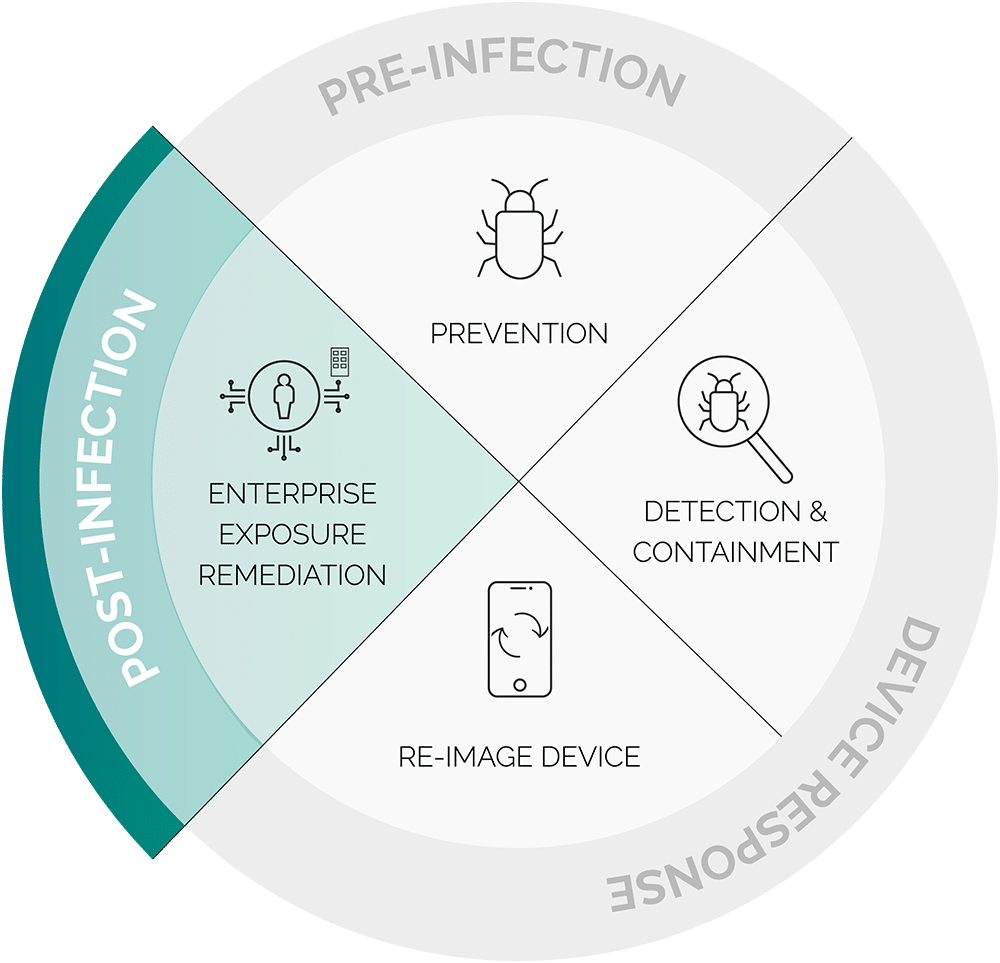
The new paradigm for preventing ransomware is Post-Infection Remediation
The game has changed for Security Operation Centers
When’s the last time your security tools and intelligence alerted you to an unexpected ransomware entry point – like a set of stolen credentials for your code repository or a stolen cookie for your SSO? This data is being siphoned from employee, vendor and contractor machines infected with infostealers. And this lack of visibility is the biggest blind spot in ransomware prevention strategies. With SpyCloud, Post-Infection Remediation enables SOC teams to improve their efficiency and their organization’s security posture.
Deep
visibility
Get visibility into malware-exposed workforce applications – with real-time alerts containing detailed evidence of exposed passwords and stolen cookies that allow criminals to bypass authentication entirely
Identity-centric
response
Modernize your malware infection response and go beyond the device – shifting your paradigm to one that’s identity-centric, enabling mitigation of organizational risk from exposures tied to the malware victim’s identity
Robust discovery,
rapid results
Eliminate guesswork and uncertainty – with clear and actionable steps to reset the credentials and invalidate active sessions for every exposed application and user
Typical infection response stops once the device has been cleared of the malware. That’s where PIR begins. With visibility into malware-exfiltrated access details, the SOC can take additional steps for a more robust response that negates follow-on attacks like ransomware. For each affected application, PIR entails the following steps:
Invalidate active sessions
Clear active sessions on all devices, which invalidates the cookies siphoned by the malware and locks the bad actor out. Prioritize SSO exposures that grants access to multiple corporate applications.
Reset password
Require the user to reset their password.
Review access logs
Review the user’s activity and access within each application. Confirm that all access was driven by the user and coming from their expected IP addresses and devices.
Explore SpyCloud
Enterprise Protection
Reduce your risk of ransomware and other critical attacks – acting on known points of compromise
Learn more
Consumer Risk Protection
Take a proactive approach to combating account takeover and stop high-risk attacks tied to malware
Learn more
Investigations
Efficiently piece together criminals’ digital breadcrumbs to reveal the identities of specific adversaries engaging in cybercrime
Learn more
Data Partnerships
Access comprehensive breach and malware data to add value to security and fraud detection products and services
Learn more
SecOps
Efficiently secure employee identities and safeguard corporate data and critical IP from cyberattacks.
Learn more
Threat intel teams
Investigate and stop threats with insights well beyond raw data and IOCs
Learn more
Cybercrime Analytics
Learn about the new way to disrupt cybercrime with automated analytics that drive action
Learn more
Test our data
We’re confident you’ll get more matches with SpyCloud – let’s do a match rate test
Learn more
Check your exposure
Uncover threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures
See your results
SpyCloud Post-Infection Remediation FAQs
Post-Infection Remediation is SpyCloud’s critical addition to malware infection response – making it possible to understand, visualize, and act on the full scope of an infection’s threat to your business. The result is negation of entry points for ransomware attacks fueled by malware-exfiltrated access details (credentials, cookies, and more).
Post-Infection Remediation provides a framework of additional steps to existing incident response protocols, designed to shut down opportunities for ransomware and other targeted attacks by resetting the application credentials and invalidating session cookies siphoned by infostealer malware. This optimized remediation enables the SOC to seamlessly and comprehensively neutralize the risk of ransomware from these exposures.
It’s an approach uniquely enabled by SpyCloud’s Cybercrime Analytics. We alert security teams each time a malware infection arises on a device accessing your workforce applications. The alerts deliver definitive evidence of entry points to your organization: detailed information about the device, along with the siphoned authentication details for the applications that matter to your business – password managers, security tools, marketing and customer databases, learning and collaboration applications, and HR and payroll systems, to name a few.
As a result of Post-Infection Remediation, security teams can now disrupt cybercriminals attempting to harm businesses.
Endpoint protection products still miss certain infostealer malware types on corporate devices, and do not account for infections on unmanaged / personal devices accessing corporate applications. Post-Infection Remediation is enabled by a product called SpyCloud Compass, which detects infostealer infections on managed, unmanaged, and undermanaged devices where authentication details have been exfiltrated and likely to be used against the enterprise. In short, Post-Infection Remediation is additive to EDR.
Next steps:
Download the guide
Get an in-depth look at how to close the gaps in malware infection response.
Read the ebook
See how criminals use malware-exfiltrated data to perpetrate ransomware attacks.
Check your exposure
Identify threats to your business from malware-infected employees and stolen cookies.