows a surprising increase in organizations that experienced multiple ransomware attacks, the costly impacts of ineffective countermeasures, and future plans to improve defenses.
Disrupting the
Ransomware Market
Malware infections siphon valuable data like fresh credentials and web session cookies, giving bad actors the virtual keys to your enterprise. SpyCloud breaks down malware infections and offers context into the steps criminals take and what can be done to stop this insidious threat.

